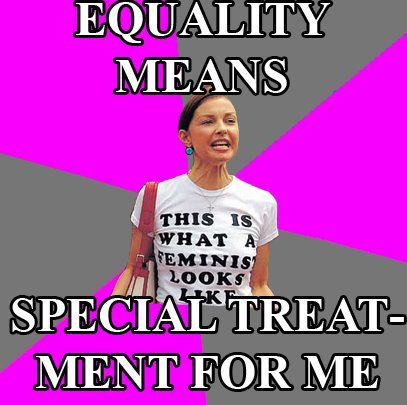(en) FTX: Safety Reboot
The FTX: Safety Reboot is a training curriculum made up of several modules for trainers who work with women’s rights and sexual rights activists to use the internet safely, creatively and strategically.
- Introduction
- Welcome to the FTX: Safety reboot
- Training modules and getting started
- Resources to prepare your training sessions
- Online gender-based violence
- Introduction and learning objectives
- Learning activities and learning paths
- Online GBV or not? [starter activity]
- Deconstructing online GBV [deepening activity]
- Story circle on online GBV [deepening activity]
- Take Back the Tech! Game [tactical activity]
- Planning response to online GBV [tactical activity]
- Meme this! [tactical activity]
- Mapping digital safety [tactical activity]
- Resources | Links | Further reading
- Creating safe online spaces
- Introduction and learning objectives
- Learning activities, learning paths and further reading
- Unpacking "safe" - visioning exercise [starter activity]
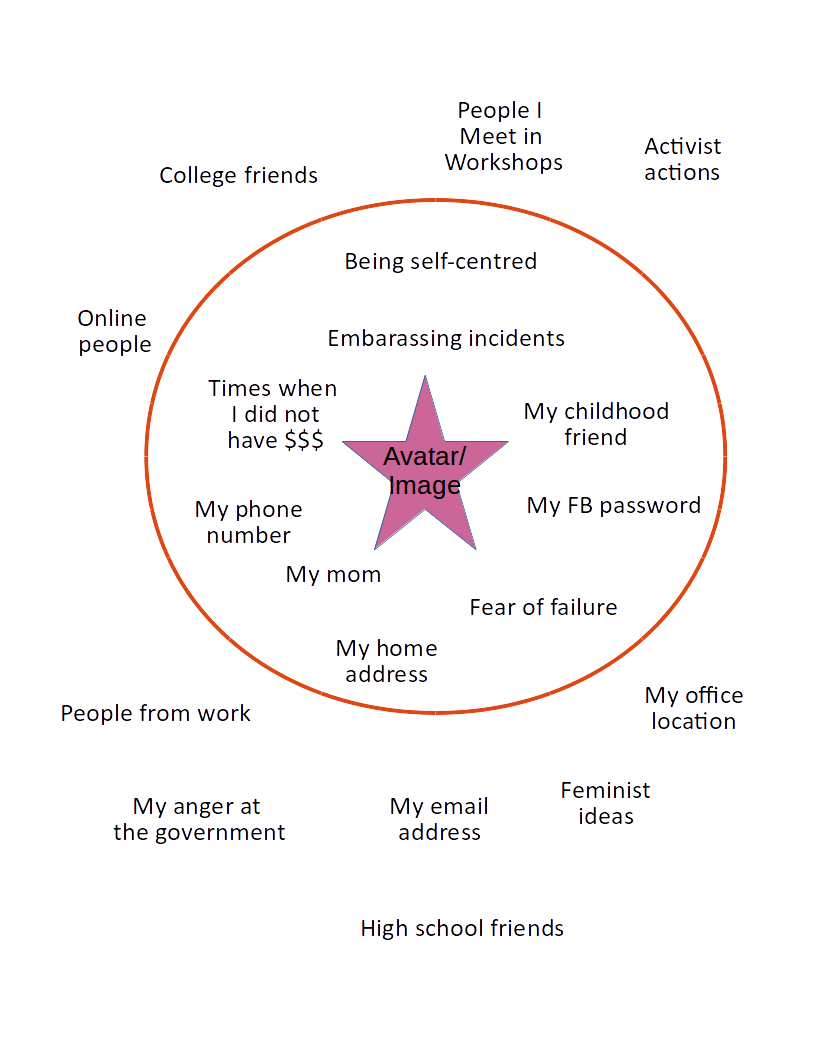
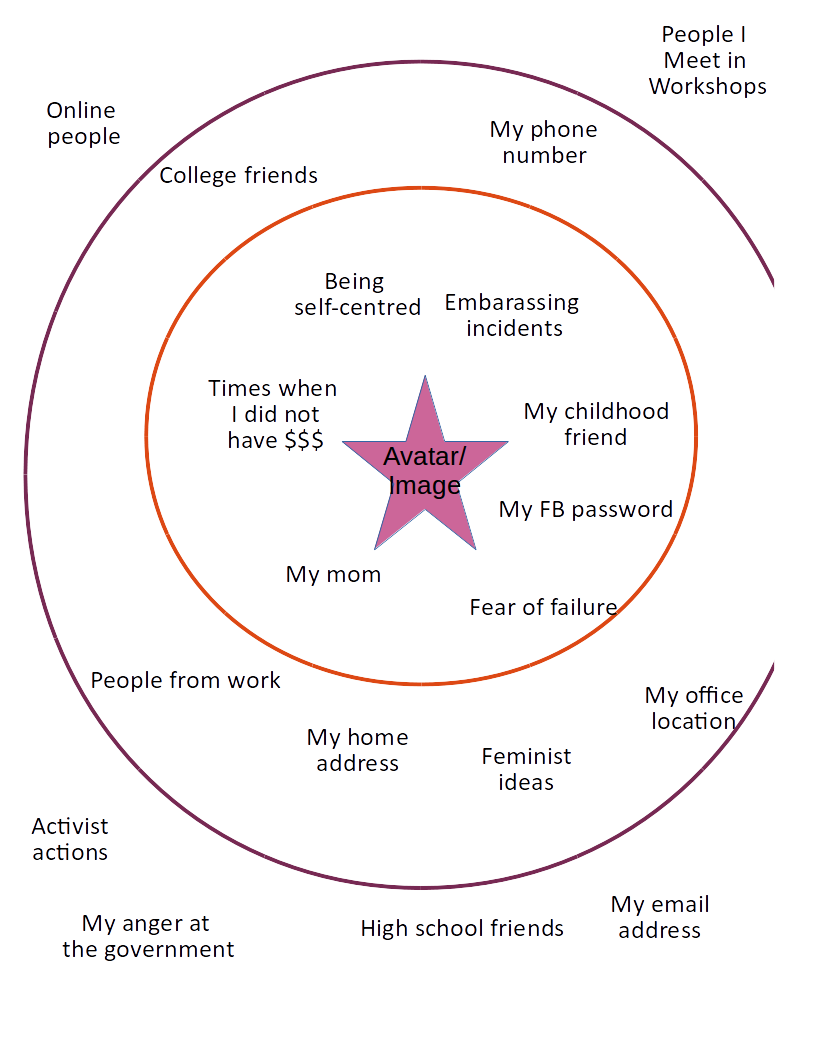
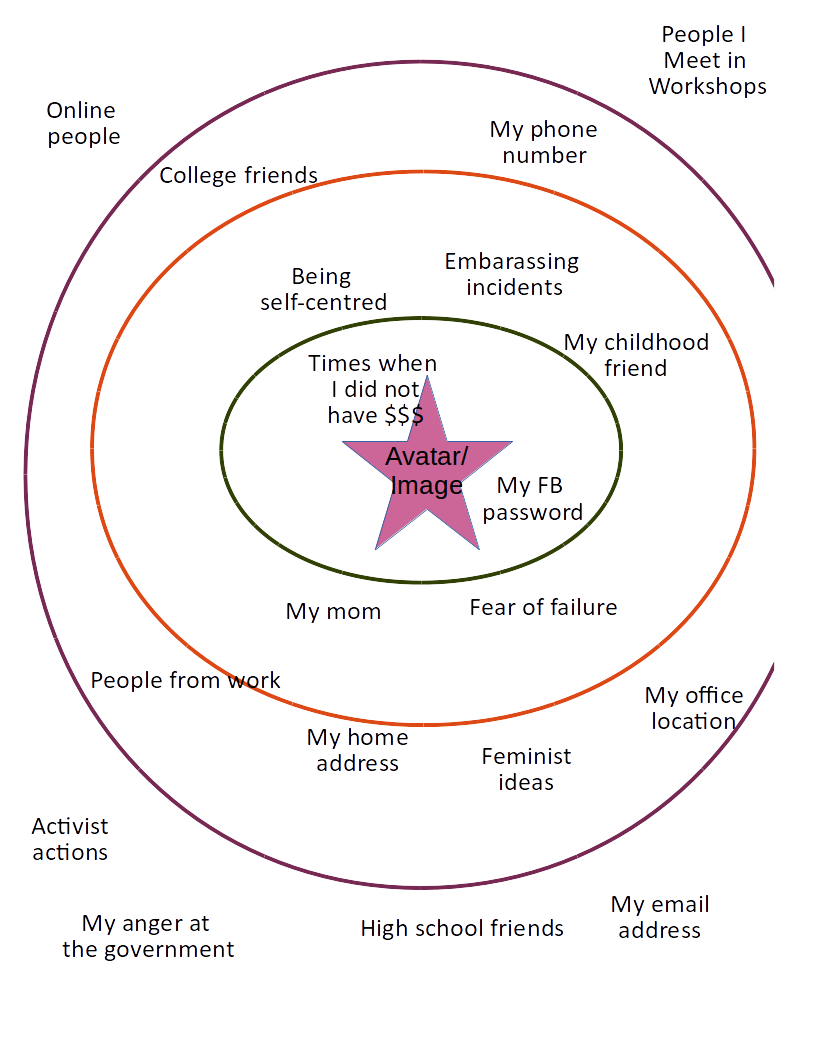
- The bubble - visualisation exercise [starter activity]
- Develop your internet dream place [starter activity]
- Photo-social-network [starter activity]
- The cloud [starter activity]
- Visioning + discussion: Settings + permissions [starter activity]
- Input + discussion: Privacy, consent and safety [deepening activity]
- Input + activity: Online safety "rules" [deepening activity]
- Making online spaces safer [tactical activity]
- Alternative tools for networking and communications [tactical activity]
- Mobile safety
- Introduction and learning objectives
- Learning activities, learning paths and further reading
- Mobiles, intimacy, gendered access and safety [starter activity]
- Making a mobile timeline [starter activity]
- Himalaya trekking [starter activity]
- Collecting phones [starter activity]
- Me and my mobile [starter activity]
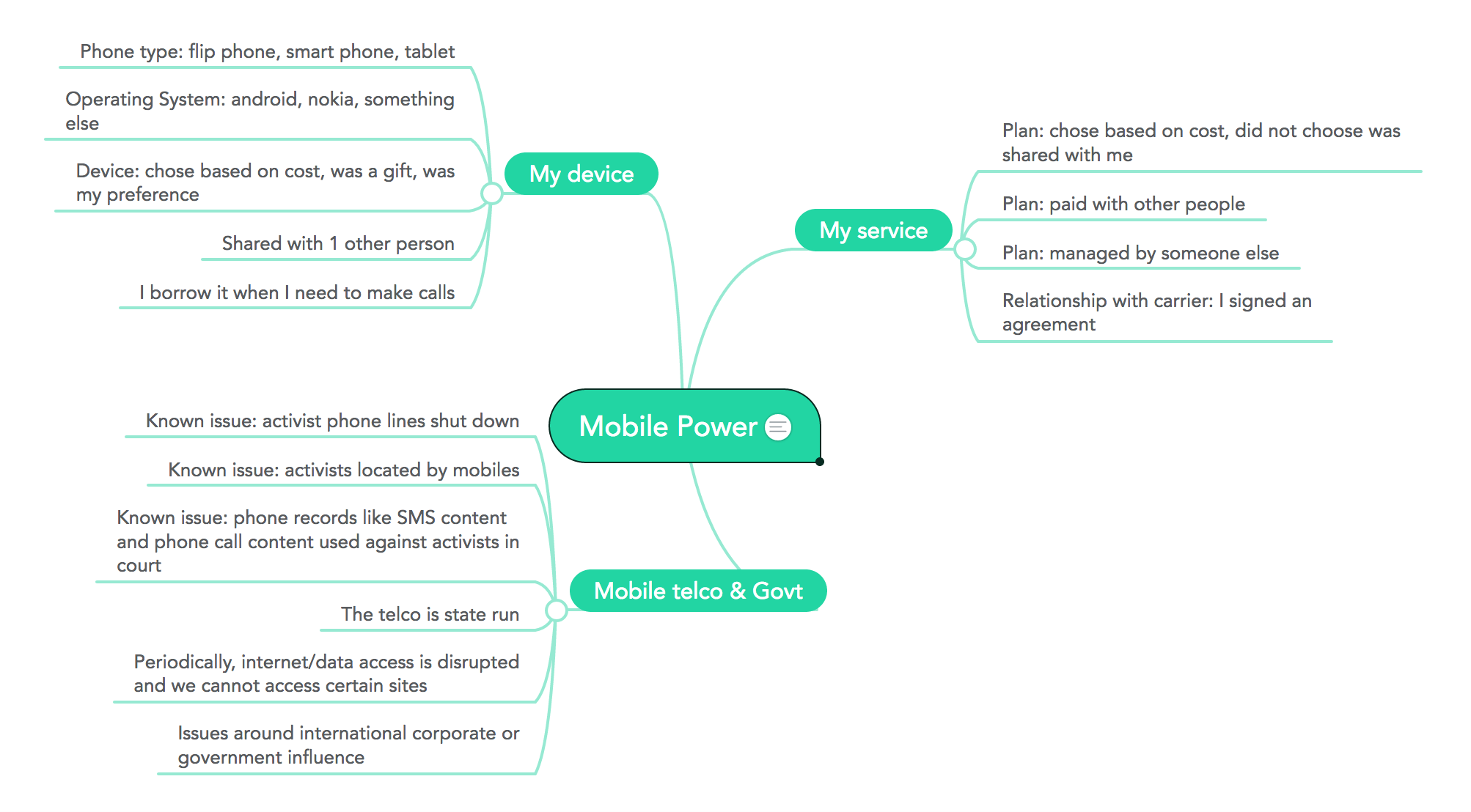
- Mobile power - device, account, service, state, policy [deepening activity]
- What is a phone? How does mobile communication work? [deepening activity]
- Debate: Documentation of violence [deepening activity]
- Planning mobile communications for actions/organising [tactical activity]
- Back it up! Lock it! Delete it! a.k.a. Someone took my mobile: Border crossings, arrests, seizure, theft [tactical activity]
- Discussion, input + hands-on: Choosing mobile apps [tactical activity]
- Using mobiles for documenting violence: Planning and practicing [tactical activity]
- Reboot your online dating safety [tactical activity]
- Safer sexting [tactical activity]
- Feminist principles of the internet
- Introduction, learning objectives, learning activities and further reading
- Introductions of internet love [starter activity]
- Imagining a feminist internet (3 options) [starter activity]
- The internet race [starter activity]
- Women's wall of internet firsts [starter activity]
- How the internet works: The basics [starter activity]
- Social movements: What’s in a tool? What’s in a space? [deepening activity]
- FPI presentation + discussion [deepening activity]
- Risk assessment
- Learning objectives and learning activities
- Introduction to risk assessment [starter activity]
- Assessing communication practices [starter activity]
- Daily pie chart and risk [starter activity]
- The street at night [starter activity]
- Re-thinking risk and the five layers of risk [deepening activity]
- The data life cycle as a way to understand risk [deepening activity]
- Organising protests and risk assessment [tactical activity]
- Risk assessment basics [foundational material]
- Risk assessment in movement organising [foundational material]
Introduction
Welcome to the FTX: Safety reboot
The FTX: Safety Reboot is a training curriculum made up of several modules for trainers who work with women’s rights and sexual rights activists to use the internet safely, creatively and strategically.
It is a feminist contribution to the global response to digital security capacity building and enables trainers to work with communities to engage technology with pleasure, creativity and curiosity.
Who is it for?
The FTX: Safety Reboot is for trainers working with women’s rights and sexual rights activists on digital safety. Trainers should be familiar with the obstacles and challenges faced where misogyny, censorship and surveillance are restricting activists’ freedom of expression and ability to share information, create alternative economies, build communities of solidarity and express desires.

Why the FTX: Safety Reboot?
The FTX: Safety Reboot explores how we occupy online spaces, how women are represented, how we can counter discourses and norms that contribute to discrimination and violence. It is about strategies of representation and expression and enabling more women’s rights and sexual rights activists to engage technology with pleasure, creativity and curiosity. It is a feminist contribution to the global response to digital security capacity building, bringing the APC Women’s Rights Programme’s unique methodology and approach, which we call Feminist Tech eXchanges (FTX).
The APC Women’s Rights Programme (APC WRP) has developed the FTX: Safety Reboot as a contribution to existing training guides on digital security but rooted in a feminist approach to technology. The FTX: Safety Reboot is a work in progress to assist trainers to enable activists to use the internet as a transformative public and political space, to claim, construct, and express ourselves more safely.
Our political framing and tool for analysis are the Feminist Principles of the Internet (http://feministinternet.org), which shape and inform our work. The FPIs build our case for a safe, open, diverse and gender-just internet.
What does it do?
FTX creates safe spaces of exchange and experience where the politics and practice of technology are informed by local, concrete and contextual realities of women. These spaces aim to build collective knowledge and ownership. We are conscious of power relations which can be easily set up, particularly around technology, an area where women are historically excluded and their contributions invisibilised. We advocate for change through working towards consciously deconstructing these power relations.

APC WRP capacity-building work bridges the gap between feminist movements and internet rights movements and looks at intersections and strategic opportunities to work together as allies and partners. APC WRP prioritises inter-movement building in order to bridge gaps and grow understanding and solidarity between movements.
What are the FTX core values?
FTX core values are: embedding a politics and practice of self and collective care, participatory and inclusive, secure, fun, grounded in women’s realities, transparent and open, creative and strategic. FTX emphasises the role of women in technology, prioritises appropriate and sustainable technologies, and is framed by the Feminist Principles of the Internet. FTX explores feminist practices and politics of technology and raises awareness on the critical role of communication rights in the struggle to advance women’s rights worldwide. Recognising the historical and current contributions of women in shaping technology, FTX grounds technology in women’s realities and lives. We emphasise local ownership of FTX and have seen the uptake of FTX by our members and partners over the years.

Training modules and getting started
What are the training modules?
The FTX: Safety Reboot currently contains the following five independent modules (with one in draft form) rooted in interactive learning activities to facilitate communities in sharing knowledge and values around representation and expression and to build confidence and skills to be safe and effective in online spaces.
Online gender-based violence |
Creating safe online spaces |
Mobile safety |
Feminist principles of the internet (FPIs) |
Risk assessment |
What do the modules contain?
The modules listed above contain information and resources that can be used independently or in groupings as needed.
Learning Activities
The learning activities in each of the modules have been divided into three kinds:

Starter Activities
Are meant to get the participants to start thinking about a topic and spark discussions. For the trainer/facilitator, these activities can be diagnostic tools to observe what levels of understanding the group has, and to adjust the workshop based on that.

Deepening Activities
Are meant to expand and dig into the topics and themes.

Tactical Activities
Are meant to respond to multiple learning objectives in practical ways. These include hands-on exercises and practical strategising activities.
Getting started
Get to know your participants
Use one of the Training Needs Assessment methods described here to learn more about your participants:
Plan your training
Design your agenda based on what you have learned about your participants, their needs and interests, and suggestions in the Learning Pathways suggested in each module. See also:
Localise your training
Activities reference real life examples and the more you can draw on local examples that are significant to the lives and work of participants, the more participants will be able to engage with the material and learning objectives.
We suggest familiarising yourself with examples that are relevant to your participants and prepare yourself to speak about these. If you are able to engage with participants before the training, ask your participants for significant incidents relating to the workshop you'll be facilitating, and research these more deeply so you understand the cases and can share them in the workshop.
Frame your training
To make your training a safe and inclusive space for discussion, you can refer to useful feminist frameworks/resources such as Intersectionality and Inclusivity and Notes for Holding up a Healthy Conversational Space. You can also refer to our Feminist Practices and Politics of Technology, our Feminist Principles of Participation and the Feminist Principles of the Internet.
Writers and Collaborators
WRITERS
- APC Women’s Rights Programme (APC WRP) - Erika, hvale vale, Jan, Jenny
- Cheekay Cinco
- Bex Hong Hurwitz w/Tiny Gigantic
- Jac SM Kee
- Helen Nyinakiiza
- Radhika Radhakrishnan
- Nadine Moawad
COLLABORATORS
- Bishakha Datta, Point of View
- Christina Lopez, Foundation for Media Alternatives
- Cecilia Maundu
- cynthia el khoury
- Fernanda Shirakawa, Marialab
- Indira Cornelio
- Javie Ssozi
- Nadège
- Nayantara Ranganathan
- Ritu Sharma
- Sandra Ljubinkovic
- Shubha Kayastha, Body and Data
- Smita Vanniyar
- Florie Dumas-Kemp
- Alexandra Argüelles
visit TakeBacktheTech
FTX Safety Reboot Convening

Resources to prepare your training sessions
Get to know your participants
In order to be able to design appropriate and relevant training workshops, it is recommended that trainers/facilitators conduct a Training Needs Analysis with their participants. Through this process, the trainer/facilitator can begin learning about the contexts, the expectations, the technical baselines, and the current understanding of the relationships between feminism and technology of their intended/expected participants.
There are various ways to do this process, depending on the time available, access to participants, and resources on-hand. Here we provide guidelines for three different types of Training Needs Analysis:
- Ideal Training Needs Analysis: There is ample planning and designing time. The trainer/facilitator has access to the participants.
- Realistic Training Needs Analysis: The trainer/facilitator has limited time to plan and design the training workshop, and limited access to participants.
- Base-Level Training Needs Analysis: There is limited time to plan and design the training. The trainer/facilitator has no access to participants.
Note: Conducting a pre-training needs analysis does not mean that the Expectations Check during the first session of the training workshop is no longer necessary. It is advised that any workshop should still include that session to confirm and reaffirm the pre-training needs analysis results.
Ideal training needs analysis
- Preparation time: More than one month
- Comprehensive Training Needs Analysis Questionnaire (Annex 1)
- Baseline Interview Questions (Annex 2)
In this scenario, the trainer/facilitator has ample time to plan and design the training workshop, which means they have the time to connect with the participants, the participants have time to respond, and the trainer/facilitator has time to process the responses.
Given that there is proper lead time for the training planning and design, there are three methodologies in the ideal scenario:
Comprehensive Training Needs Analysis Questionnaire for Participants (see Annex 1 for the questionnaire). In this questionnaire, there are questions about the participants' use of technology and tools, as well as their understanding and knowledge of feminist tech concepts and online GBV, and their expectations for the training workshop. Using this questionnaire, the trainer/facilitator will be able to get a better picture of the needs and realities of the expected participants.
Follow-up Interviews with Participants. Based on the results of the questionnaire, the trainer/facilitator can get a sample of the expected participants to take part in an interview. Ideally, the sample should include all the participants, but a minimum of 50% (depending on the number of participants) should be met. Participants who had outlier/unique responses to specific questions (i.e. the ones with the most experience and the least experience in technology; or the ones with the most knowledge and the least knowledge about feminism and technology; or the ones who have very specific expectations from the training workshop) should be part of the interview process. Usually, these interviews with participants take 60 minutes maximum.
Consultation with Organisers. In this stage, the trainer/facilitator meets with the organisers to share the results of the questionnaire and the interviews, and the proposed training plan and design. Here, the trainer/facilitator also confirms that the design and plan meet the organisers' goals and agenda. It is assumed here that throughout the entire process, the trainer/facilitator has kept in touch with the organisers.
Realistic training needs analysis
- Preparation time: Less than one month
- Use: Comprehensive Training Needs Analysis Questionnaire (Annex 1) OR Baseline Interview Questions (Annex 2)
This scenario is more common. More often than not, a trainer/facilitator has less than one month to plan and design a training workshop due to resource constraints.
Given the time constraints, the trainer/facilitator will need to short-cut the Training Needs Analysis process, and depending on an initial consultation with the organisers, choose between conducting the Comprehensive Training Needs Analysis Questionnaire, or interviewing 50% of the expected participants (see Annex 2 for Baseline Interview Questions).
Base-level training needs analysis
- Preparation time: Less than two weeks
- Use: 10-Question Training Needs Analysis Survey (Annex 3).
In this scenario, the trainer/facilitator has less than two weeks for planning and designing the training workshop. Here, the trainer/facilitator barely has time to get to know the participants before the training workshop and may distribute this questionnaire at the start of a workshop or as participants enter the workshop. While there are a few ways to make up for this lack of pre-training needs analysis during the workshop itself – Expectations Check, or running a Spectrum of Technology Use Exercise, or the Women's Wall of Technology Firsts, we still recommend trying to have the participants respond to a 10-Question Training Needs Analysis Survey (see Annex 3).
Resources
Annex 1: Comprehensive training needs analysis questionnaire for participants
linked here as an .odt document
Annex 2: Baseline interview questions
The purpose of this interview is to short-cut the Comprehensive Training Needs Analysis Questionnaire for Participants. So it will cover the general topics covered by the questionnaire, but with less detail. These interviews are supposed to be 60 minutes long. Each set of questions should roughly take about 10 minutes.
- Tell me about yourself. Your organisation, your role there. Where are you based? Which communities do you work with?
- What are the challenges you face in your work when it comes to using the internet? Is this a challenge that the communities that you work with face as well? In what way? How are you or your community members addressing these challenges?
- What internet applications do you use the most? Do you use them for work or for your personal life?
- Which device do you use the most? What kind of device is it? What operating system does it run on?
- What are your top concerns about using the internet and the applications that you use? Do you feel like those applications are secure?
- Can you tell me what your top three expectations are about the training workshop?
Annex 3: 10-Question training needs analysis
- Name, organisation, position, and description of the work that you do.
- What kind of communities do you work with, and what are their main issues?
- How long have you been using the internet?
- What operating system do you use the most?
- What kind of mobile phone do you have?
- What are the apps that you use the most?
- What are the top three concerns you have about your use of technology and the internet?
- What are the top three security tools/practices/tactics that you use?
- What do you think are the top three issues around feminism and technology?
- What do you want to learn from the training?
Evaluate your training: Training evaluation tools
Why evaluate?
- To do it better next time.
- To design follow-up support for participants around the workshop learning objectives.
Process
+/-/delta This is a simple method for participants and trainers to share input. We suggest doing this at the end of a workshop for single-day workshops, and at the end of each day for multi-day workshops. We suggest simple feedback methods for the end of workshops because people will tend to be fatigued, with attention wandering, by the end of a training period. A method like this can be quick and participants can choose to share details based on their preferences.
Ask each participant to consider and share things they think were good, things that were bad, and things that should change.
Depending on the time available and the resources you have on hand, participants can write their responses on pieces of paper and hand them to the facilitator, or you can go around and get each participant to say their responses out loud while a facilitator writes them down.
After everyone has shared, trainers/facilitators sit together, share their own +/-/delta reflections as facilitators, and review the participants' +/-/delta reflections. You can use these to:
- Create a list of learnings to share with other trainers/facilitators.
- Make adjustments to this and future workshops.
- Design your follow-up with participants.
One-week follow-up Follow up with hosts and participants to share any resources from the trainings you are able to share (facilitation guide, slides, handouts, etc.) and any reflections you may have about the workshop and next steps.
Three-month follow-up Follow up with the hosts and participants to ask about the impact of the workshop. This is a good time to ask people if they have implemented tools and tactics, revisited their own strategies, etc., as a result of your training.

Intersectionality and inclusivity
“There is no such thing as a single-issue struggle because we do not live in single-issue lives.” – Audre Lorde
What is intersectionality?
intersectionality is a framework that recognizes the multiple aspects of identity (such as race, caste, gender) that enrich our lives and experiences and that compound and complicate oppressions and marginalizations.
Here is an example to understand intersectionality in context: Between 25% and 50% of women experience gender-based violence in their lifetime. But this aggregated number hides the ways that multiple oppressions compound such violence. Women of color are more likely to experience gender-based violence than White women and wealth privilege can help to insulate some women from some forms of violence. Bisexual women are far more likely to experience sexual violence than other women. Transgender people are also more likely to experience hate violence than cisgender people. In short, all women may be at risk for gendered violence, but some women are far more at risk.

How do I practice intersectionality in conversations?
Those of us with identity privilege (example: white, straight, cis, able-bodied identities) can have a harder time including those who are oppressed in our feminism. That is why it is important to focus on creating inclusive, respectful spaces where the lived experiences of all women are valued and understood. Here are 5 quick pointers you can keep in mind to create intersectional and inclusive conversations.
- Self-reflect and recognize your privileges: Taking up the difficult work of investigating our own privilege is key to intersectional feminism. It is a good practice to look within ourselves and take upon the desire to learn about issues and identities that do not impact us personally. Being privileged doesn't necessarily imply that our existence oppresses another community. What it means is there are certain experiences we don't have to go through because of who we are.
- Decenter your perspective: It’s important to understand that feminism is about more than ending sexism — it’s also about ending all the interconnected systems of oppression that affect different women in different ways. There are things that our privileges allow us to take for granted - able bodied people don’t always notice ableism, and White people don’t always notice racism. So make an effort to avoid centering feminism around yourself or people of privilege.
- Listen to each other: On the feminist issues where we hold privilege, it's crucial to listen to the experiences of all women, including those women who don't to see the world through a more inclusive lens You can't walk the walk if you don’t know where the walk goes. So if you are a White feminist, be mindful that you are not talking over or for people of color.
- Think about the language you use: If you are a non-Muslim feminism, be wary of saying things like “It must feel hot outside in a veil”. Using terms such as #PussyPower can alienate transgender women who may not possess these body parts. These are two examples of the many ways in which the language we use can ostracize women. It is good practice to constantly check ourselves and how we talk about women who do not look like us, or who lead lives different from our own.
- Be willing to make mistakes and correct for them: Adopting an intersectional framework is not an easy process. So, sometimes despite our best efforts at being inclusive, we may slip up and get called out for our mistakes. Rather than becoming defensive, recognize that being called out is not really about your worth as a person, and that you can apologize and adjust your behavior to avoid repeating the same mistake.
- Recognize that everyone brings knowledge to the table: Recognizing that everyone brings knowledge to the table helps to lessen the distance between us and challenge the idea that some of us know more than others when really we all know some things more than others. Working together to learn from each other (as the activities in these modules are designed to achieve) helps everyone gain most from this experience.

Additional resources
- https://everydayfeminism.com/2015/01/why-our-feminism-must-be-intersectional/
- https://www.bustle.com/articles/117968-5-reasons-intersectionality-matters-because-feminism-cannot-be-inclusive-without-it
- https://www.elitedaily.com/women/feminism-inclusive-women/1507285
Notes for holding up a healthy conversational space
A conversation on gender-based violence can evoke different responses from different individuals based on their personal experiences and privileges. Here are a few pointers to keep in mind while talking about this sensitive issue.
1. All participants do not have the same level of privilege
While the included modules offer many activities and resources, many discussions are not just intellectual exercises for everyone ― people who face discrimination or have experienced violence are potentially dealing with a mental health issue.
2. Importance of trigger warnings
Trigger Warnings allow those who are sensitive to the subject of discrimination and violence to prepare themselves for discussing about them, and better manage their reactions. Remember, the key to an effective Trigger Warning is being specific - if a Trigger Warning is not specific enough, it could refer to anything from eating disorders to bullying. Thus, it’s a good idea to follow Trigger Warnings with specialized lists of content. For example, while discussing a case study on partner violence, you could specify beforehand, “A quick heads-up: This discussion contains instances of Rape, Abuse, and Partner Violence. If you feel triggered, please know there are resources to help you.”. For those who need the warning, this helps them prepare for the discussion, and for others, this helps sensitize them to the fact that those around them can find the discussion hard going.
3. Do not pressurize someone to talk about their experiences
Forcing someone to talk about a sensitive event is making someone re-live the experience and all of the negative emotions that come with it. Some people just aren’t ready to open that box of worms. Instead, give people room to explore the trauma and the the time to open up when they are ready.
How to help someone who feels triggered
Even with the best of preparations, sometimes precautions don’t work because triggers are usually individual specific. Here are a few steps you can take to help someone who feels triggered by an ongoing discussion.
1. Recognize
Recognize that your content could be hurtful to someone.
2. Apologize
Apologize for saying something that hurt the person. Remember that the apology is about the person who has been hurt, and not about you. Avoid justifying or defending your words or actions and be sincere about your apology; it is not personal.
3. Empathize
Empathize by trying to understand why the person may be hurt. You can do this by actively listening to the person who is feeling triggered.
4. Rectify
Continue the discussion by avoiding a repetition of the said trigger. Remember that triggered reactions can temporarily render people unable to focus, regardless of their desire or determination to do so. Be open to participants leaving the conversation if they feel uncomfortable. Make sure they have access to help if they need it. It is advisable to have a mental health professional on board for such emergencies at events.
If a professional is not present at the venue, here are a few resources that can enable you to help someone who’s been triggered:
- https://www.rainn.org/articles/flashbacks
- https://www.bustle.com/articles/87947-11-ways-to-help-a-friend-whos-been-triggered-because-it-is-most-definitely-a-real
Feminist practices and politics of technology
FPT embodies both a critical perspective and analysis of technology. It poses questions and defines issues relating to technology from feminist perspectives, taking into account various women's realities, women's relationships with technologies, women's participation in technology development and policy-making, power dynamics in technologies and feminist analysis of the social effects of technologies.
FPT defines our approach to training. It defines the core values that comprise feminist technology training. It is based on the experiences of women and feminists in and with technology training.
FPT is a growing idea. How it has been defined so far can change and mutate through practice, discourse and experience, and because politics and contexts change.
FPT recognises and advocates that feminist practices of technology cannot be devoid of a feminist perspective and analysis of the politics of technology.
FPT views technologies in two ways: on one hand, technology has resulted in new issues for women and in new permutations of women's issues; on the other hand, technology provides new solutions and approaches to addressing women's issues. It grounds new technologies to women's issues, interrogating how women's realities influence how technologies are developed, used, appropriated and benefitted from as well as how technologies are changing women's realities. It also looks at technologies with a strategic and creative eye, assessing how they can be developed and appropriated to support and facilitate women's rights agendas.
As a perspective, it does not define what the conclusions and issues are. Rather, it poses questions and issues that would lead to exploring and interrogating technologies from feminist perspectives.
Some of the questions include:
- How has user-generated content (as facilitated by the internet) changed women's representation in media?
- What are the new ways of and spaces for women's building on the internet?
- How have women's issues changed as a result of our increasingly technology-driven cultures?
- Is online communications secure for women?
- Who controls technologies?
- How can women's rights activists benefit from new technologies?
- What does 'control over technology' mean?
As an approach to training, FPT has core values that define 'feminist technology training'. It springs from the experiences of the FTX trainers as participants and facilitators of technology training. Most of these reflect the values that have already defined 'feminist training'. The difference is that these values are specifically relevant to technology training contexts.
The core values include:
Participatory / Inclusive
Feminist training recognises that the trainer has as much to learn from the learners as they do from her and from the other learners. As such, training will be designed in such a way that will facilitate exchange and discussion.
Feminist training allows for various ways of learning and communicating to accommodate different learning styles.
Feminist training allows for differences in opinions, in experiences and in contexts. It does not assume that all of the participants come from the same background, and it has to be flexible enough to accommodate differences.
Secure
Feminist training is a space where the participant feel safe in two ways: in their learning – that they can ask questions, raise issues, divulge information that will not be rejected, belittled and divulged without their consent in their understanding of technologies – that they are aware of the (possible) risks of certain technologies (i,e. Privacy in social networking sites, safety in using the internet to publish alternative content, etc.)
Grounded in women's realities
Feminist training should be based on the needs and realities of the participants. This means, that technologies that will be tackled will have to be appropriate and relevant to the participants. This also means that discussions on technologies must take into account the context of the participants.
Appropriate / sustainable technologies
Feminist training should prioritise technologies that the participants can apply, appropriate and use after the training for their work.
Free and Open Source software will be given priority, but only if the participants can sustain their use post-training.
Transparent / open
Feminist trainers are aware of that they have their own agenda for the training and they make their goals apparent to their participants. This means having processes where expectations from participants and trainers are negotiated and agreed upon.
Creative / strategic
Feminist training is an opportunity to look at technologies strategically and creatively to appropriate them in ways that are relevant to the participants' contexts.
Emphasising the role of women in technology
Feminist training highlights women's contribution to technology development, use and policymaking. Women like Ada Lovelace and others who have significantly contributed to technologies are great role models, specifically for learners who have fears regarding technologies.
Furthermore, this contributes to correcting the mis-representation of women in the history of technology.
Emphasising women's control of technology
Feminist training is not afraid to get into the deeper aspects of technologies (in development and in policy-making) and emphasis on 'control' and full understanding of how technologies work (and not just on use) must be made.
Fun!
Feminist training should be a space where women can have fun with technology to break down barriers that affect women's relationships and control over technologies.
Our feminist principles of participation
This document has been developed by WRP APC as a guide for ourselves and partners hosting learning and capacity building events, such as Take Back the Tech campaigns, Feminist Tech Exchanges and conversations around the Feminist Principles of the Internet. You can find a pdf version here.
We have produced this in a spirit of collaboration and co-ownership to encourage creating spaces both online and onground, that are framed as feminist and facilitate safety and fun for all as well as promoting and upholding principles of diversity, creativity, inclusivity and pleasure. We come from many communities, cultures and faiths and embody a beautiful diversity of physical, social and psychic realities. Through creating safe, fun and caring spaces, we enable engaged participation, deeper learning and the possibility of growing dynamic, responsive and caring movements.
These are the framing principles we value and apply in the spaces and events we co-create.
- Create a safe space for all participants.
- Be respectful.
- Be collaborative and participatory.
- Recognise and value diversity.
- Respect the privacy of participants.
- Be aware of language diversity.
- Handle disagreement constructively.
- Embed politics and practice of self and collective care
The principles in action
Create a safe space for all participants.
As far as possible, for example through an online survey, get to know your participants beforehand. Ask for specific needs they might have such as physical access, dietary requirements, particular travel fears or safety requirements. Ideally the venue should have light and air, be quiet and be free from surveillance and interference from non-participants. During the event, gently encourage participants to be open about subjects which might cause them distress and to take responsibility for alerting facilitators if they feel uncomfortable.
Be respectful.
Negotiate with participants at the start of the event about what is needed for a respectful and nurturing environment. Encourage deep listening – meaning that we give our full attention to each other. Acknowledge that there are things that our privileges allow us to take for granted – for example, able bodied people don’t always notice ableism, white people don’t always notice racism.
Be collaborative and participatory.
As trainers/facilitators be well prepared, open and aware of your own agenda for the event and make your goals apparent to the participants. Have processes where expectations from participants and trainers are negotiation and agreed upon -- for example, use smaller groups if some people are not comfortable speaking in plenary. Ground learning in women’s lived realities and use methodologies that prioritise participant voices and experiences. Recognise that everyone brings learnings to the table.
Recognise and value diversity.
Acknowledge differing levels of privilege in the room as well as our multiple identities. Ensure that intersectionality does not make people feel more excluded and ‘different but encourages the harnessing of diversity of identities and experiences as an opportunity for learning, exchange and enriching the space. Help people recognise that a discussion on ableism or racism is not necessarily targeting the able bodied or white people in the room as perpetrators of discrimination and encourage people to listen, think and explore systemic discrimination.
Respect the privacy of participants.
Ask for consent on photographs and directly quoting participants / giving attribution for documentation. Agree on the use (or not!) of social media. Co-develop a privacy agreement for the event. If there are discussions on sensitive issues such gender-based violence, racism, homophobia or transphobia, recognise that some participants may not be ready to speak about these things. Do not push discussion about personal experiences if this causes distress. Always ensure there is a trained person available to support participants who have experienced trauma.
Be aware of language use and respect language diversity.
Acknowledge the languages of all participants and as far as possible offer interpretation/translation. As a rule, everyone should speak clearly and slowly, and feel comfortable asking about acronyms or terms that are not understood. Ask that people think about the language they use and not to use terms that might be oppressive or offensive to others. Request that people be open if they feel offended and use these as learning opportunities. Content may involve technological terms or language that is considered academic and that could be new to some participants. Challenge the tyranny of technological terms! Make content understandable and intriguing and emphasise taking control of and growing a full understanding of how technologies actually work.
Handle disagreement constructively.
Act fairly, honestly and in good faith with other participants. Encourage empathy and take the time to rectify any disagreements, any uncomfortable or hurtful words or behaviour that may occur. Create an atmosphere of openness and facilitate space for apologies and/or explanation if needed.
Embed politics and practice of self and collective care.
Acknowledge that self-care is different for different people and depends on who we are and where we are located in our lives and contexts. Self-care and collective care impact each other. So make time for people to breathe, connect with bodies and hearts, through ritual or embodied practice, to release any tension or anxiety. As holders of space, be mindful of and try and clear any stress in the room so that people can show up to the collective and participate fully. Invite participants to suggest self-care practices.
We encourage people to read APC’s Sexual Harassment Policy can be found here: APC_Sexual_Harassment_Policy_v5.1_June_2016.pdf

