(en) Storytelling
This manual is for trainers using storytelling as a feminist approach to facilitate space for activists to tell their stories in their own voices. Participants’ stories are not mediated through another nor are they (re)presented. Through the storytelling they represent themselves. Embedded in this module is how to create stories taking into account digital safety and understanding digital safety in activism. We have arranged the modules so that they can be used together or as stand alone sections.
- Introduction and personal stories for transformation
- Embedding digital safety in storytelling
- Introduction
- Section 1: Digital identifiablity and content production
- Section 2: General safety considerations in choosing technology for storytelling and sharing your stories
- Section 3: Safety and online videos
- Section 4: Safety and podcasts
- Producing and editing a story
- Creative commons licensing, distribution and attribution
- Understanding how to reuse material
- Understanding how to attribute
- Searching openly licensed resources
- Cheatsheets
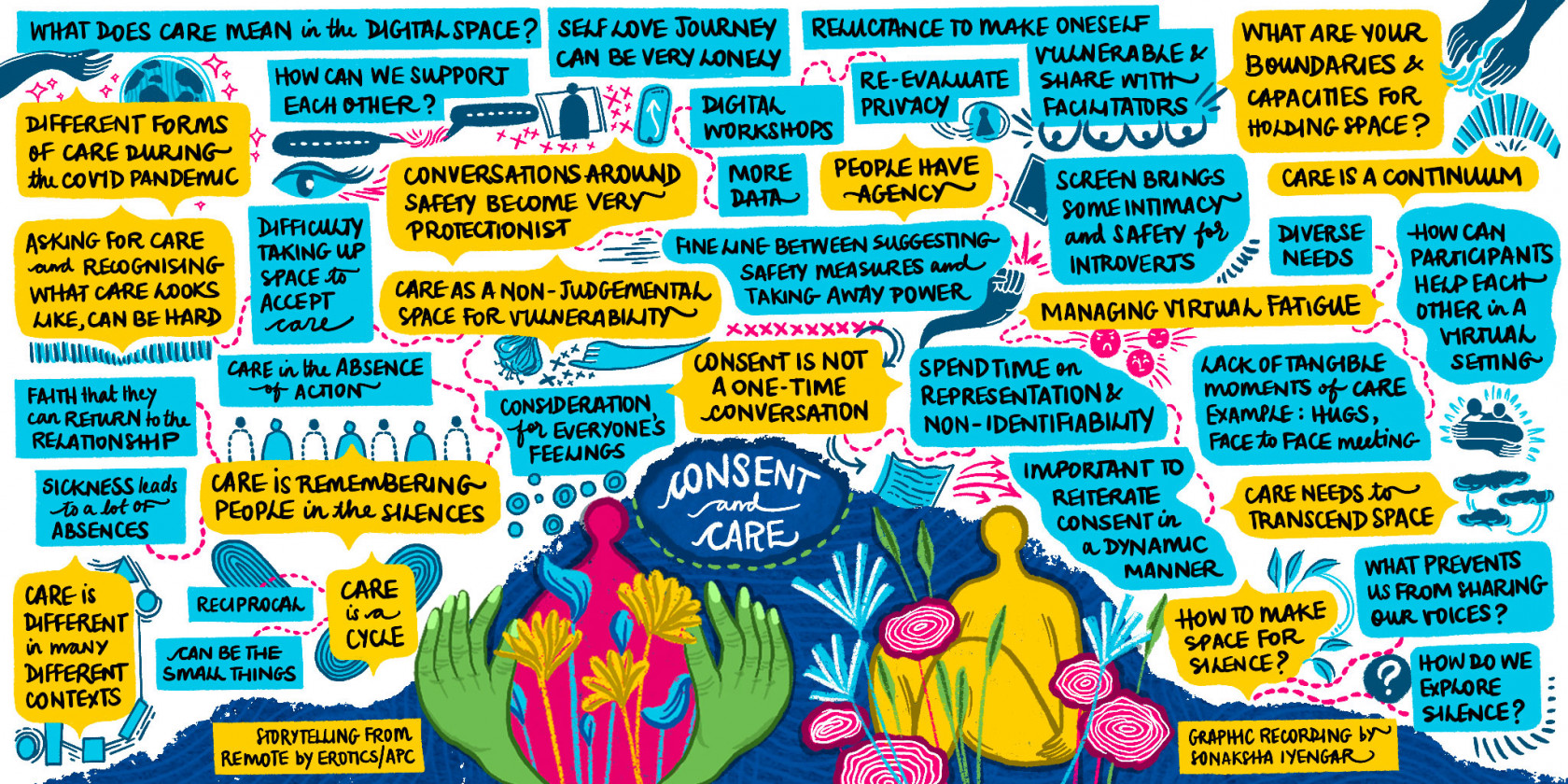
- Storytelling from remote: Safety and care in online spaces
Introduction and personal stories for transformation
Introduction to using the manual
Please note that this manual is a work in progress!
This manual is for trainers using storytelling as a feminist approach to facilitate space for activists to tell their stories in their own voices. Participants’ stories are not mediated through another nor are they (re)presented. Through the storytelling they represent themselves. Embedded in this module is how to create stories taking into account digital safety and understanding digital safety in activism. We have arranged the modules so that they can be used together or as stand alone sections.
The sections are:
- Personal stories for transformation
- The form of a story
- Representation and safety: Embedding safety in digital storytelling
- Producing and editing a story
- Creative commons licensing, distribution and attribution
- Storytelling from remote: Safety and care in online spaces
Why storytelling?
What is the first story that you remember that was told to you or that you told to someone, and how did you feel? Do you remember the voice wishpering in the evening before falling asleep, your favourite bed time story?
Stories are defining moments. They can bring intimacy, help clarify matters or bring more complexity. They are, like the internet, a mutual relationship between the teller(s) and the listener(s). They tell us about the world, the people, the culture, hopes, fears, knowledge, dreams and nightmares. Our memories are all made up by stories. They are the embodied sense of the lives we and the ones around us live. When a story is told and is listenedt to that story becomes alive, becomes part of a larger memory and that why storytelling is so deeply embedded in feminist practices.
If we move between stories we heard in our feminism and activism, we will realize how many stories populate them. We will realize how often we use storytelling to share reasons, practices, strategies, tactics and knowledge. So storytelling is not a methodology but more a practice and as such can be contextualized, located and shared from one to another.
Telling a story is an act of creation and a creative act in itself. So the more stories we share with each other and beyond our close and safe circles of activism, the more we name and populate the world with our own naratives. These narratives and perspectives all together hack, crash, transform and challenge mainstream narratives.
That is n itself, a deeply political act. The intention, will and desire to inflate the world with sounds, images, shapes that otherwise would not be seen or heard or touched. In the digital world, or better to say in this increasingly digtial time, stories become themselves digital, for the way they can be produced: podcasts, videos; for the way thay can be created: crowdsourcing, storytelling platforms, for the way they can be shared and disseminated online via mobile phones, to YouTube, vimeo and many other spaces.
We all have stories to tell.
Our worlds are created through stories. We are made of stories. Stories bring us together, enable us to explore our experiences and make sense of the world around us, our relationships to ourselves, to our loved ones, our activism – to our lives. Stories are ways of sharing, of learning of creating meaning, of finding a sense of place and belonging. It’s in the telling that we discover how much of our experience and learning we have in common with others. Stories are as powerful for the teller as they are for the listener. Stories break us open and stories heal us. Stories help us listen more deeply to our own hearts and to the hearts of others. Sharing stories in a safe and held space is an individual and collective reflective practice. It enables us to hear ourselves through the hearts and ears of others.
Our journey and approach with storytelling
The Association for Progressive Communications Women’s Rights Programme (APC WRP), started their journey with digital storytelling for transformation in 2007. Since then we have collaborated with partners around the globe to use digital storytelling as a feminist methodology for personal and collective healing, for evaluation, for building stronger networks and to build an alternative knowledge commons of people telling their own stories, in their own voices. We have partnered with organisations and individuals working on disability rights, preventing gender-based violence, sex workers, trans* activists, sexual rights activists and evaluators. Stories.apc.org
We are clear that people should tell their own stories, in their own voices and on their own terms. The storytellers own their stories. We are taking the power back and women’s stories should not be mediated by anyone else. Far too often women and gender non-conforming people have had their stories co-opted or told by others. We are claiming back our own stories.
We are now looking at storytelling more broadly and not just digital storytelling. We realised that in many of our spaces, it was the stories that opened people to a deeper and more embodied understanding of issues. In 2017 we we worked with a methodology called “The Museum of Moments” where we then adapted this to “The Museum of Movements” at our Making a Feminist internet convening.
What we are clear about is that this methodology is feminist, political and co-created in safe and inclusive spaces.
Embedding digital safety in storytelling
Issues on digital safety as it applies to digital storytelling.
Introduction
This will look at some of the issues on digital safety as it applies to digital storytelling.
We use the term “victim/survivor” or “victims/survivors” of human rights violations in our effort to fully appreciate and respect how people may identify differently depending on the trauma they have experienced, and may continue to cope with. Most people fluctuate in identifying between the two terms. See for example the articles by Danielle Campoamor (21 May 2018); and Kate Simon (20 April, no year stated).
This module has four sections:
Section 1: Digital Identifiability and Content Production
This section is aimed towards expanding how we understand anonymity, non-identifiability and storytelling. This section challenges us to shift our focus on security and our safety in telling our stories by better understanding digital identifiability, that is, how recognizable you can be depending on context, the information shared, and the digital data that tells on you.
Section 2: General Safety Considerations in Content Production and Choosing Technology for Storytelling and Sharing Your Stories
This section is about ways in which a storyteller can secure themselves, the people in their stories, and the stories themselves as they create and share their stories. This section takes the trainer through the different processes and tasks involved in digital storytelling, and looks at safety considerations for each aspect.
Section 3: Safety and Online Videos
This section is about the safety, privacy and ethical considerations in creating and publishing videos online.
Section 4: Safety and Podcasts
This section focuses on safety considerations in podcasting.
Section 1: Digital identifiablity and content production
Expand our understanding of anonymity and how it is never a permanent state of non-identifiability.
Introduction
Oftentimes, we will immediately think of being anonymous when we do not want others to recognize us in the telling of our stories. There is no doubt that anonymity has played a particularly huge role in making it easier to tell difficult stories, especially when these stories speak of atrocious human rights violations and there is a continuous need to protect the storyteller or to reduce the sense of vulnerability and targeted persecution of a marginalized individual or community.
Learning objectives
This section is aimed to expand our understanding of anonymity and how it is never a permanent state of non-identifiability. “Anonymity”, in practice, generally means to be nameless and faceless. However, you can be recognizable despite being nameless and faceless and this section explains how this can be possible. The section asks that we shift our focus on security and our safety in telling our stories or first person narratives by better understanding digital identifiability. By the end of this section, the participants will:
- Gain an increased understanding of the link between anonymity and safety.
- Be able to identify the difference between anonymity and non-identifiability.
- Gain an increased understanding of the importance of establishing trustworthiness and credibility in storytelling, especially if it is in relation to discrimination, stigma and violence.
- Understand the link between metadata and safety in digital storytelling.
Creating anonymity
Creating anonymity can be done in many ways. For example, in Nepal, domestic violence survivors have resorted to speaking behind curtains in telling their stories. In most situations, vulnerable storytellers will agree to tell their stories in videos/film as long as their faces are not shown or blurred and/or their voices distorted (see Section 2: General Safety Considerations in Content Production and Choosing Technology for Storytelling and Sharing Your Stories). However, many human rights activists and storytellers strongly discourage the blurring faces or distorting of voices; the reasons why link to establishing trustworthiness and credibility of the storyteller.
Victims/survivors of human rights violations who have told stories anonymously include, among others, domestic violence survivors, those who have been trafficked, and those who face marginalization, stigmatization and religious persecution such as lesbians, gays, bisexual, transgender, intersex and queer (LGBTIQ) persons, people living with HIV and AIDS and women who have alleged sexual harassment against perpetrators who continue to hold power over them, likely because of employment and financial dependence of other forms.
Anonymity, specifically its adjective "anonymous", is derived from the Greek word anonymia, meaning "without a name" or "namelessness". So anonymity usually means in real terms to be nameless and faceless. However, you as the digital storyteller can be nameless and faceless in various ways.
For example, in everyday circumstances, and to her family, friends, and authorities, this is Susan Chan.
Image Source: Adapted from https://freesvg.org/group-of-people-vector-image.
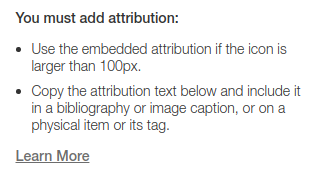
IMPORTANT Note: Photographs or images of real people are not used because of the inability to get direct consent, and at this point, a real image of a person does not necessarily better facilitate understanding.
|
Creating Anonymity |
|||
SUSAN |
ANONYMOUS |
||
| Susan (a generic or common first name, without a face). | Use an avatar-type icon but with a pseudonym: “Pootie Pie” | Instead of a name or pseudonym, just refer to her as “anonymous” (without a face) | A mere silhouette |
Image Sources: Adapted from https://freesvg.org/group-of-people-vector-image
Some people have argued that namelessness, though technically correct, does not capture what is more centrally at stake in contexts that require anonymity. This is because anonymity is not necessarily equivalent to non-identifiability, and the risk of identifiability in fact increases in digital spaces.
The important idea here is that a person be non-identifiable, unreachable, or not trackable. Anonymity is seen as a technique, or a way of realising certain other values, such as privacy, or liberty. However, anonymity does not guarantee a permanent state of non-identifiability because its effectiveness is affected by space and time, or context.
In short, it is impossible to be anonymous in every single space and at every single time. So this module is to help us shift our mind sets to linking security and safety with non-identifiability rather than merely anonymity in the telling of difficult stories, and stories of human rights violations.
Storytelling and non-identifiability
There is no doubt that in many cases, anonymity is the main technique used to secure non-identifiability. From witnessing crimes and whistle-blowing to claiming human rights from violent perpetrators and perpetrators who continue to hold oppressive power over us. So in telling difficult stories, we often have to think about, quoting Foucault, to which power are we speaking our truths. Foucault was a French philosopher, whose theories examined the relationship between power and knowledge, and how they are used as a form of social control through societal institutions. It is precisely because our difficult stories disrupt the status quo and challenge the power and privilege of some, it is important to also consider when anonymity is considered illegal in your country and under what circumstances your identity as a storyteller may have to be revealed because of the law.
This module focuses on digital storytelling and not recounting stories as victims/survivors, witnesses or whistle-blowers. The two are quite different because recounting a story as a victim/survivor, witness or as a whistle-blower requires verification of facts (by authorities and other third parties such as human rights defenders) and the establishment of the chronology of events.
The table below provides some key differences between storytelling and telling stories as victims/survivors, witnesses or whistleblowers of human rights violations/crimes, that is, telling stories for evidence-gathering.
|
The Differences between Digital Storytelling and Telling Stories as Victims/Survivors, Witnesses or Whistleblowers of Human Rights Violations/Crimes |
|
|
Telling Stories for Evidence-Gathering |
Digital Storytelling |
|
Identity has to be identifiable, at least, to selected authorities/persons and human rights defenders. |
Identity need not be identifiable |
|
Content needs to be verified by human rights organisations and/or authorities for facts/details, chronology of events, and accuracy |
Content need not be verified for facts/details, chronology of events and accuracy |
|
Content should just state what happened, and use actual visuals of persons involved (if possible), voices, places, etc. |
Content can be creatively delivered, using storyboards, and other storytelling techniques. |
Identities and non-identifiability
In using “stand-ins” to represent yourself, like avatar icons, you must always check to what extent it is identifiable with you. For example:
- A photograph of your favourite café in a specific location will render you more identifiable compared to a place you have never been to.
- Using a pseudonym that friends and others know that it is something you are fond of using or have used before, makes you identifiable. The earlier example of Susan Chan shows that she uses “Pootie Pie” as a pseudonym, but if people who know her know Susan Chan loves “Calvin and Hobbes” and in particular, Hobbes, the use of “Pootie Pie”, even though a pseudonym makes her likely identifiable.
- Using an avatar that looks like you makes you identifiable. The earlier example of Susan Chan shows that her avatar icon looks like her, short black her, similar shape of the head, etc.
- Using a photograph of your best friend or friends makes you identifiable.
- Using your initials and birthdate definitely makes you identifiable!
What you use to represent yourself as the storyteller tells a lot about you except for something generic like “anonymous” or “pseudonym”.
Some storytellers do think that their names are so generic in their social contexts that it would be difficult for people to know if it is really them, especially on social media where only handles are used or the image is non-identifiable. If you have such a name in your locality or country, do remember that while it may be a little difficult, it still means that your identity would be one of those suspected for those who have met you, know you and come across your story online. You are also identifiable by the content that you have been posting online which may refer to your regular activities, or a specific event that others know you attended.
Your identity, however, is not merely limited to your name and your face. It is your skin colour, the shape of your hands, your favourite nail polish, your favourite shoes, your worn out sandals, the way you dress, your bag, your toes, your fingers, your nose, your mouth, your eyes, your ears, the side of your face, the way you wear your hair, the kind of haircut you have, your bedroom, your study, the front of your house, the back of your house, the place you work, the road you live on, your family, your children, your partner, your friends, your neighbours, your office colleagues, any cause you are associated with, the way you walk, the way you sit, the way you stand, and the way you talk. All of these can also be easily identified with you if you have been active on social media and have been posting a lot about your life, your activities, where you go, what you do, and who you hang out with.
Identifiability and narratives
The way you talk and tell your story tells a lot about you. The way you string words together, your writing style, your favourite words and phrases, and what you usually say to express shock, anger, surprise, all tell on you.
Voice
Some of you may already be thinking “my voice is certainly identifiable with me”, but storytellers have also pointed out how the voice alone is not necessarily identifiable. This is because voices can sound similar to one another, unless your voice is a popular personality’s voice, a radio personality’s voice, a popular singer’s voice, a broadcaster journalist’s voice or a politician’s voice. Unless you have spoken in public many times, or are already a known and public/popular personality, what makes your voice identifiable is more about what you say and how you say it.
Past recounting of your story
Finally, your story will be identifiable if you have shared it before (whole or in part) or if others intimately know you and the specific experience you are speaking of. For example, an ex-husband who was violent towards you would know who you are if you speak of a particular experience, if you reference your mother, father or children. If you talk of a dress you were wearing, the kitchen where it happened, and so on.
Using storytelling techniques
What can help make you less identifiable is in telling your story in response to someone who has a similar story, someone you are unlikely to tell a story with, and someone whom your family and friends have not met. This means placing your story against another story, almost like a backdrop to your story or you may want to weave together two stories in such a way, that they reflect each other in parallel. These are tricks of storytelling and narrative development, and you may want to explore how to shape a narrative through creative storytelling techniques. Such as using a different starting point as your story, or speaking ambiguously in relation to your identity and yet tell a story that carries your truth.
REMINDER: Human rights defenders who want to use your story for witnessing or part of their evidence against a human rights crime will certainly not encourage you to use storytelling techniques. For such stories, you will likely need to talk about the specific incidence in chronological order with as much facts and clarity as possible.
