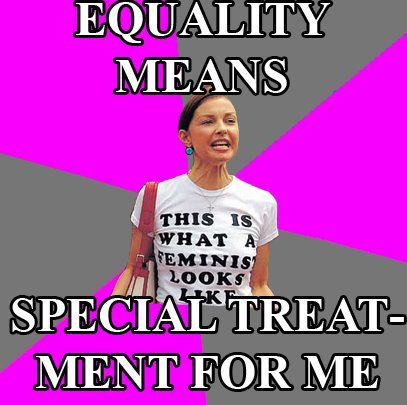Online gender-based violence
Guide participants through the issues relating to online gender-based violence – its root causes, how violence plays out on the internet, the continuum of violence that women, women-identified and queer identities experience online and offline, and its impact. We **highly recommend** that you choose a Learning Path to travel, as these include activities with different levels of depth that should help participants obtain more insight into the covered subjects.
- Introduction and learning objectives
- Learning activities and learning paths
- Online GBV or not? [starter activity]
- Deconstructing online GBV [deepening activity]
- Story circle on online GBV [deepening activity]
- Take Back the Tech! Game [tactical activity]
- Planning response to online GBV [tactical activity]
- Meme this! [tactical activity]
- Mapping digital safety [tactical activity]
- Resources | Links | Further reading
Introduction and learning objectives
Introduction
This module is about guiding participants through the issues relating to online gender-based violence – its root causes, how violence plays out on the internet, the continuum of violence that women, women-identified and queer identities experience online and offline, and its impact.
This module is based largely on the more than a decade of work that the APC Women´s Rights Programme (WRP) has done through the Take Back the Tech! campaign, the End violence: Women's rights and safety online project, MDG3: Take Back the Tech! to end violence against women project, and EROTICS (Exploratory Research on Sexuality and the Internet).
Learning objectives
By the end of this module, the participants will have:
- An understanding of the forms of online gender-based violence (online GBV) and its impacts on the survivors and their communities.
- An understanding of the continuum of violence between the offline and the online spheres, and the power structures that allow it.
- Ideas, strategies and actions about the ways in which online GBV, especially in their contexts, can be addressed.

Learning activities and learning paths
This page will guide you through the Module's correct use and understanding. Following the Learning Paths, with activities of varying depth, should allow participants to obtain a better grasp of the studied subjects.
Learning paths
How you can use the activities below – and combine them – will depend on:
- the purpose of your workshop (are you raising awareneness or are you expecting to come up with strategies to respond to online GBV?);
- your participants (are they survivors on online GBV? Or is their experience more removed?);
- your own experience in facilitating these kind of workshops (are you a seasoned digital storytelling facilitator? A digital security trainer who is now getting into online GBV? Or a campaigner who is expected to run an online GBV workshop as one of your campaign´s activities?);
- the time you have available to you to run a workshop
These learning paths are recommendations for how you can mix and match the activities in this module to create a workshop on Online GBV.
We recommend beginning with Online GBV or not? to spark discussion, surface shared understandings of online GBV, and clarify key concepts. This activity would work if your workshop is more general awareness-raising.
Following that, depending on time and the context, you can work with participants using the Deconstructing online GBV or Story circle activities to deepen the group's understanding of online GBV, and to ground the conversation in experiences of people in the room (Story Circle) or case studies (Deconstructing Online GBV). Both deepening activities may cause participants distress, they require preparation.
For the Story Circle activity, specifically, facilitation will need a lot of care and consideration. We do not recommend this activity for solo facilitators, and for those who are just beginning to do these kinds of workshops.
There are Tactical activities that are meant for strategising on response to online GBV. The Take Back the Tech! Game focuses on general approaches to addressing online GBV. If you have limited time, the tactical activity: Meme this! is shorter and faster. It could also be a light activity after a heavy one like the Story Circle on Online GBV. Planning response to online GBV activity aimed towards coming up with a more comprehensive response strategy to specific incidents.
The activity Mapping digital safety could be a standalone workshop with a focus on framing Online GBV with the Universal Declaration of Human Rights.
Some suggested combinations:
| If you have half a day for your workshop, then Online GBV or not? followed by Meme this! |
| If your workshop is focused on strategising and you have limited time, we recommend jumping straight into the Take Back the Tech! Game. |
| If your workshop is about having a comprehensive response to online GBV incidents, then we suggest doing the Deconstructing online GBV, followed the Tactical Activity: Planning response to online GBV. |
Learning activities
Starter activities

Deepening activities

Tactical activities

Online GBV or not? [starter activity]
This activity is designed to spark debate and discussion, and give you, the trainer/facilitator an opportunity to clarify concepts relating to the experiences of women and gender diverse individuals on the internet and online gender-based violence (online GBV).
About this learning activity
This activity is designed to spark debate and discussion, and give you, the trainer/facilitator an opportunity to clarify concepts relating to the experiences of women and gender diverse individuals on the internet and online gender-based violence (online GBV). This is specifically aimed towards speaking about the less obvious forms of online GBV, and to discuss the participants' assumptions on how they define what GBV is.
The main methodology in this activity is to show examples of experiences of women and gender diverse individuals online (It would be good to have exagerrated examples to encourage debate or discussion) and memes, and have the participants react with online GBV or Not GBV upon reading/hearing/seeing the example meme. Then you can ask the participants to defend their initial position through a set of guide questions.
It is essential to frame this activity as a vacuum where ALL opinions and viewpoints are allowed (as long as they are expressed in a manner acceptable to the group, assuming Participant Guidelines are established earlier in the workshop), and that what the participants say during this activity will not be quoted/publicised/shared with others. It also a good idea, especially if the group has a lot of experienced feminists, to encourage others to play Devil's Advocate in order to enrich the discussion.
Facilitation Note: It would be ideal to have established and negotiated participant guidelines about respect before-hand, just in case the debate gets heated.
For the trainer/moderator, this activity can be used to learn more about the participants' level of understanding and appreciation of online GBV.
Learning objectives this activity responds to
- An understanding of the forms of online GBV and its impacts on the survivors and their communities.
- An understanding of the continuum of violence between the offline and the online spheres, and the power structures that allow it.
Who is this activity for?
Ideally, this activity is for participants who have an understanding of internet rights, sexual rights and WHRDs.
Time required
Depending on how many examples are shown, this activity can take from 30 minutes to 90 minutes.
Resources needed for this activity
- Signs (not bigger than half a 4A sheet of paper) with Online GBV printed on one side and Not Online GBV! printed on the other. One per participant.
- A way to present the examples of women's experiences on the internet. It could be a poster of the printed memes or a projector to show the memes.
(See Resources for sample memes)
Mechanics
Show a meme or example of an experience that women and gender diverse individuals have had online.
Tip: Perhaps start with a glaringly obvious example of online GBV, then move to more nuanced examples.
After each example, you ask: Is this Online GBV or Not Online GBV?
The participants then raise their boards to show which they chose.
Once everyone has made a choice, you can then ask: Why do you consider this Not Online GBV/Online GBV? Then get an opinion from someone who had the opposite opinion, and allow the group to ask each other questions.
If there is not much disagreement among the group, then dig deep into the example through these guide questions:
- Who is being attacked in this meme? How will it impact them?
- What are the values underpinning this meme? What is the meme creator (and anyone who shares and likes this meme) really saying about women, women-identified, and/or queer individuals, and their communities?
- Does this meme reflect the values in your communities? How so?
- If you had come across this meme, how would you have reacted? How do you think we should react to it?
You can end the discussion with a bit of synthesis, and then move on to the next example.
To synthesise each example, the trainer/facilitator can:
- Do a quick summary of the discussion that the participants had over the example.
- Name what the example is, or the various ways the example has been described.
- Point out the gender stereotyping, gender bias and/or misogyny that was reflected in the meme.
Intersectionality Note: It is also important to draw out how women and gender diverse individuals and communities would be impacted differently by the messages / memes.
You don´t have to do a synthesis for each example that you show. If a discussion on a specific example is similar to a previous one, then you can just point out the similarity.
Facilitation Note: It is important, while the activity is still happening, that you, as the trainer / facilitator, do not take a side in the discussion that the participants are having. Having a facilitator siding with a group of participants is an effective silencer of discussion and debate.
At the end of the entire exercise, you then do a bigger synthesis of the activity. In this synthesis, you can go back to the examples that got the most debate and discussion from the participants, summarise the discussion, and then share your own thoughts and opinions on the matter.
Key points to raise in the main synthesis:
- The relationship between "real world" values and the creation of such memes.
- The existing power structures, patriarchal values, gender bias and bigotry that are showcased in the examples.
- What constitutes gender-based violence.
- How positionality and privilege within the different women and gender diverse sectors have different effects on indviduals and communities.
Facilitator preparation notes
From the start, you need to decide if you are playing a trainer (one with the knowledge and experience to provide answers), or a facilitator (one who guides discussions, and keeps herself from sharing her own opinion) in this learning activity. Being both will not be conducive to a good discussion or a safe space for the participants. If you are being a facilitator, you wouldn't want to provide answers at the end of the discussion, and make participants defensive. If you are being a trainer, you wouldn't want to be so strict in your opinion on the matter that it silences the participants.
Another thing to prepare for is your own assumptions about what online GBV is. Take a refresher by reading Good Questions on Technology-related Violence.
Facilitation Note: This activity is not just to show examples of obvious cases of gender-based online violence, but to have a discussion with the participants about a nuanced understanding of what is online violence and what is not. So, in the examples, include examples of common experiences that women and gender diverse individuals have on the internet – and not just the ones that are glaringly violent.
There are sample Sample Memes found below, but it would be ideal to use examples that are context-specific to the participants in the workshop. It would be good to show a range of examples, including messages or memes:
- that are misogynistic, homophobic, transphobic
- that attack women and gender diverse individuals and communities for their actions
- that name or target specific women or gender diverse individual in the message / meme
- that are overtly-violent and / or calls for gender-based violence
- that represent women and queer bodies as sex objects
- that show offline actions against women put online
- that attack women and gender diverse individuals on the basis of their social class
The point here is to not be too obvious in your sample choices but to generate a discussion among the participants.
If you have time to prepare with the participants, ask them for examples of online harassment that they have witnessed (not necessarily targeted towards them) online, and show those examples in the activity.