FTX Safety reboot convening 2018 draft agenda
Overall design and activities
Goals of the convening
- Bring together feminist practitioners and trainers working on digital safety and self-care to unpack, understand, apply, adapt, contextualise and deepen the FTX: Safety Reboot curriculum on feminist digital security which APC WRP is building.
- Create a space for skill and knowledge sharing on methodologies, approaches and pedagogies for building confidence, growing knowledge and uptake in this area by women's rights and feminist activists in different movements.
- Integrate feminist work on the politics of care and well-being into the field of digital security and promote and support political kinship, solidarity and a deepened understanding of the feminist practice of technology.
- Facilitate building a trusted network of feminist trainers and facilitators for collaborative work, continued exchange and active solidarity in this area.
Day 1: Grounding ourselves and our work
The first day will be about talking about rooting the convening on three levels:
- the context that brought everyone together: WRP´s work, FTX safety reboot, the plans for a feminist commons, etc
- the world that we live in and do our holistic security work: discussion of issues that we face, and that our participants face
- what it means to be a feminist trainer
Proposed activities
- Participant intros and agenda setting (This might happen on two levels: one with the participants from the FTX Convening and the TBTT Global Meet-up, and again in the FTX space.)
- Part of the morning will be merged with the TBTT Meet-up
- Grounding ourselves holistically [title pending] (session to be led by Sandra and Cynthia)
- Visualising where we work in, who we work with and who we are as trainers
- A session on the world in which online gender-based violence happens (merged with the TBTT folks)
Day 2: Challenging ourselves
The second day will be mostly about having facilitated sessions about the challenges we face as trainers, and different ways of doing the training work that we do. These suggestions are largely based on the responses to the survey that we sent to the participants. We can accommodate about 5, 1.5 sessions for this day.
- Integrating well-being and self-care in our work (to be led by Sandra and Cynthia)
- Digital Security At The Grassroots (Bishakha volunteered to lead this)
- Organisational security (co-facilitated by Bex and Dhyta)
- [Late afternoon] Fish bowl session on risk assessment (convergence with the TBTT Meet-up)
Other possible topics.
- Re-imagining how we train (storytelling, the use of art, avoiding fear-based tactics, not using military language, etc)
- Re-imagining risk assessment
- Countering online gender-based violence
Day 3: Exploring ways forward
This day will do focused work on the FTX modules. At the end of Day 2, it would be good to have teams of people who are looking at the parts of the FTX Safety Reboot that they want to work on more.
On Day 3, we give them time to look at the parts and to reflect on the following questions:
- How will this module be useful in your context? How would you change it? What would you add?
- What are the points in the module that will cause your participants stress? And how will you address that?
- What do you need as a trainer - facilitator to be able to apply this module? Skills, knowledge, experience, prep work?
And in their teams, they can discuss suggestions for improvement.
(I really want to have time for folks to try out activities with each other, and perhaps with the TBTT folks. But that would take time. So any ideas around how we can do that would be welcome.)
Day 4: Working together?
For this day, maybe leftover work from Day 3. But also, have conversations about:
- sustaining ourselves as trainers
- the feminist commons
- how we work together in the future, opportunities for collaboration
- what happens to the FTX modules
We will also be interfacing with the TBTT folks towards the end.
Visualising where we work in, who we work with and who we are as trainers
Activity 1
Here, we ask the participants to draw one our two typical folks that they work with in their trainings, with focus on the following parts:
- Head: what do they know, what issues do they grapple with
- Heart: what is important to them, what do they value, what do they believe in, what are their fears
- Hands: what are the skills they have, what do they bring to the training
- Feet: where are they? what contexts do they live in
This activity will allow for time for self-reflection, but the processing will happen in small group discussions.
Here, we aim to begin to start grounding the work in the realities and contexts of the people that our participants work with.
Activity 2
Using the same method as above, ask the participants to draw themselves.
Give them time to reflect on the the drawings that they have done.
Activity 3
In small groups, have time for to discuss the following questions:
- What are the threats our communities are facing? How has it changed?
- As activists and part of social movements, how does our work as trainers contribute to the cause?
- What are the limitations of training as an intervention? Are there other capacity development modes we should be exploring?
- What are the gaps between who we are as trainers and who the folks we work with?
- Given the activities, what does it mean to be a feminist trainer?
Debrief
Then we come back to the big group and have a discussion about what the groups talked about.
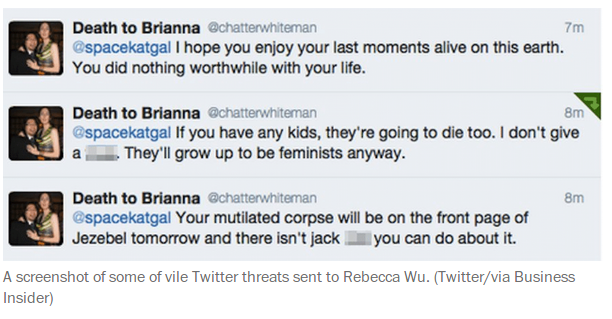
Online gender-based violence
Guide participants through the issues relating to online gender-based violence – its root causes, how violence plays out on the internet, the continuum of violence that women, women-identified and queer identities experience online and offline, and its impact. We **highly recommend** that you choose a Learning Path to travel, as these include activities with different levels of depth that should help participants obtain more insight into the covered subjects.
Introduction and learning objectives
Introduction
This module is about guiding participants through the issues relating to online gender-based violence – its root causes, how violence plays out on the internet, the continuum of violence that women, women-identified and queer identities experience online and offline, and its impact.
This module is based largely on the more than a decade of work that the APC Women´s Rights Programme (WRP) has done through the Take Back the Tech! campaign, the End violence: Women's rights and safety online project, MDG3: Take Back the Tech! to end violence against women project, and EROTICS (Exploratory Research on Sexuality and the Internet).
Learning objectives
By the end of this module, the participants will have:
- An understanding of the forms of online gender-based violence (online GBV) and its impacts on the survivors and their communities.
- An understanding of the continuum of violence between the offline and the online spheres, and the power structures that allow it.
- Ideas, strategies and actions about the ways in which online GBV, especially in their contexts, can be addressed.

Learning activities and learning paths
This page will guide you through the Module's correct use and understanding. Following the Learning Paths, with activities of varying depth, should allow participants to obtain a better grasp of the studied subjects.
Learning paths
How you can use the activities below – and combine them – will depend on:
- the purpose of your workshop (are you raising awareneness or are you expecting to come up with strategies to respond to online GBV?);
- your participants (are they survivors on online GBV? Or is their experience more removed?);
- your own experience in facilitating these kind of workshops (are you a seasoned digital storytelling facilitator? A digital security trainer who is now getting into online GBV? Or a campaigner who is expected to run an online GBV workshop as one of your campaign´s activities?);
- the time you have available to you to run a workshop
These learning paths are recommendations for how you can mix and match the activities in this module to create a workshop on Online GBV.
We recommend beginning with Online GBV or not? to spark discussion, surface shared understandings of online GBV, and clarify key concepts. This activity would work if your workshop is more general awareness-raising.
Following that, depending on time and the context, you can work with participants using the Deconstructing online GBV or Story circle activities to deepen the group's understanding of online GBV, and to ground the conversation in experiences of people in the room (Story Circle) or case studies (Deconstructing Online GBV). Both deepening activities may cause participants distress, they require preparation.
For the Story Circle activity, specifically, facilitation will need a lot of care and consideration. We do not recommend this activity for solo facilitators, and for those who are just beginning to do these kinds of workshops.
There are Tactical activities that are meant for strategising on response to online GBV. The Take Back the Tech! Game focuses on general approaches to addressing online GBV. If you have limited time, the tactical activity: Meme this! is shorter and faster. It could also be a light activity after a heavy one like the Story Circle on Online GBV. Planning response to online GBV activity aimed towards coming up with a more comprehensive response strategy to specific incidents.
The activity Mapping digital safety could be a standalone workshop with a focus on framing Online GBV with the Universal Declaration of Human Rights.
Some suggested combinations:
| If you have half a day for your workshop, then Online GBV or not? followed by Meme this! |
| If your workshop is focused on strategising and you have limited time, we recommend jumping straight into the Take Back the Tech! Game. |
| If your workshop is about having a comprehensive response to online GBV incidents, then we suggest doing the Deconstructing online GBV, followed the Tactical Activity: Planning response to online GBV. |
Learning activities
Starter activities

Deepening activities

Tactical activities

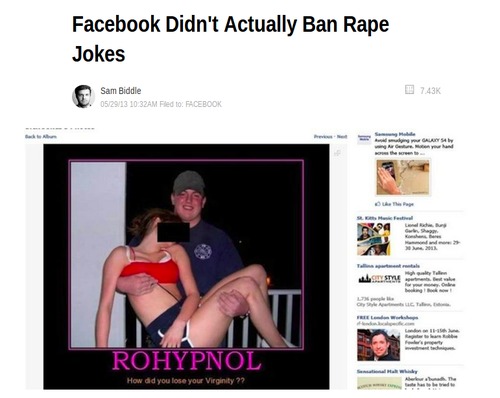
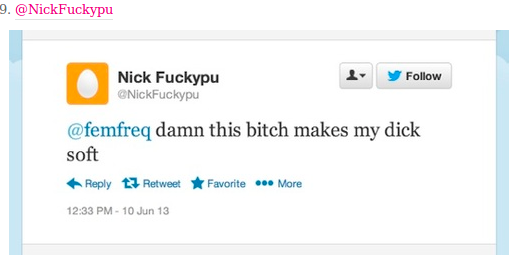
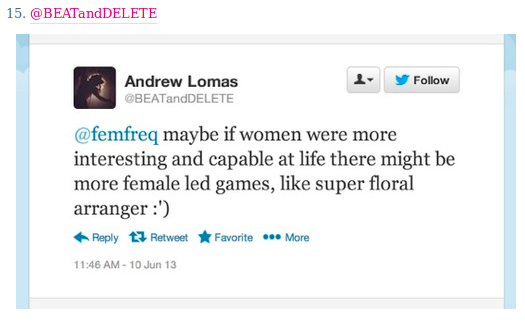
Online GBV or not? [starter activity]
This activity is designed to spark debate and discussion, and give you, the trainer/facilitator an opportunity to clarify concepts relating to the experiences of women and gender diverse individuals on the internet and online gender-based violence (online GBV).
About this learning activity
This activity is designed to spark debate and discussion, and give you, the trainer/facilitator an opportunity to clarify concepts relating to the experiences of women and gender diverse individuals on the internet and online gender-based violence (online GBV). This is specifically aimed towards speaking about the less obvious forms of online GBV, and to discuss the participants' assumptions on how they define what GBV is.
The main methodology in this activity is to show examples of experiences of women and gender diverse individuals online (It would be good to have exagerrated examples to encourage debate or discussion) and memes, and have the participants react with online GBV or Not GBV upon reading/hearing/seeing the example meme. Then you can ask the participants to defend their initial position through a set of guide questions.
It is essential to frame this activity as a vacuum where ALL opinions and viewpoints are allowed (as long as they are expressed in a manner acceptable to the group, assuming Participant Guidelines are established earlier in the workshop), and that what the participants say during this activity will not be quoted/publicised/shared with others. It also a good idea, especially if the group has a lot of experienced feminists, to encourage others to play Devil's Advocate in order to enrich the discussion.
Facilitation Note: It would be ideal to have established and negotiated participant guidelines about respect before-hand, just in case the debate gets heated.
For the trainer/moderator, this activity can be used to learn more about the participants' level of understanding and appreciation of online GBV.
Learning objectives this activity responds to
- An understanding of the forms of online GBV and its impacts on the survivors and their communities.
- An understanding of the continuum of violence between the offline and the online spheres, and the power structures that allow it.
Who is this activity for?
Ideally, this activity is for participants who have an understanding of internet rights, sexual rights and WHRDs.
Time required
Depending on how many examples are shown, this activity can take from 30 minutes to 90 minutes.
Resources needed for this activity
- Signs (not bigger than half a 4A sheet of paper) with Online GBV printed on one side and Not Online GBV! printed on the other. One per participant.
- A way to present the examples of women's experiences on the internet. It could be a poster of the printed memes or a projector to show the memes.
(See Resources for sample memes)
Mechanics
Show a meme or example of an experience that women and gender diverse individuals have had online.
Tip: Perhaps start with a glaringly obvious example of online GBV, then move to more nuanced examples.
After each example, you ask: Is this Online GBV or Not Online GBV?
The participants then raise their boards to show which they chose.
Once everyone has made a choice, you can then ask: Why do you consider this Not Online GBV/Online GBV? Then get an opinion from someone who had the opposite opinion, and allow the group to ask each other questions.
If there is not much disagreement among the group, then dig deep into the example through these guide questions:
- Who is being attacked in this meme? How will it impact them?
- What are the values underpinning this meme? What is the meme creator (and anyone who shares and likes this meme) really saying about women, women-identified, and/or queer individuals, and their communities?
- Does this meme reflect the values in your communities? How so?
- If you had come across this meme, how would you have reacted? How do you think we should react to it?
You can end the discussion with a bit of synthesis, and then move on to the next example.
To synthesise each example, the trainer/facilitator can:
- Do a quick summary of the discussion that the participants had over the example.
- Name what the example is, or the various ways the example has been described.
- Point out the gender stereotyping, gender bias and/or misogyny that was reflected in the meme.
Intersectionality Note: It is also important to draw out how women and gender diverse individuals and communities would be impacted differently by the messages / memes.
You don´t have to do a synthesis for each example that you show. If a discussion on a specific example is similar to a previous one, then you can just point out the similarity.
Facilitation Note: It is important, while the activity is still happening, that you, as the trainer / facilitator, do not take a side in the discussion that the participants are having. Having a facilitator siding with a group of participants is an effective silencer of discussion and debate.
At the end of the entire exercise, you then do a bigger synthesis of the activity. In this synthesis, you can go back to the examples that got the most debate and discussion from the participants, summarise the discussion, and then share your own thoughts and opinions on the matter.
Key points to raise in the main synthesis:
- The relationship between "real world" values and the creation of such memes.
- The existing power structures, patriarchal values, gender bias and bigotry that are showcased in the examples.
- What constitutes gender-based violence.
- How positionality and privilege within the different women and gender diverse sectors have different effects on indviduals and communities.
Facilitator preparation notes
From the start, you need to decide if you are playing a trainer (one with the knowledge and experience to provide answers), or a facilitator (one who guides discussions, and keeps herself from sharing her own opinion) in this learning activity. Being both will not be conducive to a good discussion or a safe space for the participants. If you are being a facilitator, you wouldn't want to provide answers at the end of the discussion, and make participants defensive. If you are being a trainer, you wouldn't want to be so strict in your opinion on the matter that it silences the participants.
Another thing to prepare for is your own assumptions about what online GBV is. Take a refresher by reading Good Questions on Technology-related Violence.
Facilitation Note: This activity is not just to show examples of obvious cases of gender-based online violence, but to have a discussion with the participants about a nuanced understanding of what is online violence and what is not. So, in the examples, include examples of common experiences that women and gender diverse individuals have on the internet – and not just the ones that are glaringly violent.
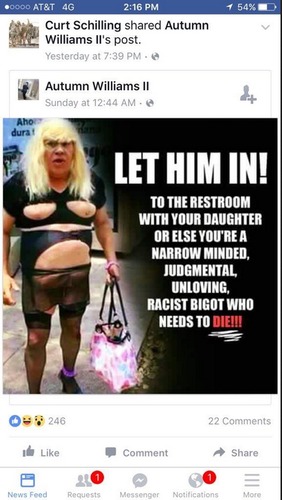
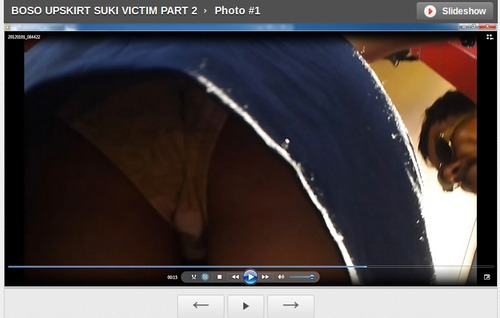
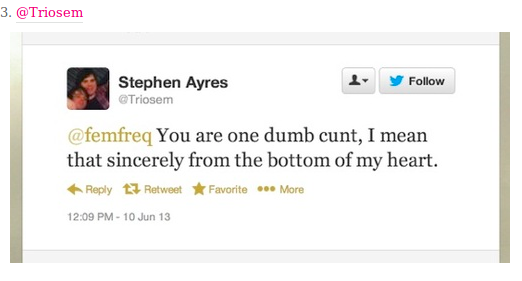
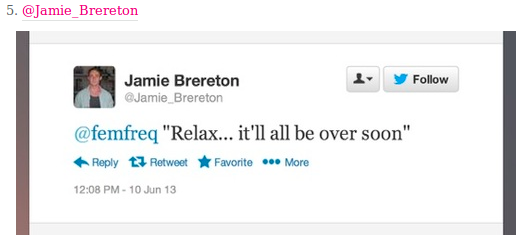
There are sample Sample Memes found below, but it would be ideal to use examples that are context-specific to the participants in the workshop. It would be good to show a range of examples, including messages or memes:
- that are misogynistic, homophobic, transphobic
- that attack women and gender diverse individuals and communities for their actions
- that name or target specific women or gender diverse individual in the message / meme
- that are overtly-violent and / or calls for gender-based violence
- that represent women and queer bodies as sex objects
- that show offline actions against women put online
- that attack women and gender diverse individuals on the basis of their social class
The point here is to not be too obvious in your sample choices but to generate a discussion among the participants.
If you have time to prepare with the participants, ask them for examples of online harassment that they have witnessed (not necessarily targeted towards them) online, and show those examples in the activity.

Additional resources
Sample Memes
Warning : This page contains racist, sexist, homophobic transphobic and rape apology material.
Facilitators Note: There are sample Sample Memes found below, but it would be ideal to use examples that are context-specific to the participants in the workshop. We encourage you as trainers to find your own memes so that they are relevant to the participants.
Intersectionality Note: In choosing sample memes, make sure that you include different race, class, religious backgrounds, sexual orientation and gender identities.

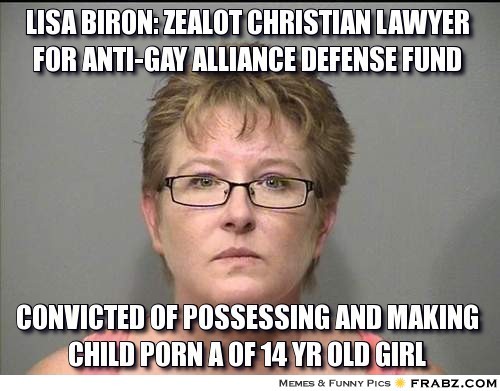
When a woman complains about the lack of women´s representation in video games, a sampling of the reactions she gets: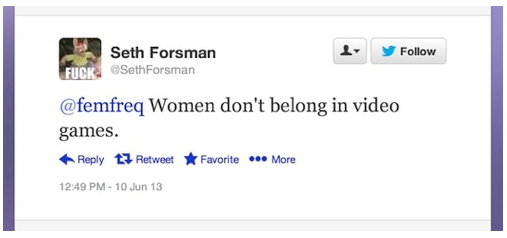

Deconstructing online GBV [deepening activity]
This activity takes the participants through a case study of an incident of online gender-based violence, and gets them to discuss the different aspects of the case study.
About this learning activity
This activity takes the participants through a case study of an incident of online gender-based violence, and gets them to discuss the different aspects of the case study.
Learning objectives this activity responds to
- An understanding of the forms of online gender-based violence (online GBV) and its impacts on the survivors and their communities.
- An understanding of the continuum of violence between the offline and the online spheres, and the power structures that allow it.
- Ideas, strategies and actions about the ways in which online GBV, especially in their contexts, can be addressed.
An important note, while this session will touch upon ideas for response, the main purpose of this activity will be to unpack an example of an online GBV incident.
Care Note: Unpacking a case study of an online GBV incident might cause participants distress.
This is not an activity to do when you do not know your participants and / or if you have not previously gained trust from the group.
In order to do this more responsibly, it is important that you are aware of the experiences of violence that your participants have (see more here: Get to know your participants), and to be observant as you run this activity about how the participants are reacting.
Encourage your participants to raise their hands if they need a break from the activity.
Knowing and having some experience in some debriefing exercises such as those found in the Capacitar Emergency Kit would be useful.
Who is this activity for?
This activity can be used with participants with different levels of experience in women's rights and technology.
Depending on the level of experience of the participants on the various aspects on relating to online GBV, the trainer / facilitator will need to prepare to intervene to clarify concepts around social media, the internet, and even national laws.
Time required
About 2 hours per case study
Resources needed for this activity
- Flip chart paper/whiteboard
- Markers
- Index cards to write down different aspects of the case study that need to be stressed.
Alternatively, you can prepare slides with the case studies and the questions.
Mechanics
You begin by describing the incident to be deconstructed, writing down the following details on individual index cards and posting them on a wall (or if you have prepared a presentation, these could be the bullet points in your slides):
- Name of the survivor + gender + social class + race + educational attainment + any other identity markers
- Country where the survivor is from + if there are laws that could protect them
- The initial incident of online violence , in which platform did this happen
- Where the incident happened , in which platform did it start
- If you can, name of the initial aggressor/s + some details, if it's important in the case study
- If the aggressor/s cannot be named, write down some details about them: their online handles, etc.
- Relationship between the survivor and aggressor, if any
Then open it up for discussion by asking the participants the following questions:
- Who else should be responsible here aside from the perpetrator?
- Who is the community around the survivor? How do you think they could have responded?
- What are the survivor's possible responses to the situation?
- How do you think this incident affected them? (impact)
Write down the responses on individual index cards and post them on the wall.
Then divulge more details of the case study, marking details that the participants have already guessed and writing down more details on individual index cards:
- How did the case escalate? In which spaces was the violence replicated?
- How did the case spill into the survivor's life outside online spaces?
- How did the community respond?
- What other spaces reinforced the initial incident of violence?
- Who else got involved?
Then open the discussion up again by asking the following questions:
- What recourse does the survivor have?
- What laws can protect them in their country?
- What other impact will this have on the survivor based on where they are from, what they do, what social class they belong to, what country they are in?
- What should happen to the initial aggressor/s? Who can make that happen?
- What should happen to the other aggressor/s, including the ones that extended and escalated the incident?
- What is the responsibility of those who own and run the platform where the incident happened?
- Who else is responsible in this scenario? What is their responsibility?
- How could the women's rights movements respond to this?
Write down the responses of the participants to each question on individual index cards and post them on the wall.
At the end of this, there will be a gallery on the wall that shows the different aspects to the case study of online GBV.
To synthesise, reinforce the following:
- The connection and continuum between online and offline violence.
- The complexity on online GBV: the varied stakeholders, both negative and positive.
- The systems and structures that facilitate online GBV as well as those that might be avenues for redress and mitigation.
Facilitator preparation notes
In order to create a relevant case study that will encourage discussion and understanding of the complexity of online gender-based violence, the case study needs to resonate with the participants, which requires knowing where they are coming from and what their concerns are [Note: There is a section here about Getting to Know Your Participants.]
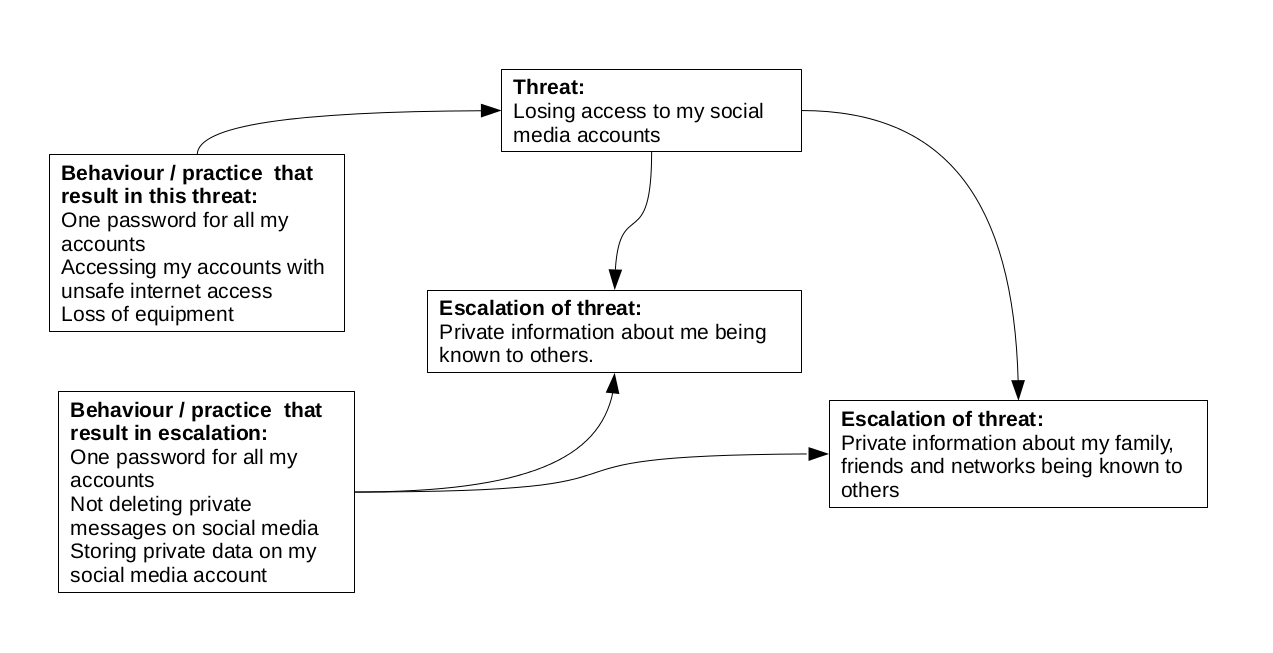
The Sample Case Study below would be useful in articulating the case study that you will share in this session. It outlines the Initial Presentation and the Escalation of the example to be deconstructed.
If you want to to create your own case study:
- flesh out the survivor, where they are coming from, their contexts
- be clear about where the incident happened first and how it escalated
- think about the impact of the incident: offline / online; on the individual, their community / family / friends; on their well-being, digital security, physical security
- try to describe the perpetrator/s´ actions but not their motivations
Additional resources
Sample case study: Selena's case
Initial presentation
Selena is in her final year of college. She attends college in Manila, Philippines, but she heads back to her province in Angeles every chance she gets to visit her parents and her younger siblings. In order to augment her limited funds for her studies, she is a part-time barista at a local coffee shop.
On one trip home, she finds her parents very upset. They accuse her of abusing her freedom in Manila and using her looks to meet foreign men. They slut-shame her, and threaten to cut off their support. They demand that she stop dating foreign men online and causing them problems.
Selena does not use any kind of dating app – she's too busy with school and work. And she already has a boyfriend.
After hours of her parents shouting at her, she finally gets a picture of what happened:
The day before, Heinz from Germany had knocked on her parents' door, demanding to see Selena. He brought with him copies of conversations that he has had with Selena, and the pictures that she has shared with him. Those conversations happened both on the dating app chat and on WhatsApp. He implied that he and Selena have engaged in cybersex. Apparently, he had sent Selena money so she could start applying for a German visa in order to visit him. When she did not get a visa, he had then sent her money to purchase a ticket so they could meet up in Bangkok, where they could be together without her conservative parents watching their every move. She did not show up. Heinz had tried getting in touch with her but she was unresponsive. So he felt he had no choice but to pay her parents a visit. They refused to let him in and threatened to call the authorities if he kept on insisting on seeing Selena.
Heinz had left, angry.
Sounds like a con gone wrong.
Problem: Selena is not aware of any of this. She has never talked to any Heinz. She has not received any money from him. She was not in a long-distance relationship with anyone.
It looks like Selena's pictures and identity were used to "catfish" Heinz.
(Catfishing is when someone takes screen-grabs of someone's photos online and creates accounts in their name in order to con other people. Sometimes, the real name of a person is attached to the fake account, but there have been cases where the photos are attached to fake names.)
Escalation
In response to the incident, Selena had removed all her photos from all her social media accounts, and had sent a message to the dating app and WhatsApp that the account with her pictures was a fake one that some people had used to swindle a German user.
She and her family have not heard back from Heinz. He seems to have left Angeles after her parents turned him away.
One day, at school, a few of her male classmates start heckling her, calling her a slut and a swindler, saying that it's a shame that a pretty girl like her would use her looks that way. One of Selena's friends show her a Facebook page called "Selena is a Slut Swindler". On that page, Heinz recounts what "Selena" had done to him – with screen grabs of their conversations, her pictures, and audio recordings of their cybersex sessions.
The page has trended, and has received a lot of likes and followers.
What can Selena do?
Sample case study: Dewi's case
Initial presentation
Dewi is based in Jakarta, Indonesia. She is a 30-something trans woman, working as a call centre agent for a large multi-national online retail company. With two of her closest friends, Citra and Indah, she has just recently started a small organisation to promote SOGIE equality in Indonesia.
Since they started the organisation, the three of them have been invited to local events around LGBTQI+ rights and have attended demonstrations to support their advocacy. She has been captured in the local news speaking out against toxic masculinity and religious fundamentalism.
One morning, as Dewa was getting ready to go to work, she receives a message on her Facebook Messenger. It´s from an account called, Mus: ¨You made me so happy last night. Do you want to make me happy again tonight?¨ She dismisses it as a wrongly-sent message, so she responds with: ¨I think this is not for me. Wrong send.¨
To which Mus replies, ¨It is meant for you, Ms. Dewi. I saw your pictures and I want to see you in person. So you can make me happy again.¨
Scared that Mus knows her name, she just messages back and says, ¨I don´t know you, please stop.¨ She then blocks Mus.
Then more messages keep showing up from different users on her FB Messenger. The messages get progressively ruder and more explicit. She is also getting more friend requests on Facebook. She opts to block those users and tries to ignore them.
She keeps Citra and Indah updated on what is happening and her two friends are getting worried for Dewi.
To try to get to a reason as to why Dewi was being harassed, Citra Googles Dewi´s name. What they find are images in which Dewi´s face is edited on to naked transwomen´s bodies. The images are all labeled with Dewi´s name, and posted on DIY pornography sites.
Immediately, the three of them write to where the images are posted to request for the take down of the photos and of Dewi´s name on them. They all hoped that that was the end of that and the harassment would stop.
Escalation
One day, Dewi´s supervisor calls her in for a meeting. Then the supervisor shows her Twitter messages addressed to their company with a copy of the doctored images with the caption: Is this what your employees look like? What kind of morals does your company have? Fire HIM!¨
According to her supervisor, their company´s Twitter account was bombarded with the same messages from multiple accounts.
What can Dewi do?
Story circle on online GBV [deepening activity]
This activity allows participants to reflect upon and share experiences of online GBV.
About this learning activity

This activity allows participants to reflect upon and share experiences of online GBV.
A safe space is the main prerequisite for this activity, and some quiet time for the participants to reflect.
This activity happens in two stages:
- Reflection Time, when each participant is given time to articulate and write down their story by answering a series of guide questions.
- Story Circle, where all the participants share their stories with each other.
It is important to note here that this Story Circle is not for the purposes of therapy. Being able to tell your story, even anonymised, has some therapeutic effects, but it should be made clear that this is not the purpose of the Story Circle. If you are dealing with a group that you know has experienced online GBV, especially if there are people in the group who have very recent experiences, you can either make sure that there is someone in the facilitating team who can provide therapy, or skip this learning activity, if you don't think you can handle the participants being re-traumatised.
Learning objectives this activity responds to
- An understanding of the forms of online GBV and its impacts on the survivors and their communities.
- An understanding of the continuum of violence between the offline and the online spheres, and the power structures that allow it.
Who is this activity for?
This activity can be carried out with participants with different levels of understanding and experience of online GBV.
It is important to know before doing this activity if there are participants whose experience of online GBV is current or fresh, as this activity might be a cause for stress for them. Knowing who your participants are, and also knowing what you as a trainer / facilitator can handle is important before considering this activity.
It is equally important for you, as a trainer / facilitator, to be honest about what you can and cannot hold. This activity is NOT recommended for situations where:
- you have not established trust between and among your participants
- you have not had the time to get to know your participants prior to the workshop
- you do not have any experience in handling difficult conversations
Based on the experience of story circle facilitators, it is ideal to have two facilitators for this activity.
Time required
Assuming that each participant will need about five minutes to tell their stories, and about 30 minutes will be needed to collectively reflect, plus some leeway to give instructions, then with a standard workshop size of 12, you will need a minimum of 100 minutes for this activity.
This suggested time for this activity does not include well-being activities that might be needed to address re-traumatisation of participants, or to take a break when needed. Ideally, for standard group size, holding this activity for half a day (4 hours, including breaks) would be sufficient to include well-being breaks and activities.
Resources needed for this activity
- Guide questions written down
- Space for people to reflect
- A big circle in the middle of the room for the participants to share.