Non-identifiability and credibility
One of the main reasons why storytellers should not ever blur their own faces is because you want to establish your trustworthiness with your audiences. Increasingly, blurring of faces and distortion of voices is often associated with being a criminal. Not showing your face does not mean you cannot show other parts of yourself (but do check the extent of identifiability) or use things to represent you (like a flower, a rainbow, a movement, a place, shoes, a river, etc.).
In the human rights sector, when storytellers speak of human rights violations and abuses, it is often anchored on the credibility of the human rights or intermediary organisations that publishes and distributes these stories, and ultimately uses them for policy advocacy and/or to pursue justice for the victims. For first person narratives, however, or what people generally refer to as personal storytelling, there are two key aspects that lend credibility:
- The clarity of your voice. The more muffled your voice sounds, the less likely you will come off as a trustworthy storyteller.
- The resonance people have with your story lends believability and credibility to the story content, which in turn allows people to give you the benefit of the doubt despite you not being identifiable as the storyteller.
These aspects are particularly important for individuals, groups and communities who are discriminated against or considered deviant such as people living with HIV and AIDS, sex workers, migrant workers, refugees and LGBTIQ persons.
CRITICAL ONGOING DEBATES: Some of the more recent debates around anonymity and human rights involve the use of encryption and the defense of our basic right to digital anonymity. This is because some governments, if not all governments, are keen on establishing a back door to encryption so that they can see what content you are browsing (such as a the use of HTTPS to help secure your browsing activities over the internet) and if you are a potential threat to national security. However, an interesting distinction is made between cultivating an opinion by doing the necessary reading and/or research, and expressing that opinion with conviction. These debates have serious implications for human rights storytelling because lived realities are fact, but perception of the experience itself, the negative impact, the perceived reasons for such violence and abuse (other than the actual acts of violence and abuse), can be said to be the storytellers attempt to try to make sense of the discrimination and violence, and should not also be penalized in any way for such expression.
Manipulating images to make them less identifiable
How-to steps
Manipulating images to make them less identifiable
What makes an image identifiable? The faces in it. Details that identify a location – common landmarks, street names, unique features.
Content producers need to determine before they start capturing images and footage if they want to make their content less identifiable as they take the photograph or the footage, or if they will manipulate the images and the footage for anonymity non-identifiability after they have captured and stored them.
The most safest option is for digital stories to to obscure images and footage as they are being captured. This means, even if someone gets access to the raw footage or images, the people in it are not going to be identifiable, and there will not be an original image or footage stored somewhere online or offline that they may get access to.
There are some techniques that a storyteller can use to make the people in a photo or a video footage anonymous:
- Don´t capture people´s faces but rather capture their hands or their feet as they are being interviewed.
- Use the silhouette effect – to place a strong light source behind the subject as described here: https://library.witness.org/product/concealing-identity/
- Keep identifiable location markers (street names, identifiable buildings) out of focus in taking a photo or a capturing footage
- Use filters available on Instastories, Tik-tok and Snapchat to make videos less identifiable.
- ObscuraCam is a tool developed by The Guardian Project that allows users to capture photos to make them less identifiable. This app can also use this appbe used to obscure existing photos.
Take a photo or open the image the you want to edit in ObscuraCam. Then click on the image.
What you will see is a movable and resizable box that will let you control what you want to obscure.
You will get the following options for obscuring the photo:
Pixelate: this will pixelate whatever is captured within the box
Invert: This will pixelate whatever is outside the box
Redact: This will delete whatever is in the box
Mask: This will add a mask on the image in the box
Then save the image.
ObscuraCam is especially useful if the storyteller opts to take anonymous or less identifiable photos from the start.
Note: If the storyteller opts to anonymise, meaning to make images less or non-identifiable after they are captured, they will have to take extra steps in storing their raw images and video footage more safely.
Using GIMP to create less or non-identifiable photos
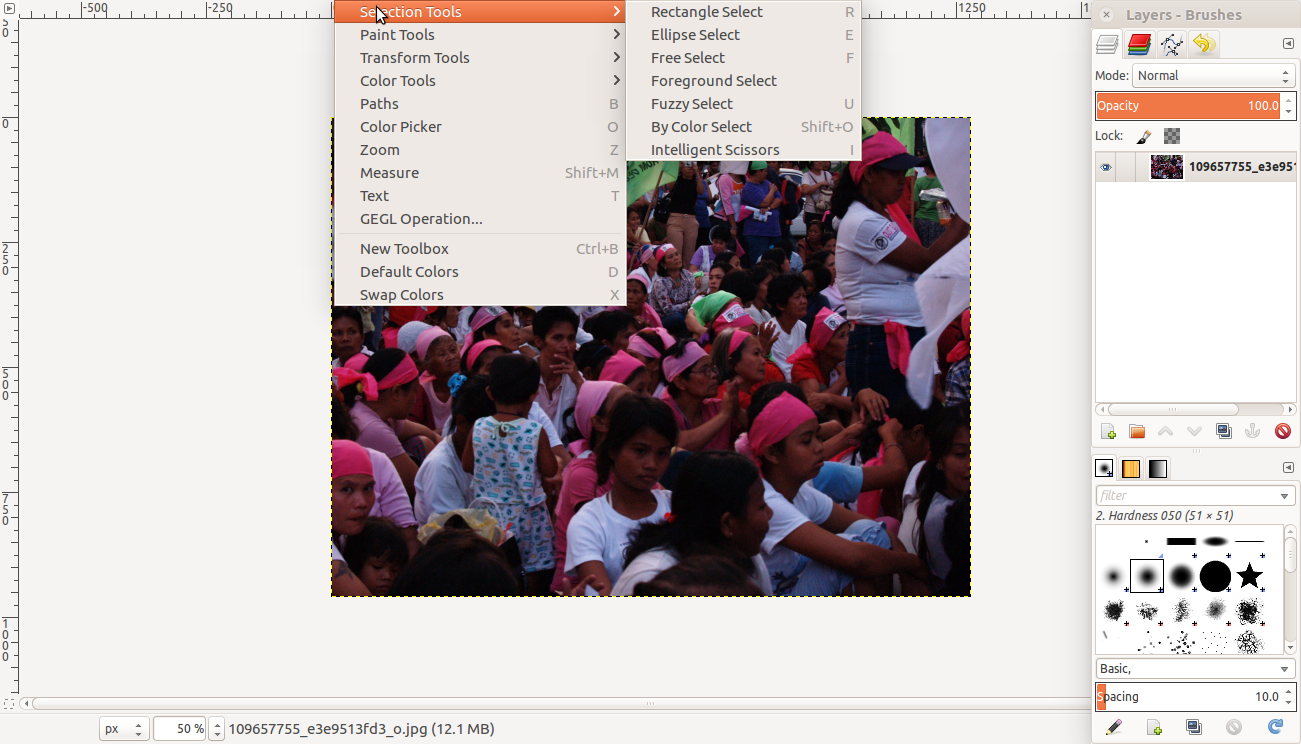
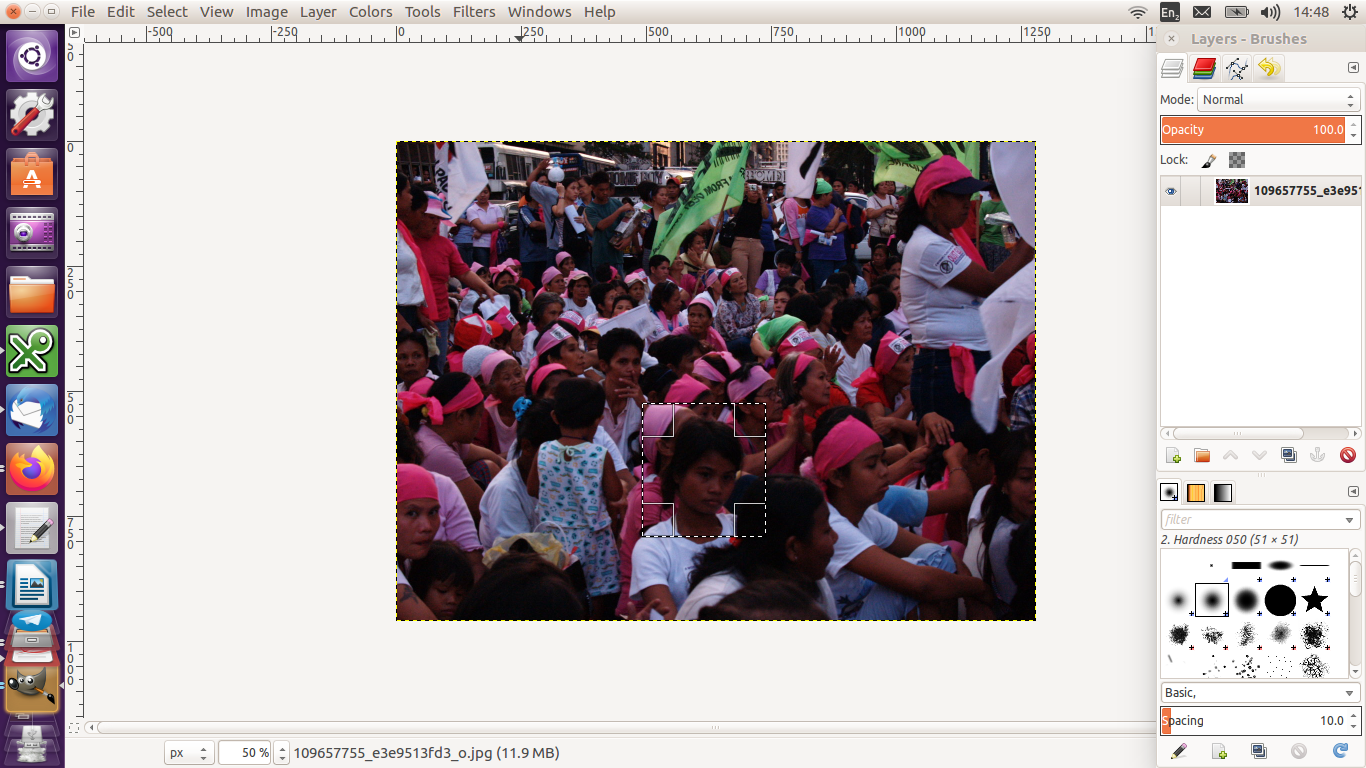
Open the image to be manipulated. Analyse what you want to anonymise or make less or non-identifiable. Do you want to anonymises identifiable make faces less or non-identifiable? Or do you want to make certain elements in the photo that will make the locations or surroundings less or non- location identifiable?
Go to Tools >> Selection Tools then choose a way to select a part of the image you want to obscure.
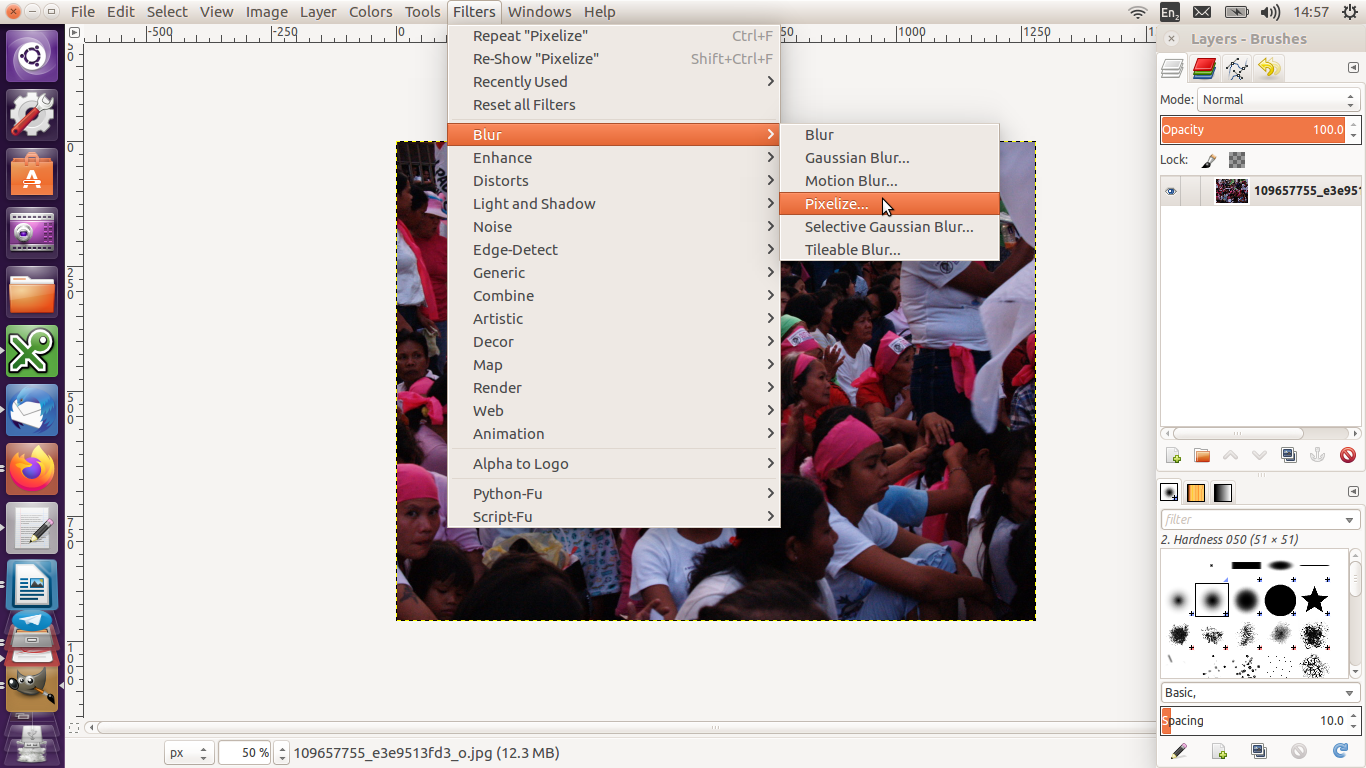
Then go to Filters >> Blur then select Pixelise. The section selected will be blurred.
You can use the other filters to obscure images.
Identifiability and metadata
“Data” refers to information. A piece of data could be a line of text, an image or a list of figures. Data is content.
“Metadata” is information about data. Metadata provides an explanation or description of the data, which is useful for finding, using and understanding of the information. It provides the context to the image or video footage. It is like the catalogue of a library, and allows for searchability of content. There are three types of metadata:
- Descriptive
- Structural
- Administrative
Descriptive metadata is typically used for discovery and identification, as information to search and locate an object, such as title, author, subjects, keywords, publisher. A simple example of metadata for a document might include a collection of information like the author, file size, date the document was created, and keywords to describe the document. Metadata for a music file might include the artist's name, the album, and the year it was released.
How to locate metadata
Usually, metadata is stored in a different file or under a different feature. For example:
- In word documents, it is located under “Properties” of the document. Just right-click on the file.
- In Facebook, you may find this under “Your Information” and then under “Your Categories”, such as your sudden change in service providers, or the fact you turned 18 because of your activities of going to bars, getting your driving license, finally being able to vote, etc.
- In most digital cameras, they are located in the EXIF (Exchangeable Image File Format) files, which includes information on the type of camera used (the make and model of the camera, and so determines which camera took what photo), camera settings like ISO speed, shutter speed, focal length, aperture, white balance, and lens type; your GPS location where you took the photo, and when (date and time) you took the photo, and the name and build of all programs which you used to view or edit the photo.
How to remove metadata
Removing metadata from Microsoft Word, Excel, or PowerPoint
Metadata makes your content identifiable, and therefore, may make you as its producer identifiable. It leaves data tracks for anyone who is looking for more information about you to find.
As content producers, it is important to have the skill and knowhow to remove metadata from the content you produce.
Delete metadata in Word, Excel, or PowerPoint
(Source: McDowell, Guy. 2019. “How to Completely Delete Personal Metadata from Microsoft Office Documents”. Online Tech Tips, 17 June. Available at https://www.online-tech-tips.com/ms-office-tips/how-to-completely-delete-personal-metadata-from-microsoft-office-documents/. Accessed on 9 February 2020)
Click on File in the top-left corner.
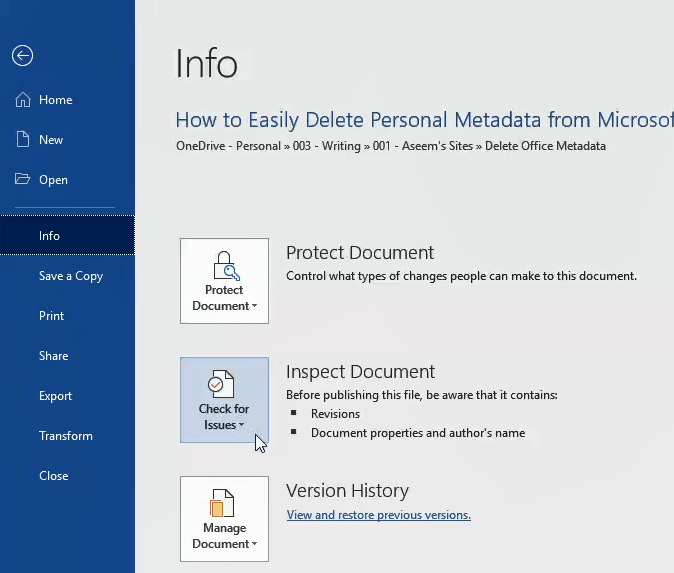
On the Info page, click on Check for Issues on the left, near the middle of the page.
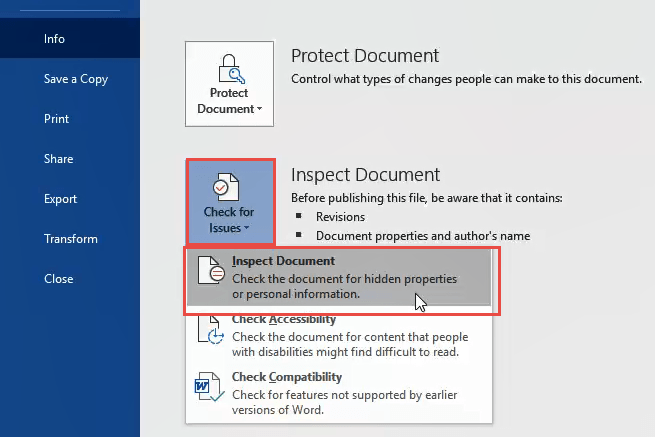
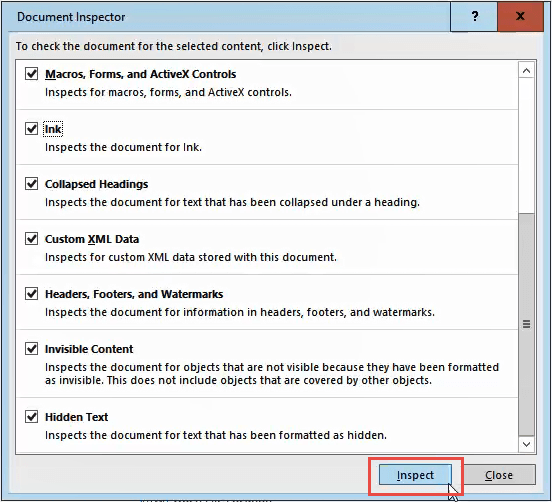
Click on Inspect Document. The Document Inspector window will open.
Make sure all the checkboxes in the Document Inspector are checked, then click the Inspect button.