Additional resources
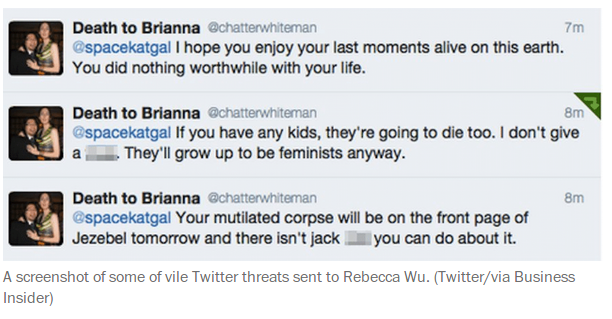
Sample Memes
Warning : This page contains racist, sexist, homophobic transphobic and rape apology material.
Facilitators Note: There are sample Sample Memes found below, but it would be ideal to use examples that are context-specific to the participants in the workshop. We encourage you as trainers to find your own memes so that they are relevant to the participants.
Intersectionality Note: In choosing sample memes, make sure that you include different race, class, religious backgrounds, sexual orientation and gender identities.

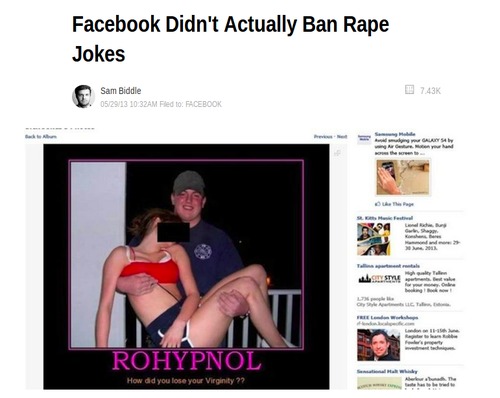
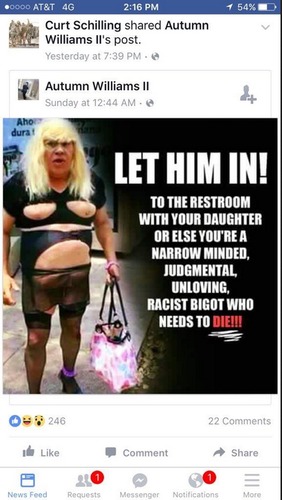
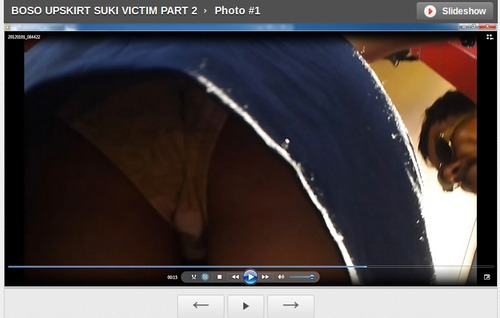
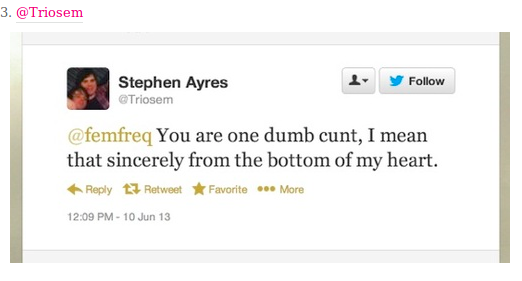
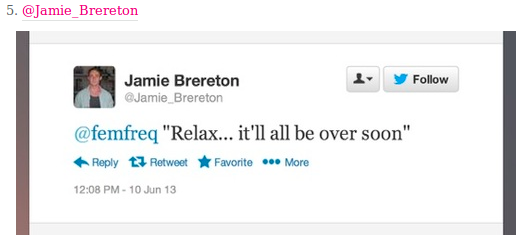
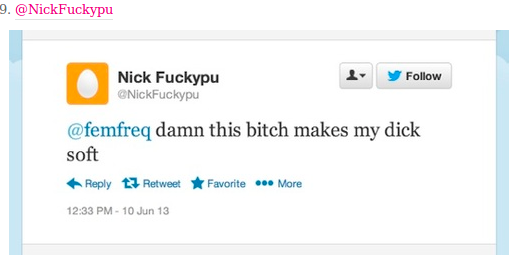
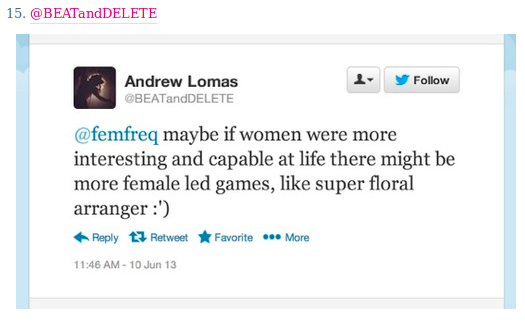
When a woman complains about the lack of women´s representation in video games, a sampling of the reactions she gets: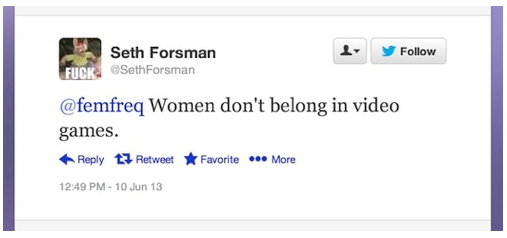