Mechanics

This activity has two stages:
- Reflection Time, when each participant is given time to articulate and write down their story by answering a series of guide questions.
- Story Circle, where all the participants share their stories with each other.
During the Reflection Time stage, the participants are given 30 minutes to reflect upon a real-life example of online GBV. They can choose to tell their own experience or someone else's. Even if they are telling their own story, everyone is encouraged to anonymise their story. They should tell one story each.
In order to facilitate reflection, the participants may use the following guide questions to write down their story:
- Who is the survivor? Who was/were the aggressor/s? Who else is involved in the story?
- What happened? Where did the story happen? What kind of violence was committed?
- What was the impact of the violence? How did the survivor react? What did they fear the most? Did the situation escalate or worsen? How?
- What kind of support did the survivor get? Who able to provide support to the survivor?
- What actions did the survivor and their supporters take? How was the case resolved?
- How is the survivor doing now? How do they feel now about what had happened? What lessons have they learned from it?
- What role did technology play in this story? How did it affect the impact of the violence? How did it help in addressing the violence?
Facilitation Note: These are guide questions, and participants don't need to answer all of them. They are just there to help them articulate their stories.
Anonymising stories
Participants are encouraged to anonymise their stories, even if the story is theirs:
- Give the survivor a pseudonym that's not close to their name.
- Make the location of the survivor more general. If there are contextual issues that would make it possible to identify the survivor based on where they are from, then give the location a bigger reach. It's one thing to say that the survivor is from Petaling Jaya in Malaysia, and another to say they are in Kuala Lumpur or even Malaysia.
- Give vague details about the survivor (keep to general markers: gender, sexuality, country, religion, race, social class) but not about their experience of online GBV (the platforms and spaces where the online GBV happened, what they experienced, how it escalated, the impact on them).
Once everyone has written down their stories, gather the participants in a circle.
Lay down the rules for this story circle. It would be good to also have these written down where everyone can see it and reiterate this message.
- What is said in the story circle does not leave the story circle without the express permission of everyone in the circle.
- No one in the circle is allowed to invalidate the experiences being shared. The severity of the violence experienced is not a competition. Don't ask about graphic details of the story.
- Listeners can ask clarification questions but not questions that are invasive. Don't ask “why” questions, ask instead “how” or “what” questions.
- There will be no interruptions when a story is being told. Listen deeply.
The point here is to create a safe space for people to share their stories.
Let everyone know that no one is being compelled to share their stories.
Open up the circle for stories.
Care Note: Think about ways in which to open and close the story circle that honours the stories shared. Some suggestions:
Open with a breathing exercise, close with a breathing exercise
Have a bowl of stones or shells that people can choose to hold, to close the story circle, have everyone put the stones or shells back in a bowl
Then close the circle once the stories have been told. In closing the circle, do something to acknowledge the stories shared and strength of the storytellers.
Depending on the type of participants, and what you are comfortable with, you can:
- Do some deep breathing exercises as a group
- Have everyone go around and thank each other for sharing
- Light an incense and pass it around to cleanse the energy in the room
- Play some music and dance
- Read a poem that relates to honouring our stories. We use an Alice Walker quote to close our digital storytelling circles. Each person has a candle and they take a turn to light the candle at the end of the storycircle from the main candle.
Note: It is essential to have a break for the participants to decompress on their own before summarising the activity.
Then the trainer/facilitator summarises the stories based on the following themes:
- What were the forms of online GBV that were shared?
- Where did the violence occur? Through this, draw out the linkages between online and offline spaces – how did they affect each other?
- Who was/were the usual aggressor/s?
- What was the impact of the online GBV, especially in the offline sphere?
- What were the issues that the survivors faced in resolving their cases?
- How did intersectional issues affect the experience of the violence? For example, specific kinds of aggression, the role of culture/religion and norms, invisibility, challenges in getting support/access to justice.
Facilitator preparation notes
This is not an activity for every trainer/facilitator. Or for every kind of participant.
If you don't think you can handle this, then choose another Learning Activity. Being able to admit what you can and cannot handle as a trainer/facilitator will only make you a better one – and capable of creating safe spaces for training.
This activity also requires a lot of trust between the facilitator and the participants. This requires mental and emotional preparation for the participants. This is not recommended as a starting activity, especially if the participants are not prepared for it.
Some guidelines to follow, if you do choose to use this learning activity:
- During the Story Circle, just allow each participant to tell their story in their own way. Don't rush them. Don't correct their grammar. Don't interrupt them.
- Do not force everyone to tell a story. Maybe, for some people, being able to write down their stories is good enough. Not everyone needs to tell a story, but encourage everyone to do so.
- If a participant is triggered, take a break. Don't force them to continue their story.
- Remind yourself and your participants that healing is a process, and telling stories and being heard is a step towards ending the cycle of violence.
- Doing this activity with a co-facilitator is ideal then you and your co-facilitator can hold the space together.
Read the section on handling emotional situations in the Holistic Security Training Guide.
Facilitation Note: How do you keep to time and respect the storyteller?
Remember, that this activity is about opening up a space for participants to share and reflect upon experiences of online GBV towards understanding the issue a bit more. So while you might want to give the participants more time than 5 minutes to share their stories, you will also have to determine a time limit so that everyone can have the chance to share their stories (if they so choose), and equally important, to have space to reflect on each others stories. Time-keeping is essential to that. It is important that you let the participants know why you are time-keeping.
There are several tactics to gently remind people of that. Here are some:
- Prepare note cards or boards that you can use to signal to them how much time they have left
- Assign a timekeeper from the group so that time keeping is a shared task among the participants
- Wait for pauses in their story telling to remind them of the time they have left

Take Back the Tech! Game [tactical activity]
This role-playing game was developed in order to help participants decide how to take action in local scenarios of online gender-based violence (GBV). Each game takes on one specific scenario of an online GBV example.
About this learning activity

This role-playing game was developed in order to help participants decide how to take action in local scenarios of online gender-based violence (GBV). Each game takes on one specific scenario of an online GBV example.
There are several different Scenarios to choose from, or you can make your own:
- Blackmailed to Go Back
- Trolled on Twitter
- Faked on Facebook
- Porn Pretender
- Disinformation to Discredit
- Watching and Waiting
To play, one Game Facilitator and three teams are needed:
- Survivor Teams A and B. Each team consists of the Survivor of the online GBV Scenario, and a set of four Advisors: Legal, Solidarity, Communications, Skills.
- A third team called the Public presents challenges for each Scenario and decides which Survivor Team chose the best strategies given each context.
Each Survivor Team will develop a Survivor persona to address the Scenario and Challenges presented by the Game Facilitator and the Public.
Survivors will justify their chosen first step to the Public, arguing why it is the best option for their persona and local context. The Public can question each Survivor about their choice. The Public then presents a new challenge in the Scenario from the Challenge cards, and Survivor Teams develop and justify new strategies for two more rounds. As Survivor Teams strategise, so does the Public, exploring possible bystander responses.
The Scenario concludes with the Public presenting a plausible ending to the escalating attack. To finalise, the Game Facilitator debriefs how each player felt in their respective role, to tease out insights, including regarding the role of bystanders and the importance of solidarity. If ever facing such a scenario themselves, with a friend or as a bystander, participants will be better equipped to consider possible response and prevention strategies from many angles.
Learning objective this activity responds to
This responds to all the learning objectives in this module.
Although you can opt for Survivor Teams to “play to win”, the real goal of this role-playing discussion is to help participants:
- explore and weigh strategies for responding to online GBV and understand that there is not just one response; responses are multiple and contextual
- appreciate the ways in which scenarios can escalate
- examine how different elements and actors are involved, and the importance of support networks
Who is this activity for?
This game can be participated in by participants with any levels of familiarity on online GBV.
Time required
1.5 – 3 hours
You can play several Scenarios or just one. Each Scenario should be played 2-4 rounds before starting another Scenario. The game entails a lot of discussion around strategies to mitigate online GBV, and how people respond to actions. There must be sufficient time to orient role players, play out the Scenario as well as unpack how people felt in each role.
Resources needed for this activity
- Printed cards for the game (details in the Cards section)
- flipchart paper
- markers
- tape
- stickers, poker chips, paper cut into small squares, or individually-wrapped candies, if using tokens
- Space big enough for teams to be able to have discussions.
- A table big enough to accommodate the Strategy Cards that each team will be presenting per round.
Mechanics

Players and cards
The participants will be split into three teams:
- Survivor Team A
- Survivor Team B
- Public: presents challenges for each Scenario and decides which Survivor Team chose the best strategies given each context.
The Survivor Teams ideally would have 5 players per team. Each player has a role:
- Survivor: Ultimately decides what strategy to play
- Content Advisor: Provides advice to the Survivor about content-based strategies. The Content Advisor holds the Content Strategy Cards.
- Legal Advisor: Provides legal advice to the Survivor. The Legal Advisor holds the Legal Strategy Cards
- Solidarity Advisor: Provides advice to the Survivor relating to getting support from other people on the internet. The Solidarity Advisor holds the Solidarity Strategy Cards.
- Skills Advisor: Provides advice to the Survivor about what she can do online. The Skills Advisor holds the Skills Strategy Cards.
The Game facilitator is an individual role. They keep time, read the scenario out loud and keep the game running smoothly.
This game requires a minimum of 10 participants and can easily accommodate groups of 30, but to ensure the quality of discussion and time limitations, it is best played with groups of under 20 people. Team size is adjusted depending on the number of participants. See chart below.
| TOTAL PLAYERS | SURVIVORS | ADVISORS | PUBLIC | FACILITATOR |
| 10 | 2 | 2 for each team=4 | 3 | 1 |
| 12 | 2 | 3 for each team=6 | 3 | 1 |
| 14 | 2 | 4 for each team=8 | 3 | 1 |
| 16 | 2 | 4 for each team=8 | 5 | 1 |
| 20 | 2 | 4 for each team=8 | 9 | 1 |
| 30 | 2 | 4 for each team=8 | 18 | 2 |
Cards
There are
- Content Strategy Cards (5 per Advisor; one Content Advisor per Survivor Team)
- Legal Strategy Cards (5 per Advisor; one Legal Advisor per Survivor Team)
- Solidarity Strategy Cards (5 per Advisor; one Solidarity Advisor per Survivor Team)
- Skills Strategy Cards (5 per Advisor; one Skills Advisor per Survivor Team)
- Scenario Cards (6 cards in total)
- Challenge Cards (31 cards in total; 5 per Scenario plus a "Make your own" Challenge card; a list of generic challenge cards can be found below)
- Role Instruction Cards (7 cards in total)

Strategy cards
All games, no matter the scenario will have these Strategy Cards.
Content advisor
- Publish a piece of writing about the experience. Note the title of the piece, where it is published and where it will be distributed.
- Contact the media about the experience. Note which media agencies you would contact and how you’d convince them to cover it.
- Ask feminist bloggers to write about the experience. Note which bloggers you’d suggest and why.
- Respond to attacks on social media. Explain the response, note what hashtag you will use and which communities will be your targets and allies.
- Come up with your own content strategy.
Legal advisor
- Call a lawyer and ask them to file a lawsuit. Note which law/s you will cite.
- Go to the police and file a report. Explain why you think the police can help.
- Document the experience for later legal use. Note what you would document and how.
- Submit an abuse report to a social media platform. Note which platform(s) and the policies that were violated.
- Come up with your own legal strategy.
Solidarity advisor
- Ask people for support. Note what kind of support you want and who you will contact.
- Create a campaign to highlight the abuse. Note the name of the campaign, target(s), allies and at least one action.
- Ask your friends be your social media filter, documenting and deleting or hiding abusive comments from your view so you don’t have to see them.
- Ignore the attack and carry on as usual. Note why this could be effective.
- Come up with your own solidarity strategy.
Skills advisor
- Double check account privacy and security settings. Do you want to hide your friends and photos from public view on Facebook? Have you tried two-step verification for logging into your accounts? Note other steps you’d take.
- Search for information or pictures of yourself online. What terms would you search for?
- Go offline for a while. Under what conditions would this be a good strategy? What are the benefits?
- Report the abusive accounts/content. Note which platform(s) and the policies that were violated.
- Come up with your own skills strategy.
Scenarios + challenge cards
Generic challenge cards
- There is no law in your country against online blackmail, extortion, or threats.
- When you go to report the problem to the police, they tell you there’s nothing they can do until something “real” happens and suggest you just go offline.
- Whoever has it in for you is great at making memes.
- You post screenshots of threats you received, and your social media platform says you violated community standards and temporarily locks you out of your account instead of taking action against the person who threatened you.
- You come from a conservative family and community, and they blame you for what is happening.
- You report the person who is doing this to you on your social media platform and get this reply: “This is not a violation of our community standards.”
- You get reported and locked out of your own account..
- You are queer. But no one in your family and your work place knows about it. If this gets out, you´re in trouble.
- Someone posts private information about you: your address, your location, your work place.
- Nude pictures of you are released on social media.
- Memes to slut and body shame you seem to be everywhere.
- Your photos accompanied by derogatory remarks that attack both your person and your values are circulated.
- Accounts using your name and photos are posting rude, racist, misogynist comments on people’s social media and on your organisation’s page.
- One of your donors/clients followed a fake account thinking it was you, now they are emailing you demanding an explanation.
- Someone has contacted your social media community one by one, sending each follower a link with false information about you.
There are specific Challenge Cards for each scenario.
1. Blackmailed to Go Back
This scenario is taken from here: https://www.takebackthetech.net/know-more/extortion
Scenario Card (printed on a card with copies given to all teams, or projected on the wall, or written on butcher paper)
An ex-partner is threatening to expose your naked pictures on the internet if you don´t get back together with them. You are desperate for a solution.
Challenge cards for Blackmailed to Go Back
- There is no law in your country against blackmail and extortion online.
- Your family and friends are conservative, and will blame you for having nude pictures.
- Your Ex just messaged you. The phone with your pictures was stolen! They’ve lost control over your photos!
- Your photos are released on social media.
- Your Ex´s followers have created memes, using your pictures, to slut and body shame you.
- Blank Challenge: The Public decides what the Challenge is.
2. Trolled on Twitter
Scenario Card (printed on a card with copies given to all teams, or projected on the wall, or written on butcher paper)
You are a feminist activist. You are opposed to the misogynistic and bigoted statements that your current President has made. You appeared in a video that went viral, criticising the President. Now, there is a Twitter mob against you.
Challenge cards for Trolled on Twitter
- Twitter responds to your reports stating there is no violation of community standards.
- You are queer. But no one in your family and your work place knows about it. If this gets out, you´re in trouble.
- Your photos are made into memes with derogatory remarks that attack both your person and your values. They get circulated.
- A local celebrity just re-tweeted a meme against you.
- Someone posts private information about you: Your address, your location, your work place.
- Blank Challenge Card: The Public decides what the Challenge is.
3. Faked on Facebook
Scenario Card (printed on a card with copies given to all teams, or projected on the wall, or written on butcher paper)
Someone is screen-grabbing all of your photos on Facebook, and has created accounts using them, with your name. You don’t know how many accounts there are or why this is happening. And you don’t know how to make it stop.
Challenge cards for Faked on Facebook
- Some of the accounts using your name and photos are posting rude, misogynist, racist comments.
- One of your donors/clients followed a fake account because they thought it was you. Now your donor/client is emailing you demanding an explanation.
- The fake accounts in your name have real information about you.
- A fake account in your name and with your photos is posting obscene photos on your organisation’s Facebook wall.
- You have been locked out of Facebook. You’ve lost access to your Facebook account.
- Blank Challenge Card: The Public decides what the Challenge is.
4. Porn Pretender
Scenario Card (printed on a card with copies given to all teams, or projected on the wall, or written on butcher paper)
You’ve just been informed by a friend that a video with someone that looks a lot like you is circulating on a do-it-yourself porn site with your first name, city and profession, and the number of views is rising.
Challenge cards for Porn Pretender
- The video starts out with you, but the explicit scenes are with someone who only looks like you.
- The site Terms of Service say consent of all subjects must be obtained before uploading. You report the video and say it does not have your consent, but they still haven’t taken it down.
- The video is being picked up and promoted by other porn sites.
- Someone just tweeted your handle with a link to the video.
- Men on the street are leering at you and say they’ve seen your video.
- Blank Challenge Card: The Public decides what the Challenge is.
5. Disinformation to Discredit
Scenario Card (printed on a card with copies given to all teams, or projected on the wall, or written on butcher paper)
Your organisation is well known for using creative strategies to fight misogyny. It works with communities of all ages, including kids. Someone is trying to discredit your organisation and its director. Now if you search for your organisation, the top result is a warning to parents that your director is part of a ring of so-called "sexual deviants".
Challenge cards for Disinformation to Discredit
- Your organisation is known for it’s community trainings, but fewer people are signing up now.
- Someone has contacted your social media community one by one, sending each follower the link with false information.
- One of your donors contacts your organisation to say they are pulling your funding.
- Your director was just paid a visit by the police after they received an anonymous tip about her.
- The lies get picked up by local media.
- Blank Challenge Card: The Public decides what the Challenge is.
6. Watching and Waiting
Scenario Card (printed on a card with copies given to all teams, or projected on the wall, or written on butcher paper)
You are receiving anonymous messages on your phone and social networks. The messages are friendly greetings, but the sender won’t say who they are and seems to know a lot about what you are doing and where you are.
Challenge cards for Watching and Waiting
- Messages are becoming more and more frequent, from one or two a day to a dozen.
- You report the problem to the police, but they say they are only messages, friendly ones at that. If you don’t like them, don’t read them.
- Your office secretary says they talked with your boyfriend and he seemed really nice. You don´t have a boyfriend.
- One of the messages mentions a close family member (your child, sibling or parent).
- The tone of the messages is becoming more aggressive towards you.
- Blank Challenge Card: The Public decides what the Challenge is.

Role instruction cards
Advisors instructions (1 for each team)
Given the Scenario, pick one strategy from your cards or create one of your own. You cannot propose a multi-step strategy. You can only show one option to your team’s Survivor and justify why you think it is a good choice. As a team, you have five minutes to discuss the presented options and help the Survivor make a decision. Your goal is not to have the Survivor pick your strategy, but for the Survivor to be able to argue their preferred choice well enough to get support from the Public.
The Public instructions (1 or 2 if it’s a large group)
Listen carefully to the Scenario and to the Survivor profiles. As Survivor teams decide on a strategy, discuss amongst yourselves who makes up the online public and how these bystanders might affect the Scenario. Once Survivors present their preferred strategy, you can ask them questions. Individually decide which Survivor has the best response to the Scenario and give them your support token (optional), explaining your choice. Then collectively choose a Challenge Card to begin the next round. In the final challenge round, discuss possible conclusions to the Scenario. After Survivors present their final strategies and tokens are counted to see who had more Public support, the Public will present their preferred ending to conclude the game.
Game Facilitator instructions (1)
Game facilitators must be familiar with all game instructions and get the game started by forming the two Survivor/Advisor teams, and the Public. Help the Public choose a good scenario for their context. Keep time: Teams will have 7-10 minutes to decide on a strategy and 5 minutes each to persuasively present their strategy and answer questions. Make sure Survivors are only presenting one strategy at a time. No round should last more than 20 minutes. The game concludes with the Public’s proposed closure to the Scenario, usually after three challenge rounds. End with a reflection on how each team felt during the process. The scenarios and challenges explored in this game could have been experienced by anyone, so it’s important for the Game Facilitator to keep a fun, light atmosphere as much as possible.

Game Play
Playing to “win”
This game is designed to have quick, strategic responses to very difficult and often triggering situations. It was purposefully designed in timed, competitive rounds and to be carried out in a light, swift way to encourage debate and discussion with a degree of distance. A gaming Scenario generates adrenalin and expectation around escalations, both a part of the online GBV experience. An atmosphere of game competition is one way to bring in these elements when strategising.
However, it is important to note that some groups are not comfortable with competition or able to assert that one Survivor Team strategy was better than the other presented, so using tokens as points and declaring a “winner” in your game is entirely optional. The Game Facilitator should decide if they want to introduce competition and tokens before beginning the role-play.
If using tokens, each member of the Public should receive four tokens (in the form of cut-up colored papers, poker chips, individually wrapped candies, stickers, etc.) at the beginning of game play. Each member of the Public will award one token per round to the Survivor Team whose strategy best fit the Survivor profile and context. At the end of three rounds the Public debates; if there is consensus, five extra points can be awarded to the Survivor who has chosen the best overall set of strategies. The total number of tokens will determine which Survivor Team “won” the scenario. The round ends when the Public provides closure to the Scenario with a plausible conclusion.
Facilitation note: When inviting people to play, the Game Facilitator should have alerted possible participants that this role-play will be talking about gender-based violence on the internet and distressing subject matter will come up, in case anyone wants to opt out beforehand. The Facilitator should remind participants of this before starting the game and encourage all participants to be sensitive to each other in the role-play process.
Game setup – 15 minutes
Game Facilitators must be familiar with the following game instructions and make sure teams understand their roles.
Get the game started by forming Survivor Teams A and B and the Public.
- It may be better if the volunteer Survivor has not experienced online GBV themselves.
- There are four types of advisors: Legal, Communications, Solidarity and Skills. The Advisors do not have to be specialists in the area assigned to them (ie legal advisors do not have to be lawyers).
- The Survivor Teams decide who plays what role in the team. That role will last until Scenario rounds are played out. If there are fewer people in the game, Advisors may have to play the role of two advisors.
Give each Survivor Team flipchart paper, markers and the Survivor and Advisor Instructions.
- Their first task is to develop the Survivor profile and context and draw that persona on flipchart paper.
- Remind them they don’t have to think up a scenario, just information about the Survivor:
- How old are they?
- Do they live in a rural or urban area?
- What are their family, friend and work communities like?
- Their sexuality, religion, language?
- Their education level, tech skills?
- Teams have only 5-10 minutes to draw up their Survivor profile.
While Survivor Teams do this, the Game Facilitator gives the Public their instruction cards and briefs them on their role:
- Encourage the Public to think about who is in their midst – are they friends, family, trolls, bystanders,representatives?
- How might bystanders affect the way the Scenario evolves?
- Members of the Public can decide to take on a specific role and react to the Survivor Teams as that role (ie conservative family member, best friend, troll), or as themselves.
The Game Facilitator or Public may choose a Scenario for the game. The available Scenarios are
- Blackmailed to Go Back
- Trolled on Twitter
- Faked on Facebook
- Porn Pretender
- Disinformation to Discredit
- Watching and Waiting
Each Scenario has its own Challenge cards. Alternatively, the Game Facilitator or Public can create one based on their context.
TIP: If creating your own Scenario, keep in mind the Scenario should start at the point that the Survivor is concerned about what is happening, but not already facing a full-blown attack.
Round 1 – 20 minutes
- Survivors present their personas to the Public.
- The Game Facilitator reads the Scenario out loud.
- In their Survivor Teams, each Advisor has 2 minutes to pick one strategy from their deck to recommend to the Survivor. Multi-step strategies are not allowed. Show one option to your team’s Survivor and justify why you think it is a good choice.
- Each Team then has five minutes to discuss the available strategies and help the Survivor make a decision, based on the best option for their Survivor profile.
- The role of the Advisors here is not to get their strategy picked, but for their team to get support from the Public with a persuasive presentation of the strategy chosen by the Survivor.
- Survivors can only pick one strategy at a time, and it is their decision, not the Advisors’.
- While the Survivor Teams discuss for no more than 8-10 minutes, the Public should also be discussing the Scenario and what strategy they think the teams should take. The Public begins to imagine possible ways the Scenario will escalate, and examines Challenge cards.
- Each Survivor presents their first strategy to the Public, arguing why it is the best option for their profile. The Public can ask questions but each Team has a maximum of 5 minutes presentation time.
- The Public provides feedback on the choices. If using tokens, each member of the Public votes, explaining their choice.
Throughout, the Game Facilitator keeps time and tries to keep a fun, light atmosphere as the scenarios and challenges explored in this game could be upsetting for participants if explored too deeply.
Round 2 – 20 minutes
- The Public selects and presents the first Challenge.
- Survivor Teams proceed the same as Round 1.
Round 3 – 20 minutes
- For the Survivor Teams, same as Round 2.
- While the Survivor Teams debate, the Public is asked to come up with a closure to the Scenario. What kind of solution do they foresee as plausible, what strategies would they add? The Game Facilitator, while not encouraging a “happy ending” does ask the Public to look for feasible, and if possible positive solutions to this escalating violence.
- Survivors present their strategies.
- If using tokens, the Public makes a consensus decision as to which Survivor Team had the most coherent set of strategies and as a group awards 5 extra tokens. Each Survivor Team counts tokens to see who “won” the Scenario. If not using tokens the Public will provide feedback.
- The Public presents their proposed solution.
Wrap up – 15 minutes
The Game Facilitator leads a discussion about strategies learned and how participants felt given their assigned roles.

Planning response to online GBV [tactical activity]
This activity is designed to unpack individual, community and movement response to incidents of online violence. For this activity to work, an example of a specific incident of online GBV is required.
Learning objectives this activity responds to
- An understanding of the forms of online online GBV and its impacts on the survivors and their communities.
- An understanding of the continuum of violence between the offline and the online spheres, and the power structures that allow it.
- Ideas, strategies and actions about the ways in which online GBV, especially in their participants´ contexts, can be addressed.
Who is this activity for?
While is activity is can be used for participants who have basic understanding of online GBV, it is more useful for folks that play a role in responding to, or organising such responses, to incidents of online GBV.
Time required
This will require at least 4 hours.
Resources needed for this activity
- Flip chart paper that explains the Mapping responses to online GBV table (see below)
- Written down online GBV examples for each group to refer to
Mechanics
It would be important to have unpacked a specific online GBV scenario with the participants before doing this activity. It is recommended that you do this Tactical Activity after you have done the Deepening Activity: Deconstructing Online GBV. Depending on the size of the group, break them down into smaller groups to plan how to respond to an incident of online GBV.
Present the table to map the response to online GBV incidents. This is a way to prioritise and timeline a variety of responses to online GBV and to have a collective approach to it.
The map has the following elements:
From Time of Incident
In the template, this is broken down into responses in the first week, within the first month, and in 6 months. Depending on the severity and escalation of the incident, this can change with the exception of the responses within the first week since the time of the incident. Some responses go beyond 6 months, especially those where the survivor takes legal and / or advocacy actions. Some kinds of online GBV are resolved quicker than other, so tables for that would not take up to 6 months. The goal here is to timeline actions according to immediate, short-term and medium term.
Individual response
This has to do with the what actions the person experiencing online GBV should take.
Community response
This means the actions that the individual´s friends, organisations, networks and communities will take to help address the online GBV or provide support to the survivor. Some guide questions for this:
- Who is the community around the individual?
- Does the individual have close friends / family they can rely on for support as they deal and recover from the incident?
Movement response
This are the actions that the larger women´s rights and feminist movements can take in response to specific online GBV cases.
Digital security response
These are the actions that the individual and their community will take to safe-guard their online communications, and prevent any more breaches of privacy or escalate the harassment. This could include: securing online spaces and / or devices, reporting incidents to platforms, self-doxxing to know what information is available online about the survivor.
Physical security response
These are the actions that the individual and their community will take in order to safe-guard the individual´s security outside of the internet. This could be preventative tactics and strategies against escalation of online GBV incidents. Or, it cases where the offline GBV already has physical security impacts, this might be corrective tactics.
Well-being response
These are actions that can be taken to ensure that the individual is able to take care of themselves. These are also actions that the community and the movement can take to make sure that the individual under threat is supported.
Advocacy actions
These are actions that can be taken in order to seek redress about the incident beyond just stopping the online GBV. These could include legal actions against perpetrators and / or platforms, or campaigns against online GBV. At the very least, Advocacy Actions documents incidents so that others may learn from it.
Mapping responses to online GBV incidents (with guide questions)
| From Time of Incident | Individual response | Community response | Movement response |
| 1st week | Digital security response | ||
| What does the survivor need to be doing to secure their online communications in the 1st week since the time of the incident? Where did the online GBV happen? What do the platforms allow its users to do to safe-guard their accounts? What information about the individual is available on the internet, and what can they do to take that content down? |
Who can support the individual if they need technical assistance to carry out actions to protect their accounts and communications? Who can support the individual in reporting the incident to the platform? |
Will there be a need for the larger movement to support the individual and their community to report the incident? | |
| Physical security response | |||
| Is information about the individual available online? What can the individual do in order to protect themselves? | What available safe spaces can the community offer? | ||
| Well-being response | |||
| Does the individual need to be offline? Does this individual need a person(s) to support them in monitoring certain platforms? Who provides support and safety for the individual? How will they stay connected to their support resources? What are the ways in which the survivor finds comfort and solace? |
Who in the community will be the support person(s)? | Does the person want others in the movement to know about the incident? | |
| Advocacy actions | |||
| What actions does the individual want to take in order to address the incident? Note: If the individual decides to go the legal route, there needs to be understanding of the national laws / policies within the group, but also the advocacy actions will be far more complicated. |
Who can support the individual in documenting the incident? | Will there be a call for the movement to respond to the incident as it happens? | |
| Within 1 month | Digital security response | ||
| What follow-up digital security tactics and action will the individual take? What changes in practice does the individual need to do in order to further safe-guard themselves? |
What changes within the community´s communication practices need to change in order to protect themselves from further incidents? Are skills and knowledge available within the community in order to implement such changes? If not, who can the community reach out to? |
||
| Physical security response | |||
| What does the individual need in order to have safer living and working conditions? | What changes within the community´s practices need to change in order to protect themselves from further incidents? Are skills and knowledge available within the community in order to implement such changes? If not, who can the community reach out to? |
||
| Well-being response | |||
| Does the individual need professional help in order to deal with the incident? | Do the individual´s main supporters need professional help in order to under deal second-hand trauma? | ||
| Advocacy actions | |||
| For legal response: Has the the incident been reported to the proper authorities? What kind of documentation is required? | What are the opportunities within the community to provide legal support for the individual? | ||
| 6 months | Digital security response | ||
| What needs constant monitoring in the individual´s online activities and communications? | |||
| Physical security response | |||
| Well-being response | |||
| Advocacy actions | |||
| Opportunities and spaces where the incident can be shared in order contribute to the larger documentation of online GBV? | |||
Filling in the table or discussing actions to take at different times at by different actors will be an opportunity to discuss and share strategies and tactics among and with the participants.
If there are multiple groups working on their tables, it is important for the trainer / facilitator to go around to see if there questions and information that needs sharing.
Facilitation Note: It doesn´t have to be a matrix. If you are not spreadsheet type of trainer / facilitator, use another way for the groups to work out actions and strategies to respond to online GBV incidents. If your participants are also not comfortable with tables, then encourage them to strategise using a different methodology. You can use sticky notes to list down the different responses and cluster them into the different types (Digital Security, Well-being, Physical security, Advocacy Actions). The purpose of this activity is to strategise responses and to make sure that the participants are thinking about online GBV response in a more integrated way (rather than just focusing on the digital security actions) and in from a collective perspective (rather than putting all the onus of the response on the individual experiencing online GBV).
To synthesise the activity, focus on the following:
- Learnings about how platforms respond to cases, and what kind of advocacy we need to do in order to make them more responsive to online GBV
- Resources available for activists that groups have not thought of.
- The importance of approaching responding to online GBV from a collective perspective
Facilitator preparation notes
In this session, the facilitator / trainer will need to have more direct interventions about the following:
- basic digital security tactics, safeguarding accounts and devices
- strategies for physical security
- knowledge of the ways in which platforms respond to incidents
- knowledge of legal redress options in the participants´s countries
- knowledge of impact of online GBV on participants´ well being and some strategies to address re-traumatisation of participants
Useful Resource: Hey! Is Your Friend Being Attacked Online?

Meme this! [tactical activity]
This activity is to get participants to respond to more general forms of online misogyny, transphobia and homophobia in a way that uses humour and wit. This is by no means intended to make light of online GBV but rather allow an outlet for participants to collectively deal with trolls on the internet.
Learning objectives this activity responds to
- Ideas, strategies and actions about the ways in which online GBV, especially in their contexts, can be addressed.
Who is this activity for?
This activity can be carried out with participants with different levels of understanding and experience of online GBV
Resources needed for this activity
- Post-its
- Flip chart paper, card
- Lots of markers
If you want to give the participant the option to create gifs: Internet connection and access to Giphy
Time required
This activity will require about 2.5 hours.
Mechanics
This activity happens in three phases:
- Confronting misogynistic / transphobic / homophobic messages
- Counter-messaging (60 minutes)
- Unpacking counter-messages (60 minutes)
With everyone in the same room, ask each participant to share up to three misogynistic /transphobic / homophobic messages they have seen online. Ask them to write down the messages on post-its, one message per post-it.
Note: The message does not have to be blatantly -phobic or sexist, they could be common points that come up all the time (i.e., "you want censorship", "you are limiting my freedom of expression", "if it´s not physical, it´s not real violence" or victim-blaming messages.)
Then on the wall, cluster similar messages. This can be an opportunity to unpack the messages and discuss ways in which they are harmful to women and queer people online.
Once the messages are clustered, group the participants.
Note: Alternatively, if the workshop is pressed for time, you can prepare the messages to create counter messaging against. But this will require you to know what messages the participants encounter most during their time online.
The goal of each group is to create counter messages to the harmful messages. They can use different ways to respond: write Tweets, create posters, create memes, create gifs (depending on the skills in the room), have a hash-tag campaign.
In creating responses, ask the groups to consider the following:
- Who is this message addressed to?
- Why will this message be effective to who is being addressed?
- What values underpin your counter-message?
- What form will it have? What kind of language?
After everyone is ready with their messages, everyone shares what they came up with. Just the messages they created. Collectively, discuss the effectivity of each counter-message based on the considerations above.
To synthesise, focus on the following:
- What kind of messages work
- Lessons learned about responding to trolls online
Facilitator preparation notes
While this activity is a bit more light-hearted than some of the activities in this module, the facilitator / trainer should also prepare for possible moments of stress for the participants.

Mapping digital safety [tactical activity]
This activity is designed to introduce participants to respond to different forms of online GBV.
About this learning activity

This activity is designed to introduce participants to respond to different forms of online GBV. The activity is carried out in three teams, and each team takes on one specific form of online GBV from among:
- Blackmail
- Cyberstalking
- Hate Speech
Each team consists of a facilitator who has a set of Scenario cards and team members who have a set of Rights cards each.
The game begins with the facilitator helping participants reflect on the specific form of online GBV and how it manifests.
After a basic understanding has been established, the facilitator then plays a scenario card, and facilitating a discussion among team members about the scenario. Team members then respond to the scenario collectively by playing one Rights card each to safeguard themselves in the scenario. Members then discuss how the Rights they have selected would be violated in that scenario. The facilitator then moves on to the next Scenario card. Two scenarios can be played out by each team.
If time is available at the end of the activity, teams can gather together to discuss their reflections about their specific forms of online GBV and the related rights that protect them.
Learning objectives this activity responds to
- an understanding of the forms of online gender-based violence (online GBV) and its impacts on the survivors and their communities
- an understanding of the continuum of violence between the offline and the online spheres, and the power structures that allow it
- ideas, strategies and actions about the ways in which online GBV, especially in their contexts, can be addressed
Who is this activity for?
This activity can be used with participants with different levels of understanding about online GBV and the rights stated in the Universal Declaration of Human Rights.
Time required
This activity will require about 2-3 hours.
Resources needed for this activity
- Printed Scenario cards (2 Scenario cards per team)
- Printed Rights cards (6 Rights cards per team member of all teams)
- Space big enough for 3 teams to be able to have discussions
- A table big enough to accommodate the Rights Cards that each team will be presenting per round

Mechanics
Players
The participants will be split into three teams:
- Team A – Discussing Blackmail
- Team B – Discussing Cyber Stalking
- Team C – Discussing Hate Speech
Each team also has a Facilitator. It is suggested that each team be comprised of 6 members and 1 facilitator.
Cards
The members of all three teams have the same deck of printed Rights cards. Each card has the Right printed on the side facing up, and a brief description of the Right facing down. Please refer to the section on Rights for examples of Rights that can be included.
Each facilitator is given 3 sets of Scenario cards specific to the team’s form of online-GBV. Please refer to the section on Scenarios for sample scenarios per team.
Rights
Some of the Rights that can be added to the deck of Rights cards are as follows:
- Right to Freedom of Expression (Article 19, Universal Declaration of Human Rights)
"Everyone has the right to freedom of opinion and expression; this right includes freedom to hold opinions without interference and to seek, receive and impart information and ideas through any media regardless of frontiers."
- Right to Privacy and Freedom from Defamation (Article 12, Universal Declaration of Human Rights)
"No one shall be subjected to arbitrary interference with his privacy, family, home or correspondence, nor to attacks upon his honour and reputation. Everyone has the right to the protection of the law against such interference or attacks."
- Right to Freedom from Violence (United Nations Declaration on the Elimination of Violence Against Women)
"States should condemn violence against women and should not invoke any custom, tradition or religious consideration to avoid their obligations with respect to its elimination. States should pursue by all appropriate means and without delay a policy of eliminating violence against women... [This includes] any act of gender-based violence that results in, or is likely to result in, physical, sexual or psychological harm or suffering to women, including threats of such acts, coercion or arbitrary deprivation of liberty, whether occurring in public or in private life."
- Right to Protect your Artistic Work (Article 27, Universal Declaration of Human Rights)
"Everyone has the right to the protection of the moral and material interests resulting from any scientific, literary or artistic production of which he is the author."
- Right to Work (Article 23, Universal Declaration of Human Rights)
(1) Everyone has the right to work, to free choice of employment, to just and favourable conditions of work and to protection against unemployment... (2) Everyone who works has the right to just and favourable remuneration ensuring for himself and his family an existence worthy of human dignity, and supplemented, if necessary, by other means of social protection...
- Right to Public Participation (Article 27(1), Universal Declaration of Human Rights)
"Everyone has the right freely to participate in the cultural life of the community, to enjoy the arts and to share in scientific advancement and its benefits."
Other Rights from the Universal Declaration of Human Rights may also be added to the deck if deemed necessary.
Scenarios
Please refer to the cartoon strip and section on “How People Experience Blackmail” here for sample scenarios on Blackmail.
Please refer to the cartoon strip and section on “How People Experience Cyberstalking” here for sample scenarios on Cyberstalking.
Please refer to the cartoon strip and section on “How People Experience Hate Speech” here for sample scenarios on Hate Speech.
Game play
Three teams are formed, one to discuss each form of online GBV from among Blackmail, Cyberstalking, and Hate Speech. Each team chooses one facilitator or a facilitator is assigned to them, and the teams with their respective facilitator move to different parts of the room. Each Facilitator is given a deck of Scenario cards specific to their team, and each team member is given a deck of Rights cards. The game is now played in 3 stages, with an optional 4th stage that can be incorporated depending on the availability of time.
Stage I: Brief reflection
The facilitator of each team can use resources from the following links to start a brief reflection session.
This is to establish a brief understanding of the specific form of online GBV before moving on to the next stage of the game involving scenarios. This reflection can be localized for the group, keeping in mind the different identities of members involved. This stage can be shortened or extended based on the experience level of the participants in the group.
Stage II: Scenarios
Once, the group is fairly comfortable with what entails the specific form of online GBV being discussed in the team, the scenario-playing can begin. The facilitator plays a Scenario card which describes a Scenario relating to the form of online-GBV being discussed in the team. The section on Scenarios links to possible sample scenarios for this purpose. The facilitator then asks some questions about this scenario.
For instance, suggested questions for Cyberstalking are:
- Do you think the situation faced by X in the scenario is a case of Cyberstalking?
- What could X have done to avoid this situation? (Please note that this question should NOT be posed in a manner that may assign any blame to the victim of cyberstalking, but in a healthy manner that highlight safe online practices)
- How would you have dealt with the situation if it were you?
The discussion around these questions can be localized to the group.
Stage III: Rights
Once a discussion of the scenarios is completed, the next stage of the game involves the Rights cards held by team members. Team members now collectively decide amongst themselves which Rights cards they want to play to safeguard themselves in the Scenario that has been played out. Each team member plays one Rights card. All the Rights cards played are placed on the table before the facilitator.(As mentioned earlier, it is suggested that this game be played with 6 members per team. However, depending on the actual number of members in the team, either the same card can be repeated by members or each member can play more than one card).
The facilitator now asks the team members details about how the Rights cards played by them would help safeguard themselves in the specific scenario.
This is a good time for the facilitator to ask team members about whether or not there are any local laws that relate to these rights and how they can be (or have been) used in similar scenarios. This discussion can also broaden into pros and cons of using the court system or law enforcement.
Some details of how the Rights relate to these specific forms of online-GBV can be found in the “Related Rights” section of the following links:
The facilitator then moves on to the next scenario card and the process is repeated. It is suggested that two scenarios be played out per team, but more can be added based on the availability of time.
Stage IV (Optional)
This stage is optional, and can be played if there is an availability of time. Once each team has played out Scenarios and Rights in their own groups, the teams can come together to discuss insights from each of their activities.
Some discussion points can include:
- What did we learn about the specific form of online-GBV discussed by our team?
- What are the scenarios we discussed that can arise relating to it?
- What are the rights we discussed can be used to safeguard ourselves in such scenarios?
Facilitator preparation notes
Some guidelines to follow, if you do choose to use this learning activity:
- During the discussion on Scenarios, allow each participant to respond to the scenario in their own way. Don't rush them. Don´t correct their grammar. Don't interrupt them.
- Do not force everyone to respond. Maybe, for some people, being able to write down their responses is preferable. Not everyone needs to respond, but encourage everyone to do so.
- If a participant is triggered, take a break. Don't force them to continue with the activity.
Please read the notes on Holding up a Healthy Conversational Space and Intersectionality and Inclusivity to know more about creating safe, inclusive spaces of discussion.
Here are resources that can help you better prepare for this activity:
Take Back the Tech! has compiled a comprehensive set of resources on each of the forms of online-GBV discussed in this activity. These resources have been cited throughout the activity, and can be referenced here for further details:
- Blackmail: https://www.takebackthetech.net/know-more/blackmail
- Cyberstalking: https://www.takebackthetech.net/know-more/cyberstalking
- Hate Speech: https://www.takebackthetech.net/know-more/hate-speech
Suggested tweaks
This activity is recommended to be carried out as a Tactical Activity. It can also be split into two activities – Stage I can be played separately as a Starter Activity, and Stage II and III together can be played as a Deepening Activity following the Starter Activity.