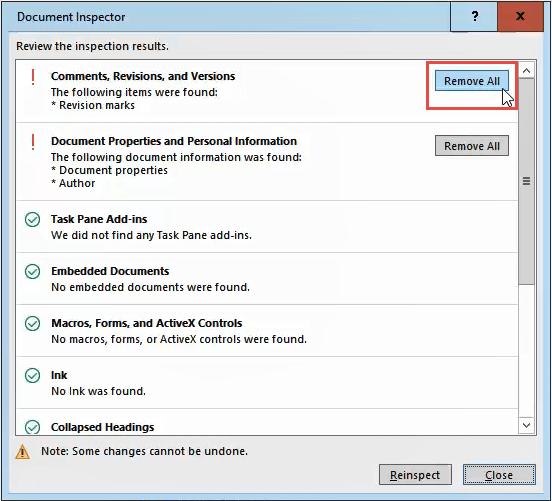
Once the Document Inspector is done, you’ll see information about what kind of data it found.
- A green checkmark in a circle means it found no data of that type.
- A red exclamation mark means it found data of that type.
Next to that data type’s description you will see the Remove All button.
Click on that to remove all data of that type. There may be several of these buttons, so scroll down to ensure you get all of them.
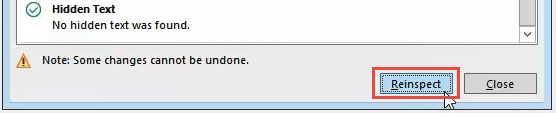
After you have removed the metadata, you may want to click the Reinspect button, just to make sure it did not miss anything.
Save your document now to ensure the data does not get re-entered.
Removing Metadata from photos
(Source: Schmidt, Casey. 2020. “The Absolute Easiest Way to Remove Metadata From Photos”. Canto, 24 January. Available at https://www.canto.com/blog/remove-metadata-from-photo/. Accessed on 10 February 2020).
Remove metadata from photos in Windows
There are plenty of third-party apps capable of removing metadata for you but the direct method is most efficient. It requires a few steps but it’s painless. Here is the entire process laid out as easy as possible to follow:
- Locate the photo you wish to alter
- Right-click it
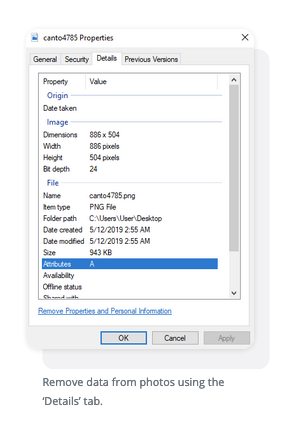
- From the popup window, select ‘Properties’
- A window will open. Click the ‘Details’ tab at the top of the window
- From there, you’ll see a list containing attributes such as name, date, size and more. Click under the ‘Value’ portion of the elements
- For the editable data, it will allow you to type in or delete whatever you want and replace the old information
- Click ‘OK’
Remove data from photos using the ‘Details’ tab.
Remove metadata from photos in Mac
Like Windows, a Mac lets users remove photo metadata in a pretty straightforward fashion. Once again, here’s an easy list to guide you:
- Open the photo using ‘Preview’
- Go to ‘Tools’ in your menu
- Select ‘Show Inspector’
- Select the (i) tab
- Click the ‘Exif’ tab and remove the data
Remove metadata from photos on mobile device
iPhone
- Open the ‘Photos’ app
- Select the intended photo
- Click ‘Share’
- Select ‘ViewExif’
- Click ‘Share’
- Save the photo ‘Without Metadata’
Without using a computer connection, you can delete pic data from mobile devices.
Android
- Open the ‘Gallery’ app
- Select the intended image and click ‘More’
- Click ‘Details’
- Select ‘Edit’
- Click the ‘-’ symbol next to details you wish to delete
Both iOS and Android have different third party apps you can download to do this process for you, like EXIF eraser.
Removing metadata from videos
(Source: Martin, Avery. “How to edit video metadata”. Techwalla. Available at https://www.techwalla.com/articles/how-to-edit-id3-tags-in-windows-media-player. Accessed on 10 February 2020).
Windows Media Player
Step 1: Launch Windows Media Player and select the "Library" tab. Select the "Switch to Library" button when in Now Playing mode.
Step 2: Right-click on the file attribute you want to edit in the library and select the "Edit" button.
Step 3: Type the new metadata information for the attribute you selected. Press "Enter" to save your changes. If you select more than one video file, then the attribute you change applies to all of the selected video files.
Step 4: Select the "Organize" tab and select "Apply Media Information Changes" if the changes are not applied immediately.
iTunes
Step 1: Launch iTunes, right-click on the file you want to edit and select "Get Info." If you want to batch edit more than one file, highlight all of the files you want to change and right-click one of the highlighted files. Click the "Yes" button to confirm that you want to change the information for multiple files.
Step 2: Click the "Info" tab and edit any of the fields to change the metadata information. You can also select the "Video" tab to edit additional fields including the show, episode ID and description. If you selected more than one file, your changes apply to every file selected.
Step 3: Click the "OK" button to save your changes.
REMINDER: Removing metadata may help you not be identifiable with the file, but what you do with the file may increase your identifiability, such as uploading that file to your social media accounts or your cloud, or e-mailing it or the link to others.
Articles on identifiability and metadata
VICE News. 2018. “All the hidden ways Facebook ads target you”. YouTube, 13 April. Available at https://www.youtube.com/watch?v=EM1IM2QUYjk. Accessed on 7 February 2020.
Matthews, Richard. 2017. “Image forensics: What do your photos and their metadata say about you?” ABC News, 23 June. Available at https://www.abc.net.au/news/2017-06-23/what-your-photos-and-their-metadata-say-about-you/8642630. Accessed on 7 February 2020.
Lea, Martin. “How your location can be discovered from a photo you post on Facebook”. Available at
https://martinlea.com/how-your-location-can-be-discovered-from-a-photo-you-post-on-facebook/. Accessed on 10 February 2020.
CRITICAL ONGOING DEBATES: There are debates to what extent digital data about your location, like your IP address, and how you access the internet, whether through mobile phone and wifi are personal data. This is because some countries have Personal Data Protection and Privacy laws. However, companies that use metadata of their users argue that these are not personal data. Chances are there is a lot of information about you on the internet, but not all of it is clear-cut “personal data”. The IP address as mentioned is one such data, but there are also other data such as the list of websites your browser has accessed, your mobile phone’s geolocation, and so on. As far as these companies are concerned, these are metadata that provide context to your usage over the internet which allows for more targeted advertising.
Section 2: General safety considerations in choosing technology for storytelling and sharing your stories
Unpacks the general safety and security considerations in digital storytelling.
Introduction
The general arc of digital storytelling is to gather photos and videos, record the narration, edit the visual and audio elements together, and then share the completes digital stories with other people. In thinking about safety and digital storytelling, storytellers are encouraged to:
Thinking about safety before beginning
When it comes to safety, there are two main considerations a storyteller should think about before production begins:
Imagining the impact of the story. The storyteller has to try to foresee how the story will affect whoever sees it. In this way, they can anticipate negative responses to their story, as well as make plans to avoid potential threats from those who are negatively affected by their story.
The Impact Field Guide has a guide to exploring a story environment for documentary films. In it, themes are categorised into four types:
FRESH: an unknown issue to your target audience and little or weak opposition.
FAMILIAR: a known issue that still has little or weak opposition.
HIDDEN: an unknown issue (to your target audience) but with strong and organised oppositional forces may require your film to prove the case - to INVESTIGATE.
ENTRENCHED: a known issue (and so possible fatigue from target audience) with strong opposition to your story and campaign - often need to offer no more new facts or assertions but simply to HUMANISE the affected communities.
It is a good idea to have storytellers think about where their stories fall into these five types, and then start thinking about what does that mean in terms of their and their story´s safety.
Some questions for storytellers to ask themselves:
- What are the positive consequences of my story? What are the negative consequences?
- Will my story hurt someone or a group of people? In what way?
- How will I feel about telling my story? Will it affect me and in what way?
- Do I have someone to speak to if telling my story makes me re-live difficult events?
- Will my story put the people in it at risk? How so?
- What can the people who are negatively impacted by story do to express their opinions? Good to think about this from what they can do to the storyteller, the people in the story, and the story itself.
Sharing of the story: Location and people. Next, based on the previous considerations, the storyteller then can think about who they want to share their story to, and how.
Generally, there are two ways that a digital story is distributed and shared. The most usual way to share digital stories is by uploading them on a commercial platform (Facebook, Twitter, YouTube). Another way to distribute digital stories is through external storage devices (DVDs, USB sticks, external hard drives).
Safety considerations in uploading digital stories on commercial platforms
The two main safety issues in sharing digital stories on commercial platforms are: the lack of control over the content and its ownership; and the lack of control over how the audience will react.
This is further explored in Section 3: Safety and Online Videos
Safety considerations in sharing via physical devices
One of the biggest issues in sharing stories via physical devices is the potential for the device to be corrupted with either malware or just reach the limit of its capacity to function. It is important therefore to have multiple copies of the content being shared, and a main back-up of the final digital story.
Safety considerations in screening your digital story
Face-to-Face Screening
If the storyteller decides to hold a face-to-face screening of their digital story, the first area of decision-making is about how private or public they want the screening to be. In order to make that decision, storytellers need to think about the following:
- What is the goal of screening this digital story? Is it to raise awareness of an issue? Is it to share personal experiences?
- Is the story going to be offensive to the viewers? Does it cover issues that people will reject because it challenges what they know or believe in?
- Will the story trigger memories in the viewers that might be difficult for them? Do you have support for these viewers from a self-care and psycho-social perspective?
- If the story will then challenge its viewers, has the storyteller taken sufficient steps to protect the people in their story to make them less identifiable and therefore, safe from repercussions?
- What can the storyteller do to prepare for possible negative, adverse reaction from the audience?
If the storyteller feels that their stories are more controversial, will put people at risk, and / or put they themselves at risk, then they can consider doing a private screening among trusted communities instead of a public one, and to be doubly sure, have a pre-registration list vetted by people whom you trust.
The next level to think about in doing face-to-to-face screenings (both private ones and public ones) is who does the storyteller want to share their stories with. In making decisions about this, the storyteller needs to reflect on a few questions:
- Who is this story for?
- Who is this story not for?
- How can I prepare the viewers of my story in managing how they will react to it?
- What can I do to prepare if sharing my story with someone offends or hurts them? What can I do to manage my own expectations about sharing my story?
- If the audience negatively reacts to my story, how can I prepare for that?
- If the audience shows minimal reactions to my story (no one loves it or think it’s a well-told story), how will I react? Will that hurt me?
- Do I need to be there as the storyteller? What risks does my presence bring me?
Learning objectives
This section aims to unpack the general safety and security considerations in digital storytelling, and to highlight strategies, tactics and decision-making points in the use of technology in the digital storytelling process.
This session will tackle the safety of the storyteller as well those in their stories, and the safety of the stories they are telling in terms of their potential impact on audiences, interested parties and authorities.
By the end of this section, the storyteller will:
- Understand why it is important to imagine the possible impact of their stories before they start making their stories
- Gain an understanding of the different safety considerations in making and sharing digital stories
- Learn about some basics of digital security as it applies to digital storytelling
It is recommended that you read the previous section on Digital Identifiability to understand the larger issues around safety and storytelling.
Safety in content gathering and production
Collection of images and videos
A typical digital story contains images and audio narration, edited together to tell a personal story. Sometimes, the storyteller will have the means to take photos, record videos and audio. Sometimes, the storyteller will have to choose to use existing photos, video and footage, and audio found online.
Protecting digital stories by using free to use content
Copyright – the right to use images, audio and other creative content made by others – is an important safety consideration in selecting which images, audio or video to use for a digital story. This is especially true if the storyteller wants to make their digital stories publicly available, and if the stories will cover topics and themes that people on the internet would object to. Copyright violations are often used as an excuse to take down content on the internet. All commercial platforms have guidelines and policies against the use of copyrighted material.
There are some strategies and tactics to make sure that storytellers are using material for their stories that do not violate copyright laws.
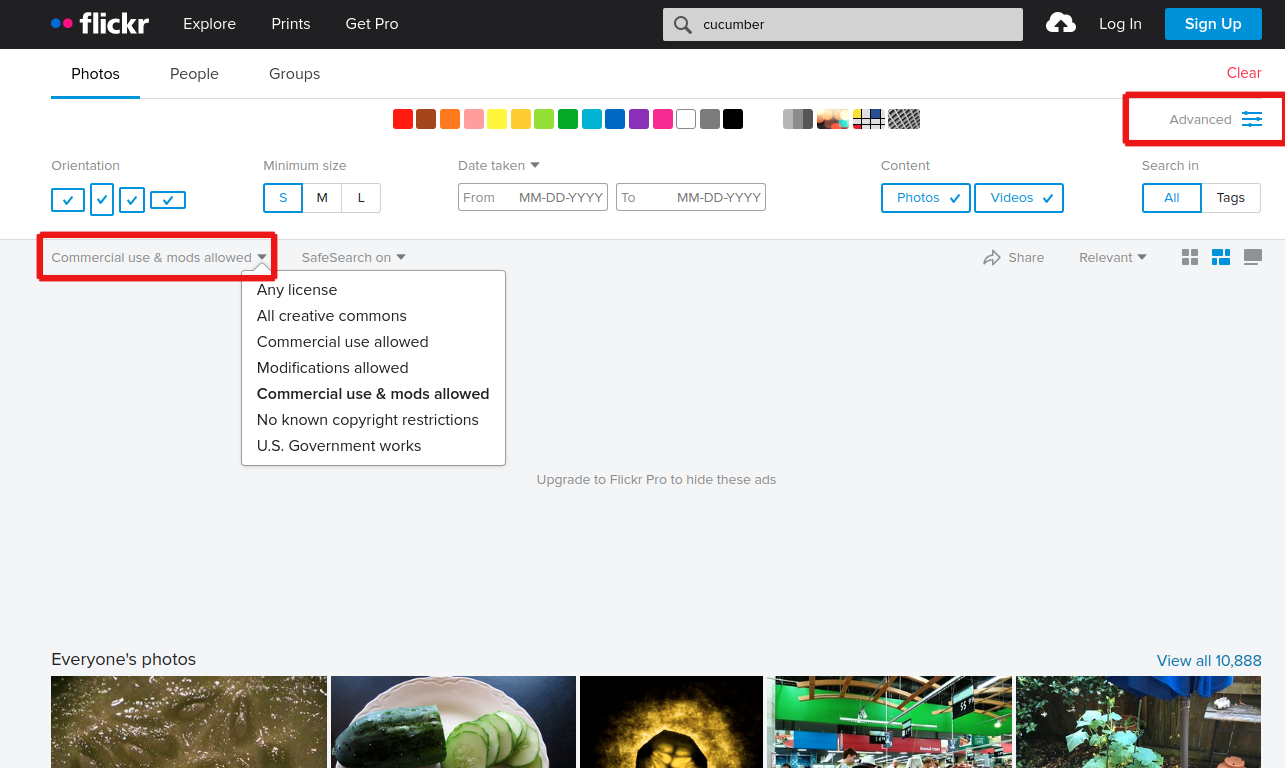
For images that are free to use and adapt:
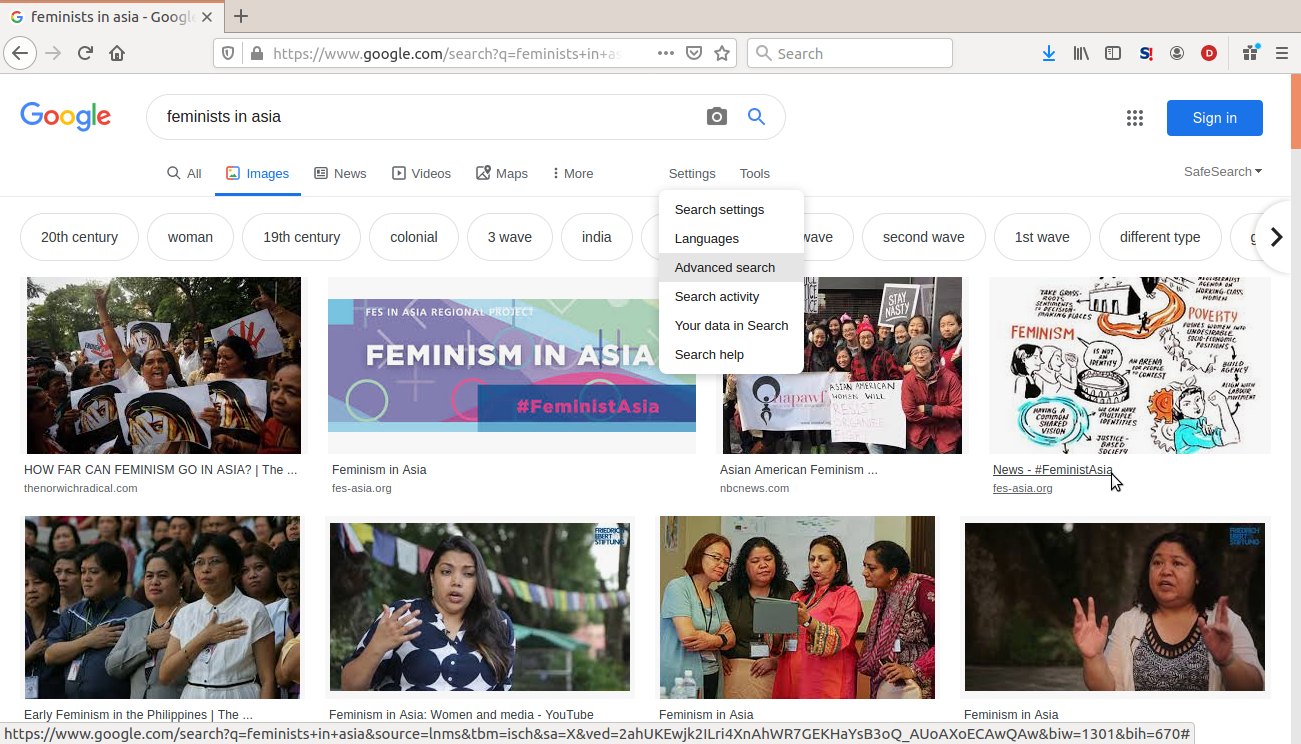
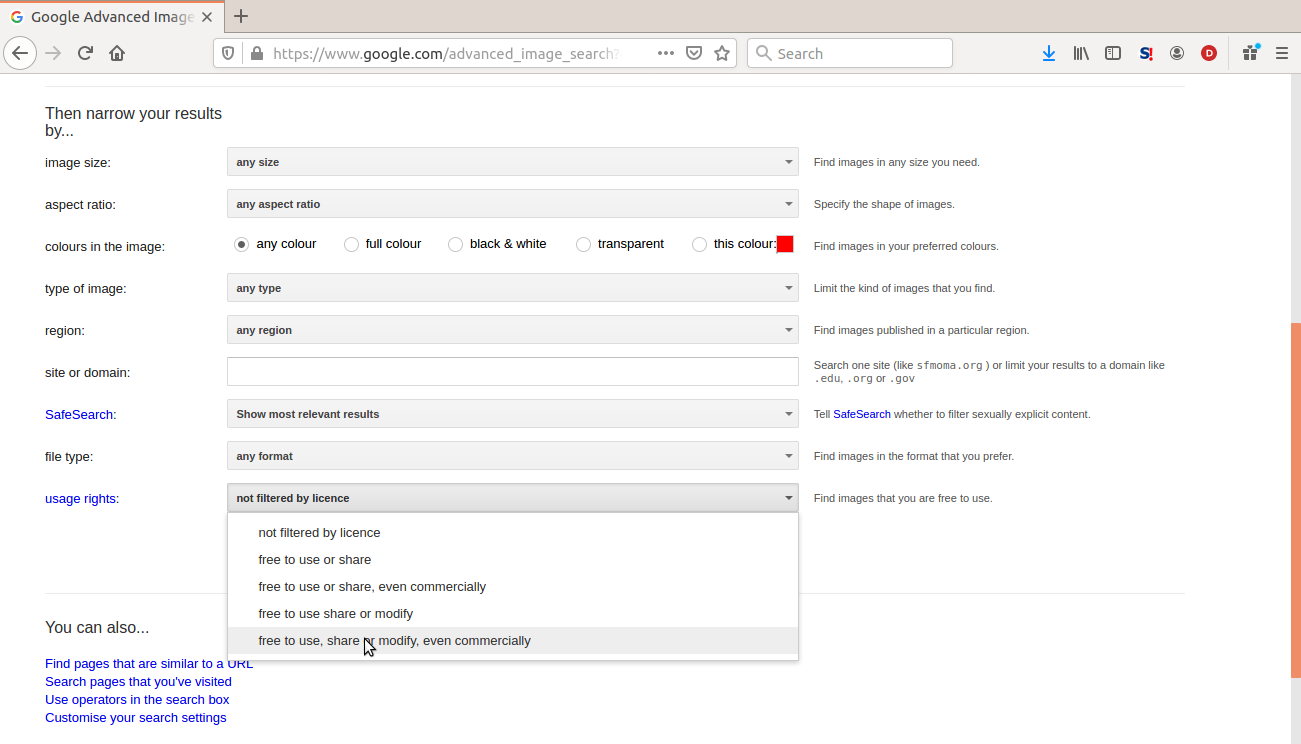
Do an advanced Google Image Search
Then select the option to only search for ¨free to use and modify commercially¨.