Deconstructing online GBV [deepening activity]
This activity takes the participants through a case study of an incident of online gender-based violence, and gets them to discuss the different aspects of the case study.
About this learning activity
This activity takes the participants through a case study of an incident of online gender-based violence, and gets them to discuss the different aspects of the case study.
Learning objectives this activity responds to
- An understanding of the forms of online gender-based violence (online GBV) and its impacts on the survivors and their communities.
- An understanding of the continuum of violence between the offline and the online spheres, and the power structures that allow it.
- Ideas, strategies and actions about the ways in which online GBV, especially in their contexts, can be addressed.
An important note, while this session will touch upon ideas for response, the main purpose of this activity will be to unpack an example of an online GBV incident.
Care Note: Unpacking a case study of an online GBV incident might cause participants distress.
This is not an activity to do when you do not know your participants and / or if you have not previously gained trust from the group.
In order to do this more responsibly, it is important that you are aware of the experiences of violence that your participants have (see more here: Get to know your participants), and to be observant as you run this activity about how the participants are reacting.
Encourage your participants to raise their hands if they need a break from the activity.
Knowing and having some experience in some debriefing exercises such as those found in the Capacitar Emergency Kit would be useful.
Who is this activity for?
This activity can be used with participants with different levels of experience in women's rights and technology.
Depending on the level of experience of the participants on the various aspects on relating to online GBV, the trainer / facilitator will need to prepare to intervene to clarify concepts around social media, the internet, and even national laws.
Time required
About 2 hours per case study
Resources needed for this activity
- Flip chart paper/whiteboard
- Markers
- Index cards to write down different aspects of the case study that need to be stressed.
Alternatively, you can prepare slides with the case studies and the questions.
Mechanics
You begin by describing the incident to be deconstructed, writing down the following details on individual index cards and posting them on a wall (or if you have prepared a presentation, these could be the bullet points in your slides):
- Name of the survivor + gender + social class + race + educational attainment + any other identity markers
- Country where the survivor is from + if there are laws that could protect them
- The initial incident of online violence , in which platform did this happen
- Where the incident happened , in which platform did it start
- If you can, name of the initial aggressor/s + some details, if it's important in the case study
- If the aggressor/s cannot be named, write down some details about them: their online handles, etc.
- Relationship between the survivor and aggressor, if any
Then open it up for discussion by asking the participants the following questions:
- Who else should be responsible here aside from the perpetrator?
- Who is the community around the survivor? How do you think they could have responded?
- What are the survivor's possible responses to the situation?
- How do you think this incident affected them? (impact)
Write down the responses on individual index cards and post them on the wall.
Then divulge more details of the case study, marking details that the participants have already guessed and writing down more details on individual index cards:
- How did the case escalate? In which spaces was the violence replicated?
- How did the case spill into the survivor's life outside online spaces?
- How did the community respond?
- What other spaces reinforced the initial incident of violence?
- Who else got involved?
Then open the discussion up again by asking the following questions:
- What recourse does the survivor have?
- What laws can protect them in their country?
- What other impact will this have on the survivor based on where they are from, what they do, what social class they belong to, what country they are in?
- What should happen to the initial aggressor/s? Who can make that happen?
- What should happen to the other aggressor/s, including the ones that extended and escalated the incident?
- What is the responsibility of those who own and run the platform where the incident happened?
- Who else is responsible in this scenario? What is their responsibility?
- How could the women's rights movements respond to this?
Write down the responses of the participants to each question on individual index cards and post them on the wall.
At the end of this, there will be a gallery on the wall that shows the different aspects to the case study of online GBV.
To synthesise, reinforce the following:
- The connection and continuum between online and offline violence.
- The complexity on online GBV: the varied stakeholders, both negative and positive.
- The systems and structures that facilitate online GBV as well as those that might be avenues for redress and mitigation.
Facilitator preparation notes
In order to create a relevant case study that will encourage discussion and understanding of the complexity of online gender-based violence, the case study needs to resonate with the participants, which requires knowing where they are coming from and what their concerns are [Note: There is a section here about Getting to Know Your Participants.]
The Sample Case Study below would be useful in articulating the case study that you will share in this session. It outlines the Initial Presentation and the Escalation of the example to be deconstructed.
If you want to to create your own case study:
- flesh out the survivor, where they are coming from, their contexts
- be clear about where the incident happened first and how it escalated
- think about the impact of the incident: offline / online; on the individual, their community / family / friends; on their well-being, digital security, physical security
- try to describe the perpetrator/s´ actions but not their motivations
Additional resources
Sample case study: Selena's case
Initial presentation
Selena is in her final year of college. She attends college in Manila, Philippines, but she heads back to her province in Angeles every chance she gets to visit her parents and her younger siblings. In order to augment her limited funds for her studies, she is a part-time barista at a local coffee shop.
On one trip home, she finds her parents very upset. They accuse her of abusing her freedom in Manila and using her looks to meet foreign men. They slut-shame her, and threaten to cut off their support. They demand that she stop dating foreign men online and causing them problems.
Selena does not use any kind of dating app – she's too busy with school and work. And she already has a boyfriend.
After hours of her parents shouting at her, she finally gets a picture of what happened:
The day before, Heinz from Germany had knocked on her parents' door, demanding to see Selena. He brought with him copies of conversations that he has had with Selena, and the pictures that she has shared with him. Those conversations happened both on the dating app chat and on WhatsApp. He implied that he and Selena have engaged in cybersex. Apparently, he had sent Selena money so she could start applying for a German visa in order to visit him. When she did not get a visa, he had then sent her money to purchase a ticket so they could meet up in Bangkok, where they could be together without her conservative parents watching their every move. She did not show up. Heinz had tried getting in touch with her but she was unresponsive. So he felt he had no choice but to pay her parents a visit. They refused to let him in and threatened to call the authorities if he kept on insisting on seeing Selena.
Heinz had left, angry.
Sounds like a con gone wrong.
Problem: Selena is not aware of any of this. She has never talked to any Heinz. She has not received any money from him. She was not in a long-distance relationship with anyone.
It looks like Selena's pictures and identity were used to "catfish" Heinz.
(Catfishing is when someone takes screen-grabs of someone's photos online and creates accounts in their name in order to con other people. Sometimes, the real name of a person is attached to the fake account, but there have been cases where the photos are attached to fake names.)
Escalation
In response to the incident, Selena had removed all her photos from all her social media accounts, and had sent a message to the dating app and WhatsApp that the account with her pictures was a fake one that some people had used to swindle a German user.
She and her family have not heard back from Heinz. He seems to have left Angeles after her parents turned him away.
One day, at school, a few of her male classmates start heckling her, calling her a slut and a swindler, saying that it's a shame that a pretty girl like her would use her looks that way. One of Selena's friends show her a Facebook page called "Selena is a Slut Swindler". On that page, Heinz recounts what "Selena" had done to him – with screen grabs of their conversations, her pictures, and audio recordings of their cybersex sessions.
The page has trended, and has received a lot of likes and followers.
What can Selena do?
Sample case study: Dewi's case
Initial presentation
Dewi is based in Jakarta, Indonesia. She is a 30-something trans woman, working as a call centre agent for a large multi-national online retail company. With two of her closest friends, Citra and Indah, she has just recently started a small organisation to promote SOGIE equality in Indonesia.
Since they started the organisation, the three of them have been invited to local events around LGBTQI+ rights and have attended demonstrations to support their advocacy. She has been captured in the local news speaking out against toxic masculinity and religious fundamentalism.
One morning, as Dewa was getting ready to go to work, she receives a message on her Facebook Messenger. It´s from an account called, Mus: ¨You made me so happy last night. Do you want to make me happy again tonight?¨ She dismisses it as a wrongly-sent message, so she responds with: ¨I think this is not for me. Wrong send.¨
To which Mus replies, ¨It is meant for you, Ms. Dewi. I saw your pictures and I want to see you in person. So you can make me happy again.¨
Scared that Mus knows her name, she just messages back and says, ¨I don´t know you, please stop.¨ She then blocks Mus.
Then more messages keep showing up from different users on her FB Messenger. The messages get progressively ruder and more explicit. She is also getting more friend requests on Facebook. She opts to block those users and tries to ignore them.
She keeps Citra and Indah updated on what is happening and her two friends are getting worried for Dewi.
To try to get to a reason as to why Dewi was being harassed, Citra Googles Dewi´s name. What they find are images in which Dewi´s face is edited on to naked transwomen´s bodies. The images are all labeled with Dewi´s name, and posted on DIY pornography sites.
Immediately, the three of them write to where the images are posted to request for the take down of the photos and of Dewi´s name on them. They all hoped that that was the end of that and the harassment would stop.
Escalation
One day, Dewi´s supervisor calls her in for a meeting. Then the supervisor shows her Twitter messages addressed to their company with a copy of the doctored images with the caption: Is this what your employees look like? What kind of morals does your company have? Fire HIM!¨
According to her supervisor, their company´s Twitter account was bombarded with the same messages from multiple accounts.
What can Dewi do?
Story circle on online GBV [deepening activity]
This activity allows participants to reflect upon and share experiences of online GBV.
About this learning activity

This activity allows participants to reflect upon and share experiences of online GBV.
A safe space is the main prerequisite for this activity, and some quiet time for the participants to reflect.
This activity happens in two stages:
- Reflection Time, when each participant is given time to articulate and write down their story by answering a series of guide questions.
- Story Circle, where all the participants share their stories with each other.
It is important to note here that this Story Circle is not for the purposes of therapy. Being able to tell your story, even anonymised, has some therapeutic effects, but it should be made clear that this is not the purpose of the Story Circle. If you are dealing with a group that you know has experienced online GBV, especially if there are people in the group who have very recent experiences, you can either make sure that there is someone in the facilitating team who can provide therapy, or skip this learning activity, if you don't think you can handle the participants being re-traumatised.
Learning objectives this activity responds to
- An understanding of the forms of online GBV and its impacts on the survivors and their communities.
- An understanding of the continuum of violence between the offline and the online spheres, and the power structures that allow it.
Who is this activity for?
This activity can be carried out with participants with different levels of understanding and experience of online GBV.
It is important to know before doing this activity if there are participants whose experience of online GBV is current or fresh, as this activity might be a cause for stress for them. Knowing who your participants are, and also knowing what you as a trainer / facilitator can handle is important before considering this activity.
It is equally important for you, as a trainer / facilitator, to be honest about what you can and cannot hold. This activity is NOT recommended for situations where:
- you have not established trust between and among your participants
- you have not had the time to get to know your participants prior to the workshop
- you do not have any experience in handling difficult conversations
Based on the experience of story circle facilitators, it is ideal to have two facilitators for this activity.
Time required
Assuming that each participant will need about five minutes to tell their stories, and about 30 minutes will be needed to collectively reflect, plus some leeway to give instructions, then with a standard workshop size of 12, you will need a minimum of 100 minutes for this activity.
This suggested time for this activity does not include well-being activities that might be needed to address re-traumatisation of participants, or to take a break when needed. Ideally, for standard group size, holding this activity for half a day (4 hours, including breaks) would be sufficient to include well-being breaks and activities.
Resources needed for this activity
- Guide questions written down
- Space for people to reflect
- A big circle in the middle of the room for the participants to share.