Resources | Links | Further reading

- What is technology related VAW?
- Forms of Online GBV
- Good questions on technology-related violence
- Cases on women’s experiences of technology-related VAW and their access to justice
- Infographic: Mapping technology-based violence against women - Take Back the Tech! top 8 findings
- TakeBacktheTech's Report Card on Social Media and VAW
- Internet Intermediaries and VAW
- The Vocabulary Primer What You Need for Talking about Sexual Assault and Harassment
Creating safe online spaces
Facilitate learning and building capacity on creating safe online spaces, specifically for at-risk groups and individuals. We **highly recommend** that you choose a Learning Path to travel, as these include activities with different levels of depth that should help participants obtain more insight into the covered subjects.
Introduction and learning objectives
This module is about facilitating learning and building capacity on creating safe online spaces, specifically for at-risk groups and individuals. Through this module you can explore, through activities and discussions, the factors that affect the ability to create spaces where feminist and sexual rights activists and their communities can feel safe. We explore the meaning of such spaces for feminist and sexual rights activists.
Learning objectives
By the end of this module, the participants will:
- Define what they mean by safe/private online space.
- Come up with some strategies to create safe online spaces for themselves and their networks.
- Develop an understanding of privacy issues, and how privacy affects women and their lives.
- Gain an understanding of the privacy limitations of most social media.

Learning activities, learning paths and further reading
This page will guide you through the Module's correct use and understanding. Following the Learning Paths, with activities of varying depth, should allow participants to obtain a better grasp of the studied subjects.
Learning paths
We suggest starting this module with one of the Starter Activities: Unpacking "safe", The bubble, or Develop your internet dream place - in order for the participants to start exploring the concepts. If you want to be more specific, there are starter activities about consent and privacy (Photo social network), cloud storage and data privacy (The Cloud), and consent and device permissions (Visioning + discussion: Settings + permissions). Depending on your group's goals, these will help ground your group in concepts of safety and privacy.
You can use the Develop your internet dream place to work with a group that needs to redesign an existing internet space or design a new one with values of safety and privacy.
Then enhance the group´s grasp of the concepts with the Deepening Activities:
- Online safety "rules" is about articulating how the participants want to safeguard their online spaces, but also an opportunity to clarify the basic principles of online safety.
- Privacy, consent and safety is an open lecture-type activity where the concepts can be further deepened and clarified.
The Tactical Activities are practical hands-on sessions.
- Making online spaces safer is an activity to make the dream places real including addressing challenges of current design and policy of online spaces being at odds with the dream space visions. If you want to get hands-on with online services, this activity provides guidance for analysizing the settings, policies and norms of spaces. It is not a step-by-step guide to adjusting settings as they change too frequently.
- Alternative tools for networking and communications is relevant for participants who want to start moving away from proprietary, commercial and less secure platforms and tools.
Learning activities
Starter activities

- Unpacking "safe" - visioning exercise
- The bubble - visualisation exercise
- Develop your internet dream place
- Photo-social-network
- The cloud
- Visioning + discussion: Settings + permissions
Deepening activities

Tactical activities

Resources | Links | Further reading

Unpacking "safe" - visioning exercise [starter activity]
This is a visioning exercise. The main purpose of the exercise is for participants to express their own definitions of a safe space and look for shared understanding of a safe space. A group might use this as a first exercise in designing new online spaces together or in redesigning an existing one with shared values of safety in mind.
This activity would work well as an ice breaker and as a way of grounding our ideas about safe online spaces in our experience of safe physical spaces.
This activity has three stages:
- Individual visualising time which can be done with words or in drawing.
- Small group discussion about "safe".
- Full group reflection to discuss and identify shared and divergent definitions of "safe" within the group.
It is highly suggested that this activity is followed by Input + Discussion: Privacy, Consent and Safety.
Learning objectives this activity responds to
- Define what they mean by safe/private online space.
Who is this activity for?
This activity can be used with participants with different levels of experience with both online spaces and creating safe spaces.
Time required
This activity will require about 40 minutes.
Resources needed for this activity
- Flip chart paper
- Markers
- Printer-size paper if participants are drawing.
Mechanics
Individual visualisation: 10 minutes
Ask your participants to close their eyes and think about a specific place/time/circumstance in which they felt the safest. Encourage them to be specific in their visualisation – not in terms of the place/time/circumstance, but in thinking about the factors that made them feel safe. This could also be an imaginary place/time/circumstance.
Option: Drawing
This can also be a visualising exercise where you ask participants to draw the place/time/circumstance in which they feel the safest, including the elements and factors that made them feel safe.
Small group discussion: 15 minutes
In small groups of three to five people each, ask participants to share with one another what they have visualised.
Note: For a workshop with six or fewer participants, you can facilitate both discussion steps as a full group. The purpose of using small groups is to ensure that each participant has time to speak about what they have visualised.
Full group: 15 minutes
To process, write "SAFE" in the middle of a sheet of flip chart paper and "mind map" the question: "What was it about the place/time/circumstance that made you feel safe?"
At the end of the exercise, you will have come up with a list of words, phrases and concepts that define "safe".
Notes for the trainer/facilitator
- Look for commonalities in participants' responses but also interrogate differences in their responses.
- Pay attention and highlight factors that can be applied to online spaces, or connect with the basic concepts above.
- Always synthesise key learnings from the activity to reinforce concepts.
Suggested tweak
- Instead of just using a flip chart to mind map the word "SAFE", you can have a co-trainer/facilitator note the words and concepts that the participants are expressing on a notepad or Word document, and as the discussion ends, use a word cloud generator to graphically show the words that define "SAFE".
The bubble - visualisation exercise [starter activity]
This is a visualising exercise. The purpose of this exercise is to facilitate discussion about privacy and for the trainer and participants to understand varying concerns about privacy in the room.
This activity is not meant to deepen awareness of privacy, but rather have the participants reflecting on their individual notions of privacy.
This activity should be paired with either Making Online Spaces Safer or Input + Discussion: Privacy, Consent and Safety.
Learning objectives this activity responds to
- Develop an understanding of privacy issues, and how privacy affects women and their lives.
Who is this activity for?
This activity can be used with participants with different levels of experience with privacy issues online and offline.
Time required
This activity will require about 40 minutes.
Resources needed for this activity
- Flip chart paper
- Markers
- Small-sized post it notes
Mechanics
This is a visualising exercise. Participants will be given flip chart paper and markers to draw.
Individual visualisation - 30 minutes
If your are comfortable, close your eyes. Imagine a dot of bright light. Is it still, is it moving? How does it move? Now, imagine a circle around this dot. And now imagine both are moving, and the dot remains in the circle the whole time. You are both yourself, the dot, and your boundaries, the circle. How does it feel to be in this? This is a visualization of you inside of boundaries that are safe for you.
First, ask participants to draw an avatar of themselves in a circle in the centre of the paper.
The circle represents their individual bubble of privacy.
There are things inside and outside of the bubble.
On post-it notes, one concept per note, ask them to put the things that they keep most private and people they share the most private things with inside their bubble, and to place things they consider public outside of their bubble.
These things could include:
- people that they share things with
- information about themselves
- feelings that they have
- their activities
A sample of what this could look like:
After they do the first circle, ask them to draw another circle, and then re-arrange the post-its according the levels of sharing of information that they want to have among different people.
This could look like this:
The lastly, ask them to draw another circle, closer to their avatar and think about the things that they would never share with anyone, and put those in that circle.
Full Group Debrief - 25 minutes
To process, ask the participants about the exercise and the reflections/insights that they had as they were drawing.
Ask them how they decided who was inside and outside their bubbles, and about the proximity of those outside the bubble to their bubbles.
Reflect on how their individual bubbles relate to creating safe spaces for themselves – online and offline.
Some guide questions for the debrief:
- How did each participant group the people and things inside and outside their bubbles?
- Was there a need to have more than 3 bubbles? Why?
- What were their insights around the responsibilities that they deal with, the emotions/feelings they have, and the things that they want to express? Was there a difference? Did their drawings show that difference?
- Have any of the participants ever experienced being forced to take a person/an emotion/an issue out of their bubbles? How did that happen? How did they deal with it? Were they able to put those things back in their bubbles?
- Of the things in your images, which things do you communicate about and which people do you communicate with in online spaces? Discuss.
Facilitation Note: Do not comment on the participants' bubbles and where their information/feelings/thoughts in. Do not encourage that kind of behaviour among the rest of the participants as well. Little things like gasping in surprise, raising an eyebrow, or laughing when some is sharing their bubble does not create a safe environment for the participants.
Develop your internet dream place [starter activity]
In this activity, participants consider elements of an online space where their community can thrive. Depending on the goals of the group and workshop, facilitators can prompt participants to consider possible activities and ways of being in online spaces.
This is a visioning exercise and can lead into a discussion about the online spaces where participants are most often and the possibilities and limitations of using these platforms in alignment with the ideal space they have envisioned.
Learning objective this activity responds to
- Come up with some strategies to create safe online spaces for themselves and their networks.
Who is this activity for?
This activity is for people who participate in online spaces. It may be a good activity for a group to address redesigning a space that is not currently serving the group, or for a group who is establishing new online spaces together.
Time required
Total suggested time for a standard workshop with 12-15 participants: 2.5 hours
- 30 minutes for discussion on Why are we online? Why is it important to us?
- 45 minutes minutes for the group work
- 30 minutes for the presentations (4-5 groups at 5-6 minutes each)
- 45 minutes for debriefing and plenary discussion.
Resources needed for this activity
- Flip chart paper
- Markers
Mechanics
Discussion: Why are we online? Why is it important to us?
Because we will be looking at the many ways that the internet is not designed for our safety or privacy, ground this conversation in the reasons participants are online. If you are familiar with the group already, you may be able to give examples of the work they are doing online. If you are less familiar with the group, ask the participants for examples of things they are doing online that are significant to them.
Make space for discussion about different facets of people's lives.
Some guide questions for this discussion:
- What spaces do you use online? What for?
- What are the limitations of the spaces that you use? It would be a good idea to tackle this per platform.
- Have there been incidents when you felt unsafe in the spaces that you use? Again, tackle this per platform / tool.
- Are you using different spaces for different aspects of your lives? How? And how do you decide which ones to use for which.
Facilitation Note: It is a good idea to stress the point that the internet dream space is for personal and political / activist work. So, depending on how the participants are responding to the guide questions, challenge them to think about their personal and their activist work and their use of the internet.
Write down the highlights of the discussion.
Small group activity
With the discussion in mind, form small groups (3–5 participants) to develop their internet dream place.
During the small group discussion, ask them to reflect upon and answer the following questions:
- What is it called?
- Why is this space significant?
- Who is it for? Who is it not for? How can you make sure?
- What kinds of things do people do in this space?
- What are the rules in this place?
- Who can join? Who cannot join?
- What will the space look like?
- How will people find each other in this place?
- What topics can people talk about in this place? What can they not talk about?
- Who has responsibility for managing the space?
Have the groups draw out this space as creatively as possible, and get them to prepare a creative presentation for the rest of the group.
To process the presentations, have the other participants ask clarification questions after the presentations, and list down more strategic/ethical/substantive questions, and hold those off until after all the groups have presented their ideas.
Debrief
To end this learning activity, discuss the following:
- What are critical things to consider when designing safe spaces (go back to the insights from the Shareback).
- Safe for whom? Ourselves, but we are also part of others. So where are the potential moments where we have to care for our own safety as well as others and vice versa (you might want to check out Online Safety Rules for reference).
- What are some limitations to this online space? Can a space be totally “safe”? What may result in a shift in safety?
- In understanding #3, bring home the point that we need to understand who has control over the shaping of a space and how, how the space works, where the space is embedded within other spaces (link also between online and offline), and if safe spaces are important to us, how we can strategise/design them more consciously in our activism?
Notes for the facilitator
- Ask questions around other considerations in creating safe online spaces:
- Who are the ones that will threaten the safety of this space? Internally and externally? How can they protect the space?
- Where are the spaces hosted (i.e. national laws have an impact on whether or not these spaces can even exist, as well as redress if the space is abused)?
- Are there legal considerations in creating such a space for the target group?
- What are the responsibilities and liabilities of social media platforms when things go wrong? What are they in reality? And what should they be? You might want to read up on the Manila Principles on Intermediary Liability.
- What are the international and national human rights standards on privacy? What are the legal privacy considerations?
- This could directly lead to an input/lecture on the principles of online safety, or a lecture on the privacy issues in social media.
Photo-social-network [starter activity]
This is a visualization activity. The purpose of this activity is to get participants thinking about online consent and data privacy through the medium of permissions and terms of services on the apps they use.
Learning objectives this activity responds to
- understand a feminist perspective in the digital space about
- meaningful / informed consent
- full control over personal data and information online
Who is this activity for?
This activity can be used with participants with different levels of experience with consent and privacy issues online and offline, preferably with access to a device with which they connect to the internet.
Time required
45 minutes, including set up and debrief.
Resources needed for this activity
- Flipchart with activity scenario written/printed on it
- Post-its
- Markers
Mechanics
This is a visualising exercise. Participants will be given post-its and markers to write.
Individual visualization - 15 minutes
First, read out the scenario from the flipchart as follows:
"Say you were the inventor / owner of a popular new photo-based social network (like Instagram). You make money by offering users the ability to advertise their posts to targeted users based on age, location, interest. To operate, you need access to the users' photo gallery. What permissions would you ask for, and what terms of service would you provide information about?"
You could ask the participants to reflect on the following aspects:
- Ownership and retention of the uploaded photos
- Access the users' photo gallery
- Using user data for advertising
Full Group Debrief - 25 minutes
To process, ask them about the exercise and reflections/insights that they have as they were writing.
Some guide questions for the debrief:
- What permissions would you ask for?
- What are some of the terms of services you would offer?
- Who would own the uploaded photos?
- Where would the uploaded photos be stored?
- How would you ask for consent to access the users' photo gallery?
- How would you use this data for advertising?
- Do you think there is a connection between how such online consent works and offline consent?
You can then reflect upon their responses and discuss them with the group.
The cloud [starter activity]
This is a visualization activity. The purpose of this activity is to facilitate discussion about cloud storage and data privacy. This activity is not meant to deepen awareness of privacy, but rather have the participants reflecting on their individual notions of privacy on the cloud.
Learning objectives this activity responds to
- to understand a feminist perspective in the digital space about full control over personal data and information online
Who is this activity for?
This activity can be used with participants with different levels of experience with privacy issues relating to the cloud.
Time required
45 minutes
Resources needed for this activity
- Sheets of blank A4 paper for drawing
- Markers
Mechanics
This is a visualization exercise on how the cloud works. Participants will be given paper and markers to draw.
Individual visualization - 15 minutes
Ask the participants to visualize the cloud as a physical space and draw the space on their papers. You could ask them to reflect on the following:
- How does the space look?
- Who is controlling this space?
- Can you see what is happening inside the space?
- Can you and your community audit/test the space?
Full Group Debrief - 25 minutes
To process, ask them about the exercise and reflections/insights that they had as they were drawing.
Some guide questions for the debrief are:
- How did each participant visualize the bubble to look like?
- Who was controlling the entrance to your space?
- Based on how much of the space was accessible to you, is your cloud proprietary or open-source?
- What would be the difference between proprietary and open-source cloud storage?
- Which kind of cloud storage would you prefer and why?
You can then reflect upon their responses and discuss them with the group.
Visioning + discussion: Settings + permissions [starter activity]
This is a visualising and discussion exercise. The purpose of this exercise is to facilitate discussion about online consent, device settings, and permissions. It can also help participants to understand varying concerns about consent on their personal devices.
Learning objectives this activity responds to
- Understand a feminist perspective in the digital space about
- meaningful / informed consent
- full control over personal data and information online
- to learn practices of control over one’s digital persona
Who is this activity for?
This activity can be used with participants with different levels of experience with consent and privacy issues online and offline, preferably with access to a device with which they connect to the internet.
Time required
This activity will require about 1.5 hours
Resources needed for this activity
- Post-its for writing
- Sheets of blank A4 paper for drawing
- Markers for writing and drawing
Mechanics
This is a visualizing and discussion exercise. Participants will be given post-its and markers to write and draw.
Individual Visualization - 30 minutes
First, ask participants which device they use to access the internet (mobiles, tablets, personal computers, desktop at work/home/other public spaces etc.). Then tell your participants to think of and write down on post-its the first three activities they consented on their mobile, regardless for which apps.
Following this, on sheets of blank paper, ask them to draw their mobile. Then ask them to identify which operative system their device uses. Finally, ask them to write down (in the drawing of the mobile outline) 5 apps they use the most, verify permissions granted to those apps, and write them down next to each of the applications.
Full Group Discussion - 1 hour
Once all participants have visualized these details, ask them to share with one another what they have visualized. Some apps (such as WhatsApp, Facebook, Twitter, Google Maps etc.) are commonly used by many people, so you may find commonalities in the responses. Look for commonalities in participant's responses but also interrogate differences in their responses.
Note: If there are more than 6 participants, you can optionally make smaller groups of 6 each to ensure that each participant has time to speak about what they have visualized.
You can then facilitate the discussion with some questions such as:
- What device did you draw?
- Does your device connect to the internet?
- If your device is a phone, is it a feature phone or a smartphone?
- What Operating System does your device use? (example: Android, iOS, Windows etc.)
- Is your Operating System open source or closed source?
- What is your device’s manufacturer?
Before going into questions on settings and permissions, you can explain:
"Since smartphones offer even more functionality and options than feature phones, the amount of information that can be observed and logged is far greater. In addition, smartphone users are sharing that very detailed identifying information about themselves and their usage to far more companies than just their mobile network operator - every app you choose to install can also send selected data about your usage, call times, contacts, and data use to whomever makes that app.
What an app can see and log is often set by the app designer, but there are very few laws and regulations constraining what they can design their app for. Similarly, the operating system and manufacturer of a smartphone has implications on where your data goes and who can see it aside from your mobile network operator." Source
Once this basic understanding has been established, you can lead to more detailed discussion on device settings and permissions. Some guide questions for the discussion:
- What are some features of your phone that your chosen apps can access? (example: camera, microphone, location etc.)
- Why do you think these apps require this information?
- Did you consent to this information being shared?
- Do you think there is a link between offline consent and such online consent?
- Where do you think this information goes?
- Do you think this information is protected?
You can refer to the following for some basic information to guide the discussion:
"Android devices share a massive amount of user data with Google, since their operating system is deeply entwined with a user’s Google account. If you use Google services and apps as well as an Android-powered smartphone, Google knows an overwhelming amount of information about you – possibly more than you’d realize about yourself, since they log and analyze that data.
Similarly, iPhones (using iOS as their operating system) provide a similar amount of information about users to Apple, which can be combined with a user’s data if they use other Apple products and services. In addition, iPhone and Apple are highly proprietary and their software and hardware are closed source. This includes the iPhone itself, as well as the Apple apps that run on it; in comparison, Android is open source, which allows everyone to review their code and know what the Android does.
Smartphones are able to use GPS (Global Positioning System) satellites in addition to the approximate location triangulation of mobile network towers can provide. This gives far more detailed location data to operators and to any apps who have access to that information. This more precise location can be attached, along with the date and other information, to any pieces of data that the phone collects to post online or store on its memory." Source
Input + discussion: Privacy, consent and safety [deepening activity]
This learning activity is about the trainer/facilitator giving input and facilitating a discussion on the issues relating to privacy, consent and safety.
About this learning activity
This learning activity is about the trainer/facilitator giving input and facilitating a discussion on the issues relating to privacy, consent and safety.
We suggest that you use this learning activity to cap the other learning activities such as: Unpacking "Safe" or The Bubble.
Learning objective this activity responds to
- Develop an understanding of privacy issues, and how privacy affects women and their lives.
Who is this activity for?
This activity can be used with participants with different levels of experience with both online space and creating safe spaces. Of course, if the participants have only a very basic understanding of feminist concepts such as agency and consent, then the trainer/facilitator will need to clarify those terms at the beginning of the input and discussion.
Time required
Minimum of 40 minutes.
Resources needed for this activity
- Flip chart paper or white board
- Markers
The trainer/facilitator can also opt to use a presentation for this activity.
Mechanics
If Unpacking "safe" or The bubble have already been done, use the insights from those activities to launch into defining privacy. Specifically:
- Draw from the the definitions of safety/safe that came from the activities that can be connected to privacy and consent issues.
- Key concepts raised during the prior learning activity that either need to be stressed/reiterated or further clarified (this is an opportunity to clarify notions/ideas that are against feminist values on privacy, consent and safety).
- Experiences shared in the prior activity that highlight the connections between privacy, consent and safety.
Unpacking consent and privacy
Key points to be raised in this input and discussion.
Unpacking "consent"
We tend to think of consent as a one-off thing. Like signing a piece of paper once and then it is set. However, from experience we know that consent is simple yet complex at the same time. Simple in its principle yet complex in its implications. Here are some things to discuss:
- Duration of consent.
- Ability to withdraw consent, what it means for a user to withdraw consent and their use of the platform or tool
- The data / information about the user that they cede when they consent to services
- How is that data used
- Conditions of consent – being able to consent only under certain circumstances and not others.
Watch the video Tea and Consent.
Show this graphic:
The facilitator can focus a few scenarios to highlight the points:
- Agreeing to the Terms of Service in proprietary, commercial platforms in order to be able to use that platform.
- Emergency scenarios where we consent to allow others to control our spaces / devices in order to safeguard it. How to we ensure that this conditional consent is temporary? Perhaps use the example of Facebook Trusted Friends as a way to highlight this point.
- Events that ask participants to sign-in at the door – what does that mean as far as consent goes?
- Sharing a password to a loved one as an act of intimacy and trust. What are the implications of this?
- Ask the participants for examples of situations where they had given their consent to different platforms or services.
Unpacking "privacy"
Key points for this input can include:
The different dimensions of privacy:
Territorial/spatial
- Why do we lock our doors? Which doors do we lock?
- How do we protect our spaces and why?
- Why do we close the door when we pee? When everyone does it?
Relational
- Do we protect the privacy of the people that we know? Who of them?
- Do we violate the privacy of our relatives, friends, colleagues when we talk about them?
Embodied
- Which parts of your body do you choose to disclose? When you pick what clothes to wear, and depending on who will see you (gaze as violation of privacy)?
- Embodiment online. Self-representation online. From simple things like user pics, to carefully crafted identities, to other kinds of information that reveals things about our bodies (health/medical/sexuality/gender). And how this also translates body as data.
Data privacy
- What data do we willingly cede about ourselves and others?
- Are we able to give consent to the collection, storage and aggregation of our data?
- How about the data about us that is collected, stored and aggregated without our consent?
Defining privacy
- Defining privacy as a fundamental human right, and why it is important for women.
- How privacy has been defined in policy (could be national, regional and international policy), and what that means for individuals, WHRDs and women.
- How privacy plays out on the internet: how social media has seemed to redefine privacy both in individual practice and the platform's use of users' data.
- How the internet – and how its being used and developed now – is challenging how we practise privacy.
- The relationship between privacy and consent.
Discussion questions
- When do we "forfeit" our right to privacy? For example: Does anonymity facilitate online harassment and GBV?
- How critical is the relationship between anonymity and privacy and safety?
- In the age of selfies and when people willingly cede information about themselves and others, is privacy dead?
- Technically, how would privacy-by-default work on the internet? What kind of changes would platforms like Facebook need to make to have privacy-by-default? (We could develop an activity around this in the future.)
Facilitator preparation notes
While this learning activity has the trainer/facilitator doing most of the speaking, it is also important to reiterate the safe, open and interactive space that all FTX workshops try to create. This can be done by framing this activity with guidelines that allow participants to raise their hands to ask questions or to argue or to stress or clarify a point being made in the presentation. The other way to encourage interactivity during presentation-style learning activities is to "popcorn" topics – ask a question to the group to start a topic, and then use their answers to launch a presentation/input.
In order to prepare for this learning activity, the trainer/facilitator will need to brush up on the following:
- The state of play on privacy issues – policies, trends, recent cases.
- Context-based understanding of privacy: current laws in the location of the workshop or the participants, recent cases relevant to the participants.
- Feminist Principles of the Internet
Additional resources
- Feminist Principles of the Internet
- "Neutral" definition of Consent (Merriam-Webster)
- "Neutral" definition of Consent (Wikipedia)
- "Neutral" definition of privacy (Merriam-Webster)
- "Neutral" definition of privacy (Wikipedia)
- Privacy and EDRI
- Three key issues for a feminist internet: Access, agency and movements
- A feminist internet and its reflection on privacy, security, policy and violence against Women
- GISWatch 2015: Sexual rights and the internet & Full report
- GISWatch 2013: Women’s rights, gender and ICTs & Report
- How much control do we have over our data?
- Establishing a baseline of privacy and security knowledge
- What privacy & anonymity have to do with tech-related VAW
- Invasion of Privacy & The Murder of Qandeel Baloch - By Digital Rights Foundation
- Peeping Tom Porn and Privacy - By Rohini Lakshané
- Mapping and privacy: Interview with Privacy International's Gus Hosein
- The ability to say NO on the Internet
Input + activity: Online safety "rules" [deepening activity]
This learning activity is about sharing basic principles of online safety, and having the participants articulate personal or organisational policies to safeguard their online safety.
This activity can be done after Input + discussion: Privacy, consent and safety or Develop your internet dream place, and be the basis for Making online spaces safer.
There are three main parts to this learning activity:
- Input on the basic principles of online safety
- Reflection on communication practices
- Articulating "online safety rules".
Learning objective this activity responds to
- Come up with some strategies to create safe online spaces for themselves and their networks.
Who is this activity for?
Participants with differing levels of experience. However, note that participants with more experience with digital security might find this too basic.
Time required
105 minutes total (1 hour, 45 minutes):
- Input on Basic Principles of Online Safety (15 minutes)
- Activity on Communication Practices (30 minutes)
- Input on Areas of Consideration for Online Safety (20 minutes)
- Activity on Articulating "Online Safety Rules" (30 minutes)
- Debrief/Synthesis (10 minutes)
Resources needed for this activity
- Flip chart paper or white board
- Markers
- Printer paper
Mechanics
Start with listing down the Basic Principles of Online Safety (see Additional Resources)
Note: It would be good to refer to examples that were shared in previous learning activities as you expound the principles.
Then move on to having the participants reflect on their communication practices by having them individually fill in this form (filled out a sample). To frame this, and to not conflate this activity, ask the participants to think about the last 24 hours and who they communicated with and what they communicated about.
| Who do you communicate with | What topics you communicate about | Is the communication private? | Communication channels |
| Mother | My current trip | Yes | Facebook messenger |
| Kartika | Details of current work | Yes | Email, Telegram, Facebook messenger |
| Lisa | Event with them next month | Yes | |
| Marina | Dinner with him next week | Yes | SMS |
| About how Trump sucks | No | Facebook group | |
| Feminist principles of technology | No | Personal blog |
Intersectionality Note: The names on the table are suggested names. You can change those names to fit in more common names in your country or context.
The starting point can be the people they communicated with, or the topics they communicated about in the last 24 hours.
After getting the participants to fill in their individual forms, have them reflect on the following questions:
- Of the communications that they had done in the last 24 hours, which of these do they think they should be securing the most?
- Of the communications that they have done in the last 24 hours, which one causes the most stress? Why?
Then move on to presenting the Areas to consider in online safety (see Additional Resources).
After, ask the participants to reflect on the areas to consider and write down their personal "online safety rules" based on this template:
- Which topics that you communicate about are private, and which are public?
- Who do you communicate with, and what about?
- Who are you permitting to have access to your communication channels?
- Which communication channel or device are you limiting access of others to?
Note: These rules are draft rules and are personal to each participant. It is important to frame this activity this way, and keep on reiterating the Basic Principles of Online Safety.
After the participants have written down their "online safety rules", debrief on the activity:
- Insights on your communication practices?
- Any concerns that were raised because of this activity?
- What else needs to be clarified?
It is suggested that you then move on to Making online spaces safer.
Facilitator preparation notes
You might want to read this piece from Level Up: Roles and responsibilities of a digital security trainer to mentally prepare for this activity.
Additional resources
Basic principles of online safety
- The idea of perfect online safety is false. The security and safety scenario is contextual – it changes over time. What is safe today may not be safe tomorrow.
- Online safety must always be end-to-end. You are only as secure as the least secure person you communicate with, or the least secure platform you use.
- Online safety will always entail a combination of strategies, behaviour and tools. Merely installing security apps does not equal being safe online, especially if you have un-secure communication practice and behaviour.
Facilitation Note: These may seem sanctimonious and might cause participants to feel paranoid about their safety. One way to go about this, as a feminist trainer, is to give examples that are personal to you and your experience. This way, the participants will not see you as someone who will judge them for their communication and digital security choices.
Areas to consider in online safety
These are areas the participants should be considering when they think about their online safety.
Who you communicate with and what you communicate with them about
- What topics do you talk about with the different people you communicate with?
- Are any of the topics you communicate about sensitive? How so? What are they?
- Are any of the people you communicate with at risk? Have they experienced surveillance? Is the work that they are doing a threat to someone with power?
- Are you at risk? Have you experienced surveillance?
What you use to communicate
- What platforms do you use? Do you know where they are hosted?
- What devices do you have?
- Do you use different devices for different people? Do you differentiate devices based on the public or private nature of your communications?
- Who has access to these communication channels? Are they shared?
Your specific context, capacity and risk
- Are there laws in your country that threaten your online safety as an individual? What are they, and how do they do this?
- Have there been examples of cases where individuals in your context (define that as you will) have had their online safety compromised? How?
- Have you ever experienced surveillance? From whom?
- Search yourself. Is there any information there that you don't want out in the public? Why?
- How do you safeguard your communication channels? Do you have passwords for each device and communication channel?
Making online spaces safer [tactical activity]
The goal of this activity is to go through the privacy options for accounts and groups of the agreed-upon (i.e. commonly used in the group) social media sites.
If you want to get hands-on with online services, this activity provides guidance for analyzing the settings, policies, and norms of online spaces.
About this learning activity
The goal of this activity is to go through the privacy options for accounts and groups of the agreed-upon (i.e. commonly used in the group) social media sites. For groups who have gone through the exercise Develop Your Internet Dream Place, this is an activity to make the dream places real, including addressing challenges of current design and policy of online spaces being at odds with the dream space visions. For groups who already have online spaces and want to alter them to make them feel more safe, you can also use this activity.
If you want to get hands-on with online services, this activity provides guidance for analysing the settings, policies and norms of online spaces. It is not a step-by-step guide to adjusting settings, as they change too frequently.
Learning objectives this activity responds to
- Come up with some strategies to create safe online spaces for themselves and their networks.
- Gain an understanding of the privacy limitations of most social media.
Who is this activity for?
This activity can be used with participants with different levels of experience with both online spaces and creating safe spaces. Participants will be asked to explore and set privacy settings in the tools they are using.
Time required
This activity will require about 3 hours.
Resources needed for this activity
- A soft-copy of the planning tables.
- Computers for people to work on their plans on
Mechanics
1. Map your space
Developing new spaces: If you have done Develop Your Internet Dream Place, you can use the work from that exercise as your map.
Redesigning existing spaces: If your group would rather redesign an existing online space, identify a space that the group already participates in or ask the participants to form groups based on spaces they participate in and facilitate the group(s) to answer the questions from Develop Your Internet Dream Place, about these existing spaces:
- What is it called?
- Why is this space significant?
- Who is it for? Who is it not for? How can you make sure?
- What kinds of things do people do in this space?
- What are the rules in this place?
- Who can join? Who cannot join?
- What will the space look like?
- How will people find each other in that place?
- What topics can people talk about in this place? What can they not talk about?
- Who has responsibility for managing the space?
Have the groups draw out this space as creatively as possible, and get them to prepare a creative presentation for the rest of the group.
2. Choosing spaces: Spaces that work and assessing safety
If you have done Input + activity: Online safety "rules", you may have already had a conversation about choosing spaces and assessing risks of online communications.
Choosing spaces for functionality
How do you choose platforms and assess risks to yourselves on those platforms? Choose spaces that help us reach our communication goals and try to participate in these spaces in ways that do not expose us to risks we do not wish to take.
Look at the map you have made. Can you identify a platform already that will allow you to create the space you have mapped? Which of the components of your space will be easy to create? Which will be difficult? Are there alternative spaces where pieces will be easier or harder?
Choosing spaces strategically
Does the space you chose match your strategy? Is this a good space for: organising, mobilising, for announcements/influencing discourse?
Facilitator: Introduce how these different activities bring with them different levels of risk.
Suggested questions to ask
- What are some risks with different types of communication?
- Who are you communicating with in these activities?
- Who are you not communicating with?
- What are the consequences if someone you do not intend your message for accesses it?
- How public can the audience be?
- What risks might people face if they are known as message creators or recipients in this communication?
This discussion leads into the next discussion section looking at risks people are most concerned with.
Note to facilitator: This section may be very quick, with everyone agreeing that they need to be on a single platform right now, for instance, Facebook. You may, however, get to talk about a variety of tools and platforms.
Discussion OR Input: Assessing dimensions of safety and the internet: What are the current issues?
Ask the group: What safety risks are you concerned about in online spaces? Facilitate this discussion to include concerns about actions that individuals can take in these spaces as well as actions taken by the software companies who own the spaces.
If you have already done Input + activity: Online safety "rules", you may reference that discussion and abbreviate this section.
Otherwise, facilitate discussion about safety risks in online spaces. Draw from the experiences of the participants but also prepare some examples of stories where privacy was breached through online spaces and that impact that had on individuals.
Discussion: Ask participants what safety concerns they have in online spaces. Are there any specific incidents or risks people are concerned about and want to address in their Dream Space or redesigned space?
Input: We suggest familiarising yourself with 2-3 case studies and sharing them here. To share these with the least amount of time, present them as a lecture. If you have more time, or want to facilitate deeper conversation and engagement with the issues, find some media like articles, short videos, interviews, regarding a case and share them with the group. Ask group members to discuss them together in pairs or small groups.
- Real name policies and their implications for organising and expression online.
- The myth that to be online is to be anonymous and therefore safe – laws and policies that don't allow for this.
- Women's experience of the internet – harassment, attacks, etc.
- The value of the internet; why do people stay in online space; how is it of value to us and our community?
- Diversity of access and comfort level of online spaces that we choose. Is it a barrier for people in our networks to participate because you´ve chosen a specifc platform?
- Are there cost implications for the space that you are choosing to use for the people in your network community?
Facilitator: ask participants to consider why the platforms we are on are not safer by design.
3. Make a plan: Address the risks of the spaces that you are using
Using the Dream Spaces or Redesigned Spaces as examples, have the participants make plans for implementing this space online.
This would be most useful if they have active spaces they want to secure and safeguard.
Issues to consider here:
- Privacy settings on social media – is it enough? What are the limitation of available settings?
- Considering moving to non-commercial spaces – what are the barriers?
- Safer options for online communications – tools that offer encryption by default.
| Consideration | Platform or Space | How will you address this |
| Who can see what | Twitter (this is an example) | Review my privacy settings; consider content that I post, respond to, like, and the default privacy settings on different types of content; reduce the number people I'm linked to; prohibit tagging |
| Do you know everyone you're linked to | review my connections; remove connections to people I do not know; | |
| Do you want to use your real name; anonymity and how hard it is | use a pseudonym; prevent others from naming you with your real name | |
| Do you want to share your location | No, I do not want to automatically share my location; turn off location services; limit photo posts showing my location |
| Consideration | Platform or Space | How will you address this |
| Ensuring that I am logging out | f-book | do not save password in browser; review setting on f-book for automatic logout |
| 2-factor on accounts and devices | set up 2-factor to be more certain that only I am logging in | |
| Shared accounts | review who has access to shared accounts; review password policies on these accounts |
Devices
| Consideration | Platform or Space | How will you address this |
| Device-level safety | Twitter or any app | do not automatically log in to any apps or through browsers |
| Do I want notifications to show on my devices | turn off audio and visual notifications |
Group Administration
If you are working with a group to implement a space online, use the following table of questions and work through the answers, finding the appropriate settings on the platform you are using to implement the group's preferences.
Example design/implementation table:
| Link to Group or Personal Page | https://www.facebook.com/APCNews | What are you doing to implement this? |
| Who can see this space? | anyone on the internet | our group is public on Facebook and searchable on the web |
| Who is this space for? | APC members, community and potential APC members | we invite APC staff and network members to join, mention them in posts, invite them to events posted through this page |
| Who is it not for? | APC members, community and potential APC members | closed/public - we limit who can post, but make the page findable on facebook and through web searches |
| What kinds of things do people do in this space? | notifications about APC work and links to APC network content published elsewhere | |
| Who can create content in this space? What kind of content? | staff and members | - |
| How do you want to communicate the rules of the space? | on our group's about page | we will write our rules based on this chart of questions and answers and post it on our about page |
Well-being Note: Bringing up risk and technology concepts might cause participants stress. Be aware of this. Pause for a breathing exercise. Or allow participants to take a walk around the venue to decompress when they need to.
Additional resources
- If you want to spend more time discussing tools and choices, there are a lot of great resources here: https://myshadow.org/.
- How to Increase Your Privacy on Twitter
- Security in a Box: Social networking
- Protect the privacy of your online communication
- Create and maintain strong passwords
Alternative tools for networking and communications [tactical activity]
This learning activity is mostly guided hands-on for individuals and groups to start using alternative tools to "free" proprietary services.
This activity is most effective when the participants are part of the network so they are able to start developing new ways of communicating among each other.
This activity will focus on three communication tools that are commonly used: Email, chat apps, and alternatives to Google docs.
Learning objectives this activity responds to
- Come up with some strategies to create safe online spaces for themselves and their networks.
Who is this activity for?
This can be run with participants with varying skill levels in using online tools.
Time required
To complete this, you will probably need at least 5 hours.
Resources needed for this activity
- Internet connection
- Laptops
- Mobile phones
- Projector
Mechanics
The point of this activity is to encourage your participants to be less reliant on commercial services that breach users privacy and security.
Protonmail hands-on
Why Protonmail?
- Non-commercial
- Hosted in Switzerland with strong data protection
- Has strong privacy policies about user data
- Offers end-to-end encryption by default (depending on the experience of the group, you might need to do explain this). By default, they employ encryption at-rest. Emails are stored encrypted on their servers – which means the people who own Protonmail will not be able to read your emails (different from the Google model where they focus on encryption in-transit only – messages are encrypted while it is being sent, but once it gets to their servers, they have the means to ¨un-lock¨ your emails). This might need some differentiation between HTTPS and GPG to explain.
- Will allow users to send password-protected emails between different email services (i.e., a Proton user can send password-protect emails to a Gmail user, and the using that same message send a password-protect email back)
- You can opt to have self-destructing messages – for your most sensitive communications.
- Has GPG built in, so if you are looking to extend the training to GPG encryption, this is a good tool to start with
Protonmail limitations
- For free accounts, only 500 MB of space. For 5GB space and more, users need to pay. https://protonmail.com/pricing
To sign up for a Protonmail account: https://protonmail.com/
Notes: If you all using the same internet connection (as we do in training workshops), Protonmail might not allow multiple sign-ups on the same IP address. This might cause delay in the activity. Having multiple access points (with different IP addresses) will mitigate this issue.
Jargon Watch: This has a lot of jargon. Please make sure that you have established a way for the participants to pause and clarify concepts they don´t understand as you do your training. It could be as simple as reminding them that they can raise their hands any time when they don´t understand something, and you asking them directly if they don´t understand a technical term.
Signal hands-on
Why Signal?
- Independently-owned and run by tech activists
- Offers end-to-end encryption
- The encryption protocol that WhatsApp uses is based on the Signal back-end. The difference is that Facebook does not own Signal – so communications and users are more secure.
- Messages in Signal are stored only on their servers until it received by a device (mobile or computer). Once it received, the message is only stored in the device that sent the message and the device that received it.
Signal limitations
- Can be slow
- The interface is basic
- Requires a mobile number to use – so for contexts where there is registration of mobile phone numbers, this can be an issue.
- There is no message syncing on Signal. So even if you can use Signal on your mobile phone and your laptop with the same account, the messages will only be stored in the device that receives the message first. This is part of what makes Signal secure.
Signal can be downloaded on the Google Play Store and on App Store.
Tasks for the Signal hands-on
- Download the app
- Set up an account. This requires the mobile number being used to be accessible to the user during set up.
- Sync contacts.
- You can opt to use Signal to manage even your SMS messages – it means it will store those messages on your phone encrypted. It will NOT encrypt your SMS messages as they are sent.
- Password protecting your Signal app. Privacy >> Screen lock
- Block screenshots in the app. Privacy >> Screen security
- Verify identities. Have everyone share with each other their Signal numbers. Once they have added people others to their Address Book, click on a contact then scroll down to look for View Safety Number, then click on Verify. This will have two users to scan each others QR codes to verify identity.
- What this means is that if ever that contact changes phones you will have to re-verify their identity on Signal. This is an extra layer of security to ensure that you are know who you are talking to, and if that person is no longer verified, you should probably take steps to be more careful with your messaging with that person.
- If needed, create a group chat on Signal.
Riseup Pad / Ethercalc hands-on
Why?
- You don´t need to sign-up for an account to use these services
- Simple, light-weight interface for communities with slow connections
- Offers anonymity
- You can control how long the pads / calcs can be retained
Limitations
- Simple formatting
- Pads can´t have tables
- Ethercalc editing is not like Excel
Set up a pad: https://pad.riseup.net/
Set up a spreadsheet: https://ethercalc.org
Safety considerations in using pads
- Check to make sure that your pads are updated as some of them expire and are deleted automatically, if not updated for a long time.
- You can password protect a pad to limit access to it
- Be sure to send pad links (and passwords, if you´re using that option) using secure communications channels
Jit.si hands-on
Why Jitsi?
- Allows you to make temporary chat rooms that don´t need log-ins
- Much harder to find a live jitsi chat room (as it is temporary)
- No applications needed (for computers) – just a web browser
- Promised end-to-end encryption
Limitations
- For more than 10 people in the room the connection becomes unreliable
Tasks for Jitsi hands-on
- Set up a chat room at https://meet.jit.si/.
- Share the link with the participants.
- For those who want to use the mobile app, download the app and enter the room name.
- Test voice, video and other functionalities in the app
Trainers notes: Before you begin, practice setting up the services/tools just in case how to do tasks have changed.
Additional resources
Alternative To is a website crowd-sources lists and ratings for alternative tools (platforms, software, apps). They have notes / tags that mention security functionalities of the listed tools. This is a good resource to find alternatives to popular tools.
After finding an alternative tool, confirm its security and privacy features by doing a search with the following terms:
- Name of software + security issues
- Name of software + privacy policy
- Name of software + security review
Mobile safety
Work with participants to share strategies and tactics for using their mobile phones more safely in situations and contexts where they live. We **highly recommended** that you choose a Learning Path to travel, as these include activities with different levels of depth that should help participants obtain more insight into the covered subjects.
Introduction and learning objectives
In this module, we work with participants to share strategies and tactics for using their mobile phones more safely in situations and contexts where they live.
This module offers guides for facilitating conversations about how women's rights and sexual rights activists experience their access to mobile technology and communications differently based on their genders and sexual identities. We'll talk about how we are using our mobile phones for personal and private communications, for public and movement communications, and strategies and tools we are using to managing our mobile communications more safely.
This module includes: group activities for and examining our use of mobiles and how this relates to our genders and sexual identities; hands-on activities for exploring and understanding how mobile phones and mobile communications work; group activities for sharing and practicing safety strategies and tactics in the context of our lives; facilitation guides for trainers to bridge issues of feminist safety and technical security.
Common questions we hear and are trying to address in this module:
- What happens if someone else has my phone? What information is on my phone? How might this affect myself, my colleagues, my movement?
- How do I know if I'm being surveilled by my partner, exes, family members, governments?
- How do I use my phone more safely?
- How can we use our phones to organize?
Learning objectives
By the end of this module, the participants would have:
- an understanding of how mobile access and communications are gendered and intimate;
- an understanding of mobile communication safety from the perspective that mobile phones are our tools for both personal, private and public, movement communications;
- an understanding of basic concepts of how mobile communications work in order to better understand the risks of mobile communications;
- shared and practiced strategies and tactics for mobile safety to manage the impacts of our mobile communications on ourselves, our colleagues, our movements;
Learning activities, learning paths and further reading
This page will guide you through the Module's correct use and understanding. Following the Learning Paths, with activities of varying depth, should allow participants to obtain a better grasp of the studied subjects.
Learning paths
For trainers/facilitators who are interested in any specific activity, you can use one or a few in combination. We recommend beginning with a starter activity to open discussion and sharing by participants about their mobile phone experience and how gender, sexuality, race, class, ability, are related to and impact their experiences.
Some specific recommendations: For groups who are considering how to use mobiles for documenting violence we recommend the deepening activity Documenting violence to open space for debate and discussion about challenges and opportunities of documenting violence and the tactical activity Using mobiles for documenting violence: Planning and practicing.
For groups who want to use mobiles for communications for actions and organizing we recommend the tactical activities including Planning mobile comms and Back it up, lock it, delete it.
For participants using mobiles for online dating and sexting, we recommend starter activity Collecting phones and tactical activities Reboot your online dating safety and Safer sexting.
Learning activities
Starter activities