You can also use the following repositories of content that have Creative Commons licenses. Creative Commons licences recognize the ownership of the content creator and is an alternative to the current accepted practices of Intellectual Property Rights, where ownership tends to lie largely with large companies. It allows the original content creator to decide who can use the content, and how it can be used (non-commercial or commercial) or modified. The most unique features of Creative Commons licences is how it ensures attribution to the original content creator and that the same practice of copyright terms and conditions must be honoured and extended to others by those who use and/or modify the original content. To learn more about Creative Commons, see https://creativecommons.org/about/.
Creative Commons licences recognize the ownership of the content creator and is an alternative to the current accepted practices of Intellectual Property Rights, where ownership tends to lie largely with large companies. It allows the original content creator to decide who can use the content, and how it can be used (non-commercial or commercial) or modified. The most unique features of Creative Commons licences is how it ensures attribution to the original content creator and that the same practice of copyright terms and conditions must be honoured and extended to others by those who use and/or modify the original content.
- Creative Commons Search: https://search.creativecommons.org/
- Wikimedia Commons: https://commons.wikimedia.org/wiki/Main_Page
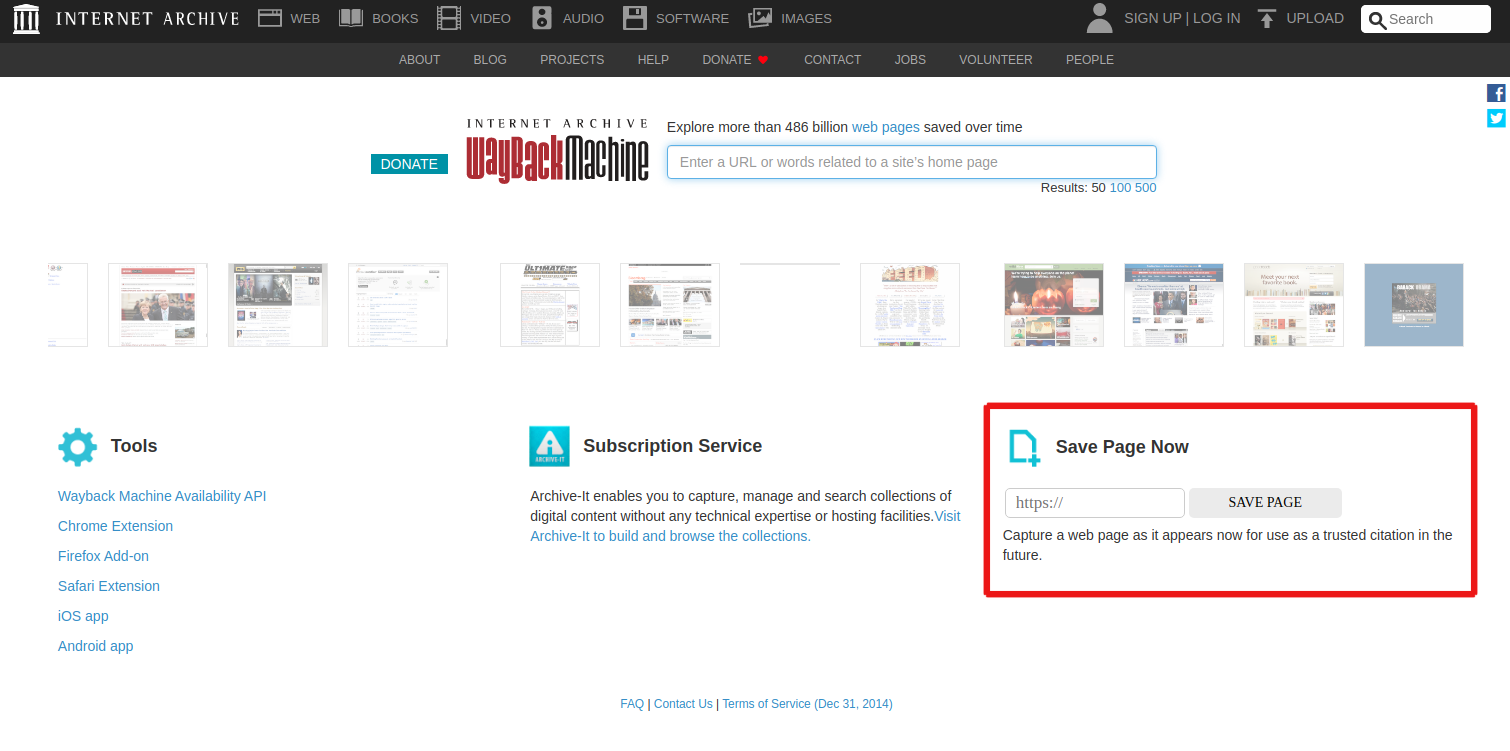
- Internet Archive: https://archive.org/
- The Public Domain Project https://www.pond5.com/free. Here you can download historical content that are free.
- Pexels Creative Commons section: https://www.pexels.com/creative-commons-images/
- Flickr´s Creative Commons section: https://www.flickr.com/creativecommons/
Free audio sites:
While these sites generally have content that is free to use, edit and adapt, e. Each material to be used has to be checked for the specifics of their copyright permissions. Some of the materials are free to use and edit / adapt but requires crediting the original creator of the content. Some do not.
It is also recommended that storyteller adds credits at the end of their story to attribute the content that they used in telling their stories.
Protecting storage devices
It is important to protect the storage devices the storyteller will be using throughout the process. Devices should be password protected, in order to secure the files within it.
Password protect computers with a more than twelve character password.
For mobile phones, there are different ways to lock the screen.
- PIN: four to six number combination
- Pattern Lock: Create a pattern with dots on your screen
- Password: any combination of numbers, letters and special characters
- Biometric locks: fingerprint, face recognition or retinal scanning to unlock your phone
Out of the options, having a secure password (more than twelve alphanumeric characters) is the safest.
- Computers and mobiles phones can also be encrypted. This provides a much more secure way to protect devices.
- According to Apple, all their computers and iPhones are encrypted by default.
- Windows machines have Bit Defender that is available on Windows 8 to later versions.
- For Android, the user has to encrypt their phones by going through the Settings.
As a digital storytelling trainer, it is good to encourage the storytellers you will be working with to do this before the training.
Backing-up content
It is a good idea to create copies of collected and created content and materials for stories in a separate device from the main working device at different points in the storymaking process. This protects the storyteller from any unforeseen and unpreventable issues like device failure or loss of files.
For example, having a USB drive where the storyteller can create a back-up of the directories of their story content. Or having an external hard disk. Depending on the sensitivity of the story as well as the internet access available to the storyteller, they can also consider backing up to cloud storage services like Google Drive and iCloud.
It is important for storytellers to determine when they are backing up their materials. Depending on the time that a storyteller is collecting content for their digital story and producing it, it is usually recommended to back up material when the collection or creation phase is over – before they work on editing or manipulating their content. Then once an edit of a material is done, there should be a back up of that. Then a back up of the final story. Do be mindful that sometimes you may realise that you do not have the content you need to create the final digital story, but do not forget to back up after all additional material is collected or created.
Section 3: Safety and online videos
Ways in which videos are created and shared online.
Introduction
Digital stories, generally, are short stories created by combining recorded narrative with images (still or moving. In short, they are a type of video as they merge audio and visual elements to tell as story.
Generally, there are two ways of sharing videos on the internet.
Produce offline, then publish online
This method is for both long-form and short-form videos. There are video-sharing sites where long-form videos can be published (YouTube, Vimeo, Daily Motion). Most popular social media platforms allow short-form videos (Twitter, Facebook, Insta-Stories).
Livestreaming: record as you post online
This is when a user records an event or an activity, and shares it as they are recording it. Some livestreaming sites (Bambuser, YouTube Live, Twitch) allow for longer streaming time. Platforms like Instagram Live, Facebook Live and Periscope (owned by Twitter) allow for shorter streaming time. Some livestreaming platforms like Instagram Live and SnapChat delete the streamed videos within a given period of time.
This section will tackle the safety consideration in both types of online video sharing.
Learning objectives
This section focuses on the ways in which videos are created and shared online. By the end of this section, it is expected that the storyteller will:
- Have an appreciation of the safety concerns in publishing videos on online platforms
- Have an understanding of how to better select video sharing platforms
Safety issues in sharing digital stories online
There are three areas of safety issues: ownership over the digital stories, what do digital storytelling platforms know about the storytellers, and safety responses of digital storytelling platforms.
First things, first: Who owns the stories?
The storyteller owns the stories -- a simple enough answer.
But when it is a digital story that they create, the answer is not that simple.
The nature of ¨digital¨ means that a storyteller has to concede some control over the ownership of their stories. Digital content can easily be copied or downloaded into individual computers or mobile phones, and then shared on other platforms.
There are software and browser plug-ins that allow people to download YouTube videos into their own machines, allowing them the ability to be able to edit videos. In that case, who then owns the story? If the user, who downloaded a video, edits it in a way that the original storyteller did not intend, is there a recourse for the storyteller?
For example, Instagram Live stories are supposed to be temporary, they are not permanent. By default, an Instagram Live video will remain on the user´s page for one month, then it is deleted. But nothing stops followers of that user from downloading those temporary Instagram Live feeds, and then sharing them on other social platforms or private online conversations -- without the knowledge and consent of the person who originally posted that story.
When a storyteller uses a commercial platform like Facebook, Instagram (which Facebook owns), YouTube (Google) or Twitter, then it becomes more complex.
According to Facebook´s license agreement, they lose ownership of content when the user deletes it. However, they clearly state that they cannot do anything about other accounts that have shared that content. In essence, because Facebook shares ownership of content with its users, they still own that deleted content which could still sit on their servers.
Secondly, what do these platforms know about the storyteller?
More than that, these platforms collect and own other data in relation to the storyteller and their stories. They also own the connections between those different data sets, and are able to share them with Third Party companies for marketing and advertising purposes. These platforms have also reported that they get approached by States for information about their users and their activities on these platforms, usually for criminal investigation1. Facebook, in fact, produces its own report on government requests for user data2.
These considerations also apply for when an user stores or backs-up their data on the cloud (for example, Google Drive and Dropbox). A storyteller might not be using video-sharing platforms to publish their stories, but they might be using internet platforms to store the raw materials for their digital stories (the images, the script, the audio recordings).
While over the years, these platforms have developed guidelines about government requests, they retain the right to change these guidelines and not inform their users about changes. More than that, this shows that these internet companies hold a lot of data, connections among data sets that provide accurate profile of users not only in terms of identity, but likes, preferences, social network and activities, and information about their users.
There are ways to obscure identity on the internet, to make connections between stories and the identities of their storytellers less obvious. Depending on how the storyteller foresees the impact of their stories, then they can take steps in protecting themselves before they share their stories on this platforms.
Thirdly, what do these platforms do when a storyteller is harassed on their platforms?
Online gender-based violence has been a growing trend on the internet for over a decade. It has escalated in a way where it is commonplace for women, queer and non-binary identities on the internet are attacked for their sexuality, appearance, opinions and even when they share lived experiences. These platforms do the minimum in response to this kind of harassment. In their End User License Agreement, they hold no liability for any harm caused over their platforms.
In simple terms, if a storyteller is harassed for their story in any of those platforms, they are on their own. At most, they can report incidents and block specific accounts, but how it gets addressed beyond that is at the platform´s discretion.
Sometimes because of the lack of knowledge of local contexts, the politics of those who own Facebook and their understanding of the exercise of freedom of speech, the common response is to tell you, the harassed victim, to block the abuser or to make your posts private. However, this only means that you are being abused in spaces where you are not privy to assess the extent of harm done against you.
Given the gaps in platform response to online harassment, it is also important to note that many feminists and women´s rights activists have found other ways to respond to the abuse and harassment they and other women and LGBTQI identities have experienced. Very often, these activists rally around someone who is being harassed online, either to report the harassers or directly respond to them. A storyteller, if they are harassed online for their stories, can reach out to feminists and activists for support.
Safety considerations in choosing platforms for video sharing
General digital security considerations
- Does the platform allow users to maintain strong passwords (more than 12 character passwords)? Better, does it tell the user that the passwords that they are using are not secure?
- Does the platform use HTTPS throughout its site? HTTPS is an encryption protocol that protects information as it travels through the internet.
Platform-specific considerations
- Will the platform allow users to control who can see their videos?
- Does the platform have a privacy setting for video content?
- Does the platform allow a user to control who can comment on their videos?
- Does the platform allow for downloading or copying of users videos without their consent?
- Does the platform allow the user to delete their videos from the platform? And would this mean that if it was shared or posted elsewhere (through the same platform) that the videos would automatically be deleted as well?
1 See for example:
https://www.theguardian.com/technology/2013/aug/27/facebook-government-user-requests;
https://techcrunch.com/2017/12/18/government-requests-for-facebook-user-data-continue-to-increase-worldwide/; and
https://techcrunch.com/2019/11/13/facebook-says-government-demands-for-user-data-are-at-a-record-high/
2 See https://govtrequests.facebook.com/government-data-requests
Section 4: Safety and podcasts
Safety considerations in podcasting
Introduction
Podcasts is is are usually part of a series of digital audio content that is made available for users to download or stream. Podcasts are episodic – each installment is complete, with a start and an end, that contributes to a larger theme (e.g. issue-themed feature news, a specific topic) or story.
Learning objectives
This section will be about unpacking some safety considerations in podcasting. Specifically, around how to mitigate some potential risks as well as how a storyteller can have more control over their content by choosing the right platform for their needs.
Preparing to podcast safely
The common format of a podcast is the main host having a conversation with a person who has experience and knowledge on a certain topic or theme. But increasingly, podcasting is being used to tell stories.
Storytellers who are considering podcasting as a way to tell their stories will have to consider some things in order to do it more safely. Generally, many podcasters use their real names and only involve others who do the same. Podcasts being all audio provides a sense level of non-identifiability because it is faceless.
However, depending on how sensitive the storyteller´s theme is as a storyteller, they you might want to consider ways in which to control their identifiability as they you podcast. Theirs and the people they you want to involved in it.
It is important for the storyteller to imagine the impact of their podcasts will be on themselves and their guests, and to try to mitigate negative consequences. These negative consequences could be:
- harassment of the storyteller or their guests from people who do not share their opinion
- re-traumatising the interviewee
- exposing the identity survivor of a human rights violation or sexual abuse and causing them harm
- re-traumatising listeners
If the theme of a podcast is too sensitive, for example on issues of equal access to justice or the weaknesses of Sharia legal systems, the storyteller might want to consider having a different format for their podcast. In recent years, some podcast producers have used fictionalised content to engage more serious topics, or to share stories. Instead of using the more standard conversation format, they instead write scripts for audio dramas. These range from short stories (each episode is a short story) to longer fictional stories (each episode is a chapter).
Whether or not the storyteller will use the more standard podcast format, or do a fictional podcast, they should still consider the following questions before they start podcasting:
- What is the podcast about? Are there going to be themes in it that will put the storyteller or the guests at risk?
- Who will be the guests on the podcasts? Are they agreeable to be identifiable? If they prefer to use a pseudonym, you as the one creating the podcast will have to be mindful of not slipping up and using your guest’s real name. If your guest prefers to be anonymous, it is common to still have some kind of reference because it is natural to want to call the person by name. So a generic pseudonym like ¨friend¨, ¨Person A¨ or a generic name in your culturecould help.
- What is already available on the internet about the storyteller? Is there information about the storyteller that can be used to harass them or those close to them? The storyteller would need to do this with people who will be guests in their podcasts as well.
It is also recommended that a storyteller gets a separate email address (not their personal or their work email addresses) for their podcasting use. They can use a free and secure service like https://proton.me or TutaNota for this. This will protect them from possible spamming of their personal accounts as well as help protect their identities on the internet.
Here's an example of a story that can be seen as very controversial, about a lesbian in a straight marriage, podcast produced by Juana Jaafar.
Juana Jaafar. 2016. “On being lesbian in a straight marriage”. JuanaJaafar.net, 21 July. http://www.juanajaafar.net/2016/07/on-being-lesbian-in-a-straight-marriage/
Safety considerations in choosing podcast hosting providers
As with any other forms of digital content that is meant to be shared, where that content is hosted (stored and shared) is an important consideration. There are a lot of podcast host services available. Most of them for a fee. Some are free – with a lot of limitations about length of the podcasts, size of the audio files, and permanence of the files on the host server.
In selecting podcast hosting providers, a storyteller must consider the following:
User control over podcasts
Will they be able to delete, edit, and / or archive episodes?
Some free podcast hosts delete podcasts after a month. If you want to archive them, ensure you have back up, but where and how you store these could have further security issues too.
Is the podcast host able to delete users content?
The storyteller needs to read the End User License Agreement of the podcast hosting provider to know if the service will be able to delete content without the user´s permission. Sometimes services will try to detect copyrighted materials or are against certain topics being promoted, like the human rights of LGBTIQ persons or environmental issues where accusations of wrong-doing may be deemed as defamatory.
Audience engagement and management
Where do the podcast hosting provider automatically feed the podcasts?
Some of them automatically feed the podcast to more mainstream platforms (iTunes, Spotify), which means the podcaster will not have that much control over who gets to listen to their podcasts. This also means the podcasts will likely reach a wider audience. The storyteller needs to consider how much they are able to control who listens to their podcasts.