Mechanics

This activity has two stages:
- Reflection Time, when each participant is given time to articulate and write down their story by answering a series of guide questions.
- Story Circle, where all the participants share their stories with each other.
During the Reflection Time stage, the participants are given 30 minutes to reflect upon a real-life example of online GBV. They can choose to tell their own experience or someone else's. Even if they are telling their own story, everyone is encouraged to anonymise their story. They should tell one story each.
In order to facilitate reflection, the participants may use the following guide questions to write down their story:
- Who is the survivor? Who was/were the aggressor/s? Who else is involved in the story?
- What happened? Where did the story happen? What kind of violence was committed?
- What was the impact of the violence? How did the survivor react? What did they fear the most? Did the situation escalate or worsen? How?
- What kind of support did the survivor get? Who able to provide support to the survivor?
- What actions did the survivor and their supporters take? How was the case resolved?
- How is the survivor doing now? How do they feel now about what had happened? What lessons have they learned from it?
- What role did technology play in this story? How did it affect the impact of the violence? How did it help in addressing the violence?
Facilitation Note: These are guide questions, and participants don't need to answer all of them. They are just there to help them articulate their stories.
Anonymising stories
Participants are encouraged to anonymise their stories, even if the story is theirs:
- Give the survivor a pseudonym that's not close to their name.
- Make the location of the survivor more general. If there are contextual issues that would make it possible to identify the survivor based on where they are from, then give the location a bigger reach. It's one thing to say that the survivor is from Petaling Jaya in Malaysia, and another to say they are in Kuala Lumpur or even Malaysia.
- Give vague details about the survivor (keep to general markers: gender, sexuality, country, religion, race, social class) but not about their experience of online GBV (the platforms and spaces where the online GBV happened, what they experienced, how it escalated, the impact on them).
Once everyone has written down their stories, gather the participants in a circle.
Lay down the rules for this story circle. It would be good to also have these written down where everyone can see it and reiterate this message.
- What is said in the story circle does not leave the story circle without the express permission of everyone in the circle.
- No one in the circle is allowed to invalidate the experiences being shared. The severity of the violence experienced is not a competition. Don't ask about graphic details of the story.
- Listeners can ask clarification questions but not questions that are invasive. Don't ask “why” questions, ask instead “how” or “what” questions.
- There will be no interruptions when a story is being told. Listen deeply.
The point here is to create a safe space for people to share their stories.
Let everyone know that no one is being compelled to share their stories.
Open up the circle for stories.
Care Note: Think about ways in which to open and close the story circle that honours the stories shared. Some suggestions:
Open with a breathing exercise, close with a breathing exercise
Have a bowl of stones or shells that people can choose to hold, to close the story circle, have everyone put the stones or shells back in a bowl
Then close the circle once the stories have been told. In closing the circle, do something to acknowledge the stories shared and strength of the storytellers.
Depending on the type of participants, and what you are comfortable with, you can:
- Do some deep breathing exercises as a group
- Have everyone go around and thank each other for sharing
- Light an incense and pass it around to cleanse the energy in the room
- Play some music and dance
- Read a poem that relates to honouring our stories. We use an Alice Walker quote to close our digital storytelling circles. Each person has a candle and they take a turn to light the candle at the end of the storycircle from the main candle.
Note: It is essential to have a break for the participants to decompress on their own before summarising the activity.
Then the trainer/facilitator summarises the stories based on the following themes:
- What were the forms of online GBV that were shared?
- Where did the violence occur? Through this, draw out the linkages between online and offline spaces – how did they affect each other?
- Who was/were the usual aggressor/s?
- What was the impact of the online GBV, especially in the offline sphere?
- What were the issues that the survivors faced in resolving their cases?
- How did intersectional issues affect the experience of the violence? For example, specific kinds of aggression, the role of culture/religion and norms, invisibility, challenges in getting support/access to justice.
Facilitator preparation notes
This is not an activity for every trainer/facilitator. Or for every kind of participant.
If you don't think you can handle this, then choose another Learning Activity. Being able to admit what you can and cannot handle as a trainer/facilitator will only make you a better one – and capable of creating safe spaces for training.
This activity also requires a lot of trust between the facilitator and the participants. This requires mental and emotional preparation for the participants. This is not recommended as a starting activity, especially if the participants are not prepared for it.
Some guidelines to follow, if you do choose to use this learning activity:
- During the Story Circle, just allow each participant to tell their story in their own way. Don't rush them. Don't correct their grammar. Don't interrupt them.
- Do not force everyone to tell a story. Maybe, for some people, being able to write down their stories is good enough. Not everyone needs to tell a story, but encourage everyone to do so.
- If a participant is triggered, take a break. Don't force them to continue their story.
- Remind yourself and your participants that healing is a process, and telling stories and being heard is a step towards ending the cycle of violence.
- Doing this activity with a co-facilitator is ideal then you and your co-facilitator can hold the space together.
Read the section on handling emotional situations in the Holistic Security Training Guide.
Facilitation Note: How do you keep to time and respect the storyteller?
Remember, that this activity is about opening up a space for participants to share and reflect upon experiences of online GBV towards understanding the issue a bit more. So while you might want to give the participants more time than 5 minutes to share their stories, you will also have to determine a time limit so that everyone can have the chance to share their stories (if they so choose), and equally important, to have space to reflect on each others stories. Time-keeping is essential to that. It is important that you let the participants know why you are time-keeping.
There are several tactics to gently remind people of that. Here are some:
- Prepare note cards or boards that you can use to signal to them how much time they have left
- Assign a timekeeper from the group so that time keeping is a shared task among the participants
- Wait for pauses in their story telling to remind them of the time they have left

Take Back the Tech! Game [tactical activity]
This role-playing game was developed in order to help participants decide how to take action in local scenarios of online gender-based violence (GBV). Each game takes on one specific scenario of an online GBV example.
About this learning activity

This role-playing game was developed in order to help participants decide how to take action in local scenarios of online gender-based violence (GBV). Each game takes on one specific scenario of an online GBV example.
There are several different Scenarios to choose from, or you can make your own:
- Blackmailed to Go Back
- Trolled on Twitter
- Faked on Facebook
- Porn Pretender
- Disinformation to Discredit
- Watching and Waiting
To play, one Game Facilitator and three teams are needed:
- Survivor Teams A and B. Each team consists of the Survivor of the online GBV Scenario, and a set of four Advisors: Legal, Solidarity, Communications, Skills.
- A third team called the Public presents challenges for each Scenario and decides which Survivor Team chose the best strategies given each context.
Each Survivor Team will develop a Survivor persona to address the Scenario and Challenges presented by the Game Facilitator and the Public.
Survivors will justify their chosen first step to the Public, arguing why it is the best option for their persona and local context. The Public can question each Survivor about their choice. The Public then presents a new challenge in the Scenario from the Challenge cards, and Survivor Teams develop and justify new strategies for two more rounds. As Survivor Teams strategise, so does the Public, exploring possible bystander responses.
The Scenario concludes with the Public presenting a plausible ending to the escalating attack. To finalise, the Game Facilitator debriefs how each player felt in their respective role, to tease out insights, including regarding the role of bystanders and the importance of solidarity. If ever facing such a scenario themselves, with a friend or as a bystander, participants will be better equipped to consider possible response and prevention strategies from many angles.
Learning objective this activity responds to
This responds to all the learning objectives in this module.
Although you can opt for Survivor Teams to “play to win”, the real goal of this role-playing discussion is to help participants:
- explore and weigh strategies for responding to online GBV and understand that there is not just one response; responses are multiple and contextual
- appreciate the ways in which scenarios can escalate
- examine how different elements and actors are involved, and the importance of support networks
Who is this activity for?
This game can be participated in by participants with any levels of familiarity on online GBV.
Time required
1.5 – 3 hours
You can play several Scenarios or just one. Each Scenario should be played 2-4 rounds before starting another Scenario. The game entails a lot of discussion around strategies to mitigate online GBV, and how people respond to actions. There must be sufficient time to orient role players, play out the Scenario as well as unpack how people felt in each role.
Resources needed for this activity
- Printed cards for the game (details in the Cards section)
- flipchart paper
- markers
- tape
- stickers, poker chips, paper cut into small squares, or individually-wrapped candies, if using tokens
- Space big enough for teams to be able to have discussions.
- A table big enough to accommodate the Strategy Cards that each team will be presenting per round.
Mechanics