- Mobiles, intimacy, gendered access and safety
- Making a mobile timeline
- Himalaya trekking
- Collecting phones
- Me and my mobile
Deepening activities

- Mobile power - device, account, service, state, policy
- What is a phone? How does mobile communication work?
- Debate: Documenting violence
Tactical activities

- Planning mobile communications for actions/organizing
- Back it up! Lock it! Delete it! a.k.a. Someone took my mobile: Border crossings, arrests, seizure, theft
- Discussion, input + hands-on: Choosing mobile apps
- Using mobiles for documenting violence: Planning and practicing
- Reboot your online dating safety
- Safer sexting
External and tool-based activities
Where modules include practice and use of specific tools and software, we have linked to external resources. We do this for a few reasons: tool designs and features and security issues change frequently and so it is best for us to link out to resources that are updated frequently.
Special note for mobile safety training
It is very rare that all the participants in your workshop would have the same kind of mobile phone. It is a good idea to do hands-on in smaller groups: for iPhone users, for different versions of Android, and/or for feature phone users.
Resources | Links | Further reading
- Video for Change guides: https://video4change.org/resource-categories/
- Witness guides: https://witness.org/resources/
- Security in a Box: https://securityinabox.org/en/
- My Shadow resources: https://myshadow.org/ [Training resources are no longer available, but a guide on how to control our data is still available.]
- EFF's Surveillance Self Defense: : https://ssd.eff.org/en
Mobiles, intimacy, gendered access and safety [starter activity]
This is an introductory discussion about the ways that participants are using their mobile devices. Facilitators can use this exercise to introduce concepts about gendered access, to highlight how we manifest many of our identities in this mobile space and how this presents unique possibilities and risks for participants.
We recommend doing this at the start of a workshop about mobile safety.
This activity has 3 stages:
Learning objectives this activity responds to
- an understanding of how mobile access and communications are gendered and intimate;
Who is this activity for?
This can work for anyone who uses a mobile phone or has used one.
Time required
This activity will require about 30 minutes.
Resources needed for this activity
- white board or chart paper (if the facilitator chooses to write during the shareback)
Mechanics
Our mobile phones are spaces of intimate interactions. We connect with loved ones, lovers, friends, share calls, messages, images, videos, private conversations and images. And insodoing, we know our mobile phones as personal intimate objects, but they are also a part of a larger context, linked to mobile phone providers, regulated by government policies, subject to getting taken, viewed without our consent.
Mobile phone access varies by gender and mobile phone use by women represents a challenge to power – people may enact violence on women using mobile phones; in another context, women may use mobile phones to report abuse.
Pair Discussions - 15 minutes
In pairs to facilitate personal sharing. Ask one partner to share first and the other to listen. Then prompt partners to swap listening and speaking roles. Each person should have about 5-7 minutes to speak. This will depend on how long it takes for pairs to form.
Questions
Write these somewhere visible to everyone or on pieces of paper that the pairs can take with them to their discussions.
- How do you use your mobile phone? When do you use it? If people are stuck, ask them how they use it with different kinds of people: friends, family, colleagues, strangers.
- How do you use mobiles for organizing?
- When do you feel unsafe using your mobile phone? What do you do to manage in these situations? Encourage participants to not discuss possibilities of theft, looking for people to share examples of things like spying housemates, partners, family members; police seizures, etc.
Facilitator make notes and synthesize. Are there any strategies in specific that you want to address, situations, scenarios?
Making a mobile timeline [starter activity]
This is an introductory activity participants share personal experiences with mobile phones and engages people through body movement and storytelling. You can expect participants to speak and hear about each other’s attitudes towards mobile phones and to share ways that they are using and accessing phones that are personal and meaningful to them.
This is similar to the activity, Women's wall of internet firsts, inviting participants to share their experiences of mobile technologies and to relate them to one another along a timeline. Through this activity, the trainer(s) can also become more familiar with the participants' experiences and relationships to mobiles.
Learning objectives this activity responds to
- An understanding of how mobile access and communications are gendered and intimate.
Who is this activity for?
This can work for anyone who uses a mobile phone or has used one.
Time required
This activity will require about 30 minutes.
Resources needed for this activity
Labels to mark a time line with dates in 5-year segments, 1990-2019. This can be numbers written on paper and laid on the ground (ex. 1990, 1995, 2000... etc).
Mechanics
Prepare a timeline in your room. Participants will stand along the timeline at specific dates in response to questions you ask. In a large group, ask participants to move to a time along the timeline in response to the following questions. When the timeline is created, ask what the first and last dates are, if there are clusters of people at certain areas of the timeline, ask them where they are.
Depending on your group size and how much time you have, choose 2 or more questions.
Ask 1-2 participants to respond to the specific questions, for example, "What was it like?"
Questions
- When did you first have a phone? What was it like? Did you share it with anyone? How old were you? What did you use it for?
- When did you have your first smart phone? What does that mean to you? Did you share it with anyone? What is your favorite app? Why?
- When did you first connect to the internet using your phone? What website did you access first? Why?
- When did you first "retire" a phone? What did you save from the phone (ie. Media like photos, text logs, hardware)? Why?
Debrief - 5-10 minutes
Ask participants if they have any comments or observations to share. Facilitator, debrief and connect what people have shared to intimacy and gendered access - consider what people have said about their attitudes towards their phones and the ways that they like to use their phones.
Intersectionality Flag: How is mobile access and privacy varying among participants based on their gender, sexuality, race, class?
Himalaya trekking [starter activity]
This is an introductory activity to raise participants' awareness about mobile security and for both participants and facilitators to assess the kinds of safety measures participants are taking and the vulnerabilities that might be the largest priorities to address. We recommend doing this at the start of a workshop about mobile safety.
Learning objectives this activity responds to
Who is this activity for?
This can work for anyone who uses a mobile phone or has used one.
Time required
This activity will require about 30 minutes.
Mechanics
Facilitator ask the participants to stand in a line shoulder to shoulder. Ask questions about mobile security of the participants. Instruct participants to take a step forward if their answer to the question is yes, a step backwards if their answer is no.
Example questions
- Do you have a screen lock?
- Do you use app locks?
- Do you have an unregistered SIM?
- Do you use an alternative email (not your main email account) for your phone?
- Have you set up remote access (Find my phone) on your phone?
- Are location services turned on your phone?
- Do you have a backup of the media on your phone (photos, messages, videos, etc)?
- Do you have an anti-virus on your phone?
Debrief - 5-10 minutes
Ask participants if they have any comments or observations to share. Facilitator, debrief and connect participants' trekking to the agenda for the day or series of sessions you will be together.
Collecting phones [starter activity]
This is an introductory activity to raise participants' feelings about their mobile devices and other people accessing the devices and contents.
Learning objectives this activity responds to
- an understanding of how mobile access and communications are gendered and intimate;
- an understanding of mobile communication safety from the perspective that mobile phones are our tools for both personal, private and public, movement communications.
Who is this activity for?
This activity works particularly well in the context because their workshop participants experience this often. We recommend this exercise if your participants are experiencing device seizure and want to discuss the impacts on them and their emotional responses.
Care note: We recommend doing this with great care. Get participants' clear and emphatic consent. This will likely work best in a context where you and your participants have already built deep trust with one another.
A note about learning pathways: This is a great starter activity to prepare for discussions and tactical activities around preparing for high-risk situations in which phones may be taken or lost.
Time required
This activity will require about 30 minutes.
Mechanics
Activity: Collect participants' mobile and discuss – 15 minutes
Collect participants mobiles in the very beginning, getting their clear and emphatic consent, but without explaining why you are collecting them.
Discussion
Ask:
- How do you feel about not having your phone in your hands?
- What are your immediate feelings?
Activity: Return mobiles and debrief - 5-10 minutes
Return the mobile which was collected from the participant in the very beginning.
Discussion
Ask:
- How did you feel to leave your mobile? Why?
- How do you feel getting your phone back? Why?
- Are there times when your mobile is taken from you? Who is taking it and what is the situation?
- How do you feel in that situation? Why?
- Why is your phone important to you? What does your phone give you access to? Encourage participants to be specific about how they relate to their phones, what the phone connects them to, the importance of their phone.
Me and my mobile [starter activity]
This is an introductory discussion. This is designed as a very short activity, to facilitate participants' thinking about how they are using their mobiles in intimate ways and to begin to share practices and concerns around surveillance and privacy related to these.
We recommend doing this at the start of a workshop about mobile safety.
Learning objectives this activity responds to
- an understanding of how mobile access and communications are gendered and intimate.
Who is this activity for?
This can work for anyone who uses a mobile phone or has used one.
Time required
This activity will require about 30 minutes.
Resources needed for this activity
- white board or chart paper (if the facilitator chooses to write during the shareback)
Mechanics
Pair discussions - 15 minutes
In pairs to facilitate personal sharing. Ask one partner to share first and the other to listen. Then prompt partners to swap listening and speaking roles. Each person should have about 5-7 minutes to speak. This will depend on how long it takes for pairs to form.
Question 1: What are the most personal and private things you do on your mobile phone?
Question 2: What do you do to take care of these interactions, media, these experiences?
Facilitator, give an example or two of what you would share in a pair. For example, nudes that you are taking for your own pleasure and expression of self, sexting or intimate conversations you are having with others.
Intersectionality Flag: How is mobile access and privacy varying among participants based on their gender, sexuality, race, class, disability?
Facilitator make notes and synthesize. Ask people to share what they spoke about. Draw out common threads from the conversation. How are people using their phones and in what ways are these uses intimate? How have participants shared that their gender relates to their access to mobile phones, to their privacy? What are people doing to care for their intimate interactions and mobile media? What are people concerned about and how are they relating privacy and gender, sexuality, race, class, disability, age, etc?
Mobile power - device, account, service, state, policy [deepening activity]
This is a collaborative mind-mapping activity. Through a facilitated conversation, the group will discuss how they relate to their phone devices, service accounts, mobile phone providers and a small amount about how corporate and government policies come into play.
We suggest doing this activity at the start of a mobile workshop.
Learning objectives this activity responds to
- an understanding of mobile communication safety from the perspective that mobile phones are our tools for both personal, private and public, movement communications;
- an understanding of basic concepts of how mobile communications work in order to better understand the risks of mobile communications;
Who is this activity for?
This can work for anyone who uses a mobile phone or has used one.
Time required
This activity will require about 45 minutes as written. If you want to cover this content faster, you could ask the participants fewer questions and instead share a slide or example mindmap.
Resources needed for this activity
- chart paper
- markers
Mechanics
Ask your participants a series of questions and mind-map their responses. The goal is to try to map the ways participants related to their mobile phones. Participants will discuss mobile power, control and agency as they discuss how they relate to their mobile devices, service accounts, mobile phone providers and corporate and government policies.
Suggestions for preparation
- Familiarize yourself with the local carriers;
- Familiarize yourself with the links between the local carriers and the state. ex. are they state run?
- Prepare some local examples of ways that women/gender rights activists are using their mobiles, how this relates to power; how corporations and/or the state react/regulate if applicable;
Draw a mind map in a visible space so people can see as you ask the following guiding questions.
- indicate places where participants speak of choices or decisions that were made for them. ex. type of phone, android/nokia; who else has access to their phone, how they chose it; service provider; plan type; who has access to their plans
example mindmap. click to view it larger.
Questions to ask
- About devices: What kind of phone do you use? How did you get your phone? Do you share it? How and with whom?
- About your mobile service: How did you select your mobile carrier? Do you share your plan? Do you manage your plan and if not, who does? Did you choose your plan? How?
Ask/discuss
The relationship between ourselves and our mobile providers. Did you sign terms of service? What did you agree to when you signed your contract? What did you provider agree to?
Note to facilitators: If you know of particular concerns with local carriers, try to find and bring examples of terms of service and/or case studies where people/consumers have engaged with the carrier around safety.
Ask/discuss
The relationship between the mobile providers and the state. Are these state run? Are they international, local, regional companies?
Note to facilitators: You may want to research in advance, state regulations or influences on mobile use. Have there been any recent state shutdowns of service? Are participants familiar with targeted shutting down of individual's lines? Do security forces seize devices?
Additional resources
Case studies: as WRP continues to use this activity, add links to relevant case studies here
- A wikipedia page listing mobile carriers by country: https://en.wikipedia.org/wiki/List_of_telephone_operating_companies
- 101: SIM Card Registration: https://privacyinternational.org/explainer/2654/101-sim-card-registration
What is a phone? How does mobile communication work? [deepening activity]
The purpose of this activity is to deepen knowledge of how mobile communications works in to support participant's ability to assess and plan for risks of mobile communications. Facilitators should include this in any mobile workshop or confirm that all participants are already familiar with the information in this activity. It is the basis of assessing technical mobile risks.
This activity has 2 stages:
- Hands-on phone dissection
- Input: Mobile communication data and risk considerations
Learning objectives this activity responds to
- Understand some basic concepts of how mobile communications work in order to inform ourselves about the potential impacts of using mobile communications;
Who is this activity for?
This activity is for anyone participating in a mobile workshop.
Time required
This activity will require about 45 minutes.
Resources needed for this activity
- some mobile phones to open up and investigate
- A whiteboard, slide, or handout with top level points
Mechanics
Mention or discuss, depending on time, that we will talk about mobile technologies – considering devices that are easily portable in a hand or pocket and have communication capabilities from voice calls and sms to web and data services. Some of this section will apply also to tablets.
Inside our phones - 5 minutes
Take this phone apart. Your phone is a tiny computer. Everyone take your out and locate:
- Parts that listen and project sound: microphones, speakers
- Parts that view and display visuals: cameras, screens
- Parts that send and receive information from other sources: GPS, Antennae, Wifi
- Parts of the computer, hardware: battery, circuitry
- Memory: SD card, other memory built-into the phone
- SIM card slot(s)
Device and SIM identity - 5 minutes
Your phone has all these pieces and it has a few identifying features, in addition to the make, model and OS, it has 2 names - a Device Identifier and a SIM Card identifier. These are important to know about because you can be identified by either one and your phone communicates this information often, especially the IMSI.
- IMEI is the name of your device
International Mobile Equipment Identifier (IMEI): https://en.wikipedia.org/wiki/International_Mobile_Equipment_Identity
- IMSI is the name of your SIM card
International Mobile Subscriber Identity (IMSI): https://en.wikipedia.org/wiki/International_mobile_subscriber_identity
Our phones in communication - 35 minutes
We use our phones to communicate with people: SMS, Messaging, Social Media, Apps, Calls. Our mobiles are also communicating information about our phones and ourselves - not just our messages but metadata, our location, etc, and this can be linked to other information about us like our social networks, our organizing networks, our habits and places of work.
It's good to be aware of these, mostly so that we can understand how our mobile phones use can act as a tracking device in the moment and as a historical record of our activities afterwards.
1. Your phone is chatty
Your phone is calling out to different types of networks and via different types of communication to announce it is near and to connect or check if anyone wants to connect.
Mobile carriers
Mobile carriers have towers and antennae that your phone communicates with. Each antenna can reach a specific area. Your phone checks in with whichever tower(s) you're nearest. It shares at least your IMSI to announce which mobile carrier you are using and your number so you can receive messages, calls, and communications to your device. Every time you are near a tower, it is like dropping a pin on a mapped timeline where you are. You mark where you are, when you are there, and what you are doing in that location in terms of using your phone.
GPS
If your GPS feature is on, your phone is communicating with GPS satellites, similarly checking in, which is like dropping pins on a mapped timeline.
Wifi
If your wifi is on, as you pass through Wifi networks, your device may both attempt to connect to those networks, leaving a pin with the wifi network, and also make a record of the network name in your phone.
Bluetooth/NFC
If these are turned on, other devices using Bluetooth and NFC may be able to communicate with your device, attempt to connect, share files. Etc.
Facilitate discussion: Which things you need to have on when? Are records of where you are a risk for you or not?
2. You are chatty
We use our phones to communicate. Different types of communication appear differently while you are communicating and once the messages have been sent.
SMS
Text messages and metadata - in communication and once stored on your device and with your carriers, are sent in cleartext. A useful analogy is that an SMS is like a post card. If someone intercepts it, they could read the entire contents as well as metadata (ex. sender, recipient, time, date).
MMS
Media messages and metadata - in communication, this may or may not be encrypted, so if someone is trying to intercept your communications, it will vary if they can see it. Once it's sent, you and your recipient's mobile providers and devices have a record of the message and so investigation into either might reveal metadata (ex. sender, recipient, time, date) and content.
Calls
Call content and metadata - similarly - calls should be encrypted as they are in progress, but your provider and your recipient's provider will store metadata about the call (ex. sender, recipient, time, date) and if your opponent has access to your providers, they may have access to listen into calls or to record them.
For more information about Apps and Messaging Apps, see:
A note about state surveillance: From country to country, state surveillance varies. In some places, governments will have access to any and all data that carriers have -- so with these, you should consider all of your metadata and contents of unencrypted services accessible to governments both in real-time and after the fact if there is an investigation for these records.
Your best defense against surveillance is End-to-End Encryption.
3. A phone is a small computer
Software bug - A phone is a computer and can be infected with malware just like a desktop or a laptop. Individuals and governments alike use software to bug other people's mobile devices. This kind of software often uses parts of the phone to act as a bug or a tracking device, listening in with the microphone or sending location data.
4. The cloud is a file cabinet
Some data that my phone accessess is not on my phone at all, it's on the cloud. The "cloud" is just a term that means "the internet" -- data that is stored somewhere physically on a device that is connected to the internet. Your apps may accessing data that is in the cloud and not actually on your device.
Considerations: Is my data encrypted in transit between myself and the service? Is it encrypted when it's stored by the service? Do I know of any instances when opponents have been able to get access to this information - when, how?
Note to facilitator: As you speak, participants may ask questions about parts of phones or risks associated with communication methods you mention. Take the time to answer questions. If you can, keep a running list of issues and topics that people ask for additional information about -- a running list on a white board will do. Also keep a running list of issues and topics you will not get to this workshop so that you address it later in the workshop or suggest as follow up after the workshop.
Additional resources
- 7 Ways to find the IMEI or MEID number of your phone: http://www.wikihow.com/Find-the-IMEI-or-MEID-Number-on-a-Mobile-Phone
- International Mobile Equipment Identifier (IMEI): https://en.wikipedia.org/wiki/International_Mobile_Equipment_Identity
- International Mobile Subscriber Identity (IMSI): https://en.wikipedia.org/wiki/International_mobile_subscriber_identity
Tactical Tech's My Shadow site has a number of great training guides to facilitate learning about mobile tech.
- My Shadow downloadable materials: https://myshadow.org/materials
- My Shadow website: https://myshadow.org/
Some videos:
- How does your mobile phone work? This video at nine minutes is likely too long to show during your workshop but can be a reference for participants and for yourself to understand how cell phones work via antennas and mobile switching centers, as well as cell phone generations. https://www.youtube.com/watch?v=1JZG9x_VOwA You might like to find shorter videos that touch on some details and are more appropriate to your specific context once you are familiar with this longer video.
Debate: Documentation of violence [deepening activity]
This is a deepening discussion activity to facilitate discussion around using mobiles to document violence and how this relates to perpetuating violence. This exercise can be used to discuss case studies specifically of activist media aimed at reducing violence to ways in which the same channels and media have been used to perpetuate violence.
Participants will share examples of how they are using mobiles to document violence and will engage in debates around the impacts of sharing documentation of violence online.
Learning objectives this activity responds to
- an understanding of mobile communication safety from the perspective that mobile phones are our tools for both personal, private and public, movement communications.
Who is this activity for?
Groups who are currently or considering using mobiles to document violence.
Time required
This activity will require about 60 minutes.
Resources needed for this activity
- Printed or linked case studies
Mechanics
In plenary - 10 minutes
Ask participants to share ways they are using mobile phones to document violence.
Care Note: People may share incidents that are activating for themselves and others in the room. When you ask for examples, acknowledge any agreements and norms of your space regarding speaking about violence. You may want to acknowledge that the exercise will discuss acts of violence and that people who are sharing are invited to share and to take care of themselves, to share in a way that they do not exceed their own capacity, to ask people to care for themselves if they are feeling activated to stop sharing or to care for themselves how they need.
Ask:
- What are examples of documenting violences and sharing the documentation that have had a positive impact on your work, advocacy, for your communities?
- What were you documenting?
- What happened?
- How did you share?
- Who did you share with and how did you choose these people?
- What was the response?
Facilitators, you may want to prepare examples of recent and local movements using mobiles to document violence and ask participants to share examples of how they are using mobiles to document violence or to share documentation. Examples may include: documenting state violence, forwarding videos of violent acts, live streaming violence, the implications of having possession of this kind of media.
Some examples are linked in the "Additional resources" section below. You may choose to use these for your small group case studies or to select examples that are more current or appropriate for your participants.
Explain that this activity is to facilitate space of discussion and debate around this use.
Small group - case studies - 20 minutes
Give each small group a case study to read and discuss. You can find case studies below – choose from and edit case scenarios, blog posts and articles from the news, or choose or write examples that are more relevant for your participants.
- What is the example?
- What are arguments for using mobiles to document violence in this instance?
- What are arguments not to use mobiles to document violence in this instance?
- What are some ways you could reduce negative impacts of this kind of video documenting violence?
Scenarios
These scenarios are examples of one way to write scenarios for your workshop participants. By writing more than 1, you can raise multiple issues that you know participants will want to discuss. The examples here are designed to spark conversations around linking documentation to movement, consent, impact and perpetuation of violence.
Scenario 1
Your community has been facing violence and harassment. You and others have organized to document specific acts and to share some of these on social media platforms with subtitles and text to explain the incidents and the ongoing violence. You link these to resources including a list of demands of your community is making and support resources for people who are experiencing similar violence.
Scenario 2
You witness an act of violence on the street and begin live streaming it to your social media channel where you have thousands of followers. You do not know the people you are filming and you do not know the context.
Scenario 3
You and your community have been livestreaming footage from demonstrations in order to both show the power of the demonstrations and to document incidences of violence and harm done to demonstrators. You become aware that the footage is being used by local police and by opposition groups to target demonstrators and edited together to create oppositional media about demonstrators that is also being shared on social media.
- What is the example?
- What arguments for and against using mobiles to document this instance of violence came up?
- What does this raise for others? Do you encounter this issue? How are you thinking about it? How are you strategising for the best possible impact and how are you reducing likelihood or negative impacts?
Facilitator, as participants shareback, draw out common themes. What are your participants concerned about most in their work – some issues that may come up and that you can facilitate sessions on more specifically later may include tactical issues of how to document, store, share; issues of verification of media, deep fakes; use media to incite violence and the possibility of sharing documentation of violence as perpetuating violence and harm.
Additional resources
Case studies and blog posts about the impacts of documenting violence
Examples of how people are using mobiles in organizing - we suggest gathering local or relevant current examples of how organizers are using mobiles and asking your participants and hosts for examples in preparation for the workshop.
- Migrant workers documenting abuses
- Centre for Migrant Advocacy´s OFW-SOS
Live streaming violent acts Case Study: The Ethical Challenges of Live Internet Broadcasting, Irie Crenshaw and Justin Pehoski https://mediaengagement.org/research/matters-of-facebook-live-or-death/
- Australia
The world is turning against live streaming, In the aftermath of the Christchurch shooting, Australia is leading the charge against raw, unfiltered video, Casey Newton, April 4, 2019 https://www.theverge.com/interface/2019/4/4/18294951/australia-live-streaming-law-facebook-twitter-periscope
- Brazil examples
Dispatch from Brazil: If killed by police, guilty by default unless there's video?, Priscila Neri https://lab.witness.org/dispatch-from-brazil-if-killed-by-police-guilty-by-default-unless-theres-video/
- Whatsapp and violence in India
WhatsApp will drastically limit forwarding across the globe to stop the spread of fake news, following violence in India and Myanmar, Kurt Wagner Jul 19, 2018 https://www.vox.com/2018/7/19/17594156/whatsapp-limit-forwarding-fake-news-violence-india-myanmar
- USA examples
Planning mobile communications for actions/organising [tactical activity]
The following are guiding considerations for groups who are organizing and participating in actions and relying on Messaging Apps. Using this guide, you can facilitate discussions to support groups in considering the kinds of communications they are having and to design group management, message and device protocols that meet the safety needs for that communication.
This activity has 3 stages:
- Mapping communications & Assessing risks
- Planning: Design groups and settings
- Installing Apps (optional)
- Implementing (optional)
If groups have not yet chosen the messaging app they want to use, you may want to do the activity Discussion, input + hands-on: Choosing mobile apps
Learning objectives this activity responds to
Who is this activity for?
This activity is for participants with varied levels of experience in using mobile phones. If participants include individuals who will be group admins for messaging groups, plan to implement the designs in the workshop.
Time required
This activity will require about 60 minutes to map and design and up to 3 hours if you will be installing messaging apps, mapping and designing, and implementing.
Resources needed for this activity
- Paper for people to draw and complete the Mapping chart
Mechanics
Mapping communications and assessing risk
Consideration: Privacy
Consider that you may have different types of messages to communicate via signal and that some messages can be more public than others. Map the kinds of communications you have and design groups to match your privacy considerations.
What kinds of communication are you doing and what considerations do you have around who has access to communication? Suggest that participants consider these different groups. Ask them if they have more types of information -- for example, is there information that only 2 people should know, that only one person should know and document and not share?
| WHO | EXAMPLE COMMUNICATIONS |
| 1 needs to be kept among a very small circle of people who know each other | location of lead organizers |
| 2 is vital for volunteers to know or for small groups to coordinate around | changes in crowd location |
| 3 can be shared openly | rally start time, groups who endorse this action publicly |
PLAN: Design groups and settings
Work with participants to design groups to correspond with the different types of communication.
Guiding suggestions around group design: We suggest starting from these design questions. We have included example suggestions for group management and settings for some common types of groups. Ask the participants what about this will work and what will not, facilitate the group in modifying the designs to respond to parts that do not work.
Membership
- WHO - Who can join this group?
- HOW - How do people join this group? What is the procedure? Do they need to be vetted, introduced, do they opt-in or sign up?
- ACKNOWLEDGEMENT - How does the group acknowledge when a person joins? Why would you want the group to do this or not?
- COMPLIANCE - What do you do if someone joins without following procedure?
- PERSONAL INFORMATION - with the messaging service you are using, can members of a group can see numbers of other members of a group? If so, for anyone who needs their number to not be known as part of the organizing, they should not join any large groups where the other people don't already know their number and that they do this work.
VERIFICATION: Know who you are talking with
For a type of communication, how will you verify who you are talking to?
- FACE-TO-FACE - will you require that any group member meets the rest of the group face to face in order to join? can a person just be added and vouched for by a member of the group
- SAFETY #s - VERIFY that your Messages are reaching the correct devices. If you are using Signal or Whatsapp, VERIFY SAFETY NUMBERS
- SAFETY WORDS - VERIFY that your calls are reaching the correct devices. If you are using Signal for calls, SPEAK THE SAFETY WORDS to one another. If you are using another calling application, do you want to have a way to check in at the start of a call to verify that a person is who you intended and speaking freely?
Message security - settings
Discuss, based on the sensitivity of the information you are communicating, what agreements do you want to make about how people are using message settings?
- DELETE Messages - How long should group members keep chat logs on their devices?
- DISAPPEAR Messages - In a Signal chat, you can set how long messages will remain before being automatically deleted. Do you want to use this feature? How and why?
- HIDE Messages on your home screen - Set Messaging apps to not preview on your home screen so that if you lose control of your device, people cannot just look at your home screen to see message content
- CODES - For extremely sensitive information, we suggest establishing code words before planning and action. For example, you might substitute words "We're ready for the tea party" instead of "Ready for the protest!"
Common group design templates
1. Small very strictly verified groups for sensitive information
Consideration/Risk: That people will join groups who you don't know and don't want to have access to information that is not okay going public.
- If you have sensitive information that needs to be shared only between a set of known people,
- Very small group, 8 or less, everyone knows each other and has met face to face;
- Only add people when you are face to face;
- VERIFY Identity (on Signal, verify Safety Numbers) in person;
- If anyone's safety numbers change, re-verify in person.
- Don't say more than you need to, don't take unnecessary risks
- DELETE
2. Pods - small groups
Consideration/Risk: That people will join the group and send information that is not useful or intentionally incorrect.
- This manages for the risk of individuals spamming the large group and making it unusable and too noisy;
- 2-20 people, whatever it takes to keep chatter down and have a manageable number of Signal Pods;
- A large group may have multiple pods to keep communication manageable and relevant;
- Pods are connected to one another so that information can flow between. You might consider having one point-person in each pod so they can push information that everyone needs to have;
3. Open group, public Information
Consider information on this channel to be public information in real-time. While information from any of the other groups could be leaked or shared outside of the group, this is a group that you automatically consider to be public.
- If you have any information to share that can be made public, use this!
Device security
If your device is taken, prevent others from pretending to be you and reading your information like signal messages, contact book, email etc. For more detailed facilitation guidance around device security, see the activity: Back it up! Lock it! Delete it! a.k.a. Someone took my mobile: Border crossings, arrests, seizure, theft
- Set your lock to immediate/trigger with any button
- Set a strong password
- Encrypt your phone
- Encrypt your SIM card
Power and service
What if people can't use SIGNAL or your chosen App, Phones, Internet, for any reason - power, busy network, shutdown etc. Do you have backup or redundant internet access - a portable wifi hotspot for instance (if it uses cellular data that would also go down)? Is there an offline plan? Will your hub have a power-charging station for volunteers?
Additional resources
- About how to Verify Safety #s and Safety Words - https://theintercept.com/2016/07/02/security-tips-every-signal-user-should-know/
Back it up! Lock it! Delete it! a.k.a. Someone took my mobile: Border crossings, arrests, seizure, theft [tactical activity]
In this activity, we plan and prepare for situations where participants and their phones may be at physical risk. Scenarios may include:
- Safety when participating in protests
- Safety at border crossings
- Safety when there is threat of arrest and seizure
- Safety when there is risk of theft and harassment
This activity has 4 stages with optional hands-on activities with installing and preparing devices. The stages include:
- Current practices in caring for ourselves
- Planning and preparing our devices
- Inputs – Optional
Optionally, follow this activity with hands-on exercises to practice the strategies and tactics.
Learning objectives this activity responds to
- an understanding of mobile communication safety from the perspective that mobile phones are our tools for both personal, private and public, movement communications;
- an understanding of basic concepts of how mobile communications work in order to better understand the risks of mobile communications;
- shared and practiced strategies and tactics for mobile safety to manage the impacts of our mobile communications on ourselves, our colleagues, our movements;
Who is this activity for?
This activity is for participants with varied levels of experience in using mobile phones to practice tactical safety with a focus on care and mobile phones.
Time required
This activity will require about 80 minutes.
Resources needed for this activity
- flip chart paper + markers to document group discussion
Mechanics
This exercise is designed to support activists who are planning to engage in risky situations with their mobile phones. In the end, they will have a map of tools and tactics they can use.
Current practices in caring for ourselves – 20 minutes
Care note: This activity is a tactical activity to plan and prepare for using mobile phones in situations where people and their devices are at risk. Begin by acknowledging that to prepare for a risky situation, we need to consider first how we care for ourselves before, during and after.
Begin with grounding and discussion about how people care for themselves in high risk situations.
Ask each individual to begin by working on their own. Hand out paper and ask them to consider these questions and to write their answers:
- What situations do you engage in where you will need to consider the physical safety of yourself and your mobile phone?
- What are you already doing to care for yourself – before, during and after these experiences?
Ask participants to divide their paper in 3 sections: before, during and after. Their paper will look something like this:
| Participants' Paper Example | ||
|---|---|---|
| BEFORE |
DURING |
AFTER |
As a full group, invite participants to share their practices. Write these on a white board or piece of paper visible to the full group. Leave this up in a place that is visible. Ask people to share practices they do as individuals and with others.
Participants will continue to use this simple method for organizing practices in the next part of the workshop.
Planning and preparing our devices - 45 minutes
If you are working with participants to prepare for a specific event, it is best to work with the actual event. The following are scenarios that you might use in case workshop participants are not preparing for a specific event or your group needs more grounding for any reason. These are examples and we invite you to take these and make them your own.
Scenario 1: Safety when participating in protests
You are about to attend a mass protest. You need to be able to keep the data in your phone safe and to keep yourself from being tracked in the protest, but also be able to use your phone to contact allies for emergency purposes. You are also thinking of using your phone to document the protest and any possible human rights violations that will happen there.
Scenario 2: Safety at (unsafe) border crossings
You are in transit, and are about to cross a border into an unsafe location. You want to be able to use your phone to keep contact with your allies, but not as a personal tracking device. Ask people what their strategies are when they know someone else may have access to their phone. Examples of situations might include border crossings, flight boarding, going to a street protest.
Scenario 3: Safety when there is threat of arrest or seizure
You have heard from a reliable contact that you are being targeted by the state for arrest and seizure of devices because of your activism.
Scenario 4: Safety when there is risk of theft and harassment
You are concerned that someone may steal your phone and use the content to harass you.
Ask participants to document their discussions on paper and to divide their paper in 3 sections: before, during and after. Their paper will look something like this:
| Participants' Paper Example | ||
|---|---|---|
| BEFORE |
DURING |
AFTER |
In small groups, facilitate participants to work through the following sets of questions.
How are people impacted: In this scenario/the event or experience you are preparing for, what are the risks? Who is impacted by this? Consider yourself, people who are on your phone in some way, your organizing/the issue you are working on (if applicable).
You can use the following questions as guiding questions for groups to consider how to reduce the impacts on people from a tactical perspective.
Before: Think about what you will do to prepare your mobile phone for this scenario.
- What files will you delete from your phone? Why?
- What applications will you install? Why?
- Who will you inform about your plans? Do you want to set up a check in system for before and after the experience, is that possible?
- What secure communications set-up will you have with others?
- What other strategies will you and your allies have in place to keep yourselves safe during this experience?
- Location services: Is it safer for you to have location and tracking on or off? Do you want other trusted people to be able to follow your location?
- Remote wipe: Do you want to activate remote deletion in case you lose access to your device?
During: Think about how you will use your phone during the scenario.
- Power: Is power a concern? How will you ensure that people’s mobile phones have charge?
- Service: Is service a concern? What will you do if people cannot use their mobile service, apps, or data? Is there an offline plan?
- Who do you want to communicate with during this scenario? How will you communicate with them?
- Are you documenting the protest? If so, are you using any special app for it?
- Who will be able to contact you through your mobile phone?