Will the podcast hosting service allow the podcaster to control the RSS feed of their own podcasts?
An RSS (Rich Site Summary or Real Simple Syndication) feed is a list of updates of new content from websites. The most common use of RSS feeds is in news content. This allows a user to get new content from different news sites using one application (examples of RSS readers, https://fossbytes.com/best-rss-reader-apps/) instead of going to these websites one-by-one for updates. Podcasting generally uses RSS feeds in order for podcasters to automatically update their podcasts on different podcasting applications (i.e., Spotify, Stitcher, iTunes). Most podcasting hosting services automatically generate RSS feeds for podcasts and share them with more popular apps. This is important if the storyteller wants to limit how their podcasts are released. What this means is that the podcast hosting service will not automatically share the podcasts with mainstream platforms but rather allow the podcaster to share it themselves.
General hosting safety
- Does the podcast have site-wide HTTPS?
- Do they allow for strong passwords? 12+ characters
- What do they publish about their users? Do they publish real names of their users? Or usernames? It is safer if the host only shares user names and not actual names of their users publicly and on their sites.
Related links
Fiction Podcasts: https://www.thepodcasthost.com/fiction-podcasts/story-format/
How to Protect Your Privacy While Podcasting: https://theaudacitytopodcast.com/how-to-protect-your-privacy-while-podcasting-tap288/
How to Stay Safe and Secure in Podcasting: https://theaudacitytopodcast.com/how-to-stay-safe-and-secure-in-podcasting-tap289/
Why you need your own privacy polices in podcasting: https://theaudacitytopodcast.com/tap079-why-you-need-your-own-privacy-policies-disclosures-and-releases-for-blogging-or-podcasting/
Producing and editing a story
This is the basics and will be updated and refined in early 2021.
Producing and editing a story
Remember, your story matters! So it is important to be careful and attentive to the practical side of producing and editing your story. Reach out and ask for help from other participants or the facilitators if you feel stuck.
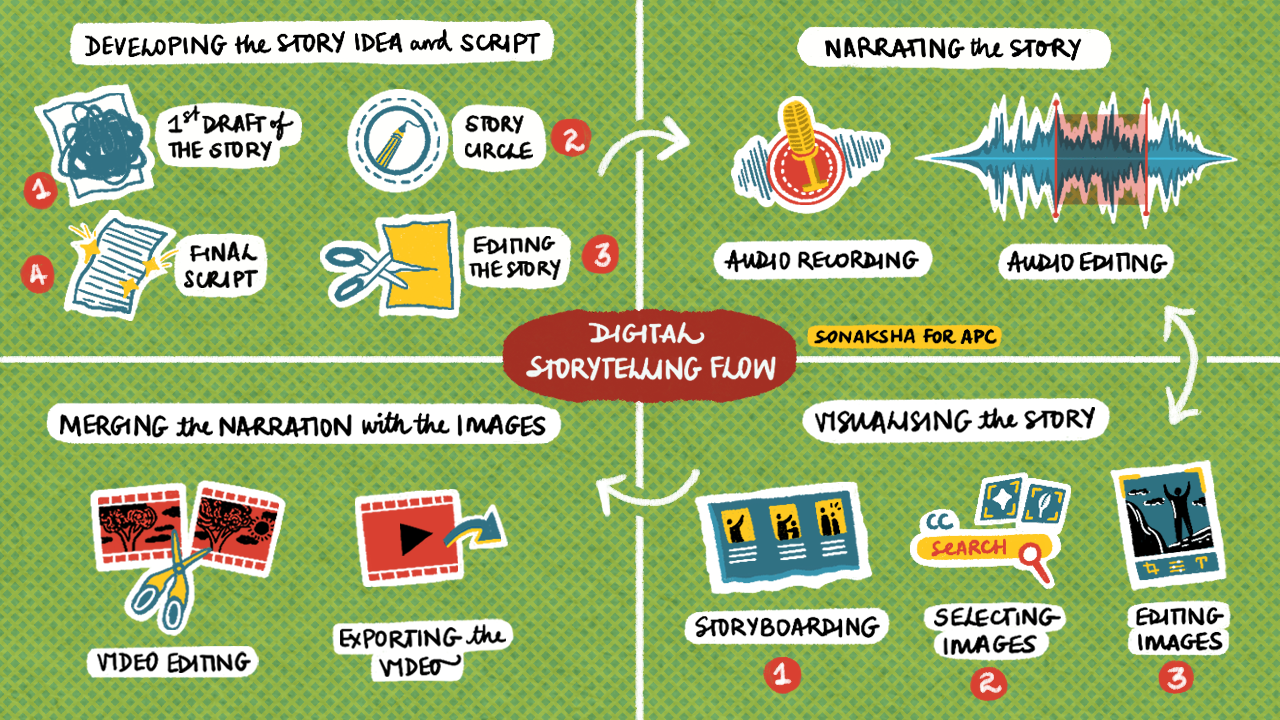
Here are the basic elements of the flow of creating a digital story. You first need to decide what form you want your story to be in. This could be a digital story, a podcast, an Instagram story, a digital collage, an e-zine etc.
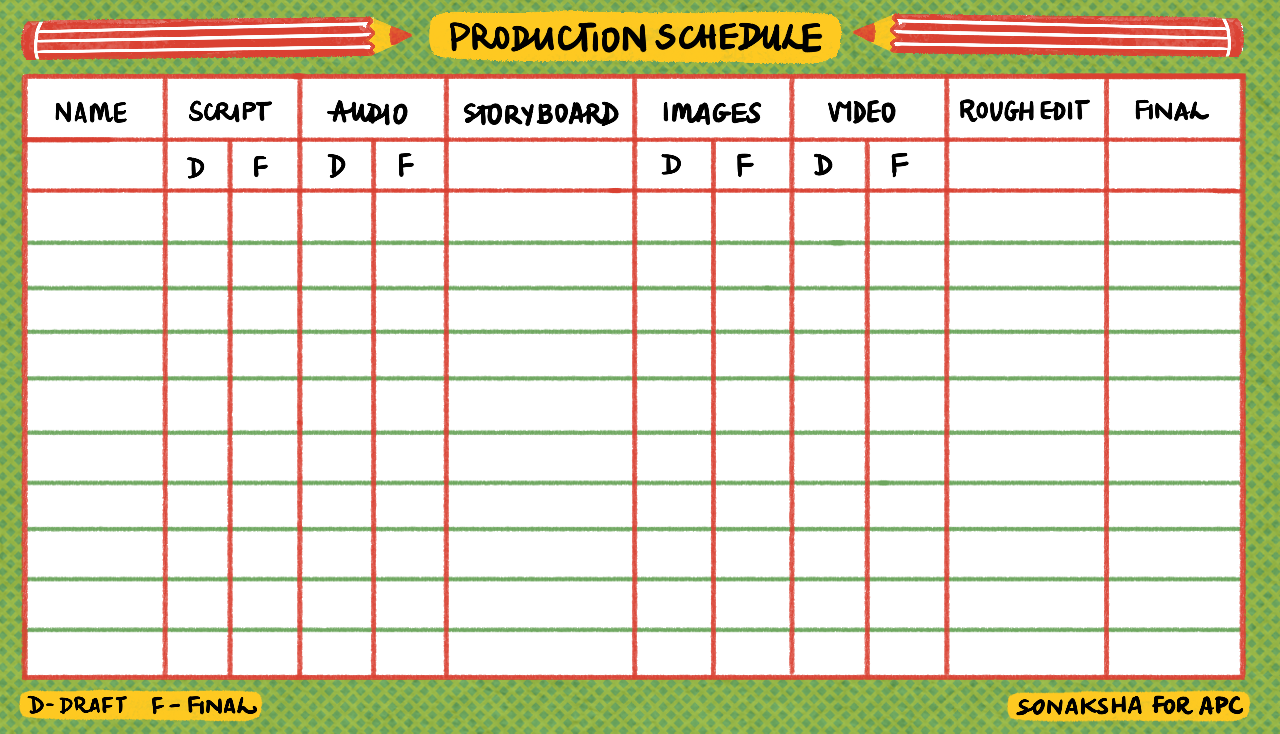
There are many stages of producing and editing a story. For the facilitators to keep track of how participants are doing in the various stages, we recommend that you set up a Production Schedule. This lists names of participants and all the tasks needed to produce a final story. As the participants complete a task, they are reminded to tick on the Production Schedule what they have completed.
Before you start the workshop, it is a good idea to crowdsource the skills that exist amongst the participants. This means that participants can assist each other and make the learning experience an exchange of skills. Perhaps someone is good at drawing, another is confident with recording audio etc. Use this Community resourcing tool.
Stages of producing and editing your story
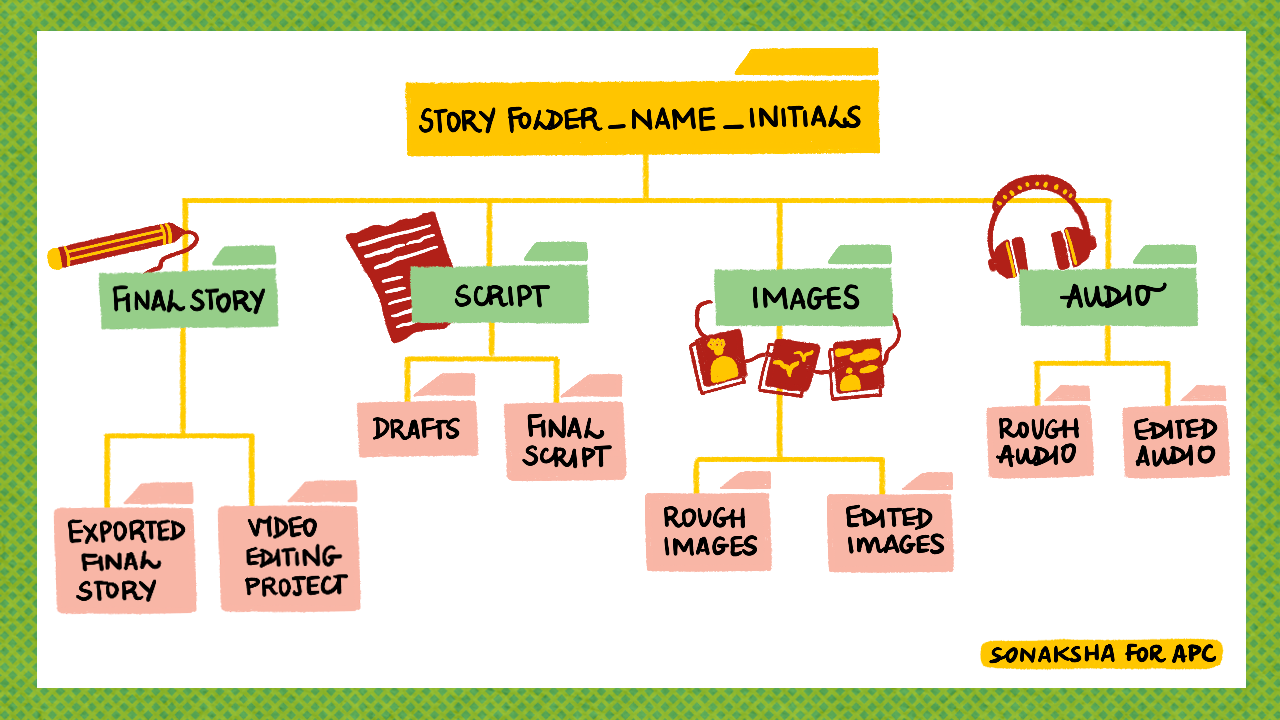
We highly recommend that you get organised before you start your story! Set up a folder on your laptop or mobile phone which has a logic to it that will help you when you are ready to put together the elements of your story. Give it a name such as MyStory and then have sub-folders for the script, the images, the audio and the final story. In each sub-folder, have a draft and a final sub-folder. Your Final Story should have a folder which is called Final Story and Video editing project.
This way you keep all your elements in case you want to re-visit your story and edit and change it.
You need a script, which is your story. We recommend a script of no longer than 500 words. This usually means your story will be about 3-5 minutes long which is a good length. See section on Form of a story for how the development of a script happens. Here you can read some tips and advice on developing your script.
The next step is a Storyboard which will assist you in knowing what visual elements you need for your story. If you are using only audio, this can still assist in breaking down the story into smaller pieces to see what is core, what lines of audio can be repeated etc. For a podcast, it is a good idea to select or draw one image that represents the core of the story and can be used for uploading to the internet.
Here is a storyboarding template to adapt and use.
To record your audio, you can use your mobile phone or any good audio recorder. Make sure that you are in a quiet space and that you won’t have any interruptions. Often it helps to have another participant with you to hold equipment and give you feedback on your recording. If you have your script on a piece of paper, remember to place that on a surface so that you don’t record turning or rusteling paper. Test your voice, test the settings and listen back for any external noises and the level of your voice. It makes a big difference to a story if the voice is clear, that you don’t rush over words and not have background noise.
We suggest that you use Audacity to edit your story. You can download Audacity for free here. https://www.audacityteam.org/ Audacity is free, open source, cross platform audio software. We like Free and Open Source! Read about the importance of Open Source at the Feminist Principles of the internet - https://feministinternet.org/en/principle/open-source
Use these supporting documents to help you with Audacity.
Another free and open source software we recommend to assist you with editing your images is GIMP. You can download it for free here https://www.gimp.org/
Here are some supporting documents to help you with GIMP.
Remember to read the section of this manual on Creative commons licensing, distribution and attribution if you are Creative commons licensing, distribution and attributiongoing to find images off the internet.
Putting your story together
If you have chosen to make a digital story, you will need software to help you put all the elements of your story together. The audio, the images and the transitions. There are quite a few softwares and tools out there to use. You can always search the internet to find one that suits you. We would suggest using for laptops and for mobile phones. But find what suits you.
We’ve liked Shotcut - https://www.shotcut.org/ which is a free, open source, cross-platform video editor. This works well for laptops.
There are many for mobile phones, such as Filmora - https://filmora.wondershare.com/
Enjoy making your story!
Creative commons licensing, distribution and attribution
Understanding how to reuse material
The availability of works under an open license has increased dramatically since the Creative Commons licenses were launched in 2002. As of today, there are around 2 billion works released under a Creative Commons license[1], and many more with other types of licenses (such as the GFDL)[2].
The reason why the Creative Commons licenses became so widespread it’s because they offer considerable flexibility to creators and users. Creative Commons licenses include six licenses and two public domain tools. Creative Commons are standardized tools. Each of the licenses and tools have three layers of legal language, user language, and machine readable code. This is what makes CC licenses such a powerful tool. They have been translated to many languages, so users can understand in their own language what they can and can’t do with a work that is licensed under a CC license.
However, it is not always easy to understand how to use works under a CC license, or how to license your own work. Additionally, CC licenses only cover the aspects of a work that are related to copyright. Any other right, such as personality or privacy rights, are not covered by the CC licenses. This means you need to examine the work you’re planning to incorporate in your storytelling or narrative to decide if you can use it.
To decide if you incorporate a particular work into your narrative, you need to first understand some important aspects of the licenses and your intended use.
Understanding your use
Before deciding where to look for works that you can use, you need to define what is your intended use of those works.
The two main things that you have to consider are:
- Is your use of the works an adaptation or a combination (also called “collection”)?
- Do you plan to give the work a commercial use?
For deciding whether your use is an adaptation or a combination, you have to ask yourself the following questions: Are you planning to remix it into a larger work, or are you planning to use it “as it is”, to illustrate a point or indicate an element? For example, are you planning to use a set of icons in a larger infographic material about the importance of regulating hate speech on social media, or are you planning to remix public domain works to make a collage poster that depicts an abstract concept of gender equality?
This is an important distinction between adaptation and combination. Adaptation is when you take a set of existing works to create a new, distinguishable work. When you adapt a work, it’s hard to distinguish when each of the works start and when they end (i.e., a collage).
Combining works (or making a collection of works) is when you take a set of existing works and combine them or arrange them in a way that still produces a new work, but where each work being combined remains its separate, own work (i.e., the icons in an infographic).
Additionally, you need to consider how you plan to use and license your work afterwards. Are you planning to sell the resulting work or use it for a for-profit purpose? How do you want to license your own work?
Creative Commons offers an extensive review of the licensing considerations that you need to consider in their FAQ section “Combining and adapting CC material”.
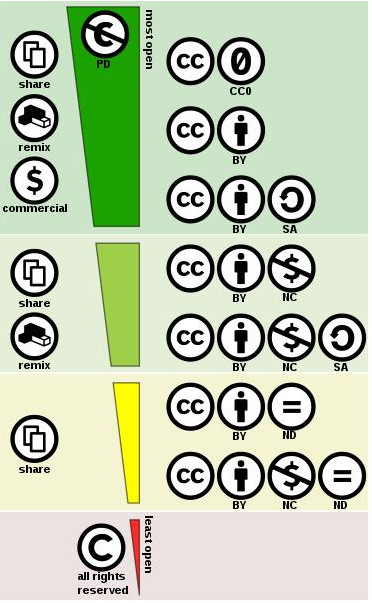
However, it’s easy to feel overwhelmed with all the different charts and considerations on how you’re supposed to incorporate works with the non-commercial, share-alike or non-derivatives clause. The easiest way to avoid all this complexity is to limit your search to materials that are made freely available with little to no restrictions. This means that you will only search for works that are preferably under a CC BY, a CC BY SA or a CC0.
Pro Tip: To avoid complexity, search for materials that you can freely reuse with little to no restrictions. This means searching for materials under the CC BY and CC BY-SA license or the CC0 tool. You can use search filters and specific media repositories that will give you only these results when searching.
If you want to use any work under the remaining licenses (CC BY-NC, CC BY-SA-NC, CC BY-ND, CC BY-NC-ND) you will have to ask yourself:
- Is the resulting work an adaptation or a combination of works?
- Do I want to make a commercial use of the resulting work?
If you want to use a material that has a CC BY-NC-ND or a CC BY-ND, you need to be aware that you can’t make distributions of any adaptations you make to the work. That means that you will only be able to incorporate works under those licenses “as they are”, without any modifications.
This graphic of the “spectrum of CC licenses” shows that the licenses placed in the dark green area of the graphic are the “most free” licenses. The works released under the licenses placed in the dark green area are also the ones that are easier to incorporate in any new work.
“Creative Commons License Spectrum” by Shaddim (CC BY 4.0)
In the next sections we will explore how to search for works that are under the licenses placed in the dark green area. But in a nutshell, different search filters and specific media repositories will give you materials licensed in these ways.
Other considerations when using and reusing CC licensed material
The CC licenses don’t cover other rights different from copyright. Any image, sound, moving image, or other representation may have other legal or ethical rights. Legal rights are rights that are enforceable while ethical considerations might not be legally enforceable, but you need to consider when respectfully using the material. These rights include:
- Trademarks: an openly licensed resource might contain representations of trademarks (for example, a photo that shows the iconic logo of a fast food chain);
- Publicity rights: certain living people depicted in openly licensed photos might be covered by publicity rights (i.e., a photo of a singer or performer);
- Privacy rights: depictions of living people might also be subject to privacy rights.
- Ethical considerations: all the other considerations that emerge but are not coded in law and/or related to copyright law in particular.
These all apply even when the resource might be openly licensed.