Players and cards
The participants will be split into three teams:
- Survivor Team A
- Survivor Team B
- Public: presents challenges for each Scenario and decides which Survivor Team chose the best strategies given each context.
The Survivor Teams ideally would have 5 players per team. Each player has a role:
- Survivor: Ultimately decides what strategy to play
- Content Advisor: Provides advice to the Survivor about content-based strategies. The Content Advisor holds the Content Strategy Cards.
- Legal Advisor: Provides legal advice to the Survivor. The Legal Advisor holds the Legal Strategy Cards
- Solidarity Advisor: Provides advice to the Survivor relating to getting support from other people on the internet. The Solidarity Advisor holds the Solidarity Strategy Cards.
- Skills Advisor: Provides advice to the Survivor about what she can do online. The Skills Advisor holds the Skills Strategy Cards.
The Game facilitator is an individual role. They keep time, read the scenario out loud and keep the game running smoothly.
This game requires a minimum of 10 participants and can easily accommodate groups of 30, but to ensure the quality of discussion and time limitations, it is best played with groups of under 20 people. Team size is adjusted depending on the number of participants. See chart below.
| TOTAL PLAYERS | SURVIVORS | ADVISORS | PUBLIC | FACILITATOR |
| 10 | 2 | 2 for each team=4 | 3 | 1 |
| 12 | 2 | 3 for each team=6 | 3 | 1 |
| 14 | 2 | 4 for each team=8 | 3 | 1 |
| 16 | 2 | 4 for each team=8 | 5 | 1 |
| 20 | 2 | 4 for each team=8 | 9 | 1 |
| 30 | 2 | 4 for each team=8 | 18 | 2 |
Cards
There are
- Content Strategy Cards (5 per Advisor; one Content Advisor per Survivor Team)
- Legal Strategy Cards (5 per Advisor; one Legal Advisor per Survivor Team)
- Solidarity Strategy Cards (5 per Advisor; one Solidarity Advisor per Survivor Team)
- Skills Strategy Cards (5 per Advisor; one Skills Advisor per Survivor Team)
- Scenario Cards (6 cards in total)
- Challenge Cards (31 cards in total; 5 per Scenario plus a "Make your own" Challenge card; a list of generic challenge cards can be found below)
- Role Instruction Cards (7 cards in total)

Strategy cards
All games, no matter the scenario will have these Strategy Cards.
Content advisor
- Publish a piece of writing about the experience. Note the title of the piece, where it is published and where it will be distributed.
- Contact the media about the experience. Note which media agencies you would contact and how you’d convince them to cover it.
- Ask feminist bloggers to write about the experience. Note which bloggers you’d suggest and why.
- Respond to attacks on social media. Explain the response, note what hashtag you will use and which communities will be your targets and allies.
- Come up with your own content strategy.
Legal advisor
- Call a lawyer and ask them to file a lawsuit. Note which law/s you will cite.
- Go to the police and file a report. Explain why you think the police can help.
- Document the experience for later legal use. Note what you would document and how.
- Submit an abuse report to a social media platform. Note which platform(s) and the policies that were violated.
- Come up with your own legal strategy.
Solidarity advisor
- Ask people for support. Note what kind of support you want and who you will contact.
- Create a campaign to highlight the abuse. Note the name of the campaign, target(s), allies and at least one action.
- Ask your friends be your social media filter, documenting and deleting or hiding abusive comments from your view so you don’t have to see them.
- Ignore the attack and carry on as usual. Note why this could be effective.
- Come up with your own solidarity strategy.
Skills advisor
- Double check account privacy and security settings. Do you want to hide your friends and photos from public view on Facebook? Have you tried two-step verification for logging into your accounts? Note other steps you’d take.
- Search for information or pictures of yourself online. What terms would you search for?
- Go offline for a while. Under what conditions would this be a good strategy? What are the benefits?
- Report the abusive accounts/content. Note which platform(s) and the policies that were violated.
- Come up with your own skills strategy.
Scenarios + challenge cards
Generic challenge cards
- There is no law in your country against online blackmail, extortion, or threats.
- When you go to report the problem to the police, they tell you there’s nothing they can do until something “real” happens and suggest you just go offline.
- Whoever has it in for you is great at making memes.
- You post screenshots of threats you received, and your social media platform says you violated community standards and temporarily locks you out of your account instead of taking action against the person who threatened you.
- You come from a conservative family and community, and they blame you for what is happening.
- You report the person who is doing this to you on your social media platform and get this reply: “This is not a violation of our community standards.”
- You get reported and locked out of your own account..
- You are queer. But no one in your family and your work place knows about it. If this gets out, you´re in trouble.
- Someone posts private information about you: your address, your location, your work place.
- Nude pictures of you are released on social media.
- Memes to slut and body shame you seem to be everywhere.
- Your photos accompanied by derogatory remarks that attack both your person and your values are circulated.
- Accounts using your name and photos are posting rude, racist, misogynist comments on people’s social media and on your organisation’s page.
- One of your donors/clients followed a fake account thinking it was you, now they are emailing you demanding an explanation.
- Someone has contacted your social media community one by one, sending each follower a link with false information about you.
There are specific Challenge Cards for each scenario.
1. Blackmailed to Go Back
This scenario is taken from here: https://www.takebackthetech.net/know-more/extortion
Scenario Card (printed on a card with copies given to all teams, or projected on the wall, or written on butcher paper)
An ex-partner is threatening to expose your naked pictures on the internet if you don´t get back together with them. You are desperate for a solution.
Challenge cards for Blackmailed to Go Back
- There is no law in your country against blackmail and extortion online.
- Your family and friends are conservative, and will blame you for having nude pictures.
- Your Ex just messaged you. The phone with your pictures was stolen! They’ve lost control over your photos!
- Your photos are released on social media.
- Your Ex´s followers have created memes, using your pictures, to slut and body shame you.
- Blank Challenge: The Public decides what the Challenge is.
2. Trolled on Twitter
Scenario Card (printed on a card with copies given to all teams, or projected on the wall, or written on butcher paper)
You are a feminist activist. You are opposed to the misogynistic and bigoted statements that your current President has made. You appeared in a video that went viral, criticising the President. Now, there is a Twitter mob against you.
Challenge cards for Trolled on Twitter
- Twitter responds to your reports stating there is no violation of community standards.
- You are queer. But no one in your family and your work place knows about it. If this gets out, you´re in trouble.
- Your photos are made into memes with derogatory remarks that attack both your person and your values. They get circulated.
- A local celebrity just re-tweeted a meme against you.
- Someone posts private information about you: Your address, your location, your work place.
- Blank Challenge Card: The Public decides what the Challenge is.
3. Faked on Facebook
Scenario Card (printed on a card with copies given to all teams, or projected on the wall, or written on butcher paper)
Someone is screen-grabbing all of your photos on Facebook, and has created accounts using them, with your name. You don’t know how many accounts there are or why this is happening. And you don’t know how to make it stop.
Challenge cards for Faked on Facebook
- Some of the accounts using your name and photos are posting rude, misogynist, racist comments.
- One of your donors/clients followed a fake account because they thought it was you. Now your donor/client is emailing you demanding an explanation.
- The fake accounts in your name have real information about you.
- A fake account in your name and with your photos is posting obscene photos on your organisation’s Facebook wall.
- You have been locked out of Facebook. You’ve lost access to your Facebook account.
- Blank Challenge Card: The Public decides what the Challenge is.
4. Porn Pretender
Scenario Card (printed on a card with copies given to all teams, or projected on the wall, or written on butcher paper)
You’ve just been informed by a friend that a video with someone that looks a lot like you is circulating on a do-it-yourself porn site with your first name, city and profession, and the number of views is rising.
Challenge cards for Porn Pretender
- The video starts out with you, but the explicit scenes are with someone who only looks like you.
- The site Terms of Service say consent of all subjects must be obtained before uploading. You report the video and say it does not have your consent, but they still haven’t taken it down.
- The video is being picked up and promoted by other porn sites.
- Someone just tweeted your handle with a link to the video.
- Men on the street are leering at you and say they’ve seen your video.
- Blank Challenge Card: The Public decides what the Challenge is.
5. Disinformation to Discredit
Scenario Card (printed on a card with copies given to all teams, or projected on the wall, or written on butcher paper)
Your organisation is well known for using creative strategies to fight misogyny. It works with communities of all ages, including kids. Someone is trying to discredit your organisation and its director. Now if you search for your organisation, the top result is a warning to parents that your director is part of a ring of so-called "sexual deviants".
Challenge cards for Disinformation to Discredit
- Your organisation is known for it’s community trainings, but fewer people are signing up now.
- Someone has contacted your social media community one by one, sending each follower the link with false information.
- One of your donors contacts your organisation to say they are pulling your funding.
- Your director was just paid a visit by the police after they received an anonymous tip about her.
- The lies get picked up by local media.
- Blank Challenge Card: The Public decides what the Challenge is.
6. Watching and Waiting
Scenario Card (printed on a card with copies given to all teams, or projected on the wall, or written on butcher paper)
You are receiving anonymous messages on your phone and social networks. The messages are friendly greetings, but the sender won’t say who they are and seems to know a lot about what you are doing and where you are.
Challenge cards for Watching and Waiting
- Messages are becoming more and more frequent, from one or two a day to a dozen.
- You report the problem to the police, but they say they are only messages, friendly ones at that. If you don’t like them, don’t read them.
- Your office secretary says they talked with your boyfriend and he seemed really nice. You don´t have a boyfriend.
- One of the messages mentions a close family member (your child, sibling or parent).
- The tone of the messages is becoming more aggressive towards you.
- Blank Challenge Card: The Public decides what the Challenge is.