- Who will you be contacting through your mobile phone?
- If you will need to use a SIM card different from your regular SIM card, how will you choose your carrier? Is there one that is safer than others for your communication? Who will be able to contact you? Who will you contact?
After: Think about what you will do after the scenario.
- Media: If applicable, what will you do with the footage, pictures, audio and other media that you gathered?
- Metadata and records that your mobile makes: What considerations do you need to take about the data your phone is creating during this scenario, consider metadata, records of communication, location of your device.
- In case of seizure: How will you know if you have a spy-ware free phone?
- In case of theft or seizure: What will you do to regain the integrity and safety of your mobile phone?
Give the groups a minimum of 30 minutes to a maximum of 45 minutes to come up with plans, strategies and tactics.
At the end of the group discussion, ask the groups to talk about their plans, strategies and tactics.
Use the results of the report-back to plan your hands-on for mobile safety.
Input (optional) - 15 minutes
Notes for trainer/facilitator Depending on your style and your participants, you may want to deepen and add inputs as groups debrief or as a planned input section. The following are notes that we believe may be useful as you plan this.
Before
- Let people know you will be in a situation where you are concerned about yourself and your personal belongings. Make plans to check in with your trusted friend as you enter and exit this situation. Choose a frequency of checking in that fits the risks you are facing.
- For a very high risk situation: We recommend planning to be in touch as frequently as every 10 minutes. For example, if you are going to be at a high-risk protest or doing a particularly risky border crossing. Plan to communicate every 10 minutes on your approach, while you wait (if possible), and upon crossing.
- For less risky situations: For example you are in a town working with a group of sex workers. You are traveling to and from meetings throughout the day. Make a plan to check in with your trusted partner when you are on your way and when you arrive at each meeting. Check in when you are going to bed, a simple “going to bed” and when you wake up “starting the day.”
- Clean it: What is on your device that you may want to keep private?
- Log out: Log out of any services that you don't need to be logged into. Don't stay logged into services you don't have to be logged into. If someone takes your phone, they will be able to access your accounts, see your activity, act as you on the service if you are logged in.
- Lock and encrypt: You can encrypt your phone, SD card, and SIM card, locking each with its own PIN will mean that if someone else has it, they won't be able to access the information on it or use it on the network without your PIN. If you are in a situation where you are being threatened for your access information, you may not be able to keep the PINs and passwords private. Discuss with others and consider this as you make your safety plans.
- Device Copying: Many law enforcement agencies have access to equipment to copy digital devices including mobile phones, laptops, hard drives. If your phone is copied and is encrypted, the person who copied it will need your password to decrypt it. If your phone is not encrypted, the person who copied your phone can access all content via the copy of the phone.
- Be quiet: turn off notification sounds and graphics, keep it on mute
- Remote wipe: You may or may not want to enable remote wipe. In some situations, you may want to prepare for remote wipe and ensure that you and a trusted colleague have the ability to remotely delete the content of your phone if someone has taken it or you have lost it.
- SIM cards and devices: Our mobile phones are devices that create and broadcast a lot of information, from messages and calls that we make and send, to data sent to apps, to location and time stamps communicated frequently with mobile phone carriers. Assess if you want to carry your personal device into a risky situation. If you do, this device may be linked to you by opponents and tracked ongoing. You may instead, choose to leave your device at home or to use a “burner” device, a device that you intend to use only for this action or event, that you expect will be linked to your activity during the action or event, and that you can and will discard afterwards. Note, you will need to have both a phone and SIM card in order for this to work. Both your phone and the SIM have an ID. If you use your regular phone and a burner SIM, and replace your regular SIM after the action, you will still be known by the ID of your phone. This is an expensive option and keeping a phone and SIM from being tracked to you will take a lot of planning and the ability to stop using and destroy the device. If you are unable to discard the device, you might still think of carrying an alternative phone into risky situations, but the more you use it, the more easily it will be linked to you.
- Removing SIM cards: If you find yourself entering a risky situation without having planned, you may want to remove sensitive parts of your phone like your SIM card and memory card (if possible). Note: in some situations this may be used as an excuse by aggressors to escalate harm.
During
- Remote wipe
- PixelKnot for encrypted messaging
- Firechat for protests and network shutdowns
After your phone has been out of your control
- Clean it or get a new device: Our best recommendation is to factory reinstall. If you can afford it, replace the device; do not reset your first device, instead send it to someone who can analyze it.
- Your services: Reset passwords to all of your services.
- Let people know: If your phone has been out of your control, let your contacts and people you had active communications with know and what the implications may be for them.
Additional resources
- EFF Surveillance Self Defense - Encrypt your iPhone - https://ssd.eff.org/en/module/how-encrypt-your-iphone
- EFF Surveillance Self Defense - Using Signal on an iPhone - https://ssd.eff.org/en/module/how-use-signal-ios
- EFF Surveillance Self Defense - Using Signal on an Android - https://ssd.eff.org/en/module/how-use-signal-android
- EFF Surveillance Self Defense - Using Whatsapp on an iPhone - https://ssd.eff.org/en/module/how-use-whatsapp-ios
- EFF Surveillance Self Defense - Using Whatsapp on an Android - https://ssd.eff.org/en/module/how-use-whatsapp-android
Discussion, input + hands-on: Choosing mobile apps [tactical activity]
This is discussion and input activity that will focus on enabling the participants to choose mobile apps for themselves, especially after the workshop.
This activity has 3 stages:
- Discussion: What are you using and why?
- Input: Best practices for choosing apps
- Hands-on Activity: Assessing Messaging Apps **OR** Hands-on Activity: Assessing Popular Apps
Learning objective this activity responds to
- an understanding of mobile communication safety from the perspective that mobile phones are our tools for both personal, private and public, movement communications;
- shared and practiced strategies and tactics for mobile safety to manage the impacts of our mobile communications on ourselves, our colleagues, our movements;
Who is this activity for?
This session may apply to anyone who has ever used a mobile phone, and wants to have a better handle on how to choose apps.
Intersectionality flag: this activity is designed as practice with assessing safety of mobile apps, specifically messaging apps. Other types of apps that may be more relevant for your participants might include the following:
- menstrual/fertility apps and the data they collect and birth control solutions they might offer
- dating apps
- messaging apps, and immediate erasure /flash apps
- safety apps, esp. for women and what they reveal, what can be turned on and off, if there is remote access,
- gaming or other apps with interactive component
- performative apps like tiktok
Time required
This requires about 60 minutes.
Resources needed for this activity
- paper for small groups to write notes
- White board or large paper for recording shared notes
- some mobile phones with data and app store capability
Mechanics
Discussion: What are you using and why? - 10 minutes
In plenary, ask: What are 5 apps you use the most? What do you use them for? Get everyone to contribute to the discussion.
- list down the apps as participants mention them, ask who else uses the apps and mark down the # of users of the app in the room
- list down their reason for using the app
Then ask: How did you choose them?
- write down the responses to how they choose the apps and
To synthesise, summarise the reasons and go into the input.
Input: Best practices for choosing apps - 5 minutes
- Research! Learn about options, learn about which is a trustworthy app. Ask participants to share their methods of research – you could read about it somewhere online/offlline, ask a friend who you know likes to research. Read positive and negative comments in the download center.
- How do you begin to make sure that it´s a secure app? Who develops it? What is their privacy policy? Is it open source? Has there been incidents of the app being used to get access to systems?
- Understanding the permissions that apps require. For example, why might a game app need access to your camera or contacts?
- What makes you feel more secure/confident using the app – can you control the permissions? Do you know where it stores information about you or that you generate with the app? / Do you know where stuff goes?
- If this is a social app, how do you want to engage with people on this app? What can you choose about who you are visible to, what is visible to people, how people can interact with you and you can interact with them? What are the default settings, what do they reveal about yourself, who do they connect you to? Do you know of any safety issues on this tool? Are there reporting mechanisms that you can use? That could be used against you?
Hands-on activity: Assessing popular apps - 15 minutes
Go into the app store and try to find an app that does something common in the context. In an urban setting, maybe a taxi-hailing app, subway system map etc.
How do you choose? Look into (1) what permissions does it ask for (2) who is distributing the app and who manages and owns the service. There are a lot of apps out there that are copies of popular apps, made to look like something you want like a game or a subway map and they are actually designed to do other things like send your location to someone else. The developer or company that is distributing the app will be named in the app store. Share what you know about who owns the app/runs the service and research to assess ways in which the values may be similar and different from yours and how that may impact your privacy and safety while using the app. If you are choosing between multiple apps that appear the same, look elsewhere online for more information about the app and who is the developer or company distributing it and double check that you are downloading this one.
Activity: Assessing messaging apps - 30 minutes
Break into small groups. In small groups:
- Identify 2-3 apps that your small group are using for messaging
- Answer the guiding questions
Guiding questions:
- Who, among participants, uses it? Is it easy to use?
- Who owns it? Who runs the service?
- Where are your messages stored?
- Is it encrypted? What other safety and security settings does it have? What other ways do you keep your communication safe when using this app?
- When is it good to use?
- When is it not good to use?
List of messaging apps and considerations
SMS
- Everyone uses SMS
- Mobile company. Particularly risky if there is history of collusion between telco and government, or it´s a government-owned telco or if the company is corrupt.
- Stored by the mobile company -- different retention policies. Messages transmitted to towers between you and the person you are sending the messages through. (to?)
- No encryption.
- Good for communication of topics that are not risky.
- Frequently a cost per message.
Calls
- Everyone uses it
- Mobile company has control over it.
- Stored in mobile company -- metadata, for sure.
- Example of insecurity: Hello, Garcie! Incident in the Philippines where a phone call between the ex-president, Arroyo, and the head of the Commission on Elections, was intercepted, witnessing the president telling the COMELEC head how much lead she wants in the next elections.
- Good for communications that are not risky.
- Frequently a cost per call.
Facebook Messenger
- Anyone with a FB account can use it.
- Comes with its own app
- Encryption promised but not verified
- Facebook owns it
- Instead of using the FB app, use Chat Secure instead. You can use your FB credentials to chat with other FB users. But for encryption to work, the people you are chatting with also need to be using Chat Secure and communicating with you via Chat Secure.
- Frequently free, otherwise requires an internet or paid data connection.
GoogleTalk
- Anyone with a Google account
- Comes with its own app
- Encryption promised, not verified
- Google owns it
- You can use Chat Secure for this as well.
Signal (recommended app)
- Run by tech activists
- End-to-end encryption
- No cloud storage. You store messages on your phone or on your computer, Signal does not store messages after they have been delivered.
- Also has encrypted calls
- Used for sensitive communications
Telegram
- Popular messaging app
- End-to-end encryption only for secret chats
- Lots of users
- Facebook owns WhatsApp although the WhatsApp developers promise to safeguard users´ privacy in their Privacy Policy
- Only stores undelivered messages. (what only stores undelivered messages, the whatsapp server?)
- End-to-end encryption, but if messages are backed up to your associated email, they are stored unencrypted.
- Good for communicating with a lot of people
- Still some concern about FB ownership
Wire
- End-to-end encryption promised, in the process of verification
- Developed by former Skype developers -- of note because Skype once had backdoors for the Chinese government that they built in collusion with that government
- Has encrypted voice calls
Additional resources
- What is encryption - https://myshadow.org/alternative-chat-apps#end-to-end-encryption-amp-perfect-forward-secrecy
- MyShadow - Alternative Chat apps: https://myshadow.org/alternative-chat-apps
- Why Signal and not Whatsapp
- EFF's Tips, Tools and How-tos for Safer Online Communications - https://ssd.eff.org/en
- It's also a good idea to do a web search about the latest security issues with the apps that you plan on training in. Key words to use are: name of app + security review + year, or name of app + known security issues + year. Depending on what you find, you might want to remove an app with known and un-solved security issues from your training.
Using mobiles for documenting violence: Planning and practicing [tactical activity]
This is a tactical activity for activists intending to use their mobile phones to document violence.
About this learning activity
This is a tactical activity for activists intending to use their mobile phones to document violence. Participants will practice doing a safety assessment and making a documentation plan. Participants will then work hands-on with their mobile phones to practice documenting using their apps and tools of choice.
Care note: Facilitators, this is a long activity and may take most of a day. Be sure to take breaks as you go through this. Acknowledge that the act of documenting is stressful and encourage your participants to share exercises that they find helpful when they are documenting for example breathing and motion exercises.
This activity has 2 parts:
Part 1: Assess and plan
Participants will first plan their work, assessing safety issues and the wellbeing of those involved and will make safety plans and decisions about managing mobile phones and media based on this assessment.
Part 2: Setup and practice
Following this, participants will practice tactics for documenting violence using mobile phones.
We recommend also using the Deepening discussion about mobiles for documenting violence and tactical Back it up, lock it, delete it.
Learning objectives this activity responds to
Who is this activity for?
Groups who are currently or considering using mobiles to document violence.
Time required
This activity will require about 1 hour 45 min.
Resources needed for this activity
- Printed or linked case studies
Mechanics
Introduction - 5 minutes
Part 1: Assess and plan – 30 minutes
Facilitate participants to make small groups based on common situations in which they are documenting violence.
Care note: Facilitators, encourage participants to assess and plan for their own care needs. Documenting acts of violence can be activating and stressful for the documenters. Encourage participants to share how they are self-resourcing, how they are working with other activists to address the impacts of documenting.
see also Back it up, lock it, delete it
Purpose and planning: Discuss the purpose of the documentation
- What are you documenting and why?
- What is the situation?
- What is the purpose of your documentation? If it is to be used as evidence, plan for evidentiary requirements. For more information, see WITNESS' Video as Evidence resources: https://vae.witness.org/video-as-evidence-field-guide/
Assessing risks and taking care: Discuss known and likely safety issues for the people documenting and being documented
- What are likely safety issues you will experience during this work? Are you likely to encounter police or antagonists?
- What about your context might change in ways that will impact your safety and how will you plan for this? Discuss some likely scenarios. Examples might include police and other antagonists becoming more aggressive or violent. Responses might include continuing to document, increasing frequency of safety check-ins among your team, stopping the process of documenting.
- Who will be participating in the documentation (filming, support, communications, etc) and what support do they have and need?
- What do you know about safety issues – does anyone in our group feel more or less safe participating based on the content or the context of this documentation? What roles are they comfortable taking?
- What strategies will you and your allies have in place to keep yourselves safe during the documentation?
- What role does consent play in this documentation? Will you seek the consent of those you document and how will they consent to being filmed or documented? Will you seek the consent of those you document regarding sharing of that footage and documentation later?
- What are safety issues related to you possessing this footage? What are safety issues for people who appear in the footage? How will you take care of the footage once it is shot and is stored on your device, on secondary storage? Consider where you will store it, who has access, if storage is encrypted, when you will delete.
- How might you be impacted by documenting violence? What resources do you need as an individual to be well and grounded while doing this work? What resources could others provide? How will you and your team support each other in your individual resourcing needs and what can you do together to support each other?
Know your rights
- Where you are, what are your rights around documentation?
- How do these relate to the context of your documentation? Example questions you might ask - is it legal to film police, is public assembly legal?
- Are police allowed to search your devices?
- Do police search your devices or force people to delete media?
Preparing your device
- Are you using your personal mobile?
- What files will you delete from your phone? Why?
- What applications will you install or uninstall? Why?
- Location services: Is it safer for you to have location and tracking on or off? Do you have colleagues who should be able to follow your location?
- Do you want to activate remote wipe / deletion in case you lose access to your device?
Discussion: Why or why not, do you use your personal mobile for documenting violence?
Input
Use information from What is a phone? to explain how mobile phones are linked to the people using them, how identification works with real-time surveillance, how metadata about phone usage and media EXIF data can be used to identify you.
After
- Make a plan to come together to debrief. How did things go? What unexpected things occurred and how did your group respond? What still needs response? How are people feeling and who will participate in the next steps?
- Sharing – review your agreements about consent and sharing. Be sure to share these agreements with anyone else you will be working with to share the footage.
Discussion
What else do you want to do after documenting?
Part 2: Setup and practice - 60 minutes
Depending on the time available, you can do these activities together or break into smaller groups and participants join whichever groups suit their needs the most.
Recording tips and tricks
How to use photo, video, and/or audio recording to document violence
- Find the built-in tools on your phone for recording: photos, video, audio
- Practice using these tools, consider the tips on WITNESS's Filming with a mobile phone tip sheet (linked in resources below)
- Plan your shots, be selective
- Capture Detail and Perspective: physically move closer to record more details and move back to show a wider perspective of events
- Keep your shots steady: choose your shot and hold steady for at least 10 seconds, avoid zooming, use both hands and keep your elbows against your body for extra stability
- Hold your phone horizontally to capture a wider angle
- Get in close for good sound: be aware of loud noises that could drown out interviews
- Be aware of lighting: record in a well-lit location and keep the sun and bright lights to your back
- If you have a lot of time, work in teams to plan documenting using these tools. Practice creating a piece of media.
- If you will be sharing on YouTube, consider using the subtitle feature: https://support.google.com/youtube/answer/2734796?hl=en
- Context and messaging. Plan your messaging. Where will you post this and what text will you post to accompany it? How will you link this to your larger objectives?
Recording phone calls
Input: This has proven useful for sex workers who were being threatened by authorities.
Using an app
You can install and use an app that allows you to record. This will require data for downloading, data for conducting the call as the app will use data and not the phone line and will take some planning ahead.
- Assess which app you would like to use and install it
- Google Voice allows you to record incoming calls, not outgoing calls
- Your mobile phone may have a built-in recording app
- Test with a partner
- Practice locating the media and saving it off your phone to a safe location where you can access it when you need it.
Using a recorder
If you are unable to or choose not to use an app for any reason, you could work with another person, using your phone on speakerphone and using a recording device or their phone to record from the call using their phone as a voice recorder. Some phones have a built in voice recording feature.
- Assess which tool or app you would like to use and install it
- Test with a partner. For best sound, get close and record in a location away from other loud sounds.
- Practice locating the media and saving it off your phone to a safe location where you can access it when you need it.
Screenshots
You can take screenshots of your phone to document textual harassment and violence.
- Choose an app to screenshot and practice:
- On Android: a phone using Android version Ice Cream Sandwich, you can press the Volume Down and Power button at the same time, hold for a second, and your phone will take a screenshot that is saved to your gallery.
- iPhone X, XS, XR: Press and hold the Side button on the right and click the Volume Up button at the same time and your phone will take a screenshot that is saved into your Albums in an album called Screenshots.
- iPhone 8 and earlier: Press and hold the Power Button on the right side and click the Home Button at the same time. This will be saved into your Photos. Look for an album called Screenshots.
- Practice locating the media and saving it off your phone to a safe location where you can access it when you need it.
Notice, you will not be able to screenshot all apps. Some apps, like Signal, have a security setting that allows a user to prevent others from screenshotting specific conversations.
Documenting the events for internal records
As an incident is occurring, whether it is brief, long, one time or repeated, it is important to document information about the event. Whereas many of the other tactics are around documentation for public and social sharing, this may be mostly useful as an internal practice. Where is the event occurring, when, who is involved, what is happening. Keeping track of this information can be useful in reconstructing events, assessing and planning responses.
Live Streaming
Adapted from the WITNESS resource: Livestreaming Protests, written for activists in the USA
You are livestreaming at an event like a protest, rally, etc. Definitely use the Planning activities and Prepare activities. This may be a great way to show events that are unfolding and to engage people who are watching in supporting. There are also some elevated risks as there may be police presence and there may be police watching now or later to target activists.
- Location: Document your location intentionally. Film street signs, buildings, and landmarks to document your location. Also, consider how revealing your location in real-time relates to your own safety and the safety of those you are filming.
- Identification of participants: Will you be able to get the consent of those you are filming? How do you want and need to protect their identities? Consider not filming faces.
- Identification of tactics: This works both ways. You might unintentionally film the tactics of the activists in a way that negatively impacts them. At the same time, you may be able to document the tactics of police to better assess their formations and likely actions in the future.
- Who to stream to: What are your goals of livestreaming? Do you want to stream to a small trusted group first who can support you by recasting your media?
- Work with a team: Work together with others who can support you by engaging viewers in comments and discussion, can repost the media to multiple channels.
- Have an ask: Engage your viewers to act.
- Your device: Do you want to user your personal device? Whichever device you use, encrypt and password protect your device. Do not use your fingerprint.
Additional resources
- Video For Change Network: https://video4change.org/
- WITNESS - Filming in Teams: Protests, Demonstrations, Rallies - https://library.witness.org/product/filming-in-teams-protests-demonstrations-rallies/
- WITNESS - Filming with a Mobile Phone - https://library.witness.org/product/filming-with-a-mobile-phone/
- WITNESS - How-to Guide for Interviewing Survivors of Sexual and Gender-based Violence - https://blog.witness.org/2013/08/new-how-to-guide-for-interviewing-survivors-of-sexual-and-gender-based-violence/
- WITNESS - How to Livestream Protests (US) - https://library.witness.org/product/livestreaming-protests-usa/ and video https://www.youtube.com/watch?v=Tm4hgbVuPIk
- https://library.witness.org/product/video-metadata/
- UWAZI, https://www.uwazi.io/ - Uwazi is a free, open-source solution for organising, analysing and publishing your documents.
Reboot your online dating safety [tactical activity]
This is a tactical activity in which participants share safety tips and tricks for online dating. Participants will work in small groups or pairs to update their own online dating profiles and practices. Participants will share their different needs and preferences around dating apps, privacy and security. Participants will share and practice different tactics for increasing the privacy of their dating app use.
Intersectionality note: Facilitators, make space for people to share how their online dating considerations and practices relate to their gender and sexuality. Among your participants, how do gender and sexuality related to the apps people are using to date? How do they relate to concerns about privacy and safety?
This activity has 2 parts:
- Sharing online dating and safety tips and tricks
- Hand-on: Reboot your online dating safety
Learning objectives this activity responds to
- an understanding of how mobile access and communications are gendered and intimate;
- an understanding of mobile communication safety from the perspective that mobile phones are our tools for both personal, private and public, movement communications;
- shared and practiced strategies and tactics for mobile safety to manage the impacts of our mobile communications on ourselves, our colleagues, our movements;
Who is this activity for?
People who are using dating apps and want to use them more safely.
Time required
This activity will require about 2-2.5 hours.
Facilitator note: The exercises take about 2.5 hours and we recommend taking a few breaks as you work.
Resources needed for this activity
- Internet access
- Mobile phones to update dating profiles
- Flipchart or whiteboard
Mechanics
Sharing online dating and safety tips and tricks
Ice breaker - 5 minutes
- Who is using a dating app, which ones? How did you choose it and why?
- How do you already think about your safety and privacy and take care of it?
Safer dating – 30 minutes
Before getting into the apps and hands-on with devices, facilitate sharing of dating safety tips between participants.
Ask:
- What is safe behavior to you while using online dating apps?
- What do you consider when deciding to meet matches face-to-face?
- What are the strategies you have in ¨knowing¨ that it is safe to meet someone?
- Do you have back-up plans for when things go wrong? Check-in time for a friend? Or letting a friend know where you are going, who you are meeting, etc?
Write this on a flipchart or somewhere visible for participants.
Dating app (safety tips)
- Make sure your photo will not give more information, especially your location, the school you are studying in
- Use a secured and separate email address
- Don’t use a user name similar with your other social media account name
- Use a photo which is different from your social media account profile pictures.
- Don’t use personal information
- Be careful and deliberate when writing your profile on the dating app
- Offline follow up: Meet the person in a public place when meeting in person for the first time. If possible, inform a friend/family member about your meeting location and timing.
- Set a password on your applications when possible
- Password protect and encrypt your device
New models for dating
Are there any features you especially like about existing dating apps that you can look for in newer apps?
What possibilities and features do newer apps offer? (i.e., red-flagging users with bad reputation, documenting scammers, sharing tips about selecting matches).
In what ways are you already connecting with your trusted friends and community members around online dating?
Hands-on: Reboot your online dating safety - 60-90 minutes
Start with lightly Doxxing Yourself – see what information is available about your name in your dating apps. Using the information on your dating app profile, look for yourself on other platforms. Try searching for your username or information you share in your profile. Reflect on what information about you that is available outside the dating you don´t want to the dating app folks to know. Based on that, re-do your profile.
In pairs, go through the Safety Tips and update your profile. Share with each other and support your partner to point out if there is identifying information or if they can change more elements to be less identifiable and meet their own safety goals.
Reboot your pix
Check and replace any images including your profile and other account photos if they do not meet the safety tips you want to follow. Consider removing identifying metadata and removing identifying information about other people in the images.
Reboot your text
Check and rewrite your text if you are revealing more information that you would like to, considering your safety. Work with a partner to rewrite this if you want!
Set up a secure separate email address.
How was that? What was surprising? What was easy? What was hard? What are you doing to do next?
Facilitators: Are participants interested in sexting? Check out the safer sexting module.
Additional resources
Privacidad y seguridad en contextos conservadores: las apps de citas para mujeres de la diversidad sexual. Steffania Paola: https://www.genderit.org/es/articles/edicion-especial-privacidad-y-seguridad-en-contextos-conservadores-las-apps-de-citas-para
Self-Doxxing: https://gendersec.tacticaltech.org/wiki/index.php/Step_1#Self-Doxing
Dating App Safety Resources
- Grindr - https://help.grindr.com/hc/en-us/articles/217955357-Safety-Tips
- Planet Romeo - https://www.planetromeo.com/en/care/online-dating/
- Tinder - https://www.gotinder.com/safety
- OKCupid - https://www.okcupid.com/legal/safety-tips
- Hornet - https://hornet.com/community/knowledge-base/tips-on-how-to-stay-safe/
- Scruff - http://www.scruff.com/gaytravel/advisories/
Safer sexting [tactical activity]
This is a tactical activity in which participants share and practice safer sexting tactics.
Learning objectives this activity responds to
- an understanding of how mobile access and communications are gendered and intimate;
- an understanding of mobile communication safety from the perspective that mobile phones are our tools for both personal, private and public, movement communications;
- shared and practiced strategies and tactics for mobile safety to manage the impacts of our mobile communications on ourselves, our colleagues, our movements;
Who is this activity for?
People who are sexting or interested in sexting and who want to discuss and practice safer sexting.
Time required
This activity will require about 2 hours.
Resources needed for this activity
- Mobile data service
- Mobile phones
Mechanics
In pairs, discuss - 10 minutes
- Have you ever sexted? When was the first time you sexted? What were you using – landlines, notes, letters, postcards, online chat.
- How do you use your phone to sext? Apps, texting, voice, photo, video, etc, what do you like, what are pros and cons of these for you?
- What safety and privacy issues do you consider when you are sexting and what do you to to take care of your safety and privacy?
Facilitate participants sharing of what is fun and pleasurable about sexting with phones.
Intersectionality flag: Is there social stigma around sexting and how do participants of different genders, sexualities, races, classes, ages, experience this stigma differently? How do participants address social disapproval?
Discussion questions you might ask:
- What kinds of media do you like to use and which apps they like to use most. What do you like the most about this? What else do you wish you could do with the app, with media?
- What is the most fun you’ve had sexting and why?
Facilitator, prepare large pieces of paper with the following titles:
- Cumming to agreements
- The love we make, the data we share
- Apps and basic safety/device considerations:
- Wildcard
Facilitate a conversation with the guiding questions below. Make notes on the large paper with strategies shared by participants.
Cumming to agreements
- Make agreements with your sexting partners – what agreements do you want to make about saving, digital or in-person sharing?
- Have you ever negotiated sexting agreements with your partners, how do you do it?
- Breakups happen, how do you negotiate with your partners after a breakup about sexting? Do you keep yours, do they?
The love we make, the data we share
– information that goes with our photos and the stories it tells:
- Think if you want to share intimate images with your face visible
- Try to cover identifying features of your body, like tattoos, birthmarks etc.
- Use Exif editors to clear a photo’s metadata, geotag etc.
- Use apps to blur out face, tattoos etc. (like Pixlr)
Apps and basic safety/device considerations
- Choose an app that offers privacy and security features like encryption, message deletion, and screen-shot blocking
- Use a secure messenger to sext so that you have control on the images and messages sent, and you can delete them if you want.
- Jargon note: Self destruct - We use snapchat and other “self-destruct” promised apps, but often these are not entirely destructed and people are able to access the images for later distribution.
- Set a password and encrypt your device
- Set a password on your applications
- Consider using a secure email address and alternative phone number for your app account (app safety, so not just selection of apps or things to do with your sexting apps maybe as a sub section?)
- Know how to delete and save
- Consider if your app is syncing and whether and how you want to sync and store sexts
Hands-on: Safer apps and image editing
Discussion about choosing sexting apps
What apps are participants using for sexting and why? What safety concerns do you have choosing an app and what safety features do you like about your app? What are you concerned about?
Use apps that are:
- Encrypted
- Password protectable
- Prevent saving and screenshots
- Where messages can be deleted
Assessing SMS and MMS. SMS and MMS do not offer any of these features. See Activity: What is a phone? How does mobile communication work? For more information SMS and MMS and surveillance.
Hands-on activities
Facilitator, this activity is an opportunity for participants to practice safety strategies recommended by contributing trainers to the FTX Safety Reboot. Select whatever activities are most appropriate for your context. Some others to consider:
- Encrypting and password protecting a device
- Removing identifying information from photos and mobiles
- Set up a secure separate email address and phone number
Hands-on with images
- Practice taking photos without your face visible
- Try to cover identifying features of your body, like tattoos, birthmarks etc.
- Use Exif editors to clear a photo’s metadata, geotag etc.
- Use apps to blur out face, tattoos etc.
Hands-on with devices and apps
- Choose and install a secure app
- Set a password on your applications
- Know how to delete and save chats
- Know how to delete images from your device
How was that for you?
- What did you do?
- Prompt participants to share media if they are willing.
- What was hard, what was easy? What were you surprised about?
- Where did you look for information when you had questions?
Additional resources
Luchadoras' Sexting Workshop – moments of sexting like lead up, during, after. Storage and sharing, Shifting consent and consent in all these moment.
Trainers Notes As deleting images from apps and devices is a bit more complicated, here are some specific instructions to support participants to “Know how to delete images from your device” (last updated May 2019): Knowing how to delete images from your device requires understanding how to do this in your app memory and also knowing the location of where your images are stored in your mobile phone. On IoS devices this more opaque as you don't have access to files aside from the apps where the files are created. This also depends on whether or not you are using the chat apps to take photos, or you are preparing photos in advance (using the mobile phone's camera app).
For Telegram users, click on the header of a conversation, then look for Photos and Videos, you can delete images from there. This will delete the images from the Telegram app but if you had saved those images on another folder in your device, you will have to use a File Manager to do delete those. You can also look at and explore shared files with a specific user or a group.
On Signal, click on the header of a conversation. You will see thumbnails of Shared media. You can delete from there. Again, this will only delete the images / shared media on Signal, and if you had saved it elsewhere on your device, there will be a copy there. This also applies to who are sexting with.
For Android users, using a File Manager Removing media and images on Telegram: go to Internal Storage, and look for the Telegram folder >> Telegram Images / Telegram Video / Telegram Documents / Telegram Audio. Then delete the files in those folders. For Signal, if you save an image / media to away from Signal you can choose where to save it. Other places where your pictures / media could be: Internal Storage >> Pictures. You will generally get a directories (folders) that store your photos. By default, saved images from Signal get saved here.
Feminist principles of the internet
Conduct activities to introduce and enhance feminists' appreciation of the Feminist Principles of the Internet. Have interactive exercises that will open up the space for feminists to look at the internet as a political space as well as connect the FPIs to their specific areas of concern. We **highly recommended** that you choose a Learning Path to travel, as these include activities with different levels of depth that should help participants obtain more insight into the covered subjects.
Introduction, learning objectives, learning activities and further reading
This page will guide you through the Module's correct use and understanding. Following the Learning Paths, with activities of varying depth, should allow participants to obtain a better grasp of the studied subjects.
Introduction
This learning module aims to conduct activities to introduce and enhance feminists appreciation of the Feminist Principles of the Internet. It is designed to have interactive exercises that will open up the space for feminists to look at the internet as a political space as well as connect the FPIs to their specific areas of concern.
Who is the FPIs learning module for?
- on the ground feminist activists who are using mobiles and internet
- women´s fund donors (grantees, safety, explain why the internet is an important space)
- WHRDs running campaigns
- sexual rights activists
The commonality among these different groups is that they are all feminists, and most likely, they have not had the time to look at the internet from the lens of feminism and as a political space.
These groups will benefit from this learning module by understanding the internet – a space and tool that they use for their work – from a feminist perspective in order to make decisions about their use of the internet with more control and knowledge.
Learning objectives
Participants will:
- understand how to engage with the internet as a political space
- understand why we are imagining a feminist internet
- have a basic understanding of the feminist principles of the internet
- be excited about feminist politics of technology
- explore/engage with the FPIs and link to their areas of activism and contexts
Learning activities
The learning activities for this module are organised as Starter Activities – exercises that begin exploring the issues of the internet as a political space; and Deepening Activities – those that focus on specific aspects of the FPIs.
Depending on time, having a combination of a Starter Activity and Deepening Activities would be ideal to have a more comprehensive session on FPIs.
Starter activities

- Introductions of internet love
- Imagining a feminist internet (3 options)
- The internet race
- Women's wall of internet firsts
- How the internet works: The basics
Deepening activities

Resources | Links | Further reading
- https://feministinternet.org/
- Feminist_principles_of_the_internetv2-0.pdf
- FPIsand5LayersofPower_2020_by_hvale.pdf
- #MFI Africa: The e-zine! (2020)
- GenderIT edition "Making a feminist internet: Movement building in a digital age in Africa" (2020)
- GenderIT edition "Making a feminist internet: Building movements, remembering resistance, hacking security and care" (2017)
- GenderIT edition "Three key issues for a feminist internet: Access, agency and movements" (2016)
- Finding the feminist internet: students respond to the feminist principles of the internet (2020)
- Imagine a Feminist Internet (2019)
- Politics of a feminist internet in Zimbabwe: Resistance and Silence (2017)
- Zimbabwean Reflections on a Feminist Internet (2017)
- A painting of an African feminist internet (2017)
- The Do-It-Yourself Feminist Internet: Cyber feminist actions from Latin America (2016)
- Imagine a feminist internet: Participation and political movements (2015)
- Why do the Feminist Principles of the Internet matter? (2014)
- Imagining a digitally secure, feminist internet (2014)
- Why is the internet a feminist issue? (2012)

Introductions of internet love [starter activity]
This activity is aimed towards encouraging the participants to think about how beneficial the internet has been -- personally, professionally, in movement building and networking. This activity is especially useful for the beginning of a workshop and / or for participants who have a lot of negative sentiments for the internet.
Participants introduce each other with their name, organisation, country and one thing they love about the internet - personally, for their activism or in general. They cannot repeat what anyone else has said. This can be done standing in a circle to see each other clearly and encourage short interventions. To make sure no participant takes up too much time, one option is to have each participant light a match and finish before it burns down (have a container for the hot matches on hand.)
Resources needed for this activity
- matches
- something to hold hot stubs
Time required
10-15 minutes depending on the number of participants, approximately 40 seconds each.