Trademarks
As a general principle, it’s a good idea to avoid using depictions or representations of trademarks or their logos. However, you might be able to use works that represent or depict a trademark if you are going to critique the trademark or if you want to illustrate a point (for example, a slide that shows the top 10 companies causing environmental harm in your country could be illustrated with their logos).
You might also want to avoid potential connections between a narrative and a trademark. For example, if you are doing storytelling on the obesity epidemic and its impact in the developing world, you want to avoid including a representation of the iconic logo of a soda company. While there might be a connection between sodas and obesity, you want to avoid being that specific. You can use something less specific (for example, a photo of a line of sodas in an aisle in a supermarket).
Publicity rights
Avoid using photos of famous people, unless the story that you are building is about the person or refers to the person somehow. The protection of publicity rights might not be as strong when related to politicians. Publicity rights vary widely: make sure to know your local laws before representing famous people.
Privacy rights
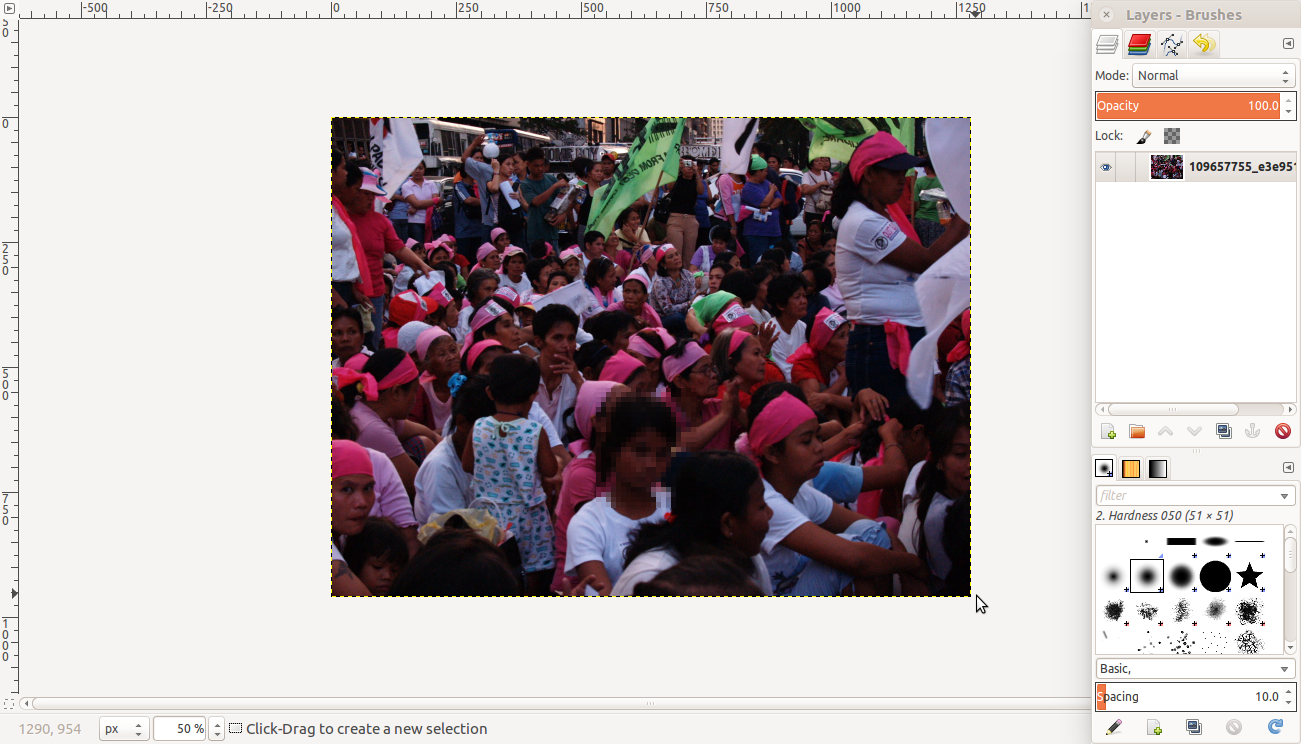
Privacy rights can be complicated legally and should be treated alongside ethical considerations. Some jurisdictions have different considerations for privacy rights. However, in many jurisdictions around the world: if a person is in a public space, then their expectations of privacy should be lower. What does that mean? In short, it means that if, for example, you decide to participate in a manifestation of some type (a public performance, protest, etc), then you should anticipate that others could be taking pictures of you without your consent. Your participation in the public space is, in a way, a form of consent.
This is highly controversial and problematic. As an example, let’s take a look at the story of the Pulitzer prize winning photos of 2015 of the Ferguson protests in the United States, taken by the white photographer Robert Cohen. The photo depicts a black man, Edward Crawford, grabbing a gas canister and throwing it back at the police with an American flag in flames. The black man was later harrased by the police (arguably because of the photos that placed him at the place of the protest) and died under circumstances that still remain unclear. This brings very interesting questions about how protests should be respectfully depicted, including but not limited to how this might put in danger other people's lives.
You need to be extremely careful in which contexts you might reuse depictions of living people. As a general principle, reusing any depiction of living people could be a misuse, in the sense that you are taking a depiction of a person and using it in a context and for a purpose that was not the context or purpose that the person being depicted anticipated. However, there are uses that are more acceptable than others. For these ethical considerations, context is everything.
Ethical considerations
Ethical considerations might or might not be rooted in legal systems. “Ethical considerations” refer mainly to respectfully using representations of people and cultures. Some of these considerations are very heavily related to context, so always bear in mind what your audience might be for your storytelling.
Pro Tip: If you are not sure whether your use or reuse is legal, ethical or respectful, then search for another resource that makes you feel more confident.
As a general principle, use the following criteria to decide whether the your intended use is appropriate:
- Did the person give consent to be depicted in the way in which she or he is being depicted? If you suspect that the media, photo or representation was taken without the consent of the person, then avoid using it in your work.
- Is the representation respectful of the situation in which the person might be situated in? For example, if you want to depict “poverty in Latin America”, avoid using images or representations that might bring stigma over the people or situation being depicted. Avoid also using tokenizing representations.
Does the representation of the person or situation put the person’s life at risk in any way?
Avoid using photos that might put someone’s life or safety at risk, even if the license allows for free reuse. Consider questions like: does the photo show someone doing something illegal? Does the photo show someone easily identifiable while protesting power? If the photos you find are in a community with ethical norms look for a way to report it: for example, on Wikimedia Commons consider also asking for deletion .
Does the use that you intend to do of the work show the person or situation being depicted in a positive, affirmative action?
There are manifestations that take place as part of affirmative actions. For example, Pride Parades in contexts where LGBTIQ+ rights are fully granted3 are a good example of such affirmative actions. This is an example of a photo taken at a Pride Parade in Berlin in 2015, which was later re-used in a set of postcards to ask for the implementation of the Marrakesh Treaty for people with print disabilities. These are examples of affirmative actions.
Does the person that took the photo belong to the cultural or geographical context?
An important aspect to consider here is also who might have produced the media you intend to use. While sometimes it’s impossible to know this for sure, there are different levels of confidence. Writer Sasha Alyson in his blog “Karma colonialism” points out how different aid agencies normally don’t hire local talent for their photo-shoots, converting these depictions into another form of colonialism and othering. There are other resources that are openly licensed that have been produced by local people, for example, the contests organized by Wiki Loves Africa.
Does your intended use include any identifiable traits of the person?
Depending on what story you are telling, you might want to avoid using works that show identifiable traits of the person. For example, if you are writing a report about working environments in Indonesia, you can use openly licensed photos, but you might want to avoid showing people whose face or traits are recognizable and that were taken in a different context from the project. Readers of your story might interpret those people as “the people impacted by the program” rather than as anonymous people. Instead, you might want to consider showing more abstract photos of working environments, or only select certain portions of the body (for example, hands on a computer).
Does the person belong to a minority group?
There are certain groups that have been historically depicted without their consent and with a colonialist perspective. That’s frequently the case of indigenous people, artifacts and customs. Some of these representations are part of archival materials stewarded by cultural heritage institutions that make them available because copyright expired. That doesn’t mean that these representations are less problematic. For example, many libraries and archives in North America have published 19th century photos of Native American traditions not meant to be shared. Reusing these images extends this injury. Ask yourself whether the representation is appropriate.
Understand how your reuse fits into your narrative
Once you have finished putting together your storytelling or narrative, you need to make sure that the overall story does not accidentally misrepresent the people or topic in a poor way. For example, you might have selected certain types of representations that build bias into your story.
When unsure, search for other resources
If you are confident your use is ethical, then search for another resource that makes you feel more confident. You might spend a bit more time on the search, but it’s better to feel safe about your reuse.
As a final consideration, also avoid works that depict scripts or languages that you don’t understand. If you don’t know the language, you might be using offensive or out of context terms without realizing. An exception to this rule is when these scripts are being displayed in public and properly contextualized, for example, the “Monument to the Reader” in Yerevan, Armenia.
What happens if I use a material offered under a CC license and the author decides to remove or change the CC license?
CC licenses are irrevocable. This means that if someone decides to change their mind about the license they are using, you can still use it under the terms that it was offered to you. However, sometimes this could potentially make someone wary of using a work under a CC license, because how might you prove that the material was offered to you under a CC license?
A good idea is that whenever you are using and reusing material offered to you under a CC license, you do one (or both) of the following:
- Upload the photo to Wikimedia Commons: using the Upload Wizard, you can add the source where you find the material, alongside with the tutorial. The Upload Wizard offers a step by step guide.
Save the link on the Wayback Machine: the Wayback Machine is an archiving service of website pages offered by Internet Archive. You can go to the Wayback Machine website and use the “Save page Now” function:
If you paste the URL in that box, it will create a “snapshot” of the page, with a unique URL. You could potentially also use that URL as an alternative source when using the “TASL approach” (more on that in the next section).
Lastly, an important point is that you might wish to respect the desires of the author that decides to change the license to their content, avoiding reusing that content in the future, even when you might have the snapshot of the website.
1 Creative Commons annual report (2019), available here: https://creativecommons.org/2020/11/05/creative-commons-2019-annual-report/
2 This tutorial will only work with CC-licensed material to avoid introducing more complexity.
3 Avoid using photos of LGBTIQ+ parades or manifestations in contexts where their rights are at risk or their lives might be in danger.
Understanding how to attribute
Using the TASL approach
Attribution is not only a legal requirement, it’s also good practice. For both copyrighted and openly licensed materials, you should always try to follow good practices on attribution. Even if the work is openly licensed, there are numerous benefits to attribution: for example, good attribution helps other users find the work, and use it themselves.
All the six CC licenses require attribution. The way in which you attribute might vary, but the rule is that your attribution has to make clear that the use that you are making of the material does not constitute an endorsement of your use or reuse by the original author.
The way in which you provide attribution is connected to your planned end work and the possibilities that the medium of that work allow. A good practice for attribution is to always include the “TASL” information, an acronym that stands for “Title, Author, Source, License”:
- Title: the title of the work1
- Author: the people that created the work
- Source: a link to the source where you obtained the material
- License: the license which the work is being distributed under.
Creative Commons has developed an extensive FAQ on all the facts that you need to know on “how to properly provide attribution”. They also have a simple resource page on “How to give attribution” and a more extensive wiki page on “Good practices for attribution”. When in doubt, make sure to check those resources.
Pro Tip: Make a copy of the website that is offering you the CC licensed content using the Wayback Machine “Save page” function or by uploading the content to Wikimedia Commons.
Additionally, platforms that have built-in support for CC licenses (such as Flickr or Wikimedia Commons) tend to make the process of attribution slightly easier, by allowing you to copy the relevant information that you need to build the TASL information.
The person releasing a work can’t require the attribution to be located in a specific place. This is very important when doing storytelling, because you might combine a very large number of resources into a single new work, and providing all the attribution for those sources might be challenging. For example, if you are doing an infographic using different icons and images, you can create a page called “Credits for resources for my beautiful infographic”, create all the proper attribution statements following the TASL approach, and then provide a link to that page in the infographic.
Some websites tend to add extra information on how you are supposed to attribute or how you are supposed to use the work. For example, such is the case of The Noun Project, that adds the two following suggestions when you download a SVG or PNG icon licensed as CC BY from their collection.
The text in the picture reads:
“You must add attribution:
- Use the embedded attribution if the icon is larger than 100px”.
- Copy the attribution text below and include it in a bibliography or image caption, or on a physical item or its tag”.
In situations using CC license, these are suggestions rather than requirements. In its FAQ CC clearly outlines that an author can’t require the exact placement of the attribution credit, but also clarifies that any additional restriction added to a CC license makes it no longer a CC license.
In a nutshell, always follow the TASL approach and make sure that the credit lines are clear wherever you place them. If for whatever reason you forget to attribute a work, under version 4.0 of the licenses (and note that only version 4.0 allows for this) you have a 30 day window period to fix the mistake after being discovered (see relevant FAQ here).
Attributing works in the public domain
Works might be in the public domain typically for any of the following reasons:1
- because copyright has expired;
- because it was never entitled to copyright to begin with;
- because the rights over the work have been waived.2
Copyright only lasts for a certain amount of years (typically, 70 years after the death of the author, although some countries only require 50 years post mortem and some other countries require more). When a work is in the public domain, typically that means that it’s free to use. However, some jurisdictions have a different approach, particularly those that strongly protect moral rights, requiring that the user of such a work still attributes the original author.
Since depending on the jurisdiction in which you are based the situation might vary, you might need to attribute the work even when the work is in the public domain. Additionally, a good idea is to follow what is suggested in the Public Domain Usage Guidelines prepared by Europeana, the aggregator of cultural heritage in Europe.
In certain cases, authors might choose to waive all their rights, and make it optional to attribute them or not. That’s the case of the authors that choose the CC0 tool (“Creative Commons Zero”), a public domain dedication that puts the work in the public domain once the author has decided to apply the tool. In this case, you can decide whether you attribute the work or not.
A note about license versions
If you are more or less familiar with the CC licenses, you have probably seen already that sometimes a number appears right after the terms of the license, for example, “CC BY-SA 4.0”. That number is the version of the license that the person is using.
When the CC Licenses were launched, there was a significant amount of work put into making them “portable”. This meant that the licenses were not only translated into a different language, but also they were made to work within each national jurisdiction that the license was being “ported” to. One of the significant changes (among others) brought by version 4.0 was that licenses are no longer “ported”. This is because the licenses are now internationalized, and they don’t require anymore to be ported. They are only translated.
However, an important thing to note is that sometimes the different license versions have different requirements when it comes to attribution, and is normally a good idea to try to use the latest versions (particularly version 3.0 and 4.0). Unfortunately, there are some bad actors as described in this article: “Automated image recognition: How using 'free' photos on the internet can lead to lawsuits and fines” that have abused the attribution requirements using the different versions. If you are curious to understand more about what changed from version to version, you can always check this chart made by Creative Commons.
In short, use the latest versions whenever possible, and never forget to follow the TASTASLL approach when attributing a work.
1 Note that with version 4.0 of the CC licenses title is no longer a requirement, but is always good practice to still include it.
2 Additionally in the US works might be in the public domain due to failure of registration prior to the granting of automatic protection, but that situation is very specific and won’t be explored here.
3 This is the case not only for authors using CC0 but also for certain types of work, such as works made by US officials in the context of their employment. However, that rule only applies under US jurisdiction, so make your own risk assessment to whether use or not any of those resources.
Searching openly licensed resources
The following guide uses the following keywords to refer to websites, repositories and content platforms:
- Multimedia: this means that you can find any type of media (images, sounds, video, documents and many more);
- Vector graphics: high quality graphics that don’t diminish their quality in comparison with raster images, mainly composed by icons and drawings;
- Images: websites that only offer images;
- Sounds: websites that only offer sounds and are better suited for searching this type of content.
General tips for your search
Search for the CC license or tool
There are many, many, many repositories out there that have openly licensed images. Some of them don’t use standard CC licenses, but rather use their Terms of Service (ToS). These terms and conditions are similar to what CC licenses offer. However, they are not compatible with the CC licenses, so you need to evaluate carefully whether to incorporate them in your work or not.
Unsplash or Pixabay have such custom Terms of Service or licenses. The license of Unsplash is similar to a CC0 waiver, but it has specific conditions that make it substantially different from a CC0. These differences can cause confusion. For example of a confusing effect, see Unsplash’s answer to: “Can you help me take down a photo on a third-party site?”. Using sites that offer CC licensed content is easier. When in doubt if the website is offering the material under a CC license or their own custom terms, check their Terms of Use or Conditions.
Additionally, you might also want to use resources that are licensed under the latest version of the CC licenses (version 4.0).
Use search filters
To get the most out of all the resources that are available under open licenses, you need to make use of the extensive search filters that repositories of content (images, videos, sound) offer. In some websites it’s easier than in others, but in general most of these repositories offer some type of search filter. In some repositories, like Wikimedia Commons, all the content you find will allow for re-use, so you will never find Non Commercial or Non Derivatives licensed content. But if you’re searching on a website like Flickr, using the search filter is crucial to only search for content you can reuse.
Pro Tip: Build your personal list of websites for finding openly licensed content. Different open-licensed content sites have different strengths and weaknesses. Focus on the ones best for your content needs.
Check the quality of the resources
Depending on which repository you are searching for content, the quality of the resources might be fit for some purposes but not for others (for example, they might be adequate for posting on the web but not for printing). Normally, most repositories will allow you to filter also for quality.
Searching in languages other than English
Some multimedia platforms and repositories support multilinguality, while others don’t. Of course, you will find out soon enough the moment you try to do a search on a language other than English and don’t get any results. That’s when no multilinguality is supported. However, in some cases what can happen is that multilinguality is supported only to a certain extent. For example, look how different the results are on Flickr if you search for “mujer”, “wanita” and “woman” (the search doesn’t have any filters by license). The same happens in most repositories, so if you don’t find what you’re searching for, try using keywords in another language, if you happen to speak more than one language.
Multimedia
Wikimedia Commons
Wikimedia Commons is the multimedia repository of the Wikimedia Foundation. It’s also the central place that stores most of the multimedia used in Wikipedia articles.
Although many people turn to Wikimedia Commons to search for pictures and other images or graphics, there is also a vast set of other important resources, such as sound, documents and video available on Wikimedia Commons.
Wikimedia Commons can be a hard repository to navigate if you use the default search box. But there are many other ways in which you can actually get the most out of Wikimedia Commons. In this whole section, the explanations will be used to find photos, but most of what is being explained can be applied to search for other multimedia content. These are general search step-by-step guides to get the most out of Wikimedia Commons.
Also, bear in mind that different search functionalities in Wikimedia Commons offer different results.
Caption: The “Search box” is the box that appears on top of the main page.
Search with Special:MediaSearch
Special:MediaSearch is an experimental search tool with improved algorithms for finding content, that is currently being tested with the Commons community. Even as a Beta service, it produces very high quality results when searching Commons:
- Go to http://commons.wikimedia.org
- On the search box on Wikimedia Commons, type: “Special:MediaSearch”.
- Special:MediaSearch will retrieve better results than a regular search in the search box.
- Special:MediaSearch is singular/plural sensitive. If you type “readers” instead of “reader”, you might receive slightly different results.
- In Special:MediaSearch you can browse through different type of media content (images, audio, video, categories, and also other file formats, such as PDF or DJVU).
- In Special:MediaSearch you can select the size for images (small, medium, large).