Role instruction cards
Advisors instructions (1 for each team)
Given the Scenario, pick one strategy from your cards or create one of your own. You cannot propose a multi-step strategy. You can only show one option to your team’s Survivor and justify why you think it is a good choice. As a team, you have five minutes to discuss the presented options and help the Survivor make a decision. Your goal is not to have the Survivor pick your strategy, but for the Survivor to be able to argue their preferred choice well enough to get support from the Public.
The Public instructions (1 or 2 if it’s a large group)
Listen carefully to the Scenario and to the Survivor profiles. As Survivor teams decide on a strategy, discuss amongst yourselves who makes up the online public and how these bystanders might affect the Scenario. Once Survivors present their preferred strategy, you can ask them questions. Individually decide which Survivor has the best response to the Scenario and give them your support token (optional), explaining your choice. Then collectively choose a Challenge Card to begin the next round. In the final challenge round, discuss possible conclusions to the Scenario. After Survivors present their final strategies and tokens are counted to see who had more Public support, the Public will present their preferred ending to conclude the game.
Game Facilitator instructions (1)
Game facilitators must be familiar with all game instructions and get the game started by forming the two Survivor/Advisor teams, and the Public. Help the Public choose a good scenario for their context. Keep time: Teams will have 7-10 minutes to decide on a strategy and 5 minutes each to persuasively present their strategy and answer questions. Make sure Survivors are only presenting one strategy at a time. No round should last more than 20 minutes. The game concludes with the Public’s proposed closure to the Scenario, usually after three challenge rounds. End with a reflection on how each team felt during the process. The scenarios and challenges explored in this game could have been experienced by anyone, so it’s important for the Game Facilitator to keep a fun, light atmosphere as much as possible.

Game Play
Playing to “win”
This game is designed to have quick, strategic responses to very difficult and often triggering situations. It was purposefully designed in timed, competitive rounds and to be carried out in a light, swift way to encourage debate and discussion with a degree of distance. A gaming Scenario generates adrenalin and expectation around escalations, both a part of the online GBV experience. An atmosphere of game competition is one way to bring in these elements when strategising.
However, it is important to note that some groups are not comfortable with competition or able to assert that one Survivor Team strategy was better than the other presented, so using tokens as points and declaring a “winner” in your game is entirely optional. The Game Facilitator should decide if they want to introduce competition and tokens before beginning the role-play.
If using tokens, each member of the Public should receive four tokens (in the form of cut-up colored papers, poker chips, individually wrapped candies, stickers, etc.) at the beginning of game play. Each member of the Public will award one token per round to the Survivor Team whose strategy best fit the Survivor profile and context. At the end of three rounds the Public debates; if there is consensus, five extra points can be awarded to the Survivor who has chosen the best overall set of strategies. The total number of tokens will determine which Survivor Team “won” the scenario. The round ends when the Public provides closure to the Scenario with a plausible conclusion.
Facilitation note: When inviting people to play, the Game Facilitator should have alerted possible participants that this role-play will be talking about gender-based violence on the internet and distressing subject matter will come up, in case anyone wants to opt out beforehand. The Facilitator should remind participants of this before starting the game and encourage all participants to be sensitive to each other in the role-play process.
Game setup – 15 minutes
Game Facilitators must be familiar with the following game instructions and make sure teams understand their roles.
Get the game started by forming Survivor Teams A and B and the Public.
- It may be better if the volunteer Survivor has not experienced online GBV themselves.
- There are four types of advisors: Legal, Communications, Solidarity and Skills. The Advisors do not have to be specialists in the area assigned to them (ie legal advisors do not have to be lawyers).
- The Survivor Teams decide who plays what role in the team. That role will last until Scenario rounds are played out. If there are fewer people in the game, Advisors may have to play the role of two advisors.
Give each Survivor Team flipchart paper, markers and the Survivor and Advisor Instructions.
- Their first task is to develop the Survivor profile and context and draw that persona on flipchart paper.
- Remind them they don’t have to think up a scenario, just information about the Survivor:
- How old are they?
- Do they live in a rural or urban area?
- What are their family, friend and work communities like?
- Their sexuality, religion, language?
- Their education level, tech skills?
- Teams have only 5-10 minutes to draw up their Survivor profile.
While Survivor Teams do this, the Game Facilitator gives the Public their instruction cards and briefs them on their role:
- Encourage the Public to think about who is in their midst – are they friends, family, trolls, bystanders,representatives?
- How might bystanders affect the way the Scenario evolves?
- Members of the Public can decide to take on a specific role and react to the Survivor Teams as that role (ie conservative family member, best friend, troll), or as themselves.
The Game Facilitator or Public may choose a Scenario for the game. The available Scenarios are
- Blackmailed to Go Back
- Trolled on Twitter
- Faked on Facebook
- Porn Pretender
- Disinformation to Discredit
- Watching and Waiting
Each Scenario has its own Challenge cards. Alternatively, the Game Facilitator or Public can create one based on their context.
TIP: If creating your own Scenario, keep in mind the Scenario should start at the point that the Survivor is concerned about what is happening, but not already facing a full-blown attack.
Round 1 – 20 minutes
- Survivors present their personas to the Public.
- The Game Facilitator reads the Scenario out loud.
- In their Survivor Teams, each Advisor has 2 minutes to pick one strategy from their deck to recommend to the Survivor. Multi-step strategies are not allowed. Show one option to your team’s Survivor and justify why you think it is a good choice.
- Each Team then has five minutes to discuss the available strategies and help the Survivor make a decision, based on the best option for their Survivor profile.
- The role of the Advisors here is not to get their strategy picked, but for their team to get support from the Public with a persuasive presentation of the strategy chosen by the Survivor.
- Survivors can only pick one strategy at a time, and it is their decision, not the Advisors’.
- While the Survivor Teams discuss for no more than 8-10 minutes, the Public should also be discussing the Scenario and what strategy they think the teams should take. The Public begins to imagine possible ways the Scenario will escalate, and examines Challenge cards.
- Each Survivor presents their first strategy to the Public, arguing why it is the best option for their profile. The Public can ask questions but each Team has a maximum of 5 minutes presentation time.
- The Public provides feedback on the choices. If using tokens, each member of the Public votes, explaining their choice.
Throughout, the Game Facilitator keeps time and tries to keep a fun, light atmosphere as the scenarios and challenges explored in this game could be upsetting for participants if explored too deeply.
Round 2 – 20 minutes
- The Public selects and presents the first Challenge.
- Survivor Teams proceed the same as Round 1.
Round 3 – 20 minutes
- For the Survivor Teams, same as Round 2.
- While the Survivor Teams debate, the Public is asked to come up with a closure to the Scenario. What kind of solution do they foresee as plausible, what strategies would they add? The Game Facilitator, while not encouraging a “happy ending” does ask the Public to look for feasible, and if possible positive solutions to this escalating violence.
- Survivors present their strategies.
- If using tokens, the Public makes a consensus decision as to which Survivor Team had the most coherent set of strategies and as a group awards 5 extra tokens. Each Survivor Team counts tokens to see who “won” the Scenario. If not using tokens the Public will provide feedback.
- The Public presents their proposed solution.
Wrap up – 15 minutes
The Game Facilitator leads a discussion about strategies learned and how participants felt given their assigned roles.