Imagining a feminist internet (3 options) [starter activity]
Option 1
People work individually for 10 minutes to write down their definition/idea of a feminist internet. (Alternatively, to complete one of these sentences “In a feminist internet….” “A feminist internet is…”) It is time for them to explore and dream. It may be necessary to “warm up” the idea by asking for some basic ideas of what a feminist internet would look like. Each participant then reads their definition out loud to the whole group. As they read, the facilitator notes key words from their definitions on a flip chart. Their definition is taped to a wall for others to see, but their is no discussion on individual definitions.
Facilitators briefly summarise keywords that emerge and are recurring, aware of how these connect to concepts in the feminist principles of the internet and clusters. The discussion can deepen with participants defining what they found most important overall or simply provide an entry point to open a presentation or further exercise on the FPI.
Resources needed
Markers, paper, butcher paper, coloured post-it notes or colored paper cut in half sheets, blue tack or masking tape.
Time required
30-40 minutes total: 10 minutes to introduce and carry out individual work. 20-30 minutes to read out and analyse definition results, depending on the number of participants.
Option 2 - Imagine a feminist internet: Group work
The exercise is the same as above but designed for groups of 4. More time is necessary for group debate than report back.
Time required
35 minutes total - 20 minutes for group work, 15 minutes for report back.
Option 3 - Develop your internet dream space
(adapted from FTX: Safety reboot, creating safe online spaces)
Briefly ask participants in plenary: Why are we online? Why is it important to us? Ask participants for examples of things they are doing online that are significant to them, in different facets of their lives.
Ask them to imagine building their dream space on the internet, based on their answers to the two questions above. Invite them into small groups of 3-5 to imagine this space together.
- what is it called?
- why is this space significant?
- who and what is it for?
- what kinds of things do people do in this space?
- what are some of the rules in that place?
- what will the space look like?
- who has responsibility for managing the space?
Have the groups draw out this space as creatively as possible, and get them to prepare a creative presentation for the rest of the group. To add a more playful element, challenge the participants to try to convince the rest how great their space is – like a pitching an idea.
In plenary, as groups share back, the facilitator should write down key elements of all the spaces, aware of the feminist principles of the internet and connections.
These can serve as an input of elements to highlight when presenting the principles in the next exercise and to provide closure of common elements and key insights emerging from the groups.
Resources needed
Butcher paper, crayons or markers of many colors for each group, masking or blue tack
Time required
1 hour: 5 minutes in plenary, 25 minutes in group work, 30 minutes shareback and facilitator sumary.

The internet race [starter activity]
The aim of this activity is to illustrate the privilege that different people have when it comes to technology and the internet, and to show that there are sectors of society that are privileged on the internet. This activity could be used to start a discussion on the inequalities of different users based on technical, gender, language, age and race privilege.
Mechanics
Invite the participants to stand in one line, side-by-side. Where that line is will be the starting line, the facilitator moves across the room from that line. Let the participants know that the point of the game is to get to the finish line – where the facilitator is standing – based on the facilitator´s instructions.
The main point here is to show the inequalities among the participants when it comes to technology and the internet, specifically to challenge the very notion that technology and the internet are neutral.
Suggestions for instructions based on themes:
Note: These are suggestions only. Each context will have a different way of defining what being privileged on the the internet means. If a suggestion doesn't work in your context, think of another one that would. Remember, this also reflects the trainer / facilitators own biases and values around what privilege means.
Technical privilege
- If you understand what HTTPS means, take two steps forward
- If you understand what VPN means, take two steps forward
- If you use a VPN software, take three steps forward
- If you use Open Source software, take two steps forward
- If your Android phone is less than two years old, take three steps forward
- If you have the latest iPhone, take three steps forward
- If you have a laptop, a tablet and a mobile phone, take two steps forward
Language privilege
- If you read, write and speak English as a first language, take two steps forward
- If you read, write and speak English as a second language, take one step forward
- If you did not grow up with English as a language of daily communication, take one step back
- If you are more comfortable communicating with language that is not English, French, German, or Spanish, take two steps back.
- If you are more comfortable communicating in an Asian language, take two steps back
- If you can use the language that you are most comfortable communicating in on your computer, take one step forward
Race and geo-political privilege
- If you are American, take four steps forward
- If you are from North America and Western Europe, take three steps forward
- If you have been to the USA more than two times, take two steps forward
Gender privilege
- If you are a CIS male, take three steps forward
- If you are female, take two steps backward
- If you are queer, take two steps backward
- If you are trans, take two steps backward
- If you are heterosexual, take one step forward
Economic privilege
- Take a step forward for every credit card that you own
- If your gadgets are less than six months old, take four steps forward
- If your laptop is second-hand, take two steps backward
- If you have had your phone for over three years, take three steps backward
Experience-age privilege
- If you have been on the internet for longer than 7 years, take three steps forward
- If you started using the internet before Facebook, take three steps forward
- Note: People who have been using the internet since they were children or teenagers may be more comfortable with technology than older people.
- Alternative: If you've been using the Internet since childhood, take two steps forward
- Alternative: If you've been using the Internet since you were a teenager, take two steps forward.
Based on your context you can create new instructions, or mix and match the one above.
Debriefing on the activity
After the race is over (either someone reaches the finish line, or you´ve exhausted the instructions), ask everyone to stay where they are and process the activity:
- Ask the person in front of the race how they feel about winning the race
- Ask the person at the back of the race how they feel
- Ask the participants what they felt during the race
Once that has been processed, deepen the discussion with the following guide questions:
- What was the race all about?
- Based on the activity, what is it that the internet and technology privileges?
- What type of person is the internet and technology built for?
Write down keywords from the discussion on flip chart paper.

Women's wall of internet firsts [starter activity]
This activity is aimed towards acknowledging the various ways that women have interacted with the internet.
Resources needed for this activity
A big wall that you can stick paper to, sticky notes. You can also prepare a linear timeline indicating years and people place their sticky notes on the timeline.
Time required
Depending on number of participants and number of firsts, an hour.
Mechanics
In this interactive session, participants will discuss questions and share milestones in their use of technology, such as:
- The first time you ever used a computer
- When you first visited a web page
- When you first understood a computer-based concept and what is it
- First time someone taught you something about tech that was really cool
- The first time you taught someone technical skills
- The first time you showed someone a website – what was it?
- The first time you attended a tech training
- First time you flirted with someone online
- The first time you tried looking for information about a topic and couldn´t find anything about it on the internet
- The first time you experienced unsolicited sexual advances online
- First time you joined a group that shared an common interest with you on the internet – what was it?
- First time you felt unsafe
- First time you realised what kind of power the internet had – what was it?
Everyone will write down their short answers (date and / or topic) on sticky notes and pin them to the wall as they share. At the end of this activity, there will be a big wall of the first experiences the participants have had on the internet.

How the internet works: The basics [starter activity]
This starter activity is aimed towards getting the participants to understand the basic concepts and requirements for the internet.
Resources needed for this activity
Sheets of paper with the concepts
Time required
1.5 hours, minimum
Mechanics
Embodying the internet
Depending on the scenario that you want the participants to grasp, there will be some basic concepts required to be either illicited from the group or handed out on separate sheets of paper.
For the scenario, "How do you connect to <insert popular website>?", these are the basic concepts:
- Devices that connect to the internet: computer, laptop, mobile phone
- Router (can also be wifi connection)
- ISPs and / or Telco
- National gateway
- Destination webserver: Google, Facebook
- Servers
For the scenario, "How does Person A send an email to Person B?", the basic concepts are:
- Person A´s device (laptop, computer, mobile phone)
- Person A´s router
- Person A´s ISP / Telco
- Person A´s national gateway
- Person A´s mail server
- Servers
- Person B´s device
- Person B´s router
- Person B´s ISP / Telco
- Person B´s national gateway
- Person B´s mail server
For the scenario, "How do you send someone a chat message?", the basic concepts are:
- Person A´s mobile phone
- Person B´s mobile phone
- Person A´s ISP / Telco
- Person B´s ISP / Telco
- Person A´s national gateway
- Person B´s national gateway
- Person A and B´s chat service (Signal, Telegram, Vibr, WhatsApp)
- Chat service server
- Servers
Assign the different concepts to individual participants by making them stand in the centre of the room. Then ask them to do show the scenario.
Alternatively, you can group the participants according to the scenario, ask them to assign each concept to each member of the team and then role-play how the scenario would work in front of the bigger group. This option requires that there are participants that have some basic understanding of Internet 101.
This exercise can be expanded to illustrate HTTPS and PGP
For HTTPS, you will need an envelope provided by the web service to show the certification needed to encrypt data in transit. This could be used for both the scenario about connecting to websites, and sending emails.
For PGP, you will need envelopes that Person A and Person B would exchange with one another to signify the key exchange.
Interactive input on the how the internet works
This input will include the history of the internet as well as the history of the women´s movements on the internet (To be added).
This could also be a great exercise in data, corporate ownership, points of interception and surveillance.

Social movements: What’s in a tool? What’s in a space? [deepening activity]
Note: This is from the Movement Building module that the APC WRP developed.
Activity 1: What's in a tool? - 15 minutes
Participants are asked to think of their favourite tool. This can be a pen, a knife, a blender, anything. Have them write it down. Ask them 2 questions:
- Who do you think the tool is made for?
- What do you think it's designed for?
Facilitators guide
Draw out the idea that tools are designed with values embedded within them. They are not neutral, and that the design to some extent, affects/directs its utility.
Similarly, the tools that we use online, is designed with an end-user in mind. They can be gendered, heteronormative etc. Use some examples to draw this out. For example, dating sites are usually designed for heteronormative couples (also porn sites are designed for the male gaze), FB took a long time to allow for genders other than women and men to be included.
Open up a discussion to find participants' examples of how they see technology design as being embedded with values and assumptions, and how they may affect its utility.
Activity 2: What's in a space?
Resources needed
open space, quarter slips of paper and markers to write tool down.
Time required
45 minutes
Mechanics
Ask participants to remember their tools. Give them a challenge that they would have to solve:
- The room only allows people who are 6 feet and above to move around.
- You can only have a say if you have a chair, but you can only sit on a chair if you have a dog.
- The door to the room is 4 feet tall
Ask them to find others and work together. Think of how they can use their tools in creative ways for which the tool is not designed and collectively solve this problem. They can think out of the box, be as outrageous as possible. Share their solutions.
Hold a discussion on their thoughts about the exercise:
- How were you able to change the use of your tools? Did this transform its embedded assumptions and values?
- How were you able to change the rules/structure by working together?
- What did this tell us about transforming power? Our own, as well as power structures in the space we occupy?
Close the discussion with a brief input. Giving the #FBrape campaign as an example.
The Day the Everyday Sexism Project Won and Facebook Changed
Facilitators guide
In the discussion, make the connection between how the tool, the space and their actions connect and affect each other.
Talk about how the way a room is structured affects how we interact with each other. How the tables and chairs are placed together. Are they nailed to the floor? How much freedom can we have to move things around? Importantly, move from the idea of the internet as a tool to a space that also regulates our ability to interact with each other. That the design of this space also has particular assumptions embedded within them. E.g. that it's for a lecturer speaking to a classroom, or a workshop kind of space where you can move around more.
In other words, internet tools and platforms are not inert tools that we hold in our hands, but also a space that affects and structures our interactions.
Talk about how the internet is a space with many spaces within them. Like land where people build houses, but fantastical houses that shape-shift depending on how we occupy the space.
Also bring in the idea of different kinds of ways to access the houses. Some people only can enter through a small window (mobiles), and how this restricts to some extent your ability to move around in the house, what you can do to change it.
However, the more well resourced the house, the stronger it is. Harder to break the infrastructure. Like Facebook – harder to negotiate its values and how it is built, although not impossible. Bring the example of the #Fbrape campaign.
The #Fbrape campaign: details. Managed to change the policy of FB to look at rape pages more carefully. How this also had a knock-on effect on Twitter, and the norms that makes other house-builders/platform builders change the logic/values of house-building
Lesson
Users can change the norms and values of a space online. Norms and values that affects and regulates our interaction.
This exercise is useful to orient participants into positive thinking of the internet as a space of activism and action, rather than a space of aggression and a reactive feminist response.
Resources needed
flipchart paper, markers and masking tape
Time required
60 minutes: 15 mins for the 1st activity, 20 minutes of group discussion, 10 minutes of gallery walk, and 15 minutes of plenary discussion.
Mechanics
Ask the participants to reflect on one tool that they use for activism by processing these questions:
- What do you think this tool is for and how have you appropriated it for activism?
- Why have you appropriated this tool and not another one that is similar?
Divide the room into pairs (or groups of 4 depending on size of workshop). Decide on the movement/struggle that they are currently part of, or identify one significant and recent social movement in their own contexts.
Draw a mindmap of this movement and the different components. Ask: How has the internet transformed power relations in the following components:
- Individual power (How did it help to strengthen individual power. How did it allow new kinds of subjectivities to be recognised and named? E.g. Dalit women, transpeople etc – allowing them to be recognised as political subjects)
- Power of the collective, the coming together (How did it enable people to gather, congregate, come together)
- Actions that can be taken (Was there a diversity of actions? How did the online and offline actions speak to and strengthen each other?)
- Political goal (How did it help to communicate the shared goal? What was the emotive motivation that enabled the coming together)
- Space (of occupying, of taking action, of claiming and renaming)
- Time (what was it responding to, is it a sustained or an immediate thing? How long did it last?)
Participants walk around the gallery of the mindmaps.
Hold a plenary discussion to close this activity:
- How has the internet helped to transform power relations in the movement? See the brackets in the questions above as ways of prompting.
- How is it different from ways of organising before?
- How can we, as feminists/women's rights activists engage with the internet more as a political space?

FPI presentation + discussion [deepening activity]
This section is under construction.

Here is a FPIs presentation that you can use : FPIsand5LayersofPower_2020_by_hvale.pdf

Risk assessment
Introduce participants to the concepts that underlie risk assessment, and how to apply risk assessment frameworks to their personal and/or organizational security. We **highly recommended** that you choose a Learning Path to travel, as these include activities with different levels of depth that should help participants obtain more insight into the covered subjects.
Learning objectives and learning activities
This page will guide you through the Module's correct use and understanding. Following the Learning Paths, with activities of varying depth, should allow participants to obtain a better grasp of the studied subjects.
Learning objectives
By the end of this module, the participants will be able to:
- understand the concepts that underlie risk assessment
- apply risk assessment frameworks on their personal and / or organisational security
- come up with their own way of doing risk assessment that is relevant to their needs
Learning activities
Starter activities
- Introduction to risk assessment (presentation + discussion)
- Assessing communication practices
- Daily pie chart and risk
- The street at night
Deepening activities
- Re-thinking risk and the five layers of risk (presentation + discussion + group work)
- Data life-cycle as way to understand risk
Tactical activities
Foundational materials
Introduction to risk assessment [starter activity]

This activity is designed to introduce and exercise a framework for doing risk assessment.
Learning objectives
Learning objectives this activity responds to:
- Understanding the concepts that underlie risk assessment.
- Beginning to apply a risk assessment framework on their personal and/or organisational security.
Who is this activity for?
This activity is designed for participants who have basic or no experience of risk assessment. It is also designed for a workshop with participants from different organisations.
Time required
Realistically, this activity requires a day (eight hours, minimum) to do properly.
Resources
- Flip chart paper and markers
- Projector
- Laptops.
Mechanics
For this activity, create a scenario of an individual or group that the participants can practice doing a risk assessment on.
Depending on your participants, some options can be:
- A human rights group in a country that just passed a law to monitor NGOs
- A transwoman launching a website to support other transwomen
- A network of women’s rights advocates working on an issue that is considered taboo in their countries
- A group with a safe house for young transpeople
- A small LGBTIQ group under attack online
- A queer woman from a racial minority group posting their opinions online.
Break the participants down into groups. They can work on the same kind of organisation/group or work on different kinds of organisation.
Facilitation note: It is important here that the scenario resonates with the participants and that it is close to their experience.
Once everyone is in their groups, present the Basic risk assessment presentation.
Group work 1: Flesh out context and scenario
Before the groups can begin filling out the Risk assessment template, they should flesh out their chosen scenario.
For a group scenario:
- Create a profile for this organisation: location, size of the organisation, general mission of the organisation.
- Name their activities, or changes in their context, that put them at risk – this could be a new law, or they’re planning an activity that their detractors will want to interrupt. This could also be an internal shift that might present risks – e.g. a recent conflict within an organisation – or an external event that is causing significant internal stress among members of the organisation.
- Name who will be hostile to their actions, and who their allies are.
For an individual scenario:
- Create a profile for this individual: age, location, sexual orientation, how active they are on social media.
- Create the opinion they are being attacked for. Or describe the website they are creating that puts them at risk. Or the context situation that creates a vulnerable situation (e.g. being thrown out of their home, leaving an abusive relationship with someone in the same organisation or movement, etc.).
- Name who will be hostile to their actions, and who will support them.
Give each group an hour to do this.
Afterwards, have each group present their scenarios quickly.
Then present the Risk assessment template.
Some notes about the table:
- Threats should be specific – what is the threat (negative intention towards the individual group) and who is threatening them?
- Think about probability of a threat in three layers:
- Vulnerability – what are the processes, activities and behaviours of the individual or the group that increases the likelihood of the threat becoming real?
- Capacity of the people/person doing the threatening – who is making the threat and what can they do to enact it?
- Known incidents – has a similar threat been made with a similar scenario? If the answer is yes, then the probability increases.
- In thinking about impact, consider not just the individual impact, but the impact on a greater community.
- Assessing low/medium/high probability and impact will always be relative. But this is important to do in order to prioritise what risks to make mitigation plans for.
- Risk – this is a statement that contains the threat and the probability of it.
Group work 2: Risk assessment
Using the risk assessment template, each group analyses the risks in their scenario. The task here is to identify different risks, and analyse each one.
Facilitation note: Give each group a soft copy of the risk assessment template so they can document their discussions directly on it.
This group work will take at least two hours, with the trainer-facilitator consulting with each group throughout.
At the end of this, debrief with the groups by asking process questions rather than getting them to report back on their templates:
- What difficulties did your group have in assessing the risks?
- What were the main threats that you identified?
- What were the challenges in analysing probability?
Mitigation tactics input and discussion
Using the text for a presentation on mitigation tactics (see the Presentation section), present the main points and have a discussion with the participants.
Group work 3: Mitigation planning
Ask each group to identify a risk that is high probability and high impact. Then ask them to create a mitigation plan for this risk.
Guide questions
Preventive strategies
- What actions and capacities do you already have in order to avoid this threat?
- What actions will you take in order to prevent this threat from being realised? How will you change the processes in the network in order to prevent this threat from happening?
- Are there policies and procedures you need to create in order to do this?
- What skills will you need in order to avoid this threat?
Incident response
- What will you do when this threat is realised? What are the steps that you will take when this happens?
- How will you minimise the severity of the impact of this threat?
- What skills do you need in order to take the steps necessary to respond to this threat?
This group work will take about 45 minutes to an hour.
Afterwards, debrief by asking about the process and questions they have about the activities they have gone through.
To synthesise this learning activity, reiterate some lessons:
- Risk assessment is useful to come up with realistic strategies (preventive and responsive).
- Focus on the threats that have a high probability of being realised, and the ones with high impact.
- Risk assessment takes practice.
Presentation
There are three things to present in this activity:
- The basic risk assessment presentation
- The risk assessment template
- The mitigation tactics input (see text below).
Text for presentation on mitigation tactics
There are five general ways to mitigate risks:
Accept the risk and make contingency plans
Contingency planning is about imagining the risk and the worst case impact happening, and taking steps to deal with it.
Avoid the risk
Decrease your vulnerabilities. What skills will you need? What behavioural changes will you have to undertake to avoid the risk?
Control the risk
Decrease the severity of the impact. Focus on the impact and not the threat, and work towards minimising the impact. What skills will you need to address the impact?
Transfer the risk
Get an outside resource to assume the risk and its impact.
Monitor the risk for changes in probability and impact
This is generally for low-probability risks.
There are two ways to look at dealing with risks
Preventive strategies
- What actions and capacities do you already have in order to avoid this threat?
- What actions will you take in order to prevent this threat from being realised? How will you change the processes in the network in order to keep it from happening?
- Are there policies and procedures you need to create in order to do this?
- What skills will you need in order to prevent this threat from being realised?
Incident response
- What will you do when this threat is realised? What are the steps that you will take when this happens?
- How will you minimise the severity of the impact of this threat?
- What skills do you need in order to take the steps necessary to respond to this threat?
Adjustments for an organisational workshop
This activity can be used in a workshop context where the risk assessment is being done by an organisation, and the role of the trainer-facilitator is to guide the organisation through the process.
In order to do this, instead of fleshing out the scenario, have a discussion on the general threats that the organisation is facing. This could be a change in law or government that has implications on the organisation’s ability to continue its work. It could also be a specific incident when the people in the organisation felt that they were at risk (for example, a partner organisation discovering they are being surveilled, or the organisation itself being monitored). Follow that up with a discussion on what capacities the organisation already has – resources, connections, supporters and allies, and skills. Grounding a risk assessment activity by building common knowledge about the threats the organisation is facing and its capacities will be important for the rest of the process.
Break the participants up by team/unit as they go through the risk assessment template.
In this context, the mitigation planning is as important as the risk assessment template, so both areas will have to have equal time.
For an organisational context, this activity may take up to two days, depending on the size of the organisation and its operations.
Further reading (optional)

Assessing communication practices [starter activity]
This activity is designed to enable the participants to look at their communication practices (the topics that they communicate about, who they communicate with, their channels of communication) and assess where their risks are.
This activity is meant to be a diagnostic tool that can be used to prioritise training topics, and / or for the participants to use in assessing their communication practices.
Learning objectives
This addresses the understanding the concepts that underlie risk assessment.
Who is this activity for?
This is for participants that are beginners and intermediate.
Time required
Introduction to the activity: 15 mins
Individual time to assess: 15 mins
Group work: 30 mins
Plenum wrap-up: 30
Total: 1.5 hours
Resources
- Soft copies of the table. Or printed copies of this table
Mechanics
Ask the participants to fill in the table below.
| Topic of communication | Who do you communicate with about this topic | Is it sensitive?(Y/N) | Who will target you for this communication? | Communication channel |
|---|---|---|---|---|
| (Y/N?) | ||||
| (Y/N?) | ||||
| (Y/N?) | ||||
| (Y/N?) | ||||
| (Y/N?) |
After each participant has done their table, ask them to share their results with each other in groups.
At the end of the group work, ask each group to discuss with the bigger group the following questions:
- What are the topics that you communicate about that are sensitive?
- Who are the groups / communities / individuals that will target you for your sensitive communications?
- What is the most used communication channel that you use? Do you think it is secure and private?
This activity can then be used to prioritise which communication channels to focus on for the rest of the workshop, or to present alternatives to less private communication platforms.

Daily pie chart and risk [starter activity]
The purpose of this activity is to get the participants to assess what their daily or weekly tasks are, and analyse how much of their working time are spent on each task. There are two parts to this exercise, the creation of the pie charts of their weekly or daily tasks, which ends in a small sharing session of their results. And the second part is figuring out where in their tasks they feel most at risk. It is important for the facilitator to not bring up the idea of risk until the second part of the activity.
This is a very basic way to do risk assessment that focuses on the tasks that they do and known risks that they commonly face at work. This activity should be done with a deeper risk assessment activity.
Learning objectives this activity responds to
- Apply risk assessment frameworks on their personal and / or organisational security
Who is this activity for?
- For participants who have not done any kind of risk assessment.
- This works for groups that do almost the same things throughout their work days.
- This would work as a starter exercise for an organisation that is going to do an organisational risk assessment.
Time required
1.5 hours, minimum
Resources
- Flip chart paper + markers
Mechanics
First part: Draw your pie chart
Each participant will be given a piece of paper where they would be asked to draw a circle, and divide the circle with their daily or weekly tasks in the organisation. The divisions should reflect the time they spend per task.
For the facilitator: Encourage the participants to be as specific as possible in listing down their tasks.
At the end of the drawing period, the group comes back together and discusses the following questions:
- Which tasks do each of them spend time in the most?
- Which tasks do the different participants share?
- Which of the tasks they are not spending that much time on do they wish they could have more time for? And why?
Basically, just have an open discussion to process their pie charts.
Second part: Identifying work risks
Ask the participants to reflect on their pie charts and answer the following questions:
- Of the tasks you do for your organisation, which do you feel has the most risk? What kind of risk? And why?
- How are you able to address the risks that you have in that task? Describe your strategies.
Then come back to the big group and have a discussion.

The street at night [starter activity]
This activity is about bringing out how we practise assessing risks in order to live and survive. In this activity, a dark street at night will be shown to the participants so that they answer the question, “What would you do in order to navigate this street alone safely?”
The exercise is meant to bring out ways that we automatically assess threats and mitigate them in this specific situation.
Learning objectives
By the end of this activity, the participants will:
- Begin to understand that risk assessment is not a foreign activity.
- Share some experiences about what they consider when looking at a risky situation.
Who is this activity for?
This activity can be done with participants who have no experience with risk assessment as well as those who have done risk assessments in the past.
Facilitator’s note: It is important for the trainer-facilitator to be familiar with the group, as this activity might activate past trauma about navigating streets at night among some participants.
Time required
45 minutes
Resources
- A projector where you can show a picture of a street a night
- A board or flip chart paper to write down responses
- Markers.
Mechanics
Introduce the exercise by showing a picture of a street at night. It is also good to remind the participants that there are no right or wrong answers.
There are some examples provided here, but you can also take your own picture that will fit into your context.
Photo: Yuma Yanagisawa, Small Station at night, on Flickr.
Photo: Andy Worthington, Deptford High Street at night, on Flickr
Give the participants time to reflect on answering the question: “How would you navigate this street alone at night?”
Intersectional note: You do not want to assume that everyone has the same physical capacities and abilities. This is why we are using navigate instead of walk.
Ask them to write down their responses for themselves .
This should take no more than five minutes. You do not want the participants to over-think their answers.
Then spend some time getting the participants to answer the question one at a time. At this point, as a facilitator-trainer, you are just writing down the participants’ answers on the board or the flip chart paper as they speak them out.
Once you see some trends in their responses – common responses as well as responses that are unique – begin asking the participants for the reason why they responded that way.
At this stage, we are somewhat reverse-engineering the process. We started with the how’s, now we are getting to the why’s. Here, we are looking for the threats – the causes of danger – that they have assumed in their answers to the how’s.
Note down the threats as well.
It is also a good idea to look at the photo again to see elements in it that could pose a threat, or that could be seen as opportunities to allow a person alone to navigate it more safely.
For example, in the first photo:
- Point out the fences and the low bushes. Are there good hiding places?
- Which side of the road would you walk on and why?
- Given that it is a road where a small station is, does that mean that the person walking on it will have someone to reach out to, in case something happens? If so, does that make it safer to walk on this street?
- What about walking along this road to be safe from cars passing by?
In the second photo:
- Which side of the street would you walk on, and why?
- Point out the two people on the street – does their presence make the street feel safer or not?
- The van further down the street – could it be a possible vulnerability or a source of assistance in case something happens?
If you are planning to do your own night-time street photo, consider having the following elements in it:
- You can have a picture where it is clear where the light source on the street is coming from, and an obvious dark side of the street.
- You can have a picture with elements on the street that add more risk to it. For example, places where someone else can hide from the person walking. Or a street with a lot of vehicular traffic.
After spending a bit of time on the why’s of the safety tactics and the threats, ask the participants the question: “What other things do you need to know about this street in order to make better decisions about how to navigate it safely?”
Allow them time to reflect on their responses.
Then gather their responses, and write them down on the board.
Synthesise the session. Highlight some key points:
- The key strategies – the why’s and how’s – that emerged from the discussion.
- The key information needed about a situation in order to better assess it that emerged from the session.
- Connect the activity to risk assessment in that during this activity, the participants looked into a situation (the dark street) and made some decisions about their safety and security in relation to that situation based on context, experience and insight. And this was done quickly.
- Being safe as you travel through a dark street at night is a common experience. And in that moment, we are able to assess the risk – How dangerous is this street? How fast can I run? Are there points on this street where I can ask for help, just in case? Am I walking alone? Are there spots where someone else could surprise me on this street? – and apply strategies and tactics to mitigate them. We mitigate risks instinctively – as a survival mechanism. Remembering this is important to do when you get into risk assessment.
- Knowing the potential risks in this specific situation has made it possible for each of us to come up with strategies and tactics to decrease our risks in the given situation.
Facilitator’s notes
- It is really important in the first part of this activity, during the participants’ reflection on how they would navigate the street safely by themselves, that they do not over-think. That is why five minutes is enough. What we want to highlight here is the importance of instinct and lived experience in assessing risks in a given situation.
- If you sense that a participant or all of them are being activated by having to respond to the experience of walking down a dark street, take a break. Give the participants a chance to breathe. Also allow participants to opt out of this activity.
- The point of this activity is to begin exploring assessing risks. It is not important here to match this activity to the standard formula, risk = threat x probability x impact / capacity. What is important is for the participants to be able to articulate the reasons why they decided on specific tactics for navigating the dark street at night.
- Reiterate that there are no right or wrong answers, only answers based on experience and reasoning.
- If you find, based on your knowledge of the participants, that doing an activity about navigating a street alone at night may activate their past trauma, you can alternatively choose to run this activity using a crowded street during the daytime, as that might not be as traumatic for participants. Or a crowded street at night, which can present different kinds of elements for thinking through risk. Here are some example photos that you can use:
Photo: Carl Campbell, El Chopo Saturday Market crowds, on Flickr.
Photo: Waychen C, Shilin Night Market, on Flickr.

Re-thinking risk and the five layers of risk [deepening activity]

At the moment, what we have is a some ideas about how to re-think risk. This has not been converted into a learning module.
Re-thinking risk and assessing risk
Realistically understanding risk
One of the challenges in risk assessment as we know it is the breadth of what we mean when we say ¨risk¨. To think about risk with a holistic approach even further widens what we mean by it (rightly so). The purpose of assessing risk is for an person to be able to come up with strategies and tactics to mitigate the risks that she faces, and to be able to make more informed decisions.
Often ¨Risk¨ is seen as anything that can go wrong in a situation without nuancing what risks one can focus on.
Another way of having a more nuanced assessment of risk is to think about it from three different angles:
- Known risks: Threats that have already been realised within the community. Cite examples. What are causes? What are its impacts?
- Emerging risks: Threats that have occurred but not within the community that the person belongs to. These could be threats that result from emerging threats from current political climates, technological developments, and / or changes within the broader activist communities.
- Unknowable risks: These are threats that are unforeesable and there is no way of knowing if and when it will emerge.
Another way to start thinking about risks is to consider these following layers: 
Infrastructure / space layer
This layer is the space in which we move, communicate and interact. These are the offline and online spaces where we practice our activism. Wherever it is that we are located, there are parameters and those parameters may be sources of risks.
For example, the one known fact about the internet is that nothing in it can be permanently deleted. What kind of risks does this post for activists on the internet? How can this fact contribute to an escalation of threats?
Movement (counter-movement)
The next level is confronting the movements that we belong to, and who our opponents are. What are our movements´ capacities? And what are our opponents´? What are the risks that we face by default as part of feminist movements? Who are our allies? Who are our enemies? And what threats do they pose to us?
Thinking about risks in movement terms will also expand our understanding of the impacts of realised threats? What are the consequences, beyond the individual or organisational, of the gender-based harassment on the internet? How does it affect the way our movements are able to use the internet for our advocacies?
Relational / interpersonal layer
One of the assumptions that many activists do not confront is that the distrust and mistrust that exists within activist communities. It is important to build relationships of trust, yes. It is equally important to determine the levels of trust that exist between and among feminist activists.
Individual behaviour / practices
How do each of communicate? How do we get on the internet? What are the pre-existing realities that we individually exist in during our moments of interaction? What kind of equipment do we have access to? What kind of tools do we use? What skills do we have? The individual behaviour / practices answers these questions.
In order to understand risk deeper, it is important to interrogate these layers.
Continuum of behaviour / practice and threats
In this framework, we start with a known threat (or the ones that our participants will have had experience in) and interrogate the behaviour / practices that make the threat real and how the threat can escalate as well as the further behaviour / practices that allow the threat to escalate.
The second level for this framework would be identifying mitigation and responsive strategies at every point in the image.

The data life cycle as a way to understand risk [deepening activity]
Look at risk assessment from the perspective of the data life cycle. Activists, organisations and movements all deal with data – from gathering/creating/collecting data to publishing information based on data.
Introduction and mechanics for a general workshop

This learning activity is about looking at risk assessment from the perspective of the data life cycle. Activists, organisations and movements all deal with data – from gathering/creating/collecting data to publishing information based on data.
There are two main approaches to the mechanics of this activity:
- The general workshop is for a general digital security workshop, where the participants come from different organisations and/or don’t belong to any organisations.
- The organisational workshop is meant for a specific group and its staff. The general context for this type of workshop is that different teams within an organisation come together to to do a risk assessment of their organisational data practice and processes.
The learning objectives and the general topics/themes covered in both approaches are the same, but the facilitation methodologies and techniques will need to be adjusted for two different kinds of workshop scenarios.
Learning objectives
Through this activity, the participants will be able to:
- Understand risk and security considerations in each phase of the data life cycle.
- Apply risk assessment frameworks to their personal and/or organisational security.
Who is this activity for?
This activity is meant to be for individual activists (in a general risk assessment or digital security workshop), or for a group (an organisation, network, collective) undergoing a risk assessment process. There are two mechanics and approaches for this activity, depending on whether it is a general workshop or a workshop for a specific group.
It can also be used as a diagnostic activity in order to prioritise which practices or tools to focus on for the rest of a digital security workshop.
Time required
This depends on the number of participants and the size of the group. In general, this activity takes a minimum of four hours.
Resources
- Flip chart paper
- Markers
- Projector to present the data life cycle and the guide questions and for participant share-backs, if needed.
Mechanics
(This is for a general risk assessment or digital security workshop, where activists from different contexts come together in a training. The learning objectives remain the same but some of the training and facilitation tactics would differ from a workshop for a more established group of people.)
Phase 1: What do you publish?
In this part of the activity, the participants are asked: What do you publish as part of your work as an activist?
The point here is to start with the most obvious part of the data life cycle – processed data that is shared as information. This could be research reports, articles, blog posts, guides, books, websites, social media posts, etc.
This could be done in plenary, popcorn style. This is when the facilitator posts a question and asks for short and brief answers from the participants – like corn popping in a pan!
Phase 2: Presentation of the data life cycle and security considerations
The presentation is aimed at reminding the participants about the data management cycle. The key points for the presentation can be found here (see cycle-basics-presentation.odp).
Phase 3: Reflection time about personal data life cycles
Group the participants according to what they publish. Ask them to choose a specific example of something that they have published (an article, a research report, a book, etc.), and ask them to form groups based on similar work.
Here, there will be time for each of them to track the data life cycle of that published output, and then time as a group to share their reflections.
Reflection time should be about 15 minutes. Then group discussion would take about 45 minutes.
The guide questions for individual reflection time will be the considerations in the presentation.
For the group work, each group member will share the data life cycle of their published work.
Phase 4: Share-back and security considerations
Instead of having each group report back, the trainer-facilitator asks each group questions that will surface what was discussed in the groups.
Here are some questions you may use to debrief on the reflection time and the group discussion:
- What are the data storage devices that were most common in the group? What were the ones that were the only one used?
- What were the differences and commonalities in access to the data storage in your group?
- What about data processing? What tools were used in your group?
- Did anyone in the group publish something that put them or someone they know at risk? What was it?
- Has anyone in the group thought about archiving and deletion practice before today? If so, what were the practices around this?
- Were there safety and security concerns at any part of your data life cycle? What are they?
Synthesise the activity
At the end of the group presentations and sharing, the trainer-facilitator can synthesise the activity by:
- Pointing to key points made.
- Asking participants for key insights from the activity.
- Asking participants about changes in their data management practice that they learned about during the activity.