- In Special:MediaSearch, for all media, you can search for specific file formats that correspond to that media (for example, in images, you can search for JPG, XFC, etc), and also sort by relevance, by choosing from the dropdown menu.
Caption: this GIF illustrates the different options available on Special:MediaSearch.
Caption: this illustrates how the dropdown works.
By sorting and filtering, you make sure that you are getting something that gets you closer to what you want. For example, you avoid getting back search results that give you small images that then you can’t reuse outside a website.
Discover through categories
Categories by type of media
Another good way to discover content in Wikimedia Commons is through the “Categories”. Categories are the way in which originally most of the information in Wikimedia platforms (including Wikipedia and Commons, but not limited to them) was hierarchically organized. Categories have then a main category and then subcategories.
When you enter to the main page, you will see the following resources being listed:
Caption: In the main page, you will see listed “Images”, “Sounds”, “Video”.
These are categories. In the Category:Images you will find subcategories organized around different criteria: technical aspects, certain types of depictions, among others. You can browse those subcategories according to your needs, but highly recommended are the subcategories Category:Featured pictures, Category:Quality images, Category:Valued images. These are images that have been featured at any given point on Wikimedia Commons due to their technical quality and their relevance to illustrate a topic.
A similar category exists for Category:Sounds and Category:Videos. The Category:Videos also has its subcategory Category:Featured media.
Categories by topics
Caption: front page of the article “Scientist”.
If you click on the photo, it will take you to the Media Viewer of Wikimedia Commons. But if you look into the right bottom corner, you will find a button that allows you to click on more details:
Caption: if you click on the right bottom corner, you can find more details of the file.
That will take you directly to the file stored in Wikimedia Commons. And, in there, if you go all towards the bottom of the page, you will find the Categories that the photo belongs to:
Caption: categories that the photo belongs to.
In this case, the photo belongs to Category:Men with microscopes. But you’re interested in women scientists. Fortunately, you can search through categories using the search box at the top of the page.
Caption: The “Search box” is the box that appears on top of the main page.
There, you can actually type and search for specific categories. So in this case, you would modify your category to be Category:Women with microscopes (and you will be redirected to “Females with microscopes”!). In short, whenever you like a photo on Wikipedia but you are not sure how to find similar or related photos, searching through categories is a good option.
Contests and campaign drives
The Wikimedia communities also organize photo contests and campaign drives to incorporate content to Wikimedia Commons. These campaigns and contest drives tend to be focused on incorporating specific types of high-quality content into the platform, for example, to highlight the diversity of a continent, of a range of cultural practices, or even of buildings. They are also normally called “Wiki Loves…” and you can find all the contests that have been happening in the page “Wiki Loves Contests”.
These contests and campaign drives have their own set of categories. Some of these very popular contests that have been running for a while are the following:
- Wiki Loves Monuments: a contest to highlight historical buildings and museums.
- Wiki Loves Africa: a contest that highlights the diversity and wealth of the African continent.
- Wiki Loves Folklore: a contest to celebrate cultures across the world.
- VisibleWikiWomen: a campaign drive to incorporate photos of women to illustrate their Wikipedia article.
You have to scroll down to the bottom of the page to find the partner category to which they belong and navigate through all the different subcategories.
How to attribute authors using the “Media Viewer” in Wikimedia Commons
Building the TASL attribution with Wikimedia files actually takes some work. Remember you have to include:
Preferably, in the title you would also include the link to the source. But there is also a simpler way to do this. However, be careful because this step doesn’t always work as expected, so you want to make sure that it is providing all the information you need to build the TASL attribution.
Suppose you entered into the file page through a search. In that page, you will find basic information and description of the file that will allow you to build your TASL attribution from scratch. But if you click in the button that says “Open in Media Viewer”, it will take you again to the Media Viewer.
Once in the Media Viewer, you can use the arrow right on top of the button “More details”. That will display different download options, but it will also display a message that “You can attribute the author” (or alternatively, “You need to attribute the author”, if the work is not in the public domain).
If you click on “Show me how”, it will give you these options: “Plain” and “HTML”. And then you just on the copy button.
Cultural heritage institutions
Another source of great quality content are cultural heritage institutions. There are many benefits to using content made available by cultural heritage institutions.
- Quality: the content that cultural heritage institutions provide tends to be of very high quality, particularly when it comes to reproductions of artworks and archival material.
- Reliability: cultural heritage institutions have workflows and processes in place for doing proper copyright clearance. This means that, when possible, they only make available content that they know for sure is free of all copyrights, or they indicate otherwise if the content is not freely available.
- Cultural relevance: many cultural heritage institutions provide content that is relevant for the region, jurisdiction or country where they are based at. While this doesn’t mean that their content is not biased in some way, they tend to provide more culturally relevant content.
Cultural heritage institutions take different approaches to how they provide content. Some offer their content through their website, through an aggregator 1, and on third-party platforms like Wikimedia Commons. But others only choose to offer their content on their website; others will only use aggregators; and others will only use third-party platforms like Wikimedia Commons or Flickr Commons. Approaches will vary, as well as in some cases their licensing practices.
Caveat: The reader might find this section biased towards North American, European or otherwise Western cultural heritage institutions. Collecting practices of cultural heritage institutions are heavily tinted by colonialist practices. Some of these institutions have “world class collections” by virtue of colonization and other similar practices. Their wealth of resources and knowledge has allowed them to enter speedily into the digital era, while the rest of the world is still unable to participate in a foot of equity. When possible, cultural heritage institutions from other parts of the world are signaled, but the copyright status of the resources being offered by these institutions is way less clear and reliable than the ones being highlighted.
Cultural heritage institutions worldwide
Knowing which institutions have decided to release their digital reproductions of work around the world can be very challenging. Luckily, the Collections Manager of Europeana, Douglas McCarthy, and Dr. Andrea Wallace, Lecturer in Law at University of Exeter, have been maintaining a spreadsheet on “Survey of GLAM Open Access Policy and Practice” (GLAM means “Galleries, Libraries, Archives and Museums''). While the goal of the survey is to track policies, it also provides useful links that allow to discover the media repositories of these institutions.
Caption: this is a screenshot of the survey.
At the time of this writing (November 2020), “Column R” offers the data “OPEN DATA SOURCE 1”. That’s the link where most of those media files can be accessed. Using the sorting functionalities of the Google spreadsheet, anyone can search, for example, all the cultural heritage institutions from COUNTRY (column A) that have as OPEN DATA SOURCE 1 (column R) “flickr.com”.
Importantly enough, this survey only tracks institutions that make their digital reproductions available under CC BY, CC BY-SA, Public Domain Mark, CC0 or No Known Copyright (a label by the RightsStatements consortium). Currently “Column K” offers the data “LICENCE/RIGHTS STATEMENT FOR DIGITAL SURROGATES OF PUBLIC DOMAIN OBJECTS”. In case of doubts on the scope of the policies being captured in the survey, you can read Douglas McCarthy summary of the survey in “Uncovering the global picture of Open GLAM”.
This survey is not a repository. Is only pointing to the repositories of institutions (currently in Column R). However, it tends to be a very good discovery tool if you want to understand where you can find the resources being made available by some of these cultural heritage institutions.
Aggregator: Europeana
Europeana is the aggregator of all the cultural heritage institutions from Europe. Europeana collects material with a “Publishing framework” that ranks institutions that openly license their content better than the ones that don’t, so whenever you are making a search, you are likely to get first the multimedia content that you can freely reuse.
However, this means that not all content you find in Europeana can be re-used. For that reason, Europeana has put together a set of search filters that allow you to search only for material that you can reuse. They explain more on their policies in this FAQ about Reusability. This is a very short FAQ that you can keep handy whenever you have doubts about reuse conditions.
Using search filters on Europeana
Europeana also holds different types of media, from images to drawings to videos and sounds, and much more. For that, they offer different search filters.
- Go to http://europeana.eu
- On the top right corner, you will find the magnifying glass that symbolizes the search function.
- Type your keywords.
- That will give you the first search results. Then you can apply the different search filters using the dropdown menus:
- Collection
- Type of media
- Can I use this?
- Providing country
- More filters
Caption: this GIF shows how to apply search filters on Europeana.
Caption: Using the search filters on Europeana.
How to attribute easily using Europeana
Once you have selected a resource that you like, you will find lots of relevant information in the resource.
Take a look at this picture from the Wellcome Collection of a “Mouse health check”, taken by Caroline Gunn.
After the picture, you will find:
- the information about the license;
- download & share buttons;
- a tab that says “Good to know” with the very basic information and then “All metadata”, that provides you more details about the photo you are looking at.
With the information that the “All metadata” tab provides, you could already put together your TASL attribution. “Mouse health check by Caroline Gunn is under a CC BY 4.0”.
However, there is even an easier way to do that. In the line of “Providing institution”, you can see that it says “Wellcome collection” and then has an arrow to indicate that if you click there, it will take you to an external site, different from Europeana. This is the source of that image. If you click there, it will take you to the page where Wellcome Collection is providing the original file. And if you expand the “Can I use this?” button, at the end it will automatically provide you the credit line:
Caption: Wellcome (original source) provides the credit line.
The only thing that you will need to add is the link to the original file in the Wellcome Collection website. Additionally, it is also good practice that you credit the cultural heritage institution that is providing the resource.
Bear in mind that not all the providing institutions will have this readily available, but most of them will. If you can’t find this credit line easily in the source file, you can still put together your TASL information by checking on the “All the metadata” tab.
At the bottom of the main page of Europeana, you will find that there is some featured content.
In there, featured content is organized in Features, Exhibitions, Blog and Galleries. This is curated content selected by staff members at Europeana. You can’t filter your search in this featured content, so you need to go to any individual file that you might like in order to check that the content is licensed in a way that you can reuse.
Aggregator: DPLA
The Digital Public Library of America is an aggregator of US cultural heritage organizations. It has over 40 million items to browse, although not all of them are re-usable. DPLA currently does not have a search filter option that allows you to filter by type of license, which means that you need to click manually on each digital object to find out whether you can re-use it or not.
On the bright side, it does have some features that allow you to browse by topic, by partner institution, or discover content through their exhibitions curated collections. Their advanced search options do offer some interesting search filters to narrow down the search. You only need to click on the “plus” sign to expand the options that the search tool offers you:
Caption: These are the options that the advanced search filter offers visitors to narrow down results.
Again, be very careful because not all the digital objects at DPLA are reusable. Search for the right status of the objects in their individual entry to find out if you can reuse them or not.
Other aggregators & featured cultural heritage institutions
Europeana and DPLA were probably the first aggregators to see the light, but there are many others, since aggregators offer a wide range of benefits to both users and cultural heritage institutions.
It would take a significant amount of time to review all the search functionalities that every aggregator offers. However, we do want to point out to some other aggregators that you might want to dig into:
- Trove brings together a range of digital content coming from libraries, archives and museums of Australia.
- Digital New Zealand offers over 30 million items from more than 300 hundred institutions of New Zealand, offering not only content from cultural heritage institutions but also content coming from government departments, the media, community groups, and others.
- Mexicana is the aggregator of cultural heritage institutions from Mexico, offering a variety of digital collections and historical documents from the country.
- National Digital Library of India allows search through over 50 million resources coming from different knowledge communities in India.
- Tainacan is actually a software platform by the IBRAM (Brazilian Institute of Museums), but several institutions listed under the use cases page are offering their content online.
Caveat: some of these aggregators offer some openly licensed content, so you need to make sure that you are following the copyright information in the description of the item or abiding by the terms of use of the website. In case of doubt about the copyright status of the objects, avoid using them.
Additionally, there are some cultural heritage institutions that need to be highlighted. These already appear in the “Survey of Open Access Policy and Practice” by Douglas McCarthy and Dr. Andrea Wallace mentioned above, but they deserve a special mention as places to search for multimedia content since they offer very high-quality and reusable multimedia content.
- The Open Access Initiative at the Smithsonian Institution offers +2.8 million items freely accessible and in most cases reusable. Make sure you check the rights field to understand whether you can reuse the digital reproductions or not.
- The Collections online search interface by the Auckland War Memorial Museum from New Zealand has an impressive amount of digital items in high quality content. In this case, be aware that some of the content might also not be reusable in respect of traditional cultural expressions by the Indigenous people from the Pacific area.
- Te Papa is also an institution from New Zealand that offers an amazing set of content.
- Qatar Digital Library covers modern history and culture of the Gulf and wider Arab region.
- The Rijksmuseum is a cultural heritage organization from the Netherlands and one of the first ones to adopt open licenses. They have a lot of content, from artworks to other types of works and content.
- The National Library of Spain changed their licensing policy this year, offering a lot of high quality content, including manuscripts, as public domain.
- The Nationalmuseum of Sweden has lots of interesting content and friendly search interfaces.
Other good cultural heritage institutions you could look for content are The Metropolitan Museum of Art & the Cleveland Museum of Art.
Internet Archive
Internet Archive is a project that offers multiple services. To begin with, as it has been mentioned here already, Internet Archive is responsible for the Wayback Machine, which functions as an archive for the web. It has also partnered with several heritage institutions around the world to digitize their public domain books and other content, offering over 20 million books and texts. It also has video, audio, TV, software, and much more. If you click in each individual icon at their front page, you can enter into each category directly.
Internet Archive has content from very different sources, from cultural heritage organizations to community people that are interested in sharing their multimedia content with the world. Internet Archive also allows for material with any type of license, even including some content that might have an “all rights reserved” statement.
Internet Archive is massive. Make use of their search filters as much as you can, because they will retrieve more useful results than if you just make a very general search. Particularly important is to browse the collections in each category. For example, if you are searching for video, and you want some interesting beginning of the 20th century videos, then you will need to check the collection of the Prelinger archives. Internet Archive has content that no one else has, but sometimes you need to be patient and be willing to browse through their content.
Finding “rights” information in Internet Archive
The search interface doesn’t have any options to filter by license, so it’s up to the user to figure out where the license is located.
In this example file, “The Road to Apollo”, the description of the file has a field “Rights” that states that the file is public domain.
In other cases, such as in this example of The Voynich Manuscript, the information appears on top of the file description:
Sometimes, like in this photo, example from The Met Museum, the field “Rights” will take you to an external URL to read the Terms & Conditions of the website where the photo is taken from.
And in some other cases you might not find any “Rights” field being displayed at all! In those cases, avoid using the files unless you are able to perform your own risk assessment.
Flickr
Flickr is a very popular website to upload all types of images and videos. Flickr was also an early adopter of CC licenses, which means that there is a wealth of content on Flickr that is openly licensed. Flickr offers the full range of CC licenses and tools (the six licenses and the two public domain tools). By using the search filters, you can pick from content that you can freely reuse. If you click on the three dotted lines on “Advanced”, Flickr will also offer you other options, like orientation, minimum size, date, and type of content. This is for example a search for “cucumber videos of medium size that allow for commercial use and modifications”. This narrowed down the results, retrieving this time-lapse video of cucumber seedlings that could be uploaded to Wikimedia Commons and used in the cucumber article, for example.
To build the attribution information, you can click on the “all sizes” button (for example in this image):
That will take you to the following page, where you can extract some of the information to build the attribution statement with the TASL approach:
Then you will need to add the title and provide the source.
Flickr Commons
Flickr Commons is the service that Flickr provides to cultural heritage institutions to upload their multimedia content. Often, content that has been uploaded to Flickr Commons is openly licensed or has a Public Domain Mark.
Other government or public institutions
More databases governments are starting to realize the benefits of openly licensing their content. They apply open licenses to databases, government websites, and even to press releases that normally include high quality photos and other types of multimedia content.
Often, Wikimedia volunteers upload these photos to Wikimedia Commons, meaning that they will likely be found there. However, since governments and state institutions are quite complex, it is hard to tell whether all the material that you might be able to find is on platforms such as Commons. A good idea is to check whether your national or local government does such releases. It is also a good idea to save the page that you are obtaining the content from with the Wayback Machine. Go back to “What happens if I use a material offered under a CC license and the author decides to remove or change the CC license?” if you have doubts on how to do that.
Vector graphics: The Noun Project
The Noun Project is a very popular tool among graphic designers, both professionals and amateurs. Their service offers over 3 million vector graphics that are under either a CC BY 3.0 license (attribution required) or a CC0 public domain waiver (optional attribution). This website is now also offering photos. They are offering them under very different CC licenses, some of them including the Non Commercial and Non Derivative elements. Make sure to check which license the photos are under.
Their search interface is also quite simple, allowing search through very random keywords. The only downside of their search interface is that it is very monolingual, so it really only allows keywords in English. Another interesting feature is that the service has different “collections” of icons that might be related to a topic. For example, if you search for the keyword “work” you will find that the search results page offers several icons. But also in the top page, it will offer icons, collections and now photos.
“Collections” put together a set of icons that are related with a topic. In this case, the “work” collections offer related icons to the “work” concept. This is useful if you know that you need more than one icon to a topic that has several different concepts related to it, and you want to keep the same style of icons.
Additionally, the Noun Project is more and more committed to diversity and being a more global community, so they are now putting out more icons that bring new representations of diverse people. Check out their very interesting collection “Redefining women”
A last note to make on the use of icons from the Noun Project. If you try to download any given icon, the Noun Project will give you the “Pro Download” option (a paid one) and the “Basic download”, as it appears in this image:
The “Pro Download” says that it gives you a vector that you can “Fully customize icon color, rotation and background”. But if you click on the “Basic Download”, it will offer you two file formats: PNG and SVG. The terms of the CC BY license (or if it’s in the Public Domain) allow you to modify the vector. This means that if you want an icon in red or blue, you can still download the SVG, open it in your favourite vector software (for example, Inkscape or the SVG editor free webservice provided by Public Domain Vectors) and modify the icon as you see fit there. Don’t forget to attribute the author, as seen in the TASL approach section.
Vector graphics: Public Domain Vectors
Public Domain Vectors is another website that offers over 60,000 vector graphics of different types of drawings. This website offers all their materials under a CC0 waiver, meaning that attribution is welcome but optional. This means that unlike other websites, you don’t need to use any search filters for licensing. The website does offer useful search filters.
You can filter by file format, by downloads or date, and by number of vectors that you want to have retrieved in each search:
Caption: between the search bar and the navigation bar, you have options to filter your search according to your needs.
Additionally, you can do a search on any given topic, for example, “fist” and select one image you like, like “Vector illustration of freedom movement hand with pencil”. The image will give you several details on the right, including the category to which it belongs (allowing you to navigate through similar, related categories), and other details such as the source; in the “Specs” you will find the file size, the date in which it was uploaded, and the number of downloads. At the bottom of the page you also have “Tags” and “Related searches” that could lead you to something in a similar line, if this doesn’t do the job you need.
Images: Other websites
There are lots of websites that offer images either freely licensed or in the public domain. Every now and then you will find blog posts that highlight “public domain resources”, such as this one: “31 Free Public Domain Image Websites”. As that same article mentions, use these websites at your own risk, and always make sure that you understand the licenses and terms of conditions of the content that you are intending to use.
Sounds
Bandcamp
Bandcamp is an online music store and also a platform for independent music and artists. Most of the content in Bandcamp is marked as “All Rights Reserved”, meaning that if you want to use that material you need to seek permission from the author or artist.
Bandcamp has some special tags for music that you can freely reuse. Check the Creative Commons, the CreativeCommons (without spaces) and the Royalty-free music tag. However, this means that you might be spending a lot of time searching for something that matches the type of work that you are looking for. Luckily, there is a tool called Camp Explorer that allows you to search with different tags. In order to use the tool, you need to enter each tag that you want to search for and press the button that says “add”. For example, to replicate the search shown below you need to write “creative commons”, press the button “add”, write the style of music you want to search for (i.e. “funk”), press the button “add”, and it will retrieve you albums that match that criteria.
From there, suppose you go into the album “A kind of Alchemy”. If you scroll down, you will find the license information, next to where the tags are. Remember to attribute using the TASL approach!
Soundcloud
SoundCloud is a platform where different people can share their audio recordings. These recordings can be music, podcasts, interviews, and much more. It also allows for uploading Creative Commons materials. Like Bandcamp, their search interface is sometimes hard to navigate. You can search for “Creative Commons music” and then filter by tag. Or you can also search with the “Creative Commons” tag.
However, you have to be extremely careful when reusing this content. Most of it says that is Creative Commons but the people uploading this content are actually not licensing it with a Creative Commons license. Always go to the track and search for the “show more” button to find the attribution information. See for example in this track “Phlex - Light Me Up (feat. Caitlin Gare) [Argofox]”
If that credit line doesn’t appear, then search for another resource that has it.
ccMixter
ccMixter is a platform where musicians can upload their music. ccMixter uses three different licenses, two of them are CC licenses (CC BY and CC BY-NC) and the other one is a special license designed by them that provides royalty free music for certain types of uses. To search for content, you need to go to their service Dig ccMixter. You can search by filters or just type a manual search.
Since the website offers only two licenses, it is more likely that you will find a CC BY content easier, particularly if you use the search filters wisely. The CC symbols are clearly displayed at the right corner of every track. 
Free Music Archive
Free Music Archive is another platform for musicians and creators. It has great search features. Their search functionality also allows you to filter by license, track duration, and genre.
FMA also displays the CC licenses in very clear ways, and provides for a very complete TASL attribution that you can copy. See the example.
1 Aggregators are websites that harvest or receive content from affiliated providing institutions, making it easier to search in one place for all the information.
Cheatsheets
Ethical and other considerations
|
YES/NO |
If you answer... |
|
|
Do you plan to modify the work that you are searching for? |
YES |
YES: Do not use any work licensed under the CC BY-ND or CC BY-NC-ND license. |
|
Does the work depict a person in an event or situation that might put her security or life at risk? |
YES |
YES: Search for another resource. |
|
Do you plan to make a commercial use of the work afterwards? |
YES |
YES: Avoid using works licensed under the CC BY-NC or CC BY-NC-SA license. |
|
Does the person or situation being depicted might contribute to sigma generation? |
YES |
YES: Search for another photo that represents the topic in a more abstract way or in a way that is not stigmatizing. |
Searching for content
Reusing content
Storytelling from remote: Safety and care in online spaces
The shift from an in-person meeting to an online workshop in response to the COVID-19 pandemic resulted in an experimental exploration of creative and feminist space-making that is grounded in collective care. Developed by Superhumans: hvale vale, Jennifer Radloff, Zana Fauzi, Liy Yusof
Introduction
Superhumans: hvale vale, Jennifer Radloff, Zana Fauzi, Liy Yusof
This module sprouted from a digital storytelling workshop for EroticsSA partners and APC staff held online in August 2020. The shift from an in-person meeting to an online workshop in response to the COVID-19 pandemic resulted in an experimental exploration of creative and feminist space-making that is grounded in collective care. A few months later in October, APC held their 2020 global member convening, Closer Than Ever, where themes of care, safety, and change emerged again. Some seeds from that event are in this document too. The facilitation team of both events saw an opportunity to create a section to share learnings and reflections as building blocks for future storytelling workshop space-making.
“There have been great societies that did not use the wheel, but there have been no societies that did not tell stories.” — Ursula K. Le Guin
Why do we tell stories?
Stories have long been one of the most powerful methods to connect people and communities. When we tell stories, we express our truth, our version of our experiences. With stories, we long to be heard, not to be judged. Our stories are the connections we have to our past and our memory. In telling our stories, we embody a part of ourselves, our gift to the people listening. In telling our stories, we recognise we are not alone in our experiences, as anyone could relate to the stories we tell. In telling our stories, we heal.
We also tell stories to advocate. Stories spark action and movement in others, whether internally or externally. Stories have the power to relate personally to people more than headlines in the news or a factual article. This is why the role of storytellers is more important than ever. As we communicate our hopes, our realities, our lessons, and our radical imaginations into the world, we have the capacity to inspire the change we need.
When we conduct storytelling workshops online, it is safe to assume that not all experiences, facilitations, and methodologies offline would easily translate online. At the same time, we can no longer assume that everyone has equal access to the tools we have, or respond the same way online as they would offline. We must consider these nuances and face them to create an inclusive and caring space.
Getting storytellers to tell stories remotely would mean we need to contend with two layers: content and data. With content, how do we represent ourselves and our communities in the way that will not sideline our and their experiences? With data, how do we get our stories out into our audience in a way that we know will not inexplicably cause harm to themselves and their identities? How do we, as trainers, inform these practices and safety decisions?
How to use this document
This module hopes to serve as an opportunity to rethink the ways we conduct storytelling workshops in a remote setting environment. It aims to embed digital safety at all levels of the storytelling process and can be used to support existing work in other themes. It is written for facilitators and trainers as a starting point of considerations for the process of making safer and caring spaces for remote storytelling workshops in any context. It has more questions than answers.
This is not an exhaustive document. We welcome every feedback and insight that will help us build an evolving storytelling manual built on the feminist principles of participation and technology, with the practical elements of care and safety made central in every step of the way.
As you read through, it may be helpful to unpack the following questions:
- Can this help us design our storytelling workshop remotely?
- How can we embed care and safety in every step of the process?
- How could this consideration look like for us? What would we need to rethink in our context to incorporate elements of care in a practical way?
Rethinking communication
Workshops should not replicate the asymmetrical communication structure of webinars. A key difference is a storytelling workshop requires a convening of a group of people to work on their stories and come to a set of conclusions with each other, and celebrate together. To run a storytelling workshop remotely is even trickier: How do we engage people in the absence of face-to-face communication? How will they work together? In what ways can we be understood and cared for? What happens if we experiment with different ways of communicating with our participants?
Synchronous vs. asynchronous communication
Trying to schedule a remote storytelling workshop is made even more challenging when your participants are spread across time zones and with various needs. Synchronous communication means an exchange of information in real-time. Asynchronous communication, on the other hand, refers to the exchange of information between us without the requirement to respond promptly and at each other’s own pace. Synchronous communication can provide our participants with a sense of togetherness and community, while at the same time, it is also recognised that asynchronous communication would allow our participants to work at their own pace.
Consider
Rethinking our over-reliance on real-time communication
Can we opt for a workshop to be run asynchronously instead? Do we really need everyone to be in the same space at the same time, or can they be assigned homework and report on some agreed timelines?
Asynchronous communication can be a form of inclusive care
It allows our participants to respond to us at their own pace and whenever they feel comfortable, prepared, and safe. What we can learn about asynchronous communication from disability justice activism, which places the utmost care and safety towards the understanding that we have varying needs and capacities— which means making learning aids, transcripts, translation, and other necessities available to our participants (that might be limited if we were to do this in real-time).
The tools we use to connect with each other
How accessible they are for everyone, and the types of communication expected from participants.
What can we learn from the practice of asynchronous communication in ‘seasoned’ remote workers
Who often use a variety of tools to get in touch with each other despite the dividing time zones and physical spaces?
Rethinking funding
With in-person meetings, we allocate funding to visas, elements of privacy, spaces for focused attention, meals, technology, and materials needed to make the workshop possible. Now that the money isn’t going to venue rental or accommodation, where should it go to achieve the care and safety of everyone involved? Is it really cheaper to move online?
Funding direct support for participants
It is not often recognised that both online and offline events require a travel process— commuting to a space where they can devote their full attention to the matter at hand. What do ‘travel costs’ look like for attending a remote gathering? Participants at remote workshops should not have to bear the burden of their varied hidden costs to be fully present at your event.
Consider
Why not include a flat per diem with no claims process that allows them to determine what they need to participate fully? This may include the cost for arranging for elder care, child care, cooked meals, renting a private space with internet access, paying for data, internet, and electricity, buying art materials needed to participate fully and commit themselves to the workshop. This could include sponsoring devices and apps.
Funding a dedicated support team
An online team looks different and may function at a slightly different dynamic than an offline team. While a clear terms of reference (TOR) are always needed for every organising team — online or offline — at physical workshops, a lot of tasks are not obfuscated by the limitation of the screens we sit in front of, so someone can easily jump in and help if the other team members need them.
(Note from Liy and Zana: It would also be helpful to solicit a list of the typical tasks of the tech team as a resource for creating TORs.)
Considerations on the documentation team
Making a list of expectations
For writing and graphics. What would be important for both the immediate and long term? Is there a meta-layer of learning that you want to capture for future organizing?
How can your documentation team be part of the agenda-making processes?
What do they need to look out for from each day’s sessions in the workshop, and what should they do about it? Consider setting expectations and co-creating ways of working together during the workshop, especially on forming links between the more immediate work of a graphic documenter and more belated work of a rapporteur. They may need briefs about what needs to be captured at different points of each day.
Is one documenter enough?
Consider that recording the session is not a substitute for coherent documentation. For example, matching the chat box to what is being said on video— or compiling side conversations in chat— needs active work simultaneously and alongside documenting the event. In our experience it requires at least two rapporteurs to get a full sense of the event’s proceedings.
Live visual documentation is an emergent practice
How do we explore it in online spaces? What expectations do we have of the process and how do we see it being useful beyond the event? In what ways can rapporteurs and artists support and build on each other’s work?
Considerations on the tech team
How many ways can the tech team offer guidance to the participants?
Some of your participants might be new to using the platforms and tools of the workshop. Consider the kind of support you want to make available to them and when.
Can they offer a short custom tutorial asynchronously or in real-time
To explain ways to use the features of each platform used for the remote storytelling workshop?
Rethinking facilitation
Circumstances have compelled us to change our notion of space, even for people already working semi-remotely. Many facilitators find it challenging to adapt to holding space online despite years of experience facilitating in-person meetings. Iterative workshops such as the Erotics digital storytelling workshops could not and will not neatly translate to online spaces. Maybe this is because the ‘space’ is not directly comparable to a tangible hall. Although visas are no longer a requirement to attend, every person in the room still accesses it from their own unique digital circumstances.
1. Recognising the digital situations of your participants.
Knowing what access needs your participants have beforehand can help you design a workshop with more safety and care.
Consider
Reflecting on how varied or particular their circumstances are
Which could include: Load-shedding, mobile data access, devices that they use, subtitles, live captions, or interpreters, physical health and circumstances, eg. no flashing lights in presentations or videos, colour blindness for designing visual material for the workshop, content warnings, being in a timezone that is not often considered in meeting design, participants who are only able to type in chat, power dynamics between participants and facilitators, and any other situations.
What can we as trainers and facilitators do to account for these variety of needs?
2. Preparing the workshop digital space
A single technology may elicit many possibilities, from the extent of communication to the politics they may impact us. In organizing the digital space for remote storytelling workshop, we need to account for the apps and technology we use for real-time and asynchronous communication throughout the event.
Consider
How much tech is too much tech?
Is it possible to opt for a low-tech setup as long as the focus is on story, community, and audience?
Are all the costs of the apps and services we use accounted for
And do we have all the features we need? Check the details of the pricing plans to avoid being charged for several extra users during or after the workshop, or having to suddenly pay for access to important features during the workshop.
How do we assess security and risk assessments for the apps involved?
What is the role of the tech person/team in this, and how is it different from the facilitators’? Would it be useful to make a decision-making guide for participants to weigh the nuances of their decisions on visibility?
How can we consider the politics of the technology and the platforms we decide to use?
Our workshops might involve the participation of marginalised people and care is important to avoid inflicting harm. When possible, prioritise FLOSS (free/libre and open source software) and open standards tools driven by community needs, sustainability, and security.
Put together a list of tools and resources for the participants
Adhering to the FLOSS and open standards tools whenever possible to prepare them for their upcoming storytelling processes together. Work with the tech team to be ready for any questions that might come up when the participants start to install these tools.
Presenting a feminist principles of participation
To orient the room to the same direction. Knowing that there are clear values grounding the space that they agree with can help them open up and participate more fully.
3. Reimagining introductions
Storytelling is a magical, creative process, but that does not mean it should just be owned by the storytellers in our workshop. We as facilitators, too, can tell stories in our very own role and capacity. What better way to do this by exploring the new ways we introduce each other in the sessions?
Consider
How many ways can we imagine memorable introduction activities done remotely?
How many ways can we adapt the existing ways we conduct introduction activities offline to online?
- One idea is to combine the Photo Exhibition activity in remote storytelling workshops with introductions by asking participants to post a photo and introduce themselves in its caption.
- Another idea is to share a current favourite song and make a playlist curated by everyone in the workshop.
4. Cameras on / off?
It might seem like a small decision, but there is a lot to account for in the request to turn a camera on.
Consider
Thinking about what is on the screen and when
Sharing something on-screen will typically minimise the facetime of the facilitator(s) or others with their cameras on, so consider what you want to be the main view on screen at different parts of the workshop process and align it with other facilitators and the tech team.
Consent and safety
What does it mean to have cameras turned on when there is a recording of the session? Give your participants the option to turn their cameras off before you begin recording any session. To help them make their decision, inform them of where and when the recording could reappear and who will have access to it.
Multiple cameras take up a lot of bandwidth
If any of your participants are connecting with mobile data, they may be streaming more data than they need to. Will the data requirement of turning cameras on affect the ability of some participants to stay connected to the whole workshop?
The story of a square
It came up at the APC Closer Than Ever convening that "what you show in your little frame says a lot about you and your circumstances." It may be a point of care to consider that a reluctance to turn on the camera may be the participants negotiating what limited control they have over their boundaries to equalise themselves in the room.
5. Working with and around mics
In a remote storytelling workshop, we would definitely expect our participants to be willing to pick up the mic and share their stories. However, there are some instances where they might forget to turn off the mic, causing some background noise to spill into our digital space, or in very rare instances, inadvertently voicing out in the middle of someone else talking. How do we, as a trainer, establish the boundaries between these many different scenarios?
Consider
Establishing some procedures
If participants want to pick up the mic and speak — for example, Zoom has the HAND option, or to type HAND in the chat area. Remind them to mute whenever they are not talking to the room.
Expecting to mute microphones on behalf of other participants
If you have the capacity to.
Establishing reminders
Before asking others to take the mic, for example not to attribute others, or offering content warnings.
Giving options for participants
Who could not speak over the mic e.g. noisy background, sore throat, feeling uncomfortable etc. to voice out in the chat area.
6. Checking for engagement
Checking for engagement matters to facilitators in an interactive online workshop space when silence falls and visual cues are lacking. Feedback forms after the event is a common practice, but it might be helpful for facilitators to ‘feed’ themselves by designing more immediate ways to discover feedback as the workshop happens.
Consider
How can we design more reciprocity in online workshops?
Maybe this could be as simple as asking everyone to respond with a word in chat if they understood or relate to what was being said. Participants could also write a word on paper and hold it up for workshop documentation (over their own faces if they prefer).
How can we reimagine the consultation process for remote workshops?
What support and availability can the facilitators offer to guide participants remotely? At the Storytelling from Remote workshop, some participants had last-minute tech emergencies, eg. a virus when trying to install editing software. From that experience we learned that participants may need to be reminded and prompted to seek guidance, and be clear about what requests they can make. These are not as easily intuited as at an in-person meeting.
Exploring ways of working with silences or non-verbal communication
At an APC care session, participants turned off their mics and talked to each other in chat while the facilitator quietly played the ukulele.
7. Exploring ways of using a facilitators back-channel
Building a good thing takes a village. In the case of our storytelling workshop, we have a team of amazing people who will be involved with us in trying to make our remote storytelling workshop a success. How does a good team relationship translate to facilitating practices?
Consider
Giving instructions in multiple ways
In offline spaces, there are ways of intuiting what to do beyond verbal instructions, but in an online space it is just a screen and a chat box. Give instructions in multiple ways beyond verbally— have it on standby in chat to paste, make a slide of instructions that stays on as long as the exercise is going on, translating instructions into more languages, check for understanding before activity begins.
Creating a different channel for facilitating team for coordination
This could work for any app the conversations will take place — Mattermost, Telegram, etc. Different platforms have different affordances, politics, and more importantly the capacities to which we will adapt. How many announcements does a backchannel platform need? Can we opt to send messages to our team to an even later / earlier time when a lot of their time zones overlap? Which platform to use best for what purpose?
8. Releasing yourself of perfection!
It is very easy to want to fall into the trap of perfection when you are in the role of a trainer, especially if this is your first remote storytelling workshop. Remember that it is as important to practice care with yourself and your team as you would practice care for your participants.
Consider
Agendas are there as a framing and holding space
Agendas change, and so we will adapt. It is helpful not to to get too attached to this agenda so you are open to shaping it strategically if needs arise.
Don’t forget to extend the endorsement of ‘No Perfection’ over to the participants and the support team
Your participants might feel uneasy to share their stories to the room especially if they are yet unfinished. Ensure them that stories are a journey and always in the making, they can share what they have. It can be as simple as telling them “Perfection is for tomorrow.”
Recommended resources, tools and further reading
Recommended resources, tools and further reading to kickstart your remote storytelling workshop
Tools we used to run our remote storytelling workshops
Tools to create your stories
These tools were used at the workshop and many were recommended by our participants.
Media, images, photos, icons, and general content
- Creative Commons: https://search.creativecommons.org
- Wikimedia Commons: https://commons.wikimedia.org/wiki/Main_Page
- Internet Archive: https://archive.org/
- The Public Domain Project: https://www.pond5.com/free
- Pexels Creative Commons: https://www.pexels.com
- Flickr Creative Commons: https://www.flickr.com/creativecommons /
- Unsplash: https://unsplash.com
- The Noun Project: https://thenounproject.com/ (icons)
- Freepik: https://freepik.com/
- Cliply: https://cliply.co (GIFs)
- Giphy royalty free GIFS: https://giphy.com/explore/royalty-free
Audio
- Musopen: https://musopen.org/
- CC Mixter: http://ccmixter.org/
- Free Music Archive: https://freemusicarchive.org/
- Bensound: https://www.bensound.com/
- Freesound: https://freesound.org/
- Youtube music library: https://studio.youtube.com/
- Thematic: http://hellothematic.com/michellephan/
- Audacity: https://www.audacityteam.org
Video
- Adobe Premiere Rush?
- Open Broadcaster Software https://obsproject.com
- https://itsfoss.com/open-source-video-editors/ (check if this complies with FLOSS)
How others tell their stories
- Using voice notes to tell stories: https://www.apc.org/en/blog/community-networks-stories-sharing-vision-and-importance-network-improve-and-strengthen-peoples
- MFI Africa E-Zine: https://archive.org/details/mfiafricaezinefinal/page/n5/mode/2up
- AfroQueer podcast: https://afroqueerpodcast.com/episodes/
- End of the World: https://www.endoftheworldshow.org
- Digital storytelling from APC: https://stories.apc.org/browse/