Planning response to online GBV [tactical activity]
This activity is designed to unpack individual, community and movement response to incidents of online violence. For this activity to work, an example of a specific incident of online GBV is required.
Learning objectives this activity responds to
- An understanding of the forms of online online GBV and its impacts on the survivors and their communities.
- An understanding of the continuum of violence between the offline and the online spheres, and the power structures that allow it.
- Ideas, strategies and actions about the ways in which online GBV, especially in their participants´ contexts, can be addressed.
Who is this activity for?
While is activity is can be used for participants who have basic understanding of online GBV, it is more useful for folks that play a role in responding to, or organising such responses, to incidents of online GBV.
Time required
This will require at least 4 hours.
Resources needed for this activity
- Flip chart paper that explains the Mapping responses to online GBV table (see below)
- Written down online GBV examples for each group to refer to
Mechanics
It would be important to have unpacked a specific online GBV scenario with the participants before doing this activity. It is recommended that you do this Tactical Activity after you have done the Deepening Activity: Deconstructing Online GBV. Depending on the size of the group, break them down into smaller groups to plan how to respond to an incident of online GBV.
Present the table to map the response to online GBV incidents. This is a way to prioritise and timeline a variety of responses to online GBV and to have a collective approach to it.
The map has the following elements:
From Time of Incident
In the template, this is broken down into responses in the first week, within the first month, and in 6 months. Depending on the severity and escalation of the incident, this can change with the exception of the responses within the first week since the time of the incident. Some responses go beyond 6 months, especially those where the survivor takes legal and / or advocacy actions. Some kinds of online GBV are resolved quicker than other, so tables for that would not take up to 6 months. The goal here is to timeline actions according to immediate, short-term and medium term.
Individual response
This has to do with the what actions the person experiencing online GBV should take.
Community response
This means the actions that the individual´s friends, organisations, networks and communities will take to help address the online GBV or provide support to the survivor. Some guide questions for this:
- Who is the community around the individual?
- Does the individual have close friends / family they can rely on for support as they deal and recover from the incident?
Movement response
This are the actions that the larger women´s rights and feminist movements can take in response to specific online GBV cases.
Digital security response
These are the actions that the individual and their community will take to safe-guard their online communications, and prevent any more breaches of privacy or escalate the harassment. This could include: securing online spaces and / or devices, reporting incidents to platforms, self-doxxing to know what information is available online about the survivor.
Physical security response
These are the actions that the individual and their community will take in order to safe-guard the individual´s security outside of the internet. This could be preventative tactics and strategies against escalation of online GBV incidents. Or, it cases where the offline GBV already has physical security impacts, this might be corrective tactics.
Well-being response
These are actions that can be taken to ensure that the individual is able to take care of themselves. These are also actions that the community and the movement can take to make sure that the individual under threat is supported.
Advocacy actions
These are actions that can be taken in order to seek redress about the incident beyond just stopping the online GBV. These could include legal actions against perpetrators and / or platforms, or campaigns against online GBV. At the very least, Advocacy Actions documents incidents so that others may learn from it.
Mapping responses to online GBV incidents (with guide questions)
| From Time of Incident | Individual response | Community response | Movement response |
| 1st week | Digital security response | ||
| What does the survivor need to be doing to secure their online communications in the 1st week since the time of the incident? Where did the online GBV happen? What do the platforms allow its users to do to safe-guard their accounts? What information about the individual is available on the internet, and what can they do to take that content down? |
Who can support the individual if they need technical assistance to carry out actions to protect their accounts and communications? Who can support the individual in reporting the incident to the platform? |
Will there be a need for the larger movement to support the individual and their community to report the incident? | |
| Physical security response | |||
| Is information about the individual available online? What can the individual do in order to protect themselves? | What available safe spaces can the community offer? | ||
| Well-being response | |||
| Does the individual need to be offline? Does this individual need a person(s) to support them in monitoring certain platforms? Who provides support and safety for the individual? How will they stay connected to their support resources? What are the ways in which the survivor finds comfort and solace? |
Who in the community will be the support person(s)? | Does the person want others in the movement to know about the incident? | |
| Advocacy actions | |||
| What actions does the individual want to take in order to address the incident? Note: If the individual decides to go the legal route, there needs to be understanding of the national laws / policies within the group, but also the advocacy actions will be far more complicated. |
Who can support the individual in documenting the incident? | Will there be a call for the movement to respond to the incident as it happens? | |
| Within 1 month | Digital security response | ||
| What follow-up digital security tactics and action will the individual take? What changes in practice does the individual need to do in order to further safe-guard themselves? |
What changes within the community´s communication practices need to change in order to protect themselves from further incidents? Are skills and knowledge available within the community in order to implement such changes? If not, who can the community reach out to? |
||
| Physical security response | |||
| What does the individual need in order to have safer living and working conditions? | What changes within the community´s practices need to change in order to protect themselves from further incidents? Are skills and knowledge available within the community in order to implement such changes? If not, who can the community reach out to? |
||
| Well-being response | |||
| Does the individual need professional help in order to deal with the incident? | Do the individual´s main supporters need professional help in order to under deal second-hand trauma? | ||
| Advocacy actions | |||
| For legal response: Has the the incident been reported to the proper authorities? What kind of documentation is required? | What are the opportunities within the community to provide legal support for the individual? | ||
| 6 months | Digital security response | ||
| What needs constant monitoring in the individual´s online activities and communications? | |||
| Physical security response | |||
| Well-being response | |||
| Advocacy actions | |||
| Opportunities and spaces where the incident can be shared in order contribute to the larger documentation of online GBV? | |||
Filling in the table or discussing actions to take at different times at by different actors will be an opportunity to discuss and share strategies and tactics among and with the participants.
If there are multiple groups working on their tables, it is important for the trainer / facilitator to go around to see if there questions and information that needs sharing.
Facilitation Note: It doesn´t have to be a matrix. If you are not spreadsheet type of trainer / facilitator, use another way for the groups to work out actions and strategies to respond to online GBV incidents. If your participants are also not comfortable with tables, then encourage them to strategise using a different methodology. You can use sticky notes to list down the different responses and cluster them into the different types (Digital Security, Well-being, Physical security, Advocacy Actions). The purpose of this activity is to strategise responses and to make sure that the participants are thinking about online GBV response in a more integrated way (rather than just focusing on the digital security actions) and in from a collective perspective (rather than putting all the onus of the response on the individual experiencing online GBV).
To synthesise the activity, focus on the following:
- Learnings about how platforms respond to cases, and what kind of advocacy we need to do in order to make them more responsive to online GBV
- Resources available for activists that groups have not thought of.
- The importance of approaching responding to online GBV from a collective perspective
Facilitator preparation notes
In this session, the facilitator / trainer will need to have more direct interventions about the following:
- basic digital security tactics, safeguarding accounts and devices
- strategies for physical security
- knowledge of the ways in which platforms respond to incidents
- knowledge of legal redress options in the participants´s countries
- knowledge of impact of online GBV on participants´ well being and some strategies to address re-traumatisation of participants
Useful Resource: Hey! Is Your Friend Being Attacked Online?

Meme this! [tactical activity]
This activity is to get participants to respond to more general forms of online misogyny, transphobia and homophobia in a way that uses humour and wit. This is by no means intended to make light of online GBV but rather allow an outlet for participants to collectively deal with trolls on the internet.
Learning objectives this activity responds to
- Ideas, strategies and actions about the ways in which online GBV, especially in their contexts, can be addressed.
Who is this activity for?
This activity can be carried out with participants with different levels of understanding and experience of online GBV
Resources needed for this activity
- Post-its
- Flip chart paper, card
- Lots of markers
If you want to give the participant the option to create gifs: Internet connection and access to Giphy
Time required
This activity will require about 2.5 hours.
Mechanics
This activity happens in three phases:
- Confronting misogynistic / transphobic / homophobic messages
- Counter-messaging (60 minutes)
- Unpacking counter-messages (60 minutes)
With everyone in the same room, ask each participant to share up to three misogynistic /transphobic / homophobic messages they have seen online. Ask them to write down the messages on post-its, one message per post-it.
Note: The message does not have to be blatantly -phobic or sexist, they could be common points that come up all the time (i.e., "you want censorship", "you are limiting my freedom of expression", "if it´s not physical, it´s not real violence" or victim-blaming messages.)
Then on the wall, cluster similar messages. This can be an opportunity to unpack the messages and discuss ways in which they are harmful to women and queer people online.
Once the messages are clustered, group the participants.
Note: Alternatively, if the workshop is pressed for time, you can prepare the messages to create counter messaging against. But this will require you to know what messages the participants encounter most during their time online.
The goal of each group is to create counter messages to the harmful messages. They can use different ways to respond: write Tweets, create posters, create memes, create gifs (depending on the skills in the room), have a hash-tag campaign.
In creating responses, ask the groups to consider the following:
- Who is this message addressed to?
- Why will this message be effective to who is being addressed?
- What values underpin your counter-message?
- What form will it have? What kind of language?
After everyone is ready with their messages, everyone shares what they came up with. Just the messages they created. Collectively, discuss the effectivity of each counter-message based on the considerations above.
To synthesise, focus on the following:
- What kind of messages work
- Lessons learned about responding to trolls online
Facilitator preparation notes
While this activity is a bit more light-hearted than some of the activities in this module, the facilitator / trainer should also prepare for possible moments of stress for the participants.

Mapping digital safety [tactical activity]
This activity is designed to introduce participants to respond to different forms of online GBV.
About this learning activity

This activity is designed to introduce participants to respond to different forms of online GBV. The activity is carried out in three teams, and each team takes on one specific form of online GBV from among:
- Blackmail
- Cyberstalking
- Hate Speech
Each team consists of a facilitator who has a set of Scenario cards and team members who have a set of Rights cards each.
The game begins with the facilitator helping participants reflect on the specific form of online GBV and how it manifests.
After a basic understanding has been established, the facilitator then plays a scenario card, and facilitating a discussion among team members about the scenario. Team members then respond to the scenario collectively by playing one Rights card each to safeguard themselves in the scenario. Members then discuss how the Rights they have selected would be violated in that scenario. The facilitator then moves on to the next Scenario card. Two scenarios can be played out by each team.
If time is available at the end of the activity, teams can gather together to discuss their reflections about their specific forms of online GBV and the related rights that protect them.
Learning objectives this activity responds to
- an understanding of the forms of online gender-based violence (online GBV) and its impacts on the survivors and their communities
- an understanding of the continuum of violence between the offline and the online spheres, and the power structures that allow it
- ideas, strategies and actions about the ways in which online GBV, especially in their contexts, can be addressed
Who is this activity for?
This activity can be used with participants with different levels of understanding about online GBV and the rights stated in the Universal Declaration of Human Rights.
Time required
This activity will require about 2-3 hours.
Resources needed for this activity
- Printed Scenario cards (2 Scenario cards per team)
- Printed Rights cards (6 Rights cards per team member of all teams)
- Space big enough for 3 teams to be able to have discussions
- A table big enough to accommodate the Rights Cards that each team will be presenting per round

Mechanics
Players
The participants will be split into three teams:
- Team A – Discussing Blackmail
- Team B – Discussing Cyber Stalking
- Team C – Discussing Hate Speech
Each team also has a Facilitator. It is suggested that each team be comprised of 6 members and 1 facilitator.
Cards
The members of all three teams have the same deck of printed Rights cards. Each card has the Right printed on the side facing up, and a brief description of the Right facing down. Please refer to the section on Rights for examples of Rights that can be included.
Each facilitator is given 3 sets of Scenario cards specific to the team’s form of online-GBV. Please refer to the section on Scenarios for sample scenarios per team.
Rights
Some of the Rights that can be added to the deck of Rights cards are as follows:
- Right to Freedom of Expression (Article 19, Universal Declaration of Human Rights)
"Everyone has the right to freedom of opinion and expression; this right includes freedom to hold opinions without interference and to seek, receive and impart information and ideas through any media regardless of frontiers."
- Right to Privacy and Freedom from Defamation (Article 12, Universal Declaration of Human Rights)
"No one shall be subjected to arbitrary interference with his privacy, family, home or correspondence, nor to attacks upon his honour and reputation. Everyone has the right to the protection of the law against such interference or attacks."
- Right to Freedom from Violence (United Nations Declaration on the Elimination of Violence Against Women)
"States should condemn violence against women and should not invoke any custom, tradition or religious consideration to avoid their obligations with respect to its elimination. States should pursue by all appropriate means and without delay a policy of eliminating violence against women... [This includes] any act of gender-based violence that results in, or is likely to result in, physical, sexual or psychological harm or suffering to women, including threats of such acts, coercion or arbitrary deprivation of liberty, whether occurring in public or in private life."
- Right to Protect your Artistic Work (Article 27, Universal Declaration of Human Rights)
"Everyone has the right to the protection of the moral and material interests resulting from any scientific, literary or artistic production of which he is the author."
- Right to Work (Article 23, Universal Declaration of Human Rights)
(1) Everyone has the right to work, to free choice of employment, to just and favourable conditions of work and to protection against unemployment... (2) Everyone who works has the right to just and favourable remuneration ensuring for himself and his family an existence worthy of human dignity, and supplemented, if necessary, by other means of social protection...
- Right to Public Participation (Article 27(1), Universal Declaration of Human Rights)
"Everyone has the right freely to participate in the cultural life of the community, to enjoy the arts and to share in scientific advancement and its benefits."
Other Rights from the Universal Declaration of Human Rights may also be added to the deck if deemed necessary.
Scenarios
Please refer to the cartoon strip and section on “How People Experience Blackmail” here for sample scenarios on Blackmail.
Please refer to the cartoon strip and section on “How People Experience Cyberstalking” here for sample scenarios on Cyberstalking.
Please refer to the cartoon strip and section on “How People Experience Hate Speech” here for sample scenarios on Hate Speech.
Game play
Three teams are formed, one to discuss each form of online GBV from among Blackmail, Cyberstalking, and Hate Speech. Each team chooses one facilitator or a facilitator is assigned to them, and the teams with their respective facilitator move to different parts of the room. Each Facilitator is given a deck of Scenario cards specific to their team, and each team member is given a deck of Rights cards. The game is now played in 3 stages, with an optional 4th stage that can be incorporated depending on the availability of time.
Stage I: Brief reflection
The facilitator of each team can use resources from the following links to start a brief reflection session.
This is to establish a brief understanding of the specific form of online GBV before moving on to the next stage of the game involving scenarios. This reflection can be localized for the group, keeping in mind the different identities of members involved. This stage can be shortened or extended based on the experience level of the participants in the group.
Stage II: Scenarios
Once, the group is fairly comfortable with what entails the specific form of online GBV being discussed in the team, the scenario-playing can begin. The facilitator plays a Scenario card which describes a Scenario relating to the form of online-GBV being discussed in the team. The section on Scenarios links to possible sample scenarios for this purpose. The facilitator then asks some questions about this scenario.
For instance, suggested questions for Cyberstalking are:
- Do you think the situation faced by X in the scenario is a case of Cyberstalking?
- What could X have done to avoid this situation? (Please note that this question should NOT be posed in a manner that may assign any blame to the victim of cyberstalking, but in a healthy manner that highlight safe online practices)
- How would you have dealt with the situation if it were you?
The discussion around these questions can be localized to the group.
Stage III: Rights
Once a discussion of the scenarios is completed, the next stage of the game involves the Rights cards held by team members. Team members now collectively decide amongst themselves which Rights cards they want to play to safeguard themselves in the Scenario that has been played out. Each team member plays one Rights card. All the Rights cards played are placed on the table before the facilitator.(As mentioned earlier, it is suggested that this game be played with 6 members per team. However, depending on the actual number of members in the team, either the same card can be repeated by members or each member can play more than one card).
The facilitator now asks the team members details about how the Rights cards played by them would help safeguard themselves in the specific scenario.
This is a good time for the facilitator to ask team members about whether or not there are any local laws that relate to these rights and how they can be (or have been) used in similar scenarios. This discussion can also broaden into pros and cons of using the court system or law enforcement.
Some details of how the Rights relate to these specific forms of online-GBV can be found in the “Related Rights” section of the following links:
The facilitator then moves on to the next scenario card and the process is repeated. It is suggested that two scenarios be played out per team, but more can be added based on the availability of time.
Stage IV (Optional)
This stage is optional, and can be played if there is an availability of time. Once each team has played out Scenarios and Rights in their own groups, the teams can come together to discuss insights from each of their activities.
Some discussion points can include:
- What did we learn about the specific form of online-GBV discussed by our team?
- What are the scenarios we discussed that can arise relating to it?
- What are the rights we discussed can be used to safeguard ourselves in such scenarios?
Facilitator preparation notes
Some guidelines to follow, if you do choose to use this learning activity:
- During the discussion on Scenarios, allow each participant to respond to the scenario in their own way. Don't rush them. Don´t correct their grammar. Don't interrupt them.
- Do not force everyone to respond. Maybe, for some people, being able to write down their responses is preferable. Not everyone needs to respond, but encourage everyone to do so.
- If a participant is triggered, take a break. Don't force them to continue with the activity.
Please read the notes on Holding up a Healthy Conversational Space and Intersectionality and Inclusivity to know more about creating safe, inclusive spaces of discussion.
Here are resources that can help you better prepare for this activity:
Take Back the Tech! has compiled a comprehensive set of resources on each of the forms of online-GBV discussed in this activity. These resources have been cited throughout the activity, and can be referenced here for further details:
- Blackmail: https://www.takebackthetech.net/know-more/blackmail
- Cyberstalking: https://www.takebackthetech.net/know-more/cyberstalking
- Hate Speech: https://www.takebackthetech.net/know-more/hate-speech
Suggested tweaks
This activity is recommended to be carried out as a Tactical Activity. It can also be split into two activities – Stage I can be played separately as a Starter Activity, and Stage II and III together can be played as a Deepening Activity following the Starter Activity.

Resources | Links | Further reading
- What is technology related VAW?
- Forms of Online GBV
- Good questions on technology-related violence
- Cases on women’s experiences of technology-related VAW and their access to justice
- Infographic: Mapping technology-based violence against women - Take Back the Tech! top 8 findings
- TakeBacktheTech's Report Card on Social Media and VAW
- Internet Intermediaries and VAW
- The Vocabulary Primer What You Need for Talking about Sexual Assault and Harassment