Mechanics for an organisational workshop
This is for a workshop for an organisation and its staff.
Phase 1: What information does each unit/programme/team of the organisation share?
Based on the configuration and structure of the organisation, ask each unit or team for an example of one thing that they share – within the organisation or outside the organisation.
Some examples to encourage response:
- For communications units – what are the reports that you publish?
- For research teams – what is the research that you report on?
- For administration and/or finance teams – who gets to see your organisation’s payroll? How about financial reports?
- For human resources departments – what about staff evaluations?
Facilitation note: This question is much easier to answer for teams that have outward-looking objectives, for example, the communications unit, or a programme that publishes reports and research. For more inward-looking units, like finance and administration or human resources, the trainer-facilitator may need to spend time on examples of what information they share.
The goal in this phase is to get the different teams to acknowledge that they all share information – within the organisation or outside of it. This is important because each team should be able to identify one or two types of information that they share when they assess risk in their data management practice.
Phase 2: Presentation of the data life cycle and security considerations
The presentation is about reminding the participants about the data management cycle. The key points for the presentation can be found here (see file cycle-basics-presentation.odp).
Phase 3: Group work
Within teams, ask each group to identify one to two types of information that they share/publish.
In order to prioritise, encourage the teams to think about the information that they want to secure the most, or information that they share that is sensitive.
Then, for each type of shared or published information, ask the teams to backtrack and look at its data life cycle. Use the presentation below to ask key questions about the data management practice for each piece of published or shared data.
At the end of this process, each team should be able to share with the rest the results of their discussions.
In general, the group work will take about an hour.
Phase 4: Group presentations and reflecting about safety
Depending on the size of the organisation and the work that each unit has done, give them time to present the results of their discussion to their co-workers. Encourage each team to think about creative presentations and highlights of their discussions. They do not need to share everything.
Encourage the listeners to take notes about what is being shared with them, as there will be time to share comments and give feedback after each presentation.
Realistically, this will take about 10 minutes/group.
The role of the trainer-facilitator here, aside from timekeeping and managing feedback, is to also provide feedback to each presentation. This is the time to put on your security practitioner hat.
Some areas to consider asking about:
- If the data gathering process is supposed to be private, wouldn’t it be better to use more secure communications tools?
- Who has access to the storage device in theory and in reality? In the case of physical storage devices, where are they located in the office?
- Who gets to see the raw data?
As a trainer-facilitator, you can also use this opportunity to share some recommendations and suggestions to make the organisation’s data management practices safer.
Facilitator’s note: There is a resource called Alternative Tools in Networking and Communications in the FTX: Safety Reboot that you might want to have a look at to guide this activity.
Phase 5: Back to the groups: security improvements
After all of the teams have presented, they return to their teams for further discussion and reflection on how they can better secure their data management processes and data.
The goal here for each group is to plan ways to be safer in all of the phases of their data life cycle.
By the end of this discussion, each team should have some plans as to how to be more secure in their data practice.
Note: The assumption here is that the group has undergone some basic security training in order to do this. Alternatively, the trainer-facilitator can use Phase 4 as an opportunity to provide some suggestions for more secure alternative tools, options and processes for the group’s data management practice.
Guide questions for group discussion
- Of the types of data that you manage, which ones are public (everyone can know about them), private (only the organisation can know about them), confidential (only the team and specific groups within the organisation can know about them) – and how can your team ensure that these different types of data can be private and confidential?
- How can your team ensure that you are able to manage who has access to your data?
- What are the retention and deletion policies of the platforms that you use to store and process your data online?
- How can the team practise more secure communications, especially about the private and confidential data and information?
- What practices and processes should the team have in place in order to preserve the privacy and confidentiality of their data?
- What should change in your data management practice in order to make it more secure? Look at the results of the previous group work and see what can be improved.
- What roles should each team member have in order to manage these changes?
Phase 6: Final presentation of plans
Here, each team will be given time to present the ways that they will secure their data management practice.
This is an opportunity for the entire organisation to share strategies and tactics, and learn from each other.
Synthesising the activity
At the end of the group presentations and sharing, the trainer-facilitator can synthesise the activity by:
• Pointing to key points made.
• Asking participants for key insights from the activity.
• Agreeing on next steps to operationalise the plans.
Presentation
Another way to understand risks in increments is to look at an organisation’s data practice. Every organisation deals with data, and each unit within an organisation does as well.
Here, there are some security and safety considerations for each phase of the data life cycle.
Creating/gathering/collecting data
- What kind of data is being gathered?
- Who creates/gathers/collects data?
- Will it put people at risk? Who will be put at risk for this data being released?
- How public/private/confidential is the data gathering process?
- What tools are you using to ensure the safety of the data gathering process?
Data storage
- Where is the data stored?
- Who has access to the data storage?
- What are the practices/processes/tools you are using to ensure the security of the storage device?
- Cloud storage vs physical storage vs device storage.
Data processing
- Who processes the data?
- Will the analysis of the data put individuals or groups at risk?
- What tools are being used to analyse the data?
- Who has access to the data analysis process/system?
- In the processing of data, are secondary copies of the data being stored elsewhere?
Publishing/sharing information from the processed data
- Where is the information/knowledge being published?
- Will the publication of the information put people at risk?
- Who are the target audiences of the published information?
- Do you have control over how the information is being published?
Archiving
- Where are the data and processed information being archived?
- Is the raw data being archived or just the processed information?
- Who has access to the archive?
- What are the conditions of accessing the archive?
Deletion
- When is the data being purged?
- What are the conditions of deletion?
- How can we be sure that all copies are deleted?
Facilitator’s notes
- This activity is a good way to be able to know and assess the digital security contexts, practice and processes of participants. It is a good idea to focus on that aspect rather than expect this activity to yield strategies and tactics for their improved digital security.
- For an organisational workshop, you may want to pay attention to the human resources and administration teams/units. First, in many organisations, these are usually the staff members who have not had prior digital security workshop experience, so many of the themes and topics may be new to them. Second, because a lot of their work is internal, they may not see their units as “publishing” anything. However, in many organisations, these units hold and process a lot of sensitive data (staff information, staff salaries, board meeting notes, organisational banking details, etc.) – so it is important to point that out in the workshop.
- Pay attention to the physical storage devices as well. If there are file cabinets where printed copies of documents are stored, ask where those cabinets are located and who has physical access to them. Sometimes, there’s a tendency to focus too much on online storage practice, and they can miss out on making their physical storage tactics more secure.
Further reading (optional)
- FTX Safety Reboot: Alternative Tools in Networking and Communications
- FTX: Safety Reboot :Mobile Safety Module
- Electronic Frontier Foundation's Surveillance Self-Defense – while this is largely for a US-based audience, this guide has useful sections that explain surveillance concepts and the tools used to circumvent them.
- Front Line Defenders' Guide to Secure Group Chat and Conferencing Tools – a useful guide to various secure chat and conferencing services and tools that meet Front Line Defenders’ criteria for what makes an app or service secure.
- Mozilla Foundation's Privacy Not Included website – which looks at the different privacy and security policies and practices of different services, platforms and devices to see they if match Mozilla's Minimum Security Standards, which include encryption, security updates, and privacy policies.

Organising protests and risk assessment [tactical activity]
Guide a group of people who are planning a protest into reflecting about and addressing the risks and threats that they may face. This activity can be applied for protests that are offline or online as well as protests that have offline and online components.
Introduction

This activity is about guiding a group of people who are planning a protest into reflecting about and addressing the risks and threats that they may face. This activity can be applied for protests that are offline or online as well as protests that have offline and online components.
This is not a protest planning activity but rather a risk assessment activity for a protest. It is assumed that before this activity is held, the group has already done some initial planning for what the protest will be about and its main strategies, tactics and activities.
Learning objectives
Through this activity, participants will learn to:
- Understand the different risks that they face in carrying out protest activities.
- Create a plan to respond to the identified risks in order to carry out a more secure protest.
Who is activity for?
This activity is useful for a group of people (organisation, network, collective) who have agreed to plan a protest together.
The group should have had initial planning about their protest, so the main strategies, tactics and activities have been discussed and agreed upon prior to this activity.
Time required
This activity will take a minimum of four hours.
Resources
- A big wall where sticky notes and flip chart paper can be pinned. If there is not a well suitable for this purpose, there should be a space cleared on the floor where participants can do this work together.
- Markers.
- Sticky notes.
- Devices where discussions can be electronically documented. It is important to assign people in the group to document the discussions and make sure that if the documentation is shared, it is via secure channels.
Mechanics for a workshop for a group planning a shared protest
This activity has three main phases:
- Phase 1 is about looking at risk from the angle of organisers, supporters and adversaries as sources of threats (direct and indirect threats as well as confronting ways that the protest can fail). Phase 1 is broken down into three different exercises that are designed for the group to arrive at a shared understanding of the possible risks that their planned protest is facing.
- Phase 2 is about strategising ways to mitigate possible vulnerabilities and failures of the protest, and what roles organisers have in the mitigation plan.
- Phase 3 focuses on operationalising secure internal communications among the participants.
Phase 1: Assessing where risks can come from
This phase has a few levels of participation and interaction in order to assess where the risks for the protest may be coming from. To make the mechanics clearer, the different levels have been marked as “exercises”.
Prepare a sheet of flip chart paper for each of the following:
- Organisers of the protest: Groups and individuals involved in planning the protest. They also include allies.
- Supporters: Groups and individuals that you expect to take part or participate in the protest actions.
- Adversaries of the protest: Groups and individuals who will be negatively affected by this protest as well as those that support them.
- Activities of the protest: The planned actions for the protest and where those actions are happening. Activities can be both online activities and offline activities.
Exercise 1: Naming the who and what of the protest
Give the participants time and space to fill in each of these sheets of flip chart paper with sticky notes with their responses. Alternatively, they can also just write directly on the flip chart paper.
Facilitation note: To do this in a more organised way, especially if the group is made up of more than seven people, break the participants into four groups. Each group will work on one sheet of flip chart paper first. One can start with “Organisers of the protest”, and another group can start with “Supporters of the protest”, and so on. Give them time to fill in their answers for their sheet of flip chart paper, then ask them to move to the next sheet until all groups have had time with each one. This is usually called the World Cafe methodology.
Exercise 2: Unpacking organisers, supporters and adversaries
After all the sheets of flip chart paper are filled with answers, get the participants to break out into two groups:
- Group 1 will take the flip chart paper for the organisers and supporters
- Group 2 will take the flip chart paper for the adversaries
The flip chart paper on Activities will be left in the common area for everyone’s reference.
Each group will have their own set of guide questions to start unpacking where the risks are in their focus areas.
For organisers and supporters, the guide questions are:
- Who among the organisers is currently facing threats? What are they? How can that impact the protest?
- Are there internal conflicts among the organisers? Tensions that we should be aware of? What might the potential impact be to the organising?
- Among the supporters that we expect, who among them have the potential to receive a lot of backlash?
- What are the threats of backlash that can be anticipated? Have there been similar protests that received backlash before? What was it?
- Where would the backlash or attacks happen? Do you know which social media spaces are especially targetted by adversaries? What might the impact of the backlash be on offline realities, during or after the protest?
For adversaries, the guide questions are:
- Who among this list of adversaries will be most active against the protest?
- Where do they congregate? Where do they congregate offline and online?
- Who are the leaders or influencers among the adversaries?
- What capacities do they have?
- What is it that they can do against the protest and those involved?
- How can the adversaries affect the planning of the protest?
- How can they disrupt the planned activities during the protest?
- What might post-protest backlash look like? How might adversaries try to disrupt the message of the protest through backlash? Who would they target? Where would this take place, and what is the role of social media in this?
Facilitation note: Most protests these days will have online and offline components. The questions above are applicable to both online and offline scenarios, protests and contexts. But, if you observe that the participants are focusing too much on offline contexts, then perhaps prompt them with questions about the online contexts of their organisers, supporters, and adversaries. If they are tending to focus on the online factors, then prompt them with questions about offline contexts. Prompt them on how the online activities or events can impact on offline activities or events, and vice versa.
The group discussion should take about 45 minutes to one hour.
At the end of the group discussion, each group will share back their discussion results. For the share-back, each group should focus on the following questions:
For the organisers/supporters group:
- Who among the organisers/supporters are currently facing threats? What threats are they facing?
- What kind of backlash are you expecting the organisers and supporters to face for participating in the protest?
- Were there internal conflicts or tensions that might pose a risk to the protest, and what might those be?
For the group that worked on adversaries:
- Who among the adversaries will potentially take action to disrupt the protest?
- What kind of disruptions do you expect from them?
- How does this look different for different stages of the protest: planning, during and post?
It is also a good idea to ask the groups to be as specific in their share-backs as they can be.
Exercise 3: Reflecting on possible failure
This exercise is about surfacing some of the possible ways that the protest can fail.
After this, all the participants will be given some time to reflect on this question: What do you NOT want to happen in this protest?
To further unpack this big question, you might want to raise these questions to prompt the group:
- Think about your organisers and supporters – what possible negative effects can this protest have on them?
- If the protest is happening offline and online, then how can your adversaries disrupt the protest in both spaces?
- Think about the spaces of your protest activities – what do you not want to happen to them?
- Think about your protest activities – what can cause them to fail?
Ask them to reflect on the discussions they’ve had and the share-backs they’ve listened to. Ask them to write down their answers on separate sticky notes and then have them post them up on the wall after a few minutes of reflection.
Cluster the responses to come up with general themes to discuss further.

Phase 2: Planning mitigation strategies and tactics
Exercise 1: Group work to mitigate possible vulnerabilities and failure
Based on the clusters from Exercise 3 of Phase 1, divide the participants into groups.
Each group will discuss the following questions:
- What can you do to prevent this negative outcome?
- What strategies, what approaches, what safety protocols will be required to avoid it?
- Are there different strategies for the planning stage, during the protest itself, and after?
- What will you do if this potential negative outcome becomes real? What steps will you take?
- Who should lead these strategies?
By the end of the discussion, each group should have a list of approaches and strategies as well as security protocols (rules) in relation to the negative outcome. These should be listed down on flip chart paper and/or documented electronically. Organise these according to the different stages of the protest: before, during and after. Each group will present their lists to the rest for discussion.
The role here of the trainer-facilitator is to provide feedback on the approaches and strategies, suggest improvements (if needed), and find common strategies among the groups.
Exercise 2: Discussion about roles
In the big group, have a discussion on the roles necessary to mitigate negative outcomes, adhere to security protocols, and manage secure communications – before, during and after protest activities. It would be important for the group to finalise these roles and who will fill them.
Phase 3: Communicating securely
Here, the trainer-facilitator can present options for secure communications for the group as they carry out the protest.
Then, the group can spend time installing and making sure that they are able to communicate with each other through the chosen channel.
To help you plan this, read Alternative Tools for Networking and Communications and the Mobile Safety module.
Security note: One of the ways that you can exercise these tools is to make sure that the people who are documenting are able to share copies of their notes and documentation via secure communication channels.
Adjustments for a general workshop
In general, risk assessment activities are more effective when they are done with groups that have common goals, contexts and risk scenarios (i.e. organisational risk assessment interventions, or risk assessment for a network of organisations). Therefore, this activity was designed for a group of participants who are already planning to carry out a protest together and have done some initial planning about their shared protest. But the activity can be adjusted for a more general digital security scenario of individuals from different contexts who are thinking about organising their own protests with their groups.
In order to adjust this activity for more general use, having a sample protest will be a good way to get the participants to practice this activity, and learn lessons that they can bring back to their groups/networks/collectives so that they can assess the risk of their actual protests.
Some guidelines about creating a sample protest:
- Locate the protest in reality: It is important to locate the protest in a real context, because then the sample protest will have the boundaries and parameters of an actual protest, and the participants will be able to be more specific in their analysis and their strategies.
If all the participants are from the same country, then locate the protest in that country. If they are from different countries, then have a regional protest. - Design a sample protest for an issue that resonates with the participants: This way, the protest will be familiar to the participants even though it is an imaginary one. They would have organised and/or participated in one in the past.
- State the protest demands or objectives: Make them clearly related to the issue at hand, to help with the exercise.
- Design offline and online protest activities: Make sure that when you identify the protest activities, you have a combination of online and offline tactics. Be specific about these activities – where will they happen, when will they happen, how long will these activities last?
- Base it on an actual protest: If you know of a protest that can work for the participants in your workshop, then use that as the sample protest.
The key in creating a sample protest is to try to simulate as much as you can a real protest scenario. Again, risk assessment activities are most effective with specifics.
You will also need to find ways and adjust your timing so that the participants can learn and absorb the sample protest. You can share the sample protest details before the training, but don’t assume that everyone has had time to read before the workshop. You can present the sample protest at the start of the workshop and give the participants hand-outs so that each group will have the information available to them as they go through the phases and exercises of this activity.

Risk assessment basics [foundational material]
Introduction
We assess our risk all the time. This is how we survive. It is a process that is not unique to digital and/or information security.
When take a walk at night on a quiet street, we make decisions about which side of the street to walk on, how to behave, what to prepare, how to walk, based on our understanding of the situation: Is this street known for being a dangerous one? Is the community where this street is a dangerous one? Do I know anyone on this street who could come to my aid? Can I run fast, if something happens? Am I carrying anything of value that I can bargain with? Am I carrying anything that can put me in greater harm? Which part of this street can I walk on to avoid possible harm?
When our organisations plan a new project, we consider the ways in which it could fail. We make design decisions based on what we know of the context and the factors in it that would lead to the project not achieving its goals.
When we organise protests, we look at ways to keep the protest and those in it safe. We organise buddy systems. We make sure there is immediate legal support in case of arrests. We instruct those attending about how to behave to avoid being harassed by authorities. We strategise ways in which to conduct a protest peacefully in order to lessen the risk to those participating. We have people in the protest whose responsibility is to maintain its safety.
While assessing our own risks may be a practice that we do instinctively, risk assessment is a specific process we undergo – usually as a collective – in order to know how we can avoid threats and/or respond to those threats.
Risk assessment: Online and offline
Assessing our risks online is not as instinctive, for various reasons. Many of us do not understand how the internet works and where its threats and risks are – and these continue to evolve and grow. Some have the attitude of perceiving online activities, actions and behaviour as not being “real”, with less serious effects than what happens to us physically. At the other end of the spectrum, those that know of or have experienced incidents where a person’s “real” life was affected by their online activities (people being scammed on dating sites, people whose taboo internet interactions were made public, or activists being arrested for saying something against their government) tend to have a paranoid view of the internet.
The reality is that for many activists, the online/offline binary is false. The use of digital devices (mobile phones, laptops, tablets, computers, etc.) and internet-based services, apps and platforms (Google, Facebook, Viber, Instagram, WhatsApp, etc.) is commonplace in the work of many activists – in organising and in advocacy work. How we organise and do our work as activists has evolved as technology has advanced and developed – and will continue to do so. The internet and digital technologies are a critical part of our organising infrastructure. We use them in communicating, organising activities, building our community, and also as a site of our activities. In-person gatherings and advocacy events are often accompanied by online engagement, especially on social media and through hashtags. In recent protest movements, there is often a seamless flow between online and offline mobilising, organising and gatherings.
Instead of perceiving what happens on the internet as something separate from our physical realities, think of offline <-> online realities as interconnected and porous. We exist in both, most of the time, at the same time. What is happening in one affects how we are in the other one
This also means that the risks and threats move from online to offline and vice versa. For example, advanced state surveillance strategies against activists and their movements exploit un-secure use of technologies (i.e. clicking on unverified links, or downloading and opening unverified files) in order to be able to gather more information about activists and their groups and movements that may eventually lead to physical surveillance. Anyone who has experienced online gender-based violence (OGBV) knows the psycho-social effects of such attacks and harassment. There have also been cases where OGBV has escalated to affecting the physical security of those who have been targeted. Different forms of OGBV (stalking, doxxing, harassment) have been tactics used against feminist and queer activists in order to threaten them into silence and compliance.
Thinking about the porous online <-> offline nature of threats and risks can be overwhelming – where do we begin assessing and knowing what the threats are and where they are coming from, and strategising what to do about them?
What is risk assessment?
Risk assessment is the beginning of a process to become more resilient in responding to changing contexts and threats. The purpose of assessing risk is to be able to come up with strategies and tactics to mitigate the risks, and to be able to make more informed decisions.
In general terms, risk is the exposure to the possibility of harm, injury or loss.
In risk assessment, it is the capacity (or lack thereof) of an individual/organisation/collective to respond to the impact(s) of a realised threat, or the capacity of an individual/organisation/collective avoid a threat from being realised.
There is a known formula for risk assessment:
Risk = threat x probability x impact/capacity
Wherein:
- Threat is any negative action aimed towards a person/group.
- Direct threats are declared intention to cause harm.
- Indirect threats are those that happen as a result of a change in a situation.
- In defining threats, it is important to identify where the threat is coming from. Even better, who is the threat from.
- Probability is the likelihood of a threat becoming real.
- A related concept to probability is vulnerability. This can be about location, practice and behaviour of the individual/group that increase the opportunities for a threat to be realised.
- This is also about the capacity of the groups/individuals that are making the threat, especially in relation to the individual/group that is being threatened.
- To assess probability, ask if you have real examples of a threat happening to someone or a group that you know – and compare that situation with yours.
- Impact is what will happen when the threat is realised. The consequences of the threat.
- Impact can be on the individual, organisational, network or movement.
- The higher the degree and number of impacts of one threat, the greater the risk.
- Capacities are skills, strengths and resources a group has access to in order to either minimise the probability of the threat, or respond to the impact of the threat.

Case study - threats and mitigation
Case study: Deya
To illustrate this, let’s use the fictional but fairly common experience of Deya. Deya is a feminist activist who uses her Twitter account to call out those who promote rape culture. As a result of this, Deya has been been harassed and threatened online.
The threat she is most concerned with are the people that promise to find out where she lives and share that information on the internet to invite others to cause her physical harm. In this case, the impact is clear – physical harm towards Deya. There are other threats such as harassing her employers to fire her from her job, and to harass her known friends online.
To do risk assessment, Deya will have to go through these threats and analyse them to assess their probability and impact – in order to plan how she can mitigate her risks.
Threat 1: To find out where she lives and share that information online
Most of the threats come from accounts online – most of whom she does not know, and cannot verify if they are actual people or fake accounts. She recognises a handful of those participating in these online threats as known actors who often take part in attacking women online. Based on her knowledge of their previous attacks, she knows that personal details have sometimes been published online, and this has created a real sense of fear for her personal safety.
Is there are a way for her to prevent this from happening? How likely is it that her harassers and attackers will find out where she lives? She needs to figure out how likely it is that her address is either already available on the internet or can be made available by one of her attackers.
In order to assess this, Deya can begin by doing a search for herself and the information that is available about her online – to see if there are physical spaces that are associated with her, and if these will point to her actual physical location. If she discovers that her home address is available on the internet, is there something she can do about it? If she discovers that her address is currently searchable on the internet, then what can she do to avoid having it publicly available?
Deya can also assess how vulnerable and/or secure her home is. Does she live in a building with guards and protocols for non-tenant access? Does she live in an apartment that she has to secure on her own? Does she live alone? What are the vulnerabilities in her home?
Deya will also have to assess her own existing capacities and resources to protect herself. If her home address is made public on the internet, can she move locations? Who is available to offer her support during this time? Are there authorities that she can call on for protection?
Threat 2: To harass her employers to get Deya fired from her job
Deya works for a human rights NGO so there is no threat of her being fired from her job. But the organisation’s office address is publicly known in her city and available on their website.
For Deya, the threat of being fired from her job is low. But the publicly available information about her NGO may be a vulnerability to Deya and the staff’s physical security.
In this scenario, the organisation must do their own risk assessment as a result of the threats being faced by one of their staff.
What to do with risks? General mitigation tactics
Beyond identifying and analysing threats, probability, impact and capacities, risk assessment also deals with making a mitigation plan for all the risks identified and analysed.
There are five general ways to mitigate risks:
Accept the risk and make contingency plans
Avoid the risk
This means decreasing the probability of a threat happening. This may mean implementing security policies to keep the group more secure. This could also mean behavioural changes that will increase the chances of avoiding a specific risk.
Control the risk
Sometimes, a group may decide on focusing on the impact of a threat and not on the threat itself. Controlling the risk means decreasing the severity of the impact.
Transfer the risk
Get an outside resource to assume the risk and its impact.
Monitor the risk for changes in probability and impact
This is usually the mitigation tactic for low-level risks.
Case study: Deya
To use Deya’s example again, she has options about what to do with the risks she is facing based on her analysis of each threat, the probability of each threat happening, the impact of each threat, and her own existing capacities to handle the threat and/or the impacts of the threat.
In a scenario where Deya’s home address is already searchable on the internet, the risk will have to be accepted and Deya can focus on making contingency plans. These plans can range from improving the security of her home to moving homes. What is possible will depend on Deya’s existing realities and contexts.
The other option for Deya in this scenario is to ask where her address is publicly available to take down that content. But this is not a foolproof tactic. It will help her avoid the risk if none of her harassers have seen it. But if some have seen it and taken a screenshot of that information, then there is very little that Deya can do to stop the information from spreading.
In a scenario where Deya’s address is not publicly known and available on the internet, there is more breathing room to avoid the risk. What can Deya then do to prevent her home address from being discovered by her harassers? Here, she can take down posts that are geo-tagged that are close to her home, and stop posting live geo-tagged posts.
In both scenarios (about her address being publicly available or not), Deya can also take steps to control the risk by focusing on protecting her home.
Good risk mitigation strategies will involve thinking about preventive strategies and incident response – assessing what can be done in order to avoid a threat, and what can be done when the threat is realised.
Preventive strategies
• What capacities do you already have in order to prevent this threat from being realised?
• What actions will you take in order to prevent this threat from being realised? How will you change the processes in the network in order to prevent this threat from happening?
• Are there policies and procedures you need to create in order to do this?
• What skills will you need in order to prevent this threat?
Incident response
• What will you do when this threat is realised? What are the steps that you will take when this threat happens?
• How will you minimise the severity of the impact of this threat?
• What skills do you need in order to take the steps necessary to respond to this threat?

Reminders
Risk assessments are time-bound
They happen within a specific time period – usually when a new threat emerges (e.g. change in government, change in laws, changes in platform security policies, for example), a threat becomes known (e.g. online harassment of activists, reports about activists’ accounts being compromised), or there is a change within a collective (e.g. a new project, new leadership). It is important, therefore, that risk assessments be revisited, because risk changes as threats emerge and disappear, and as the ability of a group and individuals within that group to respond to and recover from the impact of a threat changes.
Risk assessment is not an exact science
Each person who is part of a group that is undergoing a risk assessment process comes from a perspective and a position that affects their ability to know the likelihood of a threat to be realised, as well as their own capacities to either avoid a threat or respond to the impact of it. The point of risk assessment is to collectively understand these different perspectives within the group, and have a shared understanding of the risks they face. Risk assessments are relative. Different groups of people may face the same risk and threats, but their ability to avoid those threats and/or their ability to respond to the consequences of the threats differ.
Risk assessment will not ensure 100% safety, but it can prepare a group for threats
As there is no such thing as 100% safety and security, risk assessments cannot promise to guarantee that. What they can do is to enable an individual or a group to assess the threats and risks that can potentially affect them.
Risk assessment is about being able to analyse risks that are known and are emerging, in order to figure out which risks are impossible to predict
There are different types of risks:
• Known risks: Threats that have already been realised within the community. What are their causes? What are their impacts?
• Emerging risks: Threats that have occurred but not within the community that the person belongs to. These could be threats that result from from current political climates, technological developments, and/or changes within the broader activist communities.
• Unknowable risks: These are threats that are unforeseeable and there is no way of knowing if and when they will emerge.
Risk assessments are important in planning
They allow an individual or group to look at what will cause them harm, the consequences of those harms, and their capacities to be able to mitigate the harms and their consequences. Undergoing a risk assessment process allows groups to make realistic decisions about the risks they are facing. It allows them to prepare for threats.
Risk assessment is way to manage anxiety and fear
It is a good process to go through to unpack what people in a group fear – to create a balance between paranoia and complete lack of fear (pronoia), so that, as a group, they can make decisions about which risks to plan for.

Risk assessment in movement organising [foundational material]
Overview
When thinking about risk assessment at the level of movement organising, it means expanding the scope of consideration to also include shared spaces, processes, resources or activities that are helmed collectively – formally or informally.
Movements are larger than an organisation, and made up of relationships of shared political commitment and action between different actors. Movement actors can be comprised of individuals, organisations, collectives, community members or groups, and bring different knowledge, skills, contexts and priorities into a movement. How movement actors organise themselves, figure out roles and areas of responsibilities and come to agreements are important dimensions of movement organising, where risk assessment can also play a part in surfacing potential points of stress.
Risk assessment from a movement perspective
It's often easier to identify movements from hindsight, as they grow organically through time and in response to concerns of specific contexts and moments. Sometimes, we think of movements as protests, since that is often the site where many movements are visible and grow. But not all movements end (or begin) in protest. For example, many LGBTIQ++ movements in places where visibility carries a high cost organise and take action in less visible ways, such as creating closed community spaces online, where individuals can convene, converse, provide support and strategise for different kinds of interventions.
A movement is made up of many different moments or stages, such as community outreach, building evidence, deepening understanding, consensus building, taking action, holding space for collective care, distribution of resources and so on.
Each of these moments or stages can be specific times in which collective risk assessment can be undertaken by those who are holding space or process. It might be useful to think about movement security as having the conditions in which the many stages or components of movement work can take place and thrive.
Layers of risk
One way to begin the process of risk assessment from the perspective of movements is to unpack the different layers that need consideration. There are three components that interplay with each other.
1. Relationships and protocols
2. Spaces and infrastructure
3. Data and information
The next sections describe what each layer is about, and some of the components within them, including questions for discussion that can help to unpack, analyse and understand the risks, towards coming up with a plan.
1. Relationships/protocols
At the heart of strong movements are strong relationships which are built on the basis of trust. This is particularly important as movements are less about form than about the strength and tenacity of their relationships at different levels.
Risk assessment can take place at the level of the individual, organisation or informal groups. When approached from a movement building perspective, it means paying attention to the relationships between those levels.
For example, if an individual is undergoing a lot of stress because they are working from pay check to pay check, this can affect their ability to participate fully, which in turn can impact on the organising work as a whole. Or if an organisation is under attack by the government, its affiliation to other organisations or individuals in the movement can also render them open for similar attacks. Or if there is abuse between members of a collective, this can weaken the movement as a whole from both external as well as internal stresses.
In other words, risk from a movement perspective is something that is taken on collectively, and is affected by the practices and well-being of the different nodes/actors who are part of movement organising.
To manage risks at the level of relationships, the following three areas can be looked at:
a) Collective care
Collective care is both an individual responsibility and a matter of collective accountability to each other. This means that assessing and planning for risks needs to take into consideration different individuals’ state of well-being, as well as in relation to each other in terms of shared spaces, platforms, resources and processes.
- What are some of the risks to well-being currently faced by different actors in the group?
- What may some of the impacts be?
- What is the technology layer to this question around care and well-being? For example, are there protocols around switching off from social media, limits to online meetings, or enacting bystander solidarity activism when a member is attacked?
- How can some collective practices be developed to mitigate or address some of the risks or impacts? Are there resources or skills that can be pooled together or shared? For example, can different organisations or individuals pool funds together to subscribe to a more secure communication channel or hosting platform that allows for greater control over data?
b) Inclusion and representation
This is in terms of processes and criteria for including people into different layers of organising spaces. Sometimes this is only considered when a security breach has happened, such as information about an event being leaked to hostile parties because everything happens in one WhatsApp or Facebook group. Thinking about inclusion mechanisms can help in being more purposeful in developing different security levels of information sharing and communication channels. Thinking about representation in movement activities can help to also surface particular risks to individuals or groups of people, and how to mitigate, distribute or prepare for this risk.
- What are the protocols around bringing in new people, or when people leave? For example, mailing lists or other kinds of discussion and work spaces.
- Are there specific risks around having many or singular faces to visible moments of the movement? How can this be planned for? For example, when a call for participation is being published, is there a plan for which accounts this should come from (personal accounts, single-use accounts set up for the specific activity, organisational accounts, etc.), and timing so that it cannot be traced back to one initial source?
- What are some of the risks associated with solidarity actions with allies in a particular instance, and how can this be planned for? For example, highlighting consent around documenting and posting pictures in social media, especially of targeted identities, or distributing risk by having many people.
- What are the different internet connectivity and technical capacity contexts of those within the movement – and how does that affect their ability to securely participate in the movement?
c) Managing conflict
This is often an area that is least addressed within movements, as we assume shared politics, values and interest. However, it’s important to allow for these to be surfaced, discussed and planned for, as they can serve to support the overall justice mission of the movement, as well as ensure that internal vulnerabilities or power differences are addressed.
A plan doesn’t have to be complex, but it can begin with a frank and carefully held discussion, surfacing shared values and coming to agreements, and then making a plan around this including who should be involved, what measures can be taken, and how shared values can be collectively enacted.
- What are some of the potential conflicts that could present as risks to a movement? In particular, conflict between members – what might the impact be? For example, loss of trust, community members taking sides, loss of control over movement resources such as passwords, access to sites, etc.
- How can a response plan be developed for different kinds of conflict? For example, sexual harassment within the movement, intimate partner violence between members of the movement, romantic or sexual relationships between members of the movement that ended badly, decision making around shared resources or funding, disagreements around core values or strategies, etc. Some of these are longer-term, sustained mechanisms, while others may be contingent upon specific activities.
2. Spaces/infrastructure
The digital layer is an increasingly critical component for organising and movement building in current times. Because movements are not located within an institutional space, digital infrastructure and platforms become an important shared space for coming together, coordinating and planning activities, documenting decisions/transparency, as well as the living archive of collective history, etc. It's a critical part of the ecosystem of movements today.
Often, digital infrastructure of movements is a combination of different platforms, tools and accounts that are employed or emerge across time in evolution with the movement as it grows. Unlike within an organisation, there may be several people taking care of different kinds of spaces for different purposes, which may also serve different communities. Some of these could be personal accounts, some could be temporary accounts set up for an activity or event, and some can be subscriptions and spaces created specifically for a coming together of different information, content and community streams. Taking a moment to understand this as an ecosystem – interconnecting components of a shared movement infrastructure – and to assess potential risks can help to surface collective responsibility, care and stewardship over these spaces, as well as to develop safety plans around potential compromises.
The following areas can be discussed when thinking about risk assessment on spaces and infrastructure, with some questions that can be considered:
a) Platform/tool/hosting decisions
Movement and organising work relies heavily on information sharing and effective communication. As such, thinking through risks related to which platform or tool to use for organising, and where they will be stored, can have a large implication on the safety and security of the people, groups and work of the movement. In assessing risks related to vulnerability to breaches and attacks, it may be useful to consider if there are feminist/activist-developed or hosted solutions for that specific need, as they generally pay greater attention to issues of privacy and security.
It’s also important to consider accessibility, usability, ease and likelihood of effective adoption by larger movement members. It’s not always useful to choose the most technically secure solution, when it requires a lot of investment in time and energy to learn how to use it, which may not always be possible or preferable.
- What are the current platforms, tools and spaces being used, for what purpose, and who has access to them?
- What are the potential risks associated with particular platforms/tools/hosting for the need at hand? What are the impacts of these risks?
- What are the literacy, skills and capacity needed for adoption? How can these literacy, skills and capacity be shared and built with wider pools of people within the movement to not create an internal technology-based power hierarchy?
- Is this platform/tool accessible to most people who need to use it? Will barriers to ease of use end up creating more insecure practices instead? How can this be addressed?
- Can risks be distributed by also distributing platform/tool use for specific purposes?
b) Ownership and resourcing
Ownership and management of shared digital infrastructure is both responsibility as well as power and potential gatekeeping. The more a movement is able to surface this as a political conversation around shared values and understanding on governance, economy and community building, the more sustainable some of the shared technology practices can be.
- How will use of specific infrastructure, platforms or tools be resourced? How are they currently resourced? What are the internal shared movement economics of distributing costs when it comes to use of and commitment to particular technology(ies)?
- What are the risks of use of “free” platforms when it comes to control over data and functions, and the risks of paid services when it comes to ability to commit to costs for a sustained period of time? How can these be planned for?
- How can this also be reflected in the politics of the movement? For example, developing protocols around common ownership, management and resourcing. Can ad hoc, informal and light cooperative economic arrangements be made? How can these be sustainable and transparent?
c) Administration and protocols
In the context of movement organising, thinking about infrastructure as shared space means that having clarity around how these spaces are managed and by whom can help to surface not only collective care, but also potential risks related to access to, care of and potential loss of information and community space.
- Who has control over access to specific spaces? How much of this is about who owns the space (personal accounts) or settings, and how much is it about literacy, device or connectivity preconditions for access?
- What are the risks involved in compromises to specific spaces? Where might these compromises come from (think of both internal and external threats), and what might the impacts be? How can this be planned for?
- How are spaces managed? And what are the protocols for e.g. how many people have administrative access, their location (individual, organisation, network), how often this is changed, conditions for change, changing passwords, etc.?
- Are there protocols around deleting spaces or data, and archiving? Or are there existing practices that can be discussed and translated into protocols?
- How, where and when do discussions about risk assessment on shared digital infrastructure happen?
- Who will respond if there are incidents within spaces/infrastructure that affect the safety and security of the movement?
- What changes in the spaces that the movement uses (e.g. new security policies in platforms, the removal of security features, etc.) and within the context of the movement (e.g. changes in country situation, changes in government, new laws that affect the ability of the movement to continue its work, etc.) will trigger a larger discussion within the movement about its spaces/infrastructure? Who will monitor these changes?

3. Data/information
Data and information are being produced and generated all the time while organising. This can be in the form of formal or informal, deliberate or shadow forms of data. Another way to understand risks in increments is to look at the data practice of a specific activity or strategy of a movement. Think about this from either a specific working group within a movement that is responsible for carrying out specific tasks or strategies, or from the perspective of an activity. This can also be used at the level of an organisation, as every organisation deals with data, and each unit within an organisation does as well.
Here, there are some security and safety considerations for each phase of the data life cycle. There is an activity called “Data life cycle to as a way to understand risk” that operationalises this section.
a) Creation/gathering/collection of data
- What kind of data is being gathered?
- Who creates/gathers/collects data?
- Will it put people at risk? Who will be put at risk if this data is released?
- How public/private/confidential is the data gathering process?
- What tools are you using to ensure the safety of the data gathering process?
b) Data storage
- Where is the data stored?
- Who has access to the data storage?
- What are the practices/processes/tools you are using to ensure the security of the storage device?
- Cloud storage vs physical storage vs device storage.
c) Data processing
- Who processes the data?
- Will the analysis of the data put individuals or groups at risk?
- What tools are being used to analyse the data?
- Who has access to the data analysis process/system?
- In the processing of data, are secondary copies of the data being stored elsewhere?
d) Publishing/sharing of information from the processed data
- Where is the information/knowledge being published?
- Will the publication of the information put people at risk?
- Who are the target audiences of the published information?
- Do you have control over how the information is being published?
e) Archiving
- Where is the data and processed information being archived?
- Is the raw data being archived or just the processed information?
- Who has access to the archive?
- What are the conditions of accessing the archive?
f) Deletion
- When is the data being purged?
- What are the conditions of deletion?
- How can we be sure that all copies are deleted?
Conclusion
This background document aims to help provide you with a conceptual overview of how to think about risk assessment from the perspective of movement organising. Often, risk assessment is done at the level of an individual, or an organisation. Thinking about this at the level of movements means asking participants to situate themselves as significant, yet partial, parts of a larger community of organisers.
This can be helpful as a common ground for groups of people who are organised differently to come together and think through a common plan, when a shared context, aim or activity is identified. It can also help to facilitate processes for collective thinking around sustainability and organising by anticipating and planning for risks related to group and relational dynamics, and where information and communications technologies play a critical role as movement infrastructure.
Further reading
More broadly on understanding movement building and collective organising, as well as on digital realities:
- ICTs for Feminist Movement Building: Activist Toolkit: https://genderit.org/resources/icts-feminist-movement-building-activist-toolkit
- Making a Feminist Internet: Movement building in a digital age: https://www.genderit.org/editorial/making-feminist-internet-movement-building-digital-age
- Achieving Transformative Feminist Leadership: A Toolkit for Organisations and Movements: https://www.sexualrightsinitiative.org/resources/achieving-transformative-feminist-leadership-toolkit-organisations-and-